On April 23, 2022, according to Beosin EagleEye, the NFT project Akutar’s AkuAuction contract has locked 11,539 ETH (worth ~$34 million) permanently due to vulnerabilities in the smart contract itself. Beosin security team analyzed the incident and the findings are shown below.
Akutar Introduction
Akutar is an NFT project. The official website: https://aku.world/
Relevant Information
Contract with vulnerabilities:
0xf42c318dbfbaab0eee040279c6a2588fa01a961d
Vulnerability Analysis
There are two vulnerabilities in Akutar’s contract.
Vulnerability one:
- The first vulnerability is in processRefunds, where the designer performs a loop-refund based on refundProgress.
- However, the call function here is used to perform the refund operation and the result of the refund is used as the judgment condition of require.
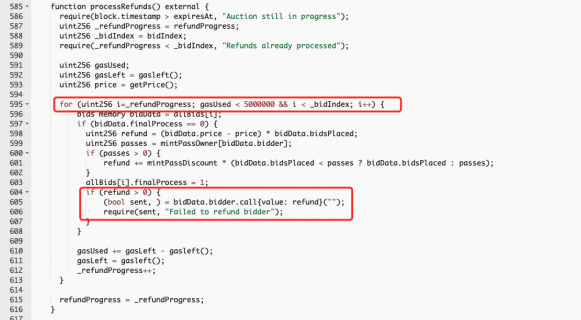
3. So if there is an attacker in the queue for refunds, and the call is invoked to refund the attacker, a malicious revert by the attacker in the fallback will cause the refund queue to get stuck with the attacker, thus preventing everyone behind the queue from getting a refund.
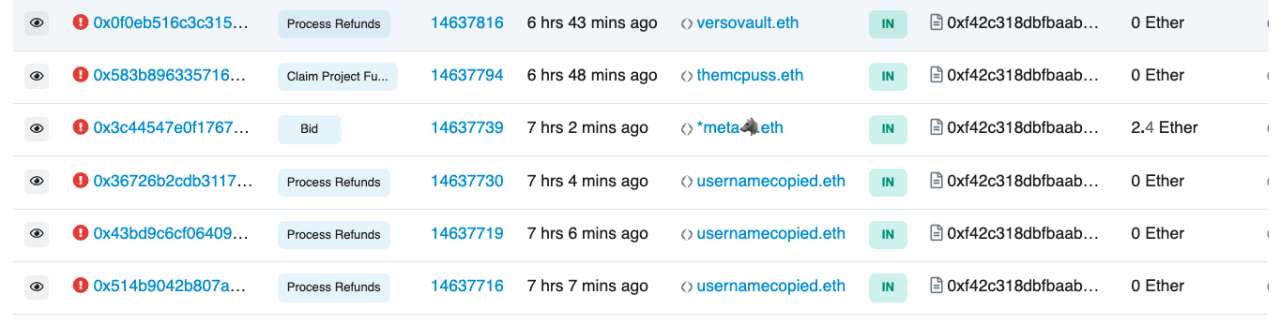
4. This vulnerability was proven valid on the chain, but then the attack contract was unlocked and no exploit was performed.
Vulnerability two:
This vulnerability is also the cause of ~$34 million assets being locked into the contract.
- The claimProjectFunds function is mainly used for withdrawals for the project owner. In order to avoid the high authority from the project owner to transfer all the assets in the contract before the user finishes withdrawing them, resulting in the user not being able to refund, all the refund operations should be completed before the project owner can withdraw. The business logic is designed to be fine. However, in the specific code implementation, the current code is vulnerable to vulnerability one, which causes the project party to be unable to withdraw, but this is only a potential risk, and the root cause of this lockup is not this one.
- Note the 620th line of code in the function: require (refundProgress > = totalBids) where refundProgress indicates how many users’ refunds have been processed, totalBids indicates the total number of NFTs bid by all users. Since a user can bid multiple NFTs, refundProgress may be smaller than totalBids when just comparing the values.
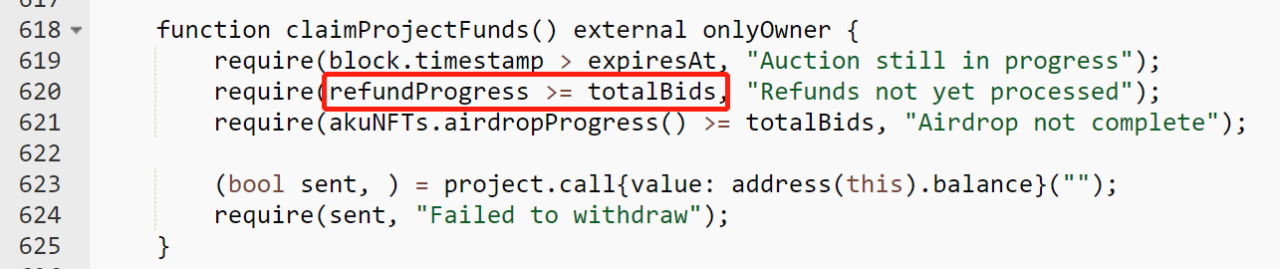
And again in the refund function processRefunds: require(_refundProgress < _bidIndex); bidIndex represents all users participating in the bid, and refundProgress will never be higher than bidIndex.
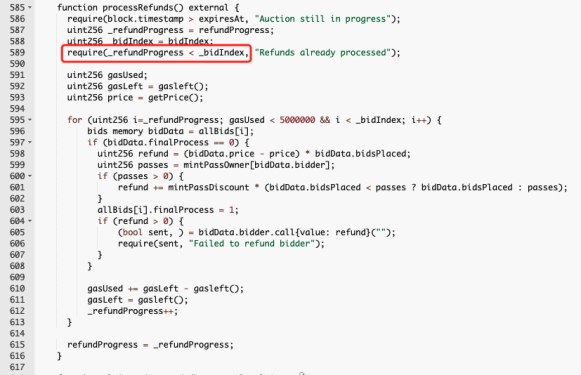
Here the value of bidIndex is 3669.
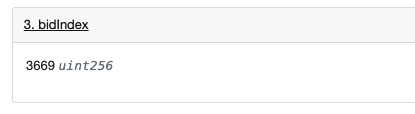
The value of totalBids is 5495.
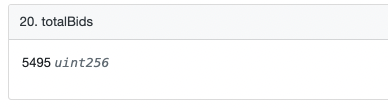
So the judgment condition that refundProgress>=5495 and refundProgress<669 will never be valid, and ultimately the project team will never be able to perform subsequent withdrawal operations. Here refundProgress should be compared with bidIndex, and the devs made a very low-level mistake. Ultimately, this resulted in the 11539 ETH (worth about $34 million) being locked from withdrawal.
Summary
In response to this incident, Beosin security team recommends:
-
Developers should have a basic awareness of security development and be familiar with the security issues that should be paid attention to in smart contract development.
-
Pay attention to the correctness of the code implementation when designing and implementing the contract.
-
Before the project goes live, it is highly recommended to choose a professional security audit company to conduct a comprehensive security audit to avoid security risks. In the case of Akutar, the incident can be completely avoided by auditing.
If you have need any blockchain security services, please contact us: