Digital identity system
A digital identity system is an essential and fundamental building component in our digital world. It is responsible for bridging users from the physical world to the digital one.

The digital identity system is responsible for identifying users in the digital world through an identifier. It is also responsible for authenticating users against their identifiers. After the authentication procedure, the user can interact with the digital system and initiate digital interaction.
Identifiers are an essential concept in any system. Almost, we found identifiers everywhere. Examples:
-
National ID cards: this is your national identification number as a citizen. Any interaction with any service in your country is associated with your national ID.
-
Passport ID: you’re identified at the international level by your passport.
-
Postal address: it is an identifier in the postal mail network.
-
Telephone number: it is an identifier in the telephone network. When you want to call someone, you tap his identifier.
-
Email address: it is an identifier in the email network.
-
IP address: it is a machine identifier in the internet network.
An identifier is a critical component in a digital identity system. It is how a digital system(eBay, LinkedIn, Facebook, Amazon, etc.) refers to users. Examples: username, email, phone number.
The most common method to authenticate users is through a password.
Digital identity models
Model 1: Siloed identity

In this model, the end-user has a digital identity with each used digital system. In more detail, he has a digital identity that is issued, managed, only known, and discoverable to a particular digital system. We often have a few centralized digital identifiers like email addresses, phone numbers, etc. We use them to create many digital identities.
If you use N digital system, you will have N digital identity. So, one user in the physical world is mapped to an N different users in the digital world.
This model required registration with each digital system. It defines how this system will identify you in the digital world. The registration process is a demand to the digital system to create a new digital identity(specify a digital identifier and the parameter needed by an authentication procedure). The company will verify the specified identifier via mail if you use your mail address or SMS if you use your phone number as an identifier.
In this model, centralized companies own and control our digital identity. They act as intermediaries that manage our digital identity. Our digital identifiers are centralized, owned, and controlled by companies.
Model 2: Federated Identity(Third-Party IDP)

The idea of the second model is to choose a digital system that will manage your digital identity. Then, you can share it with others.
Social Login is a single sign-on for end users. Using existing login information from a social network provider like Facebook, Twitter, or Google, the user can sign into a third-party website instead of creating a new account(digital identity) specifically for that website.
This model is also used a lot by companies. When a company has multiple software programs that their workers use, it is known as a Single Sign-On(SSO) for workers where an identity provider(IDP) exchanges digital identity data with a service provider(SP). You have one digital identity(one digital identifier) within the company you‘re working on. You will use the same one with all applications and enterprise platforms inside the company.
Multiple standards define protocols and the data format to exchange digital identity(authentication and authorization data) information between different digital systems like SAML, Oauth2, and OpenID Connect.
This model has an advantage from a user digital experience perspective. Instead of creating a new digital identity with every used digital system, you can make a few ones and share your identity between digital systems. But it has a significant disadvantage. Suppose you use your social login to share your digital identity with other online services. If the company blocks your account, is out of business, stops digital identity sharing, or you want to delete your account, you will lose your account with other online services that use your social login.
In this model, a few companies(Facebook, LinkedIn, google, etc.) act as intermediaries that manage our digital identity. Your digital life is under the control and authority of a few companies. They own your digital identity. They can decide to delete you from the digital world whenever they want. They have all the authority over your digital life and digital existence.
The siloed identity and federated identity are centralized models: your digital identity is owned and controlled by a centralized companies. The federated identity model is more centralized than the siloed model.

