Ready to build on Arweave? Get funded right now.
Find out more:
What is iExec?
Founded in 2016 by Gilles Fedak and Haiwu He in Lyon, France, iExec is an open-source decentralized cloud computing platform built on Ethereum. Initially positioned as an alternative to cloud providers like AWS and Azure, the iExec team has since updated its roadmap to focus on developer tools that make confidential computing simple.
Backed by strategic partnerships with Intel, Aethir, and AR.IO, iExec is part of a growing ecosystem focused on building infrastructure for secure, decentralized AI and DePIN applications.
This article explores how iExec enables confidential AI and DePIN through developer tools for privacy, and how Arweave provides the verifiable, permanent storage layer that supports the iExec ecosystem.
Protecting User Privacy in the AI Era
The rapid growth of AI has led to a data privacy crisis. Users routinely hand over sensitive information to centralized databases and AI systems with little visibility into how it’s processed or monetized.
As Nathan Chiron, CRO at iExec, warns:
We are in the age of AI, where we are providing immense amounts of data to these models, with many of them being centralized. (Source: This Isn’t About Hiding, It’s About Owning, July 2024)
To address these concerns, iExec has developed privacy tools that leverage Intel SGX and TDX hardware alongside blockchain governance. These tools provide builders with access to confidential computing for AI and DePIN applications across the iExec ecosystem.
Technical Overview: Confidential Computing
In the iExec network, confidential computing tasks are executed by a decentralized set of worker nodes running Intel CPUs with SGX or TDX hardware extensions. These extensions enable secure enclaves within the CPU, known as Trusted Execution Environments (TEEs), that protect data during computation from unauthorized access.
After executing a task, each worker node submits a cryptographic attestation to the iExec network to prove that the task was performed on authorized hardware.
iExec Confidential Computing Workflow
-
Submit Task: Users select a TEE-compatible application and submit a job through the iExec marketplace.
-
Assign Worker: The task is matched to a certified worker node equipped with an SGX- or TDX-supported CPU.
-
Initialize the Enclave: The worker launches a secure enclave and sends an attestation report to the Secret Management Service (SMS), which verifies the enclave’s integrity by checking its cryptographic hash.
-
Provision Secrets: Once verified, the SMS securely transmits encrypted inputs, such as API keys or model weights, into the enclave via a protected channel.
-
Execute Privately: The application runs entirely within the enclave, ensuring complete confidentiality of both code and data.
-
Generate and Validate Results: After execution, the enclave encrypts the output and generates a proof of execution containing metadata (task ID, execution hash, timestamps). This proof is submitted to the Bellecour blockchain for validation under iExec’s Proof-of-Contribution (PoCo) protocol.
-
Finalize and Reward: Once validated, the task is marked complete on-chain, the worker is rewarded in RLC tokens, and the user receives the encrypted result.
Web3Telegram
iExec makes integrating confidential computing straightforward. The network includes developer tools and ready-to-use code, making it ideal for confidential AI inference and data processing.
One example of an application built using iExec’s privacy tools is Web3Telegram, a messaging service developed by iExec. It enables users to send and receive encrypted messages via Telegram using only their Ethereum address, without exposing their Telegram ID. All chat IDs are encrypted within a Trusted Execution Environment (TEE), and users can grant or revoke access at any time.
How Web3Telegram Works
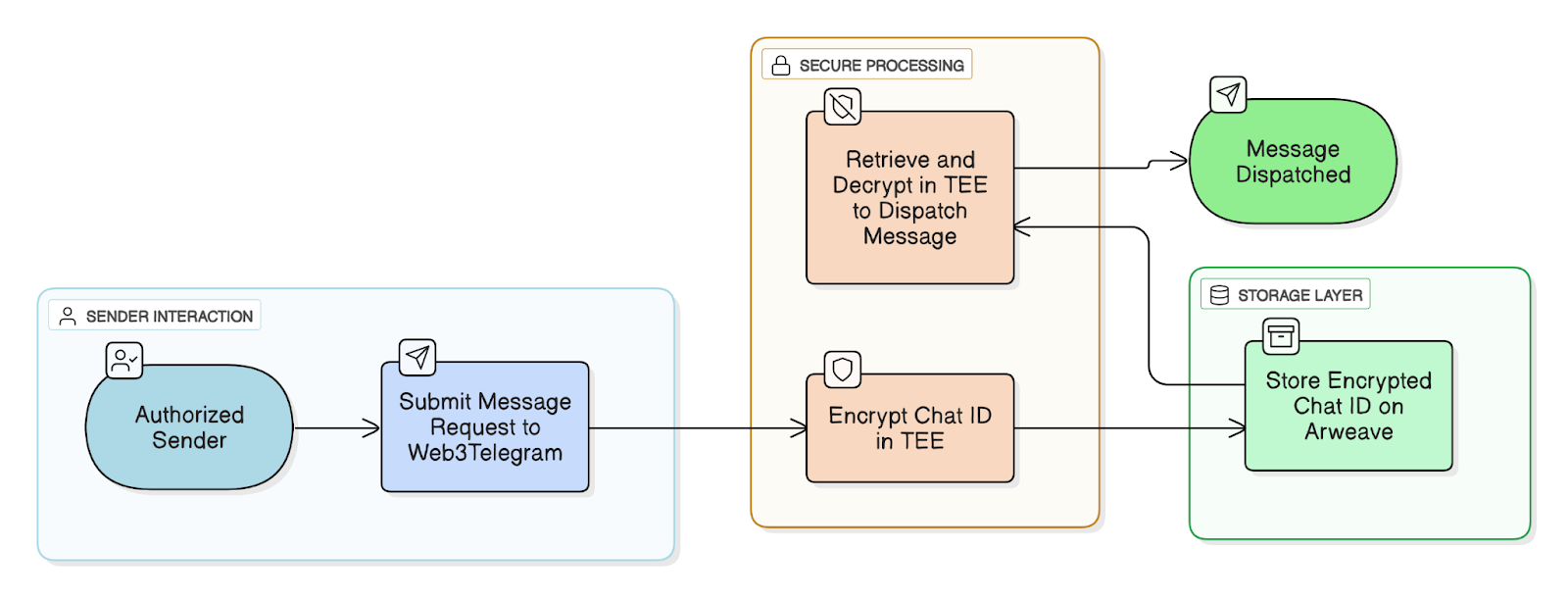
-
An authorized sender submits a message request to Web3Telegram.
