Our team has extensive experience in investigating all kinds of thefts of cryptoassets.
As a rule, our investigation is divided into four main stages:
-
DETAILED INTERVIEWING
Detailed interviews help us gather the right data and clues for the next stages. -
**OSINT ANALYSIS OF DIGITAL FOOTPRINTS OF INTRUDERS
**The information collected about the victim’s interactions with the intruders is carefully parsed by the analysts. All valuable information (blockchain addresses, nicknames, websites, contacts, etc.) is extracted from the content of their correspondence and enriched with data from public sources. -
**ANALYSING THE MOVEMENT OF STOLEN FUNDS ON THE BLOCKCHAIN
**We use our own software “EYE”, which allows us to track the flow of funds between addresses, the transfer of assets through DEX to other blockchain networks, and automatically searches hundreds of different databases for new valuable information. -
**MAKING RECOMMENDATIONS FOR FURTHER ACTION
**At the end of the job, you get a detailed report with as much data on the incident as possible.
For law enforcement agencies, this report will be the basis for initiating proceedings, as well as simplify and speed up the process.
REAL CASE DESCRIPTION
A crypto-user found all his funds missing on a certain day. There was no clue how it could have happened: he kept the SEED phrase from the wallet on a piece of paper, as recommended; only the user himself had access to the device.
STAGE 1 — INTERVIEW
As a result of the interview we found out that a couple of months ago the user bought a new device and installed the Metamask Wallet on it. Our initial hunch that the user had been exposed to a phishing site was confirmed. After collecting all available information, we started our investigation.
STAGE 2 — OSINT INVESTIGATION
Introductions
On October 26, 2021, the victim was installing Metamask Wallet on his new laptop. It was searched using the Yandex search engine on request “download Metamask”.
The victim got to the phishing site metamask.io-ss.ru through the service Yandex.Direct and, most likely, entered his SEED phrase. Then the intruders redirected the victim to a real site so that he or she would not suspect anything.
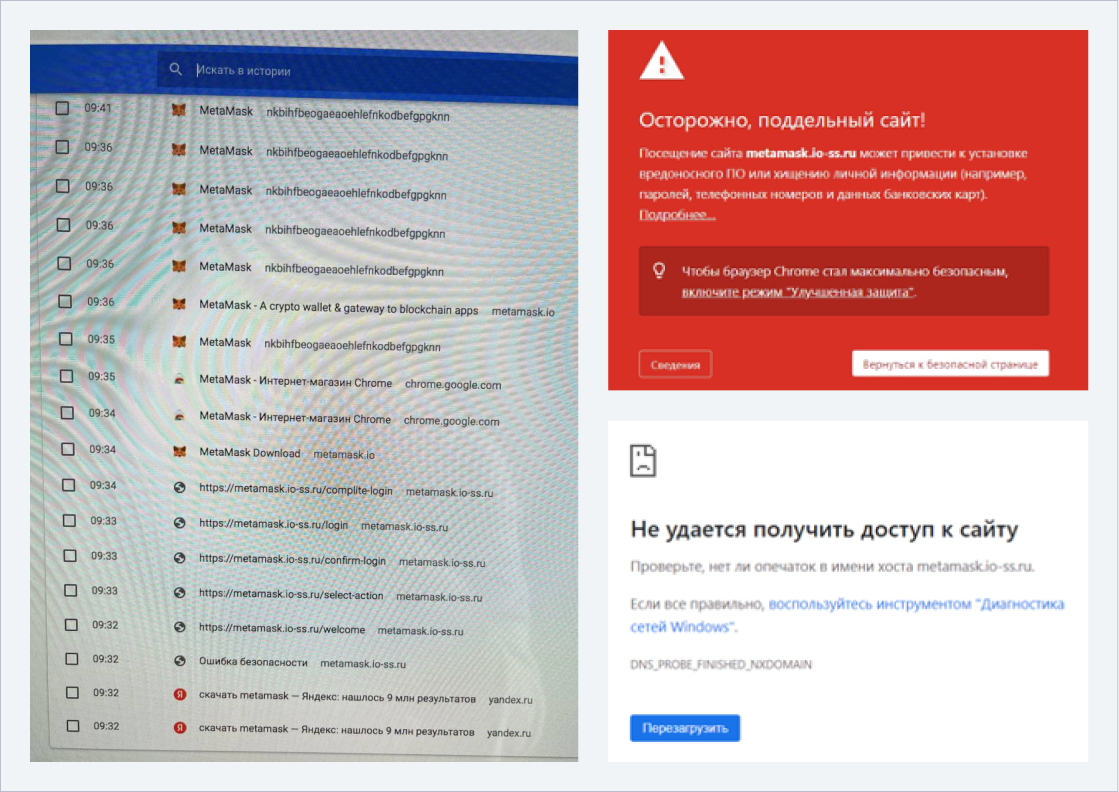
At this point, search engines are already notifying that this resource is dangerous. There have probably already been incidents and referrals. By ignoring the browser warning, we go to the phishing site and see that the intruder has removed it.
Mentions of the site
The mentioned site is in the list of phishing resources in the Github account. No other mentions of the site were found.
Whois, DNS
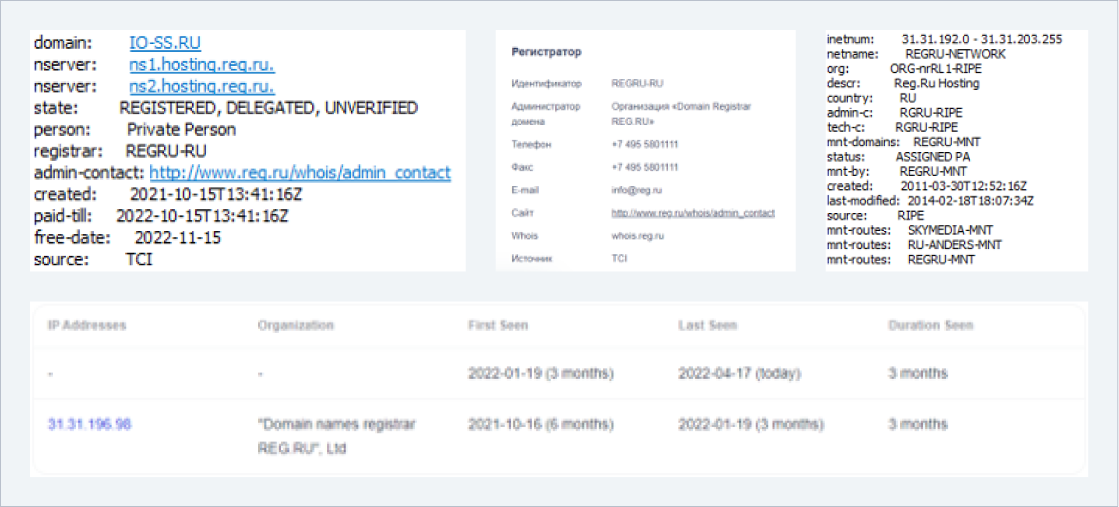
- Whois Data io-ss.ru
• Registrar of the domain: Reg.ru, registered on 10/15/2021
• The main domain and the investigated subdomain are located at IP 31.31.196.98
• ASN 197695 | AS-REG, RU
There are 6,048 domains on this IP.