Model 3: Blockchain-based identity

A new type of identifier and a passwordless authentication technique(based on a digital signature) lead to a more efficient digital identity model. It is a decentralized model where intermediaries do not manage our identity. So, blockchain provides a new model to identify physical users in our digital world.
An identifier that is decentralized is the key point to having a decentralized identity system. A blockchain address is a new identifier owned and controlled by the end user.
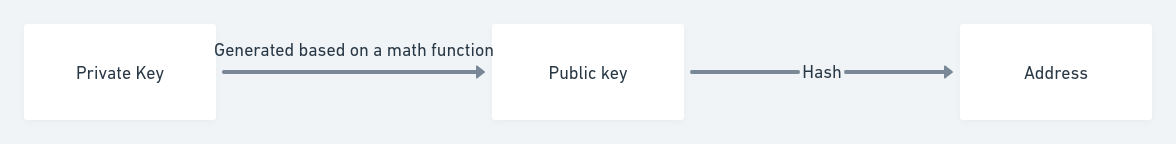
The private key is generated randomly by the end user. The public key is derived from the private key. It is based on public key cryptography. Then, an address is the hash of the public key.
For example with Bitcoin, The private key (k) is a number, usually picked at random. From the private key, we use elliptic curve multiplication, a one-way cryptographic function, to generate a public key (K). From the public key (K), we use a one-way cryptographic hash function to generate a bitcoin address (A).

Example of Bitcoin address:
-
1GrkYWRfTVaj5996gitTz3yWFAjtE9cZMz
-
1Bir32WNYixVaE282o6krQFXH9DN57FeMZ
Example of Ethereum address:
-
0x8448Ff4b2733b52f62d81ca46d64bD16786299Cd
-
0x2555e3a97c4ac9705D70b9e5B9b6cc6Fe2977A74
The authentication procedure is based on a digital signature. The idea is to sign the digital interaction with the private key. A sign function will generate a digital signature. Then, the digital system can verify the validity of the digital interaction based on the digital interaction, address, and digital signature.


Digital signatures are based on public key cryptography, also known as asymmetric cryptography. They ensure transaction authorization. An important thing to understand is if you don’t have the signing key or if somebody doesn’t have your signing key, they cannot sign on your behalf. It doesn’t matter how many signatures they see. No one cannot generate signatures on your behalf if they don’t have your signing key. The private key must keep secret. There are three purposes of the digital signatures in a blockchain:
-
Authentication: make sure the message was created by a known sender.
-
Non-repudiation: the sender cannot deny sending the message.
-
Data integrity: the message wasn’t altered in transit.
The user's digital identity is no longer owned and controlled by intermediaries; instead, it is owned and controlled by him: our sovereignty over our digital identity(our digital identifier). The digital identity system is decoupled from centralized companies. This model is a fully decentralized digital identity system.The software that allows users to manage their digital identity in a decentralized manner is called a wallet.
The wallet manages our identifiers in the digital world, which are addresses. They generate them using seed phrases. The wallet is also responsible for signing digital interactions based on the private key corresponding to the selected address. The most used wallet is called “Metamask”.
Now, as an end user you should be familiar with wallets as you did with browsers before.
EIP-4361: Sign-In with Ethereum(SIWE)
It is a movement that tries to standardize the use of blockchain-based digital identity by off-chain services like web2 platforms. The identifier used within SIWE is a blockchain address.
Sign-In with Ethereum describes how Ethereum accounts authenticate with off-chain services by signing a standard message format parameterized by scope, session details, and security mechanisms (e.g., a nonce).
Sign-In with Ethereum is a new form of authentication that enables users to control their digital identity with their Ethereum account and ENS profile instead of relying on a traditional intermediary.
It can be extended to use any blockchain address: Solona, Tezos, etc. This concept is well used by OpenSea(The biggest NFTs marketplace in the world) within their platform.
Model 4: Self-sovereign identity(SSI)
It is a new digital identity paradigm. It is based on a new digital identifiers called decentralized identifiers(DIDs).
Self-sovereign identity—commonly abbreviated SSI—is a new paradigm for digital identity on the internet: i.e., how we prove who we are to the websites, services, and apps with which we need to establish trusted relationships to access or protect private information. It manages our digital identities in a decentralized manner. It allows users to self-manage their digital identities without depending on a centralized third party (an intermediary).
A decentralized identifier (DID) is simply a new type of globally unique identifier—not that different from the URLs you see in your browser’s address bar. But at a deeper level, DIDs are the atomic building block of a new layer of decentralized digital identity. DIDs become a W3C Recommendation

SSI is a new totally new digital identity paradigm. For more information, you can visit: