We previously explored three new concepts - chain IPs, verifiable addressing and blockspace locality. Let’s go deeper and explore what kind of hypothetical world these two ideas can enable from a builder and user POV.
Merging Chain IPs with IPs
Domain name providers such as D3 and ENS own chain TLDs (e.g. .eth, .sol etc..) that map to chain IPs. A user entering a domain name into their browser gets routed to an account on the chain that hosts the code for a decentralized front end.
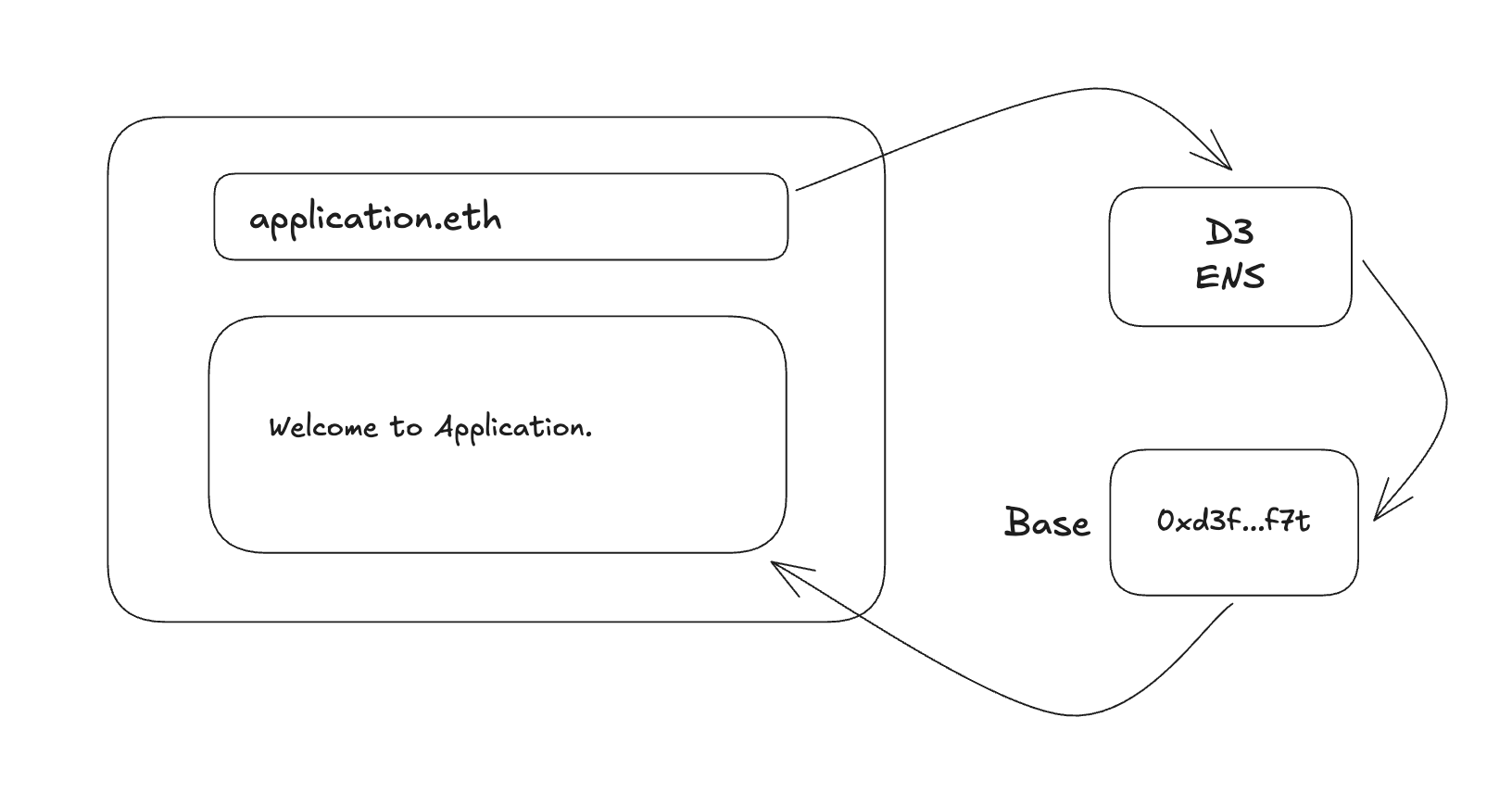
An application that sends a packet to a chain IP is able to communicate with a smart contract just as if it were communicating with an API server. An API server could write to a chain IP which maps to a rollup as a database server or some other infrastructure component.