Other subdomains were not detected:
metamask.io-ss.ru
io-ss.ru
Possible further actions
To request information from “Registrar of domain names REG.RU” LLC about the IP, registration data and payment means of the persons who have bought the domain in question. To request other matches in the context of domains by IP, payment data, and user credentials of the requested domain.
To request Yandex LLC to provide information about IP, registration data and payment means of the persons who have paid for advertising of the site in question. To request data about whether the persons in question have advertised other sites. To request other matches for IP, payment data, user credentials of the requested domain.
After obtaining data on the IP addresses used, send requests to Yandex LLC, Google LLC, and VKontakte LLC in order to identify user accounts that were authorized from them. What search queries were made by these users, what services were used, their payment and other data, as well as other IP authorization addresses.
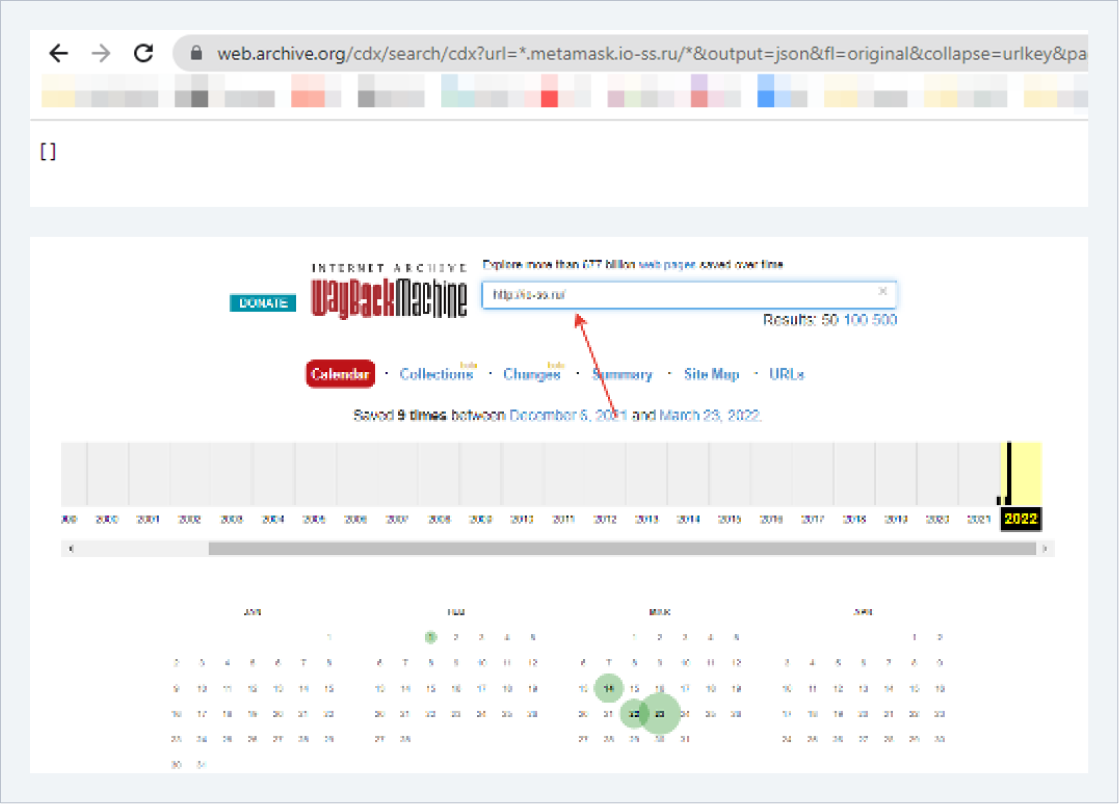
Web Archive
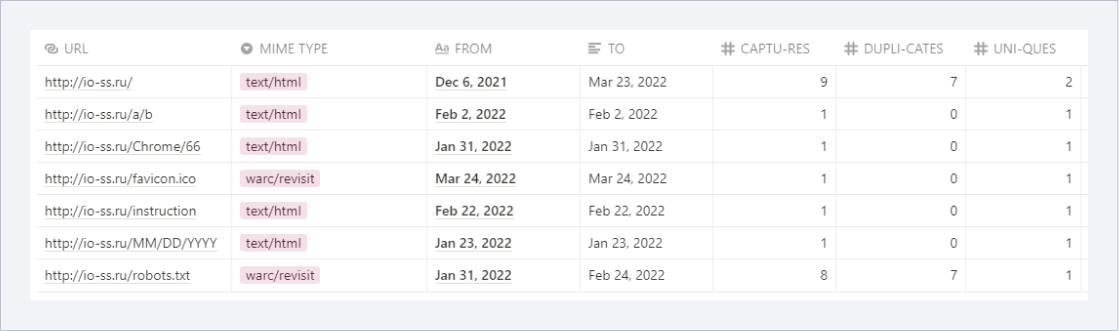
Analysis of the source site io-ss.ru at web.archive.org revealed that the intruder used the TDS.SO (traffic distribution and filtering) service to create mass redirects in order to bypass security systems. An analysis of the pages of the site in question yielded no additional results.
Possible further actions
To request information about the people who signed up for the TDS.SO service on io-ss.ru: IP, registration and payment details.
Initial de-anonymization of the admins of the official TDS.SO Telegram chat was carried out to identify the contacts of the service representatives. No results were found.
Historical data on the domain
Inaccurate information revealed that the original site may have been located on another IP: 136.243.214.242 (domenolog.ru/io-is.ru).
The check was performed in December 2021, most likely before the TDS.SO service was connected.