-
Inside a Trusted Execution Environment (TEE), the system creates and uses an encrypted version of the user's Telegram chat ID.
-
This encrypted chat ID is stored on Arweave for future retrieval.
-
When a message needs to be sent, the encrypted chat ID is fetched from Arweave and decrypted inside the TEE to dispatch the message. The raw Telegram ID remains private and never leaves the TEE.
Arweave Partnership
To ensure permanent and verifiable access to encrypted data, iExec partnered with AR.IO to integrate Web3Telegram with Arweave’s decentralized storage layer. Through AR.IO’s gateway network, iExec publishes encrypted metadata—such as transaction IDs, timestamps, signatures, and custom tags—to the Permaweb, ensuring tamper-proof and persistent availability.
Integration Benefits
This integration enhances Web3Telegram by enabling:
-
Permanent, censorship-resistant storage of encrypted outputs from confidential tasks.
-
Decentralized publishing and retrieval of metadata, increasing transparency and removing central points of failure.
-
Seamless interoperability between iExec and the Arweave ecosystem, making it easy for confidential applications to manage persistent, auditable data.
This collaboration also opens the door for future integrations, where Arweave’s Permaweb could provide permanent, verifiable storage for other confidential computing applications in iExec’s ecosystem.
Other Strategic Partnerships and Collaborations
In addition to its partnership with AR.IO, iExec is scaling its confidential computing ecosystem through collaborations focused on enterprise adoption and real-world applications.
-
Intel Partner Alliance: iExec became a Gold Member in July 2025, marking a milestone in a multi-year collaboration with Intel focused on combining Intel SGX with blockchain. Their work includes co-authoring the EEA’s Off-Chain Trusted Compute Specification and developing secure AI model monetization. See iExec’s article for more details.
-
Aethir Collaboration: iExec partnered with Aethir to power Confidential AI using Aethir’s decentralized NVIDIA H100 GPU infrastructure. The integration enables scalable, privacy-preserving AI workloads by combining iExec’s TEE architecture with Aethir’s globally distributed GPU compute. See Aethir’s blog post for more details.
-
DeCC Alliance: iExec is a founding member of the DeCC Alliance, helping lead efforts to promote TEE-based privacy in Web3 through events, education, and ecosystem coordination. See iExec’s article for more details.
-
NVIDIA Inception Program: Through the NVIDIA Inception Program, iExec gained access to advanced GPU technology to support confidential AI. The team is integrating NVIDIA H100 GPUs to power complex AI workloads alongside Intel TDX. See iExec’s article for more details.
Future Outlook
As AI advances and the demand for privacy grows, iExec is uniquely positioned at the intersection of secure offchain computing and decentralized blockchain verifiability. With its privacy tools powering GPU-enabled confidential AI and a growing network of tools and partners, iExec is building the trust layer for DePIN and AI.
In 2025, iExec will accelerate its efforts across developer support, AI agent tooling, and token utility, scaling infrastructure and adoption while making confidential computing accessible to both builders and end users.
Learn more in iExec’s Academy article on Decentralized Confidential Computing (DeCC), or follow @iEx_ec on X for the latest updates.
Start Building on Arweave, the Permanent Storage Layer for AI
Developers need a foundation that’s not only decentralized but also secure, private, and persistent. Whether you're building autonomous agents, AI protocols, or data-heavy apps, Arweave ensures your data stays verifiable and immutable forever.
Future‑proof your AI stack with Arweave:
About the author: Vitti is a Web3 writer who turns complex ideas into clear content.
Follow Vitti on X for insights into AI and Web3.