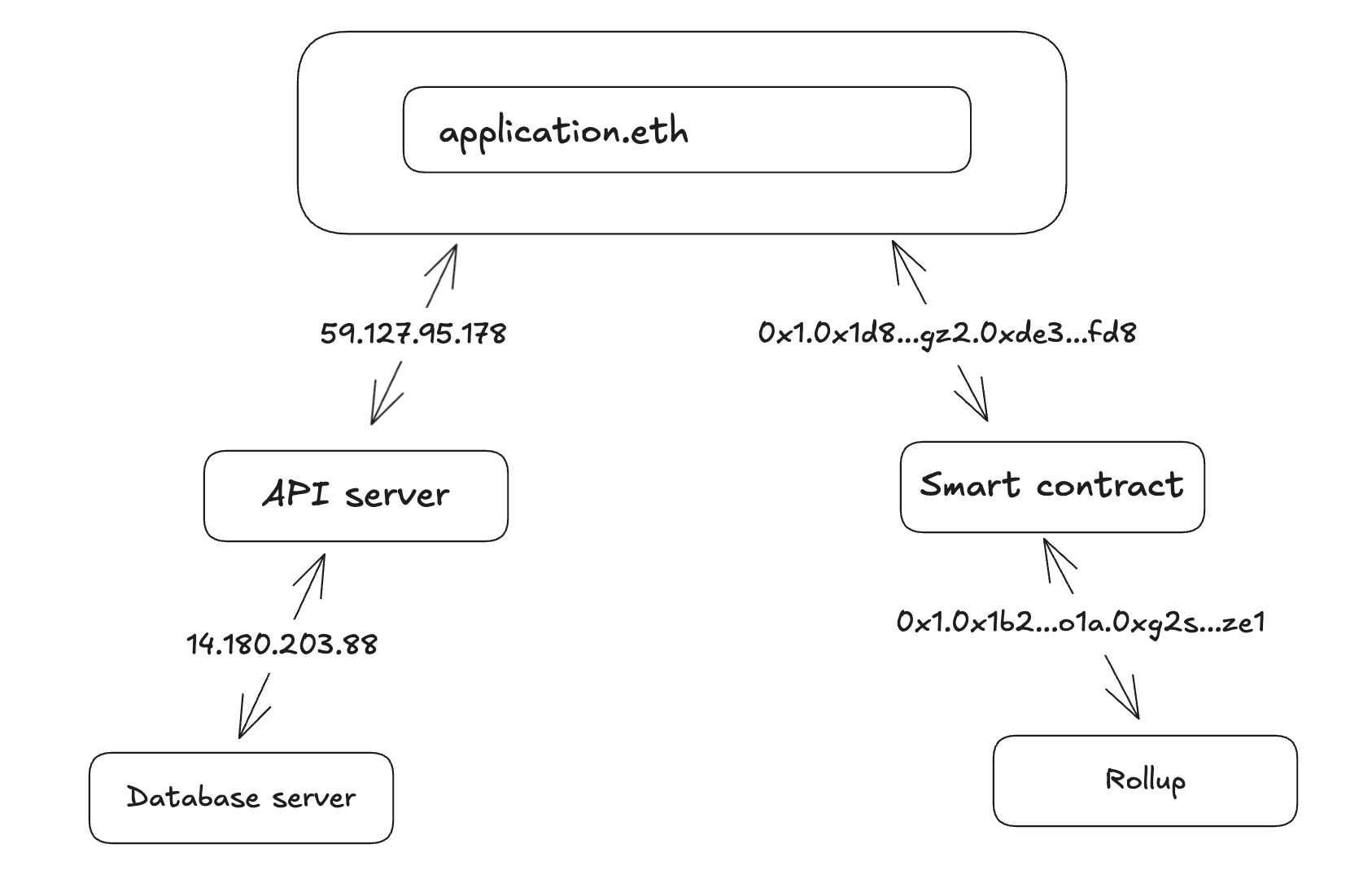
Co-existing Routing Infrastructure
Existing IP routing infrastructure does not need to be replaced. Chain IPs initially resolve to a rollup which can embed its own IP routing table. This means that each rollup retains sovereignty over its IP addressing.