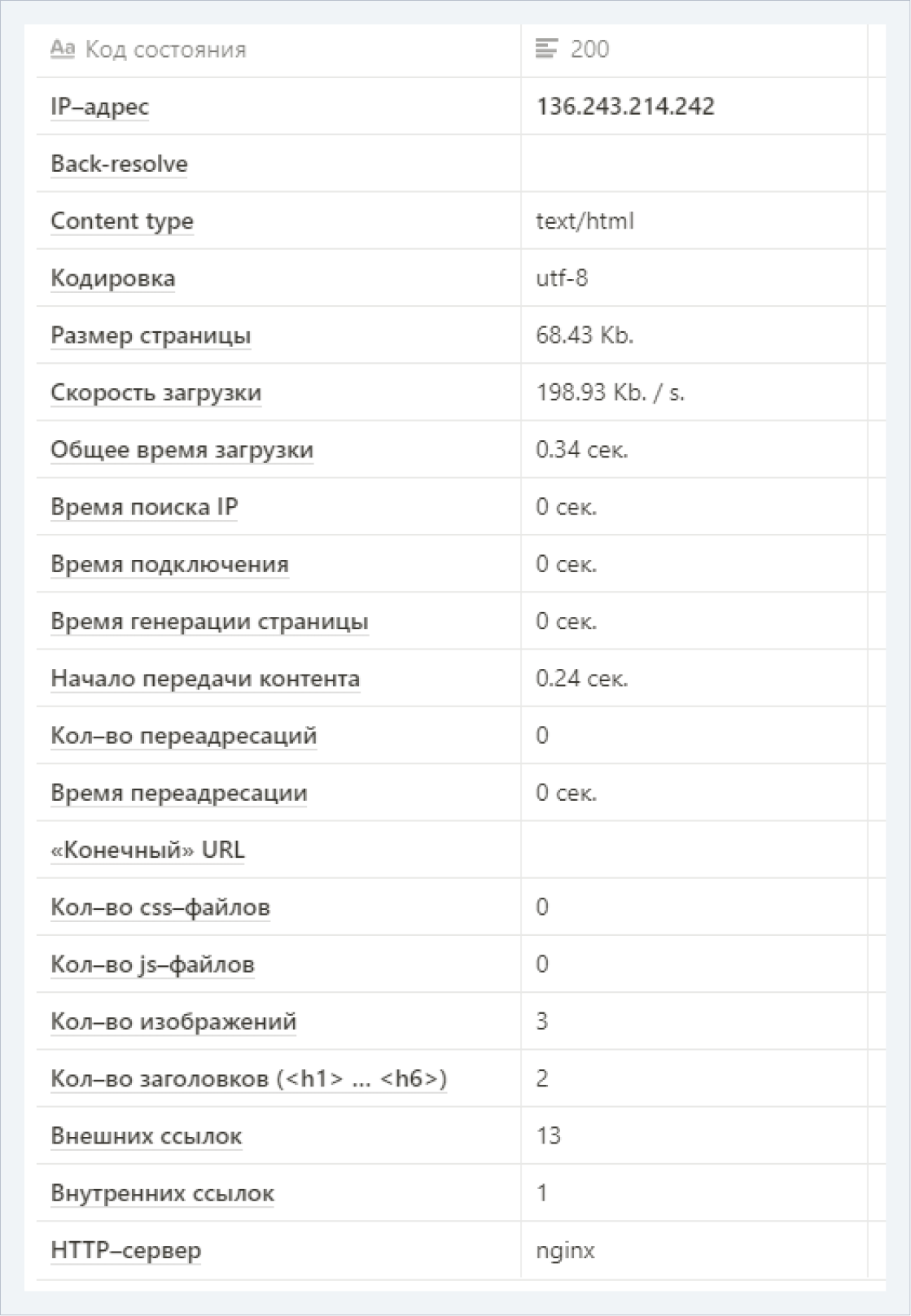
Additional information
Internet resources similar to the intruder’s site were detected:
→ IO-LL.RU *(registered on 09/12/2021)
*→ METALKMSK.RU *(01/10/2022)
*→ IO-CC.RU *(01/19/2022)
*→ METANMSK.RU *(01/24/2022)
*→ IO-RR.RU (02/10/2022)
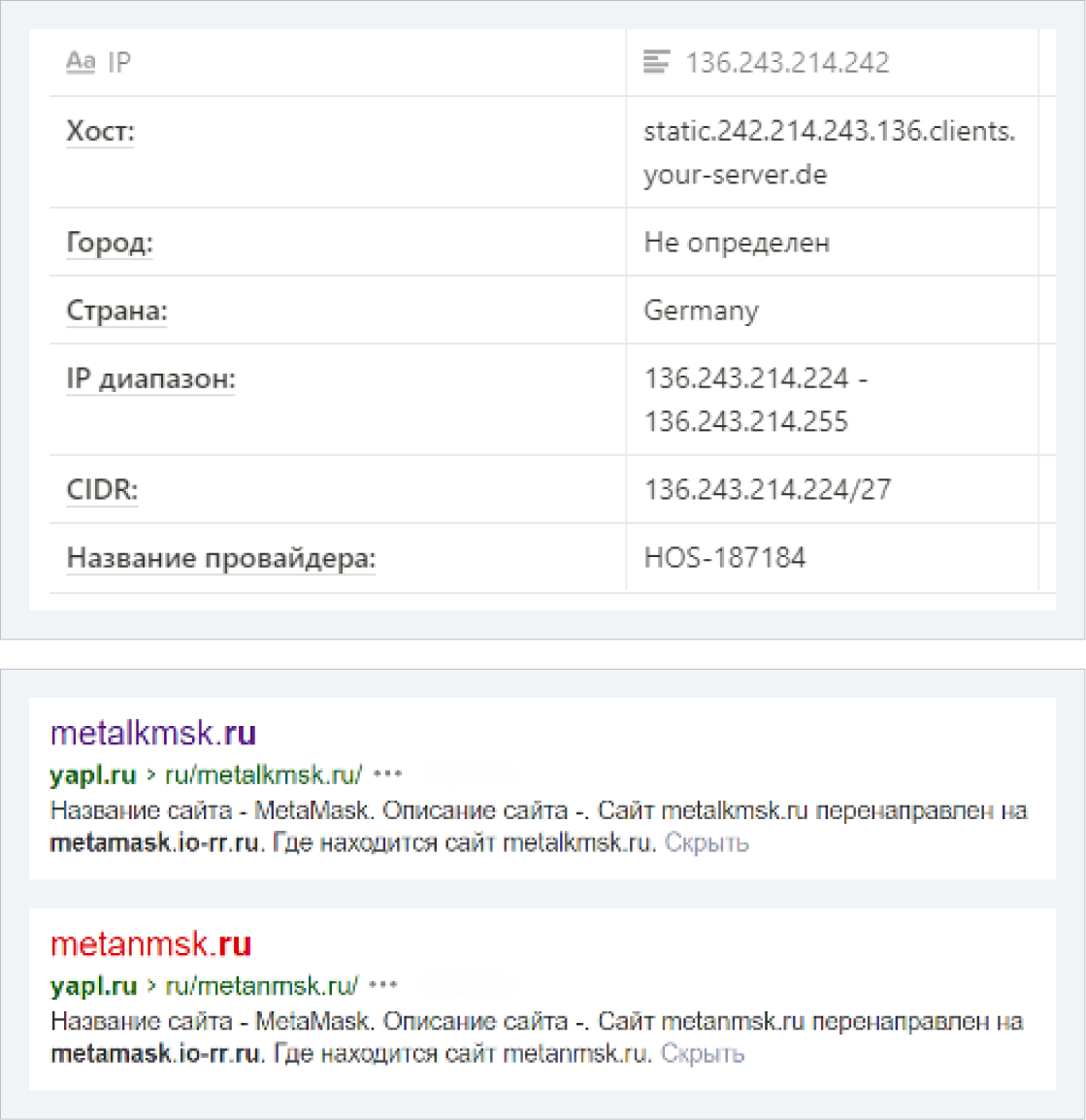
All the domains mentioned are linked to Reg.ru and are full copies of the official Metamask wallet website. Some of the resources are also listed on Github as phishing.
Possible further actions
Sending similar requests for domains IO-LL.RU, METALKMSK.RU, IO-CC.RU, METANMSK.RU, IO-RR.RU as for io-ss.ru.
STAGE 3 — BLOCKCHAIN INVESTIGATION
Investigated address: 0xbfe… on the FTM Fantom network. Funds are stolen on the FTM network, so we go to the Fantom explorer (blockchain browser) and look for transactions on it.