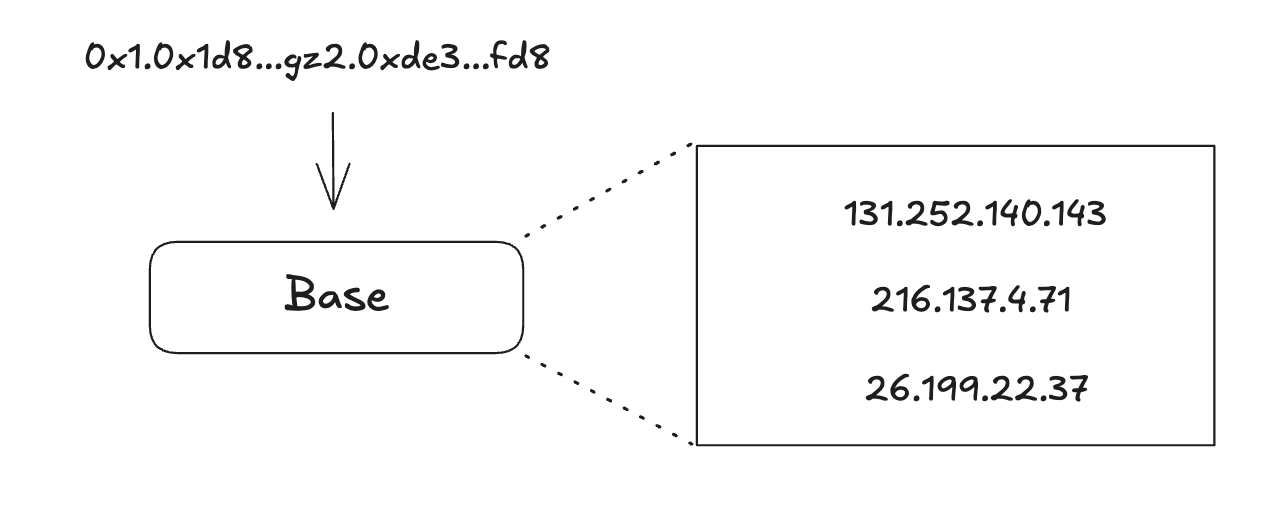
IP routing itself is unsafe as packets can be spoofed but chain IPs are verifiable. Both sender and destination and cryptographically linked via the L3 → L2 → L1 settlement. The entire hierarchical path can be proven. Chain IP routing overlayed on top of IP routing is akin to TLS where Ethereum acts as the core root of trust for the entire internet. In an alternate world, perhaps Ethereum could have provided trust within the context of TLS itself if it existed.
RaaS to SaaS
RaaS providers and cloud providers merge. Deploying a new server in the cloud results in a rollup being deployed at a specific locality level. Rollups for generic compute will be low latency and high throughput like MegaETH. Application builders can now deploy their application to multiple localities to best serve their end users.
To coordinate over these horizontally scalable apps, cloud providers run verifiable infrastructure services that handle application level sharding and coordination. These infrastructure primitives are either rollups themselves or EigenLayer AVS like constructs.
Securing the New Internet
The high value portion of this internet will be fully verified with zero knowledge proofs. This will naturally happen for much of the financial layer where the fees from value transacted greatly exceeds the cost of proving.
The rest of the internet will be secured by optimistic systems. To improve the efficiency of securing such a system at immense scale, execution sampling techniques are applied at scale.
The verifiable internet spawns open marketplaces that power a new generation of applications that live independent of nations. Everything is now both on and off chain simultaneously - the Uber, Amazon and Facebooks of tomorrow.