Stealing
On the evening of March 24, between 7:24 p.m. and 7:25 p.m., the intruder withdrew the following funds from the victim’s address to 0xbfe…:
-
971,662 YOSHI / equivalent of 1.4 million USD
-
260,310 1ART / equivalent of 26 thousand USD
-
3,632 FTM / equivalent of 5,266 USD
We see the movement of ERC-20 (Ethereum token protocol) YOSHI and 1ART tokens, FTM tokens in the BSCSCAN.COM browser.
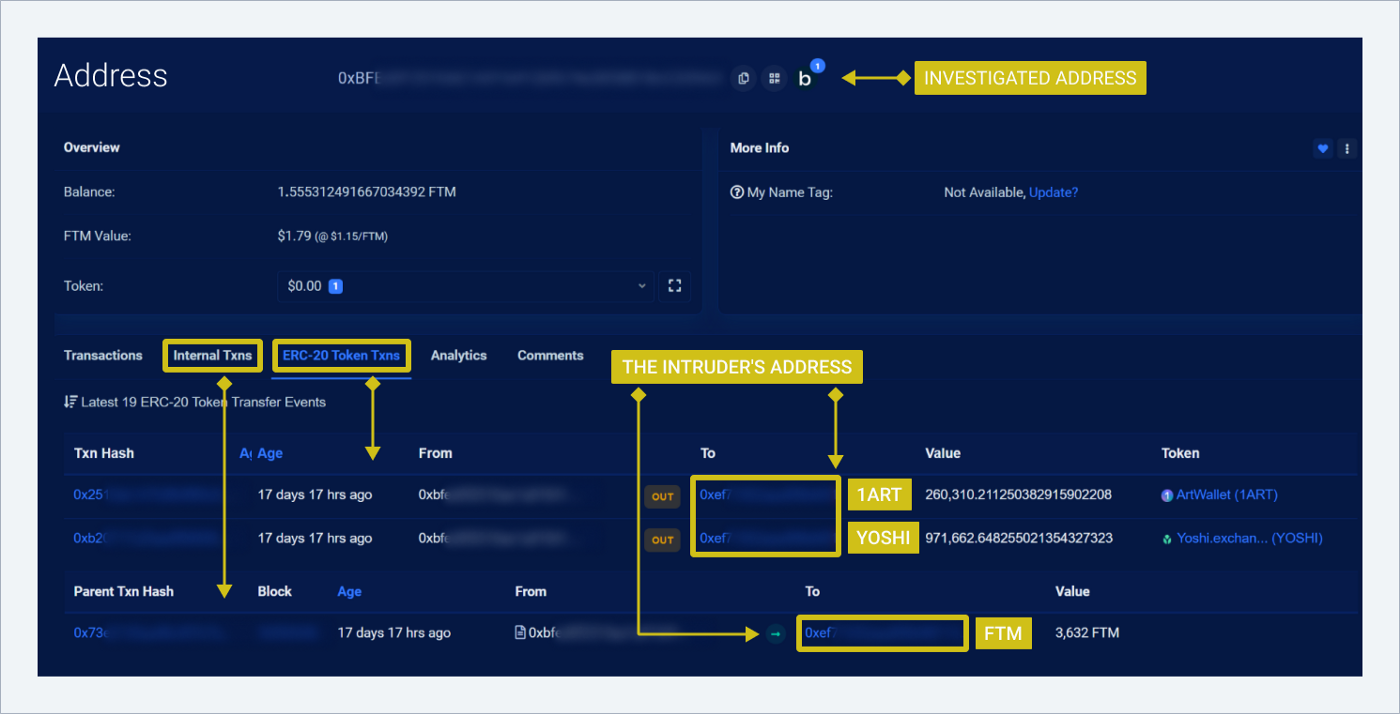
Next, we find out what the intruder did with the tokens:
→ Go to the intruder’s address in the browser
→ Watch earlier transactions and look for ones that came from the victim’s address, which means that the subsequent transactions are withdrawals of stolen funds
→ We see the exchange of YOSHI and 1ART tokens for anyFTM token in subsequent transactions
Smart contract for YOSHI exchange: 0x51d…f653e
Smart contract for 1ART exchange: 0x671…ca8df
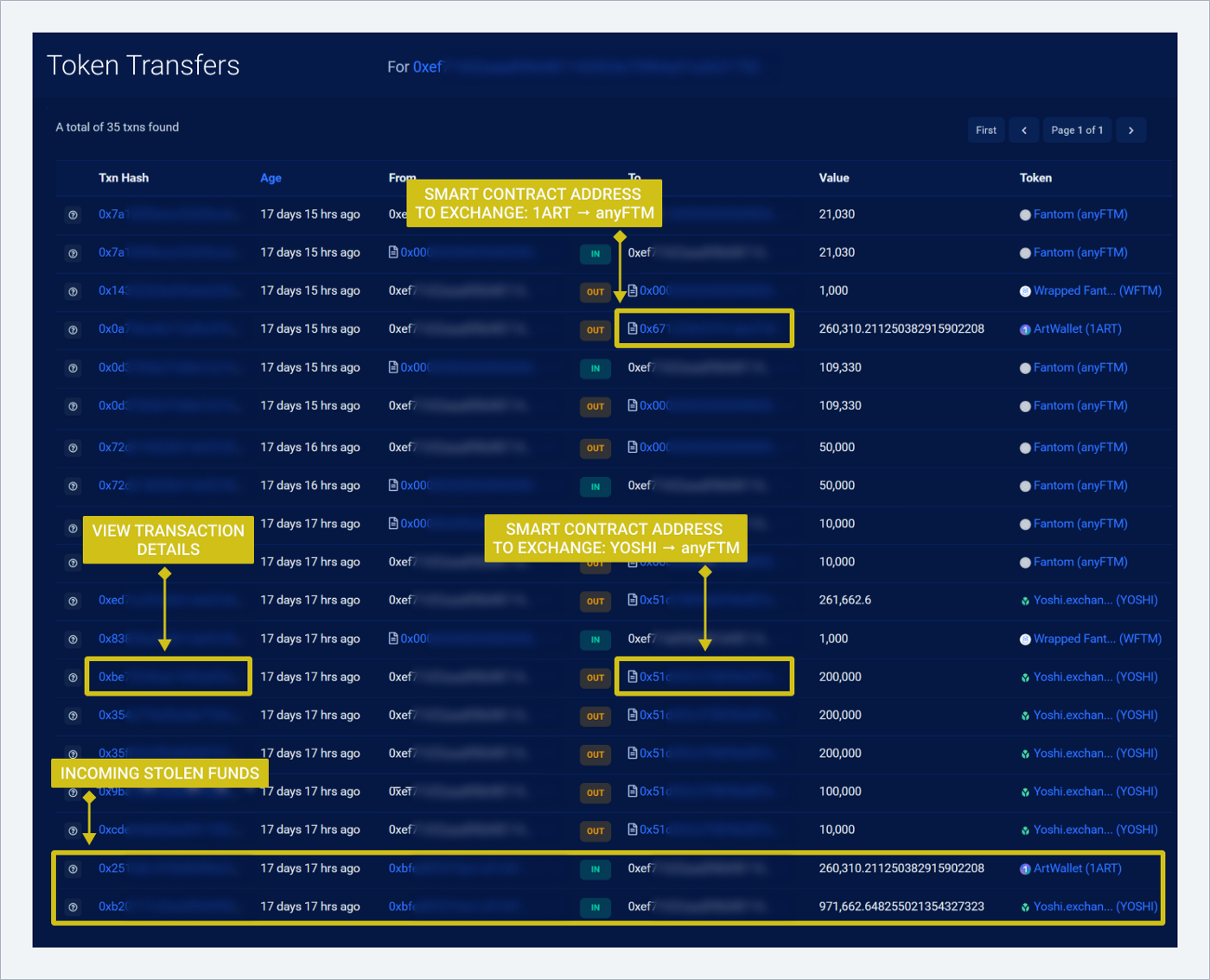
We see that YOSHI was exchanged for FTM in the transaction details:
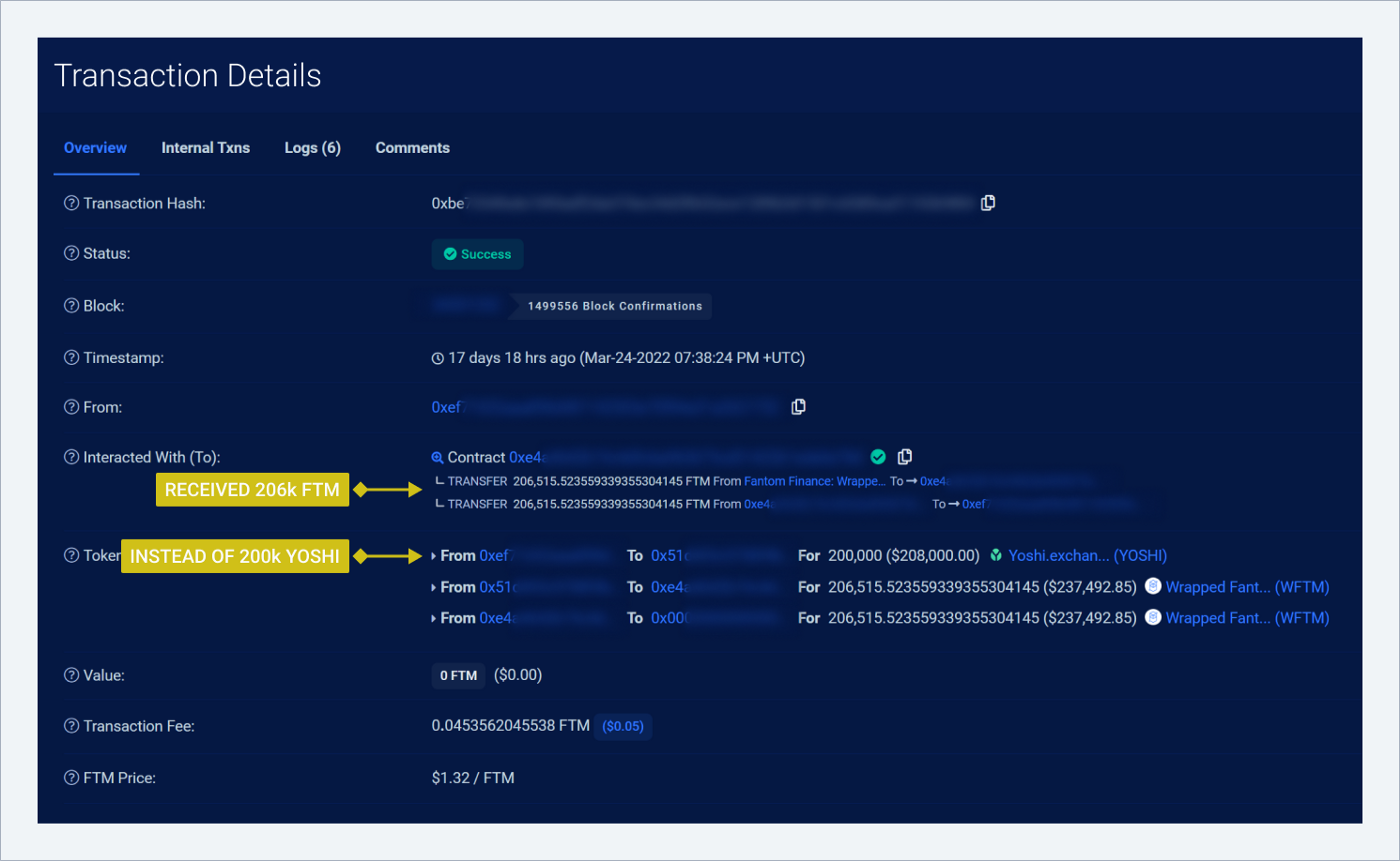
The corresponding transaction in the browser — we see a match both in the amount and in the ID:
Withdrawal of funds
Withdrawal of funds was made in several ways (calculations below in USD):
→ 1.18 million was sent to the ETH network to the same address of the intruder 0xef7…
→ 113k was converted to USDC via DEX in the FTM network
→ Sent to Binance:
• 101k to address 0xf32… (70k FTM)
• 20k to address 0x89b… (14k FTM)
• 87k to address 0xd04… (60k FTM)
Binance Exchange was determined by the fact that the funds was transferred to the address 0xbb3… from these three addresses. So, from this address, outgoing transactions are carried out only to one address — 0x28C…, signed on the Etherscan explorer as “Binance 14”.
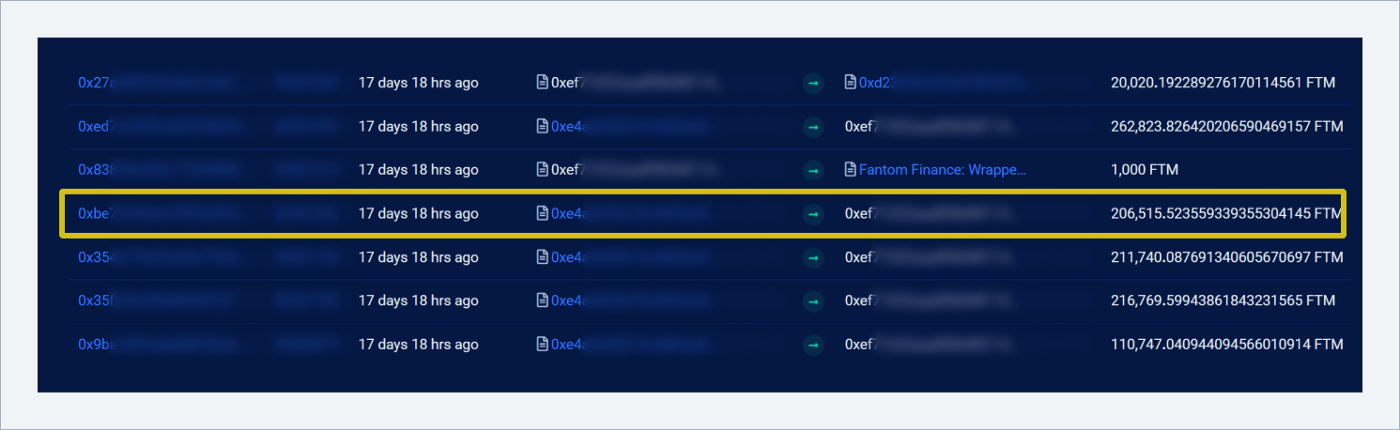
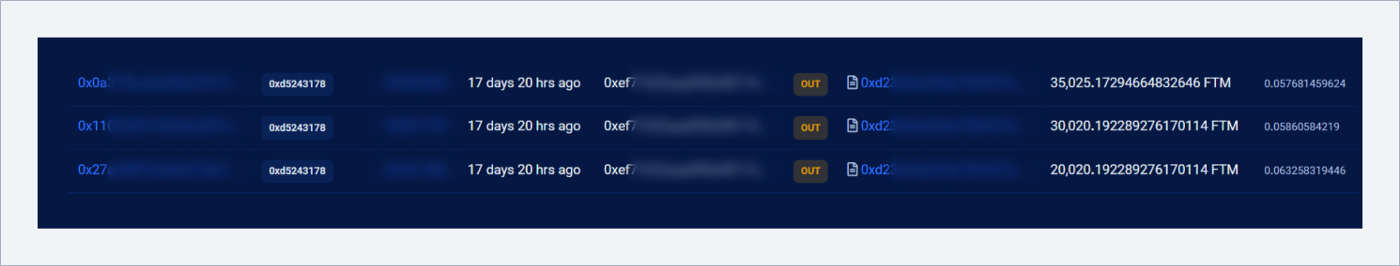
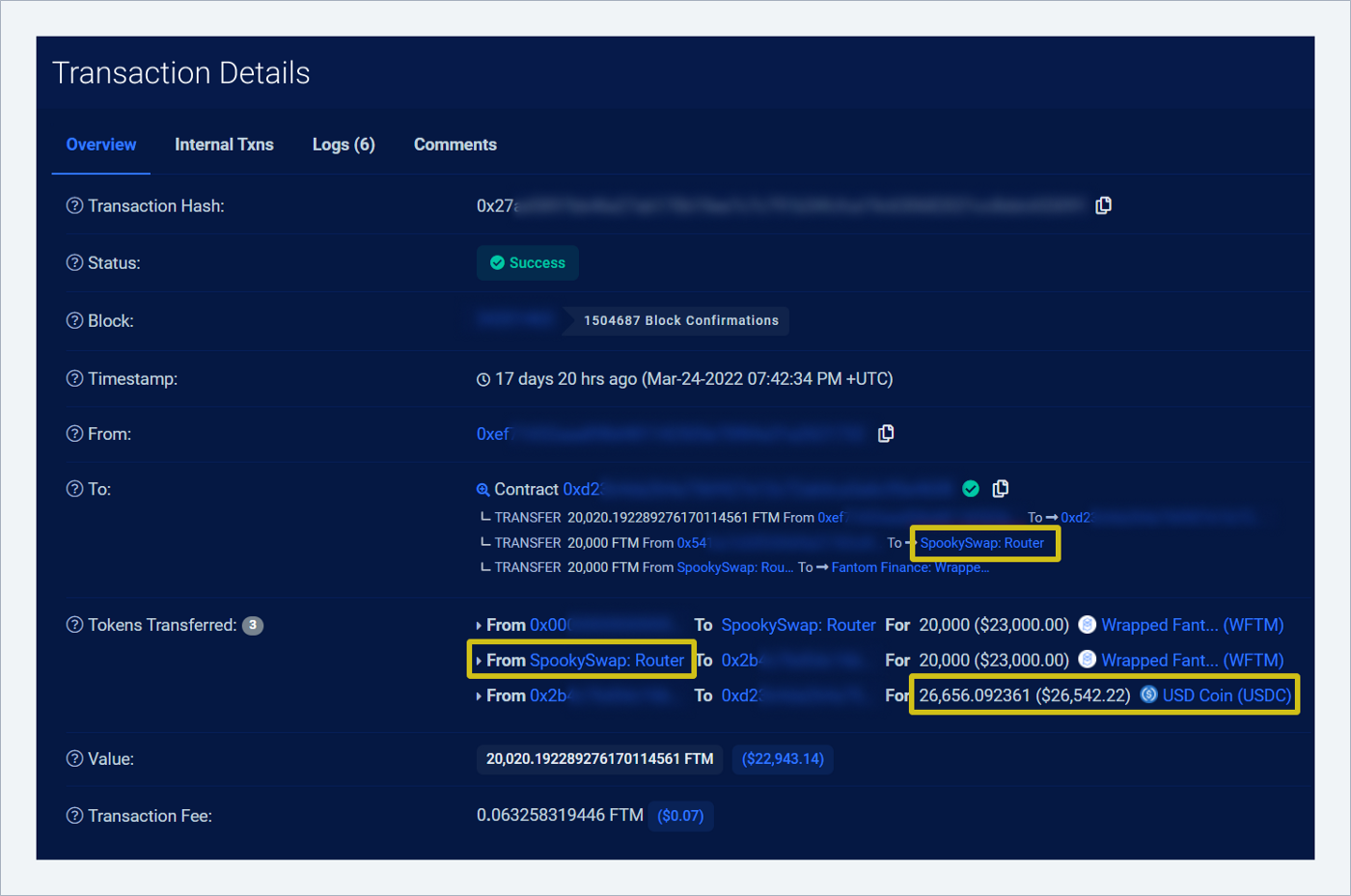
Three transactions of exchanging 85k FTM for 113k USDC via DEX SpookySwap:
Why through SpookySwap? Because we see the SpookySwap contract and the amount in USDC, when we open a transaction:
The principal of the funds is sent to the ETH network via AnySwap (Multichain):
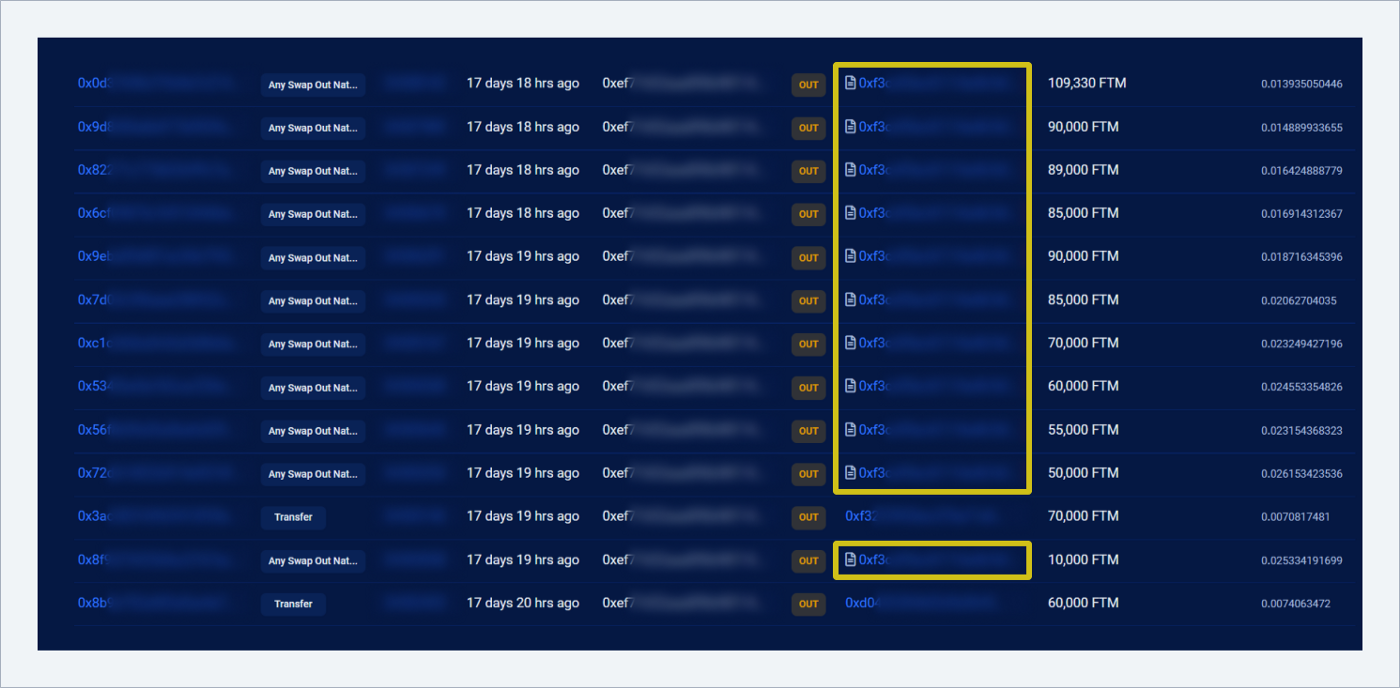
Corresponding transactions in the ETH network at the same address are:
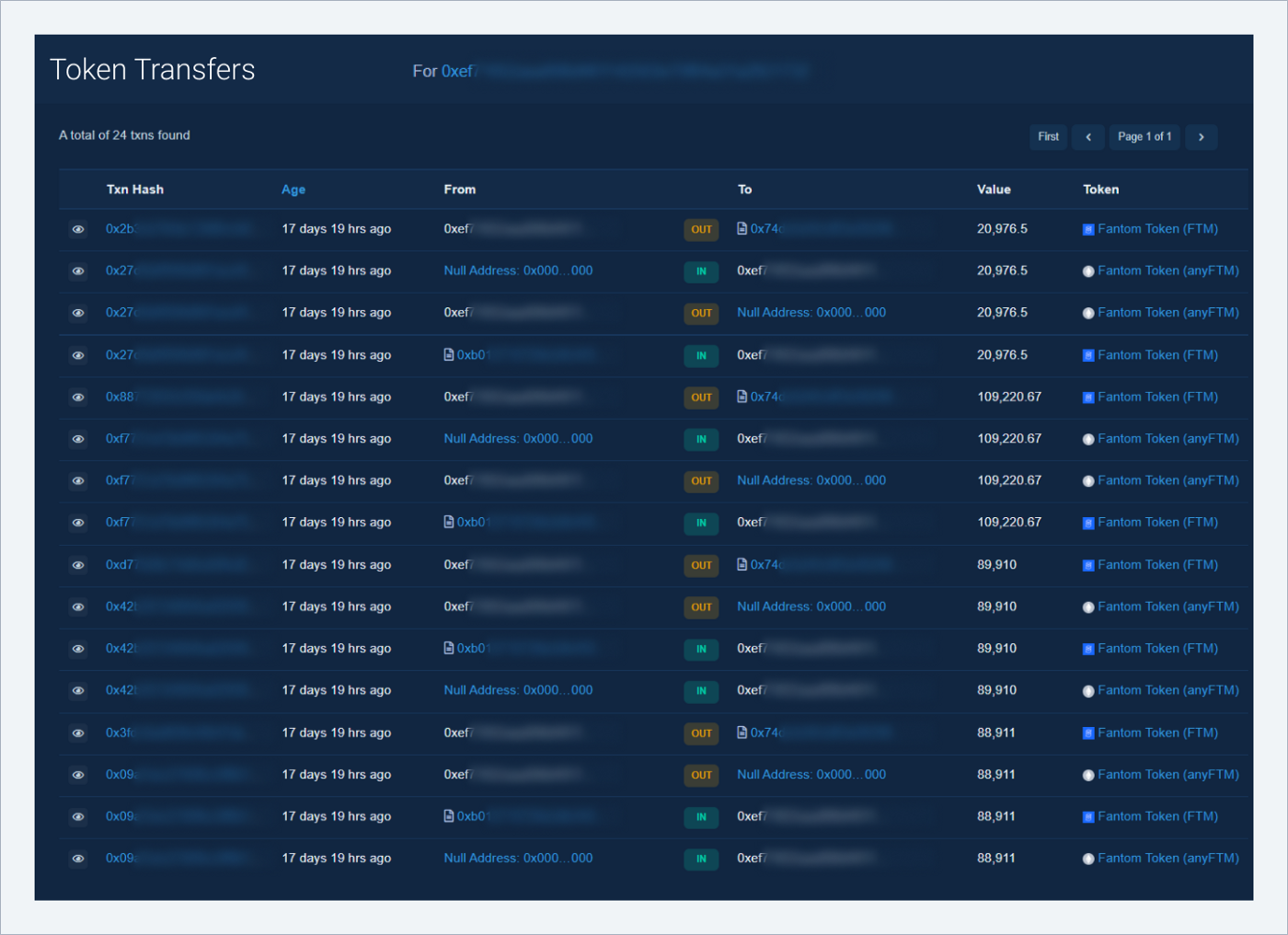
More visual here:
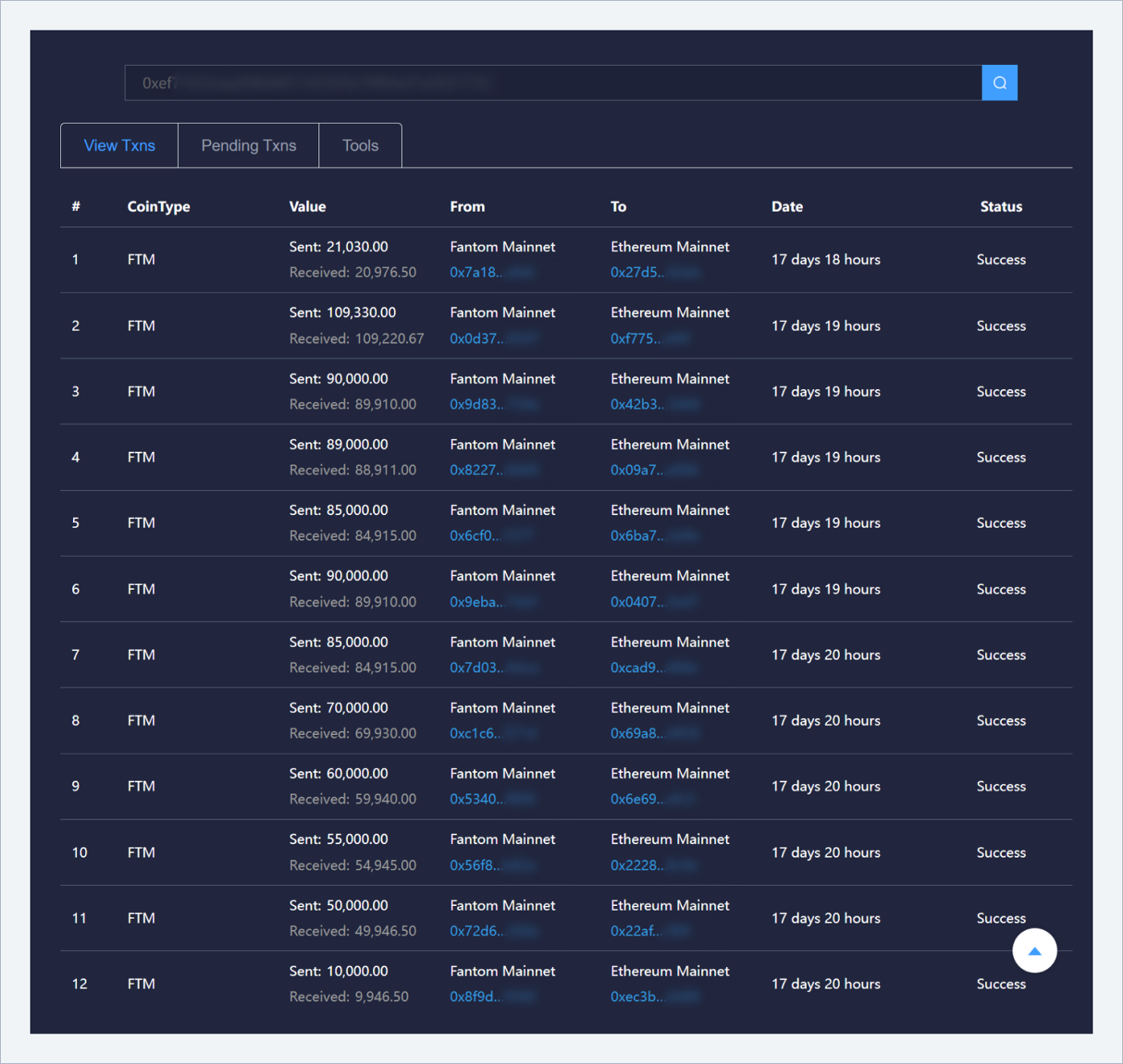
ETH
In the ETH network, funds were sent to address 0x077…, which has many complaints about the transfer of stolen funds. It’s probably the anonymous changenow.io exchanger, a guess based on the same comments on Etherscan.
Also from the intruder’s address, the funds are sent to 0xca6…, which sends them also to 0xbb3… mentioned above. (Binance). This address also has comments about the stolen funds. Transactions on it are much less frequent than on 0x077….
Interaction with 0x077… and 0xca6… occurs via transit addresses probably generated by the exchanger for replenishment.
Transaction Flowchart
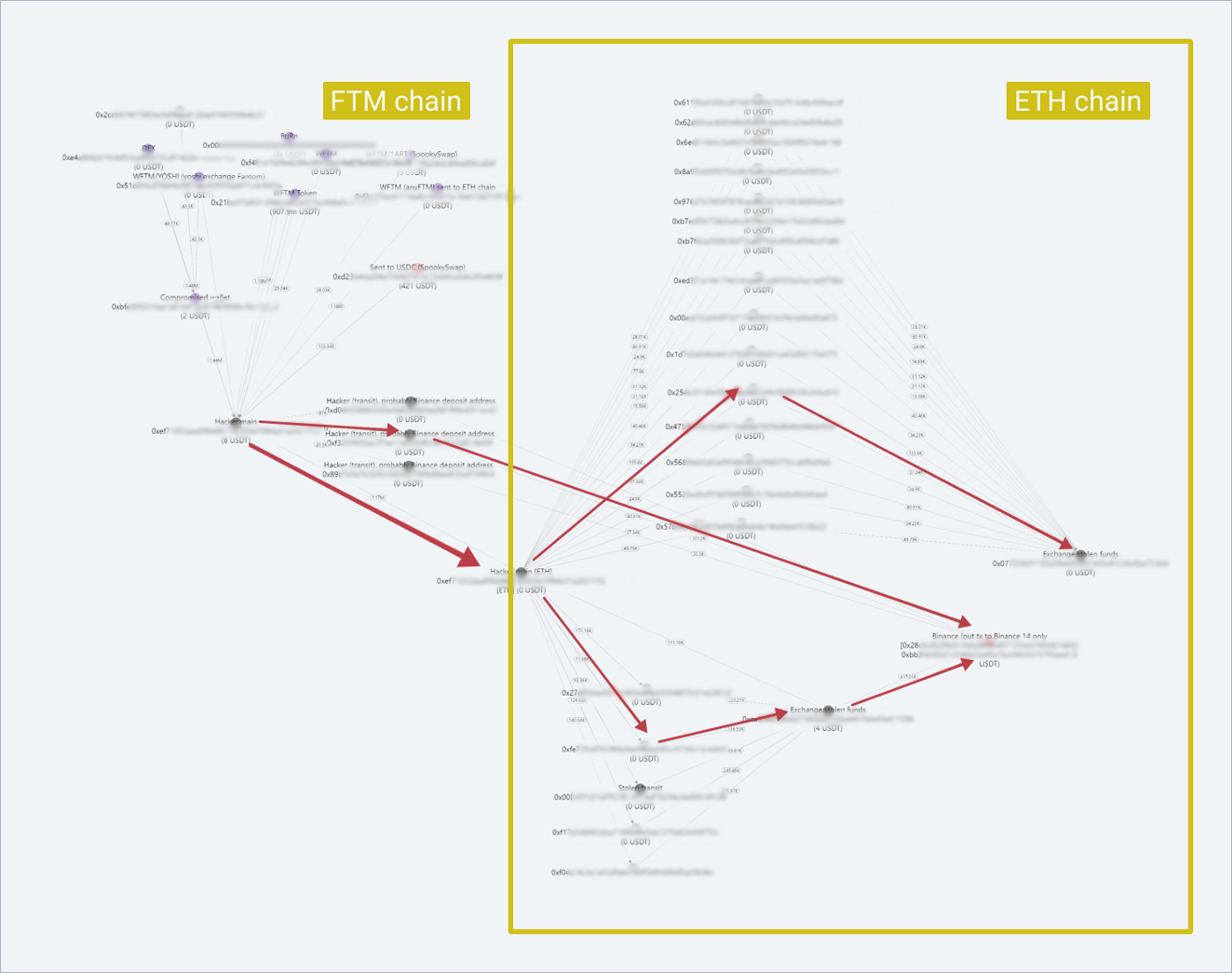
Possible further actions
Appealing to Binance on the fact of fraud.
STAGE 4 — RECOMMENDATIONS FOR FURTHER ACTIONS
Depending on the circumstances of the case, we recommend to contact the law enforcement agencies, depending on the location: the victim / exchanges to which the funds were withdrawn / the intruder (if his alleged location became known during our investigation) / in a place with a more well-regulated law. Each of the options has its own characteristics.
Once you receive the paperwork from law enforcement, we recommend that you send the Binance form with all the information.
This will allow identifying the Binance user whose account was used for misuse, and law enforcement agencies will have all the information they need to make the appropriate inquiries.
-
A detailed description of how and when the hack/theft occurred (this report)
-
References to all transactions involved (our report includes the necessary references)
-
A signed NDA or statement in which you agree to comply with Binance’s non-disclosure standards
-
A scan of the accepted law enforcement statement