Ignorance is the parent of fear. — — Moby Dick
Photo by Mackenzie Marco on Unsplash
Suppose you are a whale who loves to trade vast amounts of assets via Uniswap, Curve, Dodo, and Balancer; you’d better take precautions from now on. Otherwise, you will fall prey to a sandwich front-running attacker lurking in the darkest corners of these trading venues and lynching uninformed whale traders. I.e., dubstepnerd.eth, the victim of this sandwich enabled by a $153.9M flash loan, the biggest one of November on Ethereum.
MEV Summary
When making the sandwich, utilizing a leveraged position, the MEV Bot collateralized part of its token and flash-loaned 127,006 WETH on AAVE. Then it borrowed DAI to swap USDC in a Curve LP, in which the price of the token pair was impacted. Next, it saved the USDC to MakerDAO, deposited the minted DAI to AAVE, burned part of the debt of DAI, and withdrew 127,006 WETH to pay back the flash loan.
Key Contracts, Roles, and Addresses
Attacker EOA(from address): 0xf480fAb87c07EC2dDd68A83eC0319BB466B1Afa2
MEV Bot: 0x0000000000590b74eb97457bf7b3ff6d63c6fde2
Borrower: 0x2a9152d882ba3fc4265d47447a7a00970f90a25e
The three addresses above can be seen as the same group belonging to the attacker.
Curve LP: 0xbebc44782c7db0a1a60cb6fe97d0b483032ff1c7
Balancer Vault: 0xba12222222228d8ba445958a75a0704d566bf2c8
MakerDAO PSM: 0x0a59649758aa4d66e25f08dd01271e891fe52199
AAVE’s aWETH contract: 0x030ba81f1c18d280636f32af80b9aad02cf0854e
**Uniswap USDC/WETH V2 Pool: **0xB4e16d0168e52d35CaCD2c6185b44281Ec28C9Dc
Frontrun of the Sandwich
Open this link to view the frontrun transaction with features like step-by-step, P/L, and CallTrace Tree.
The goal of this transaction: raise the price of USDC against 3CRV in the Curve Pool.
Here is the token flow chart of it.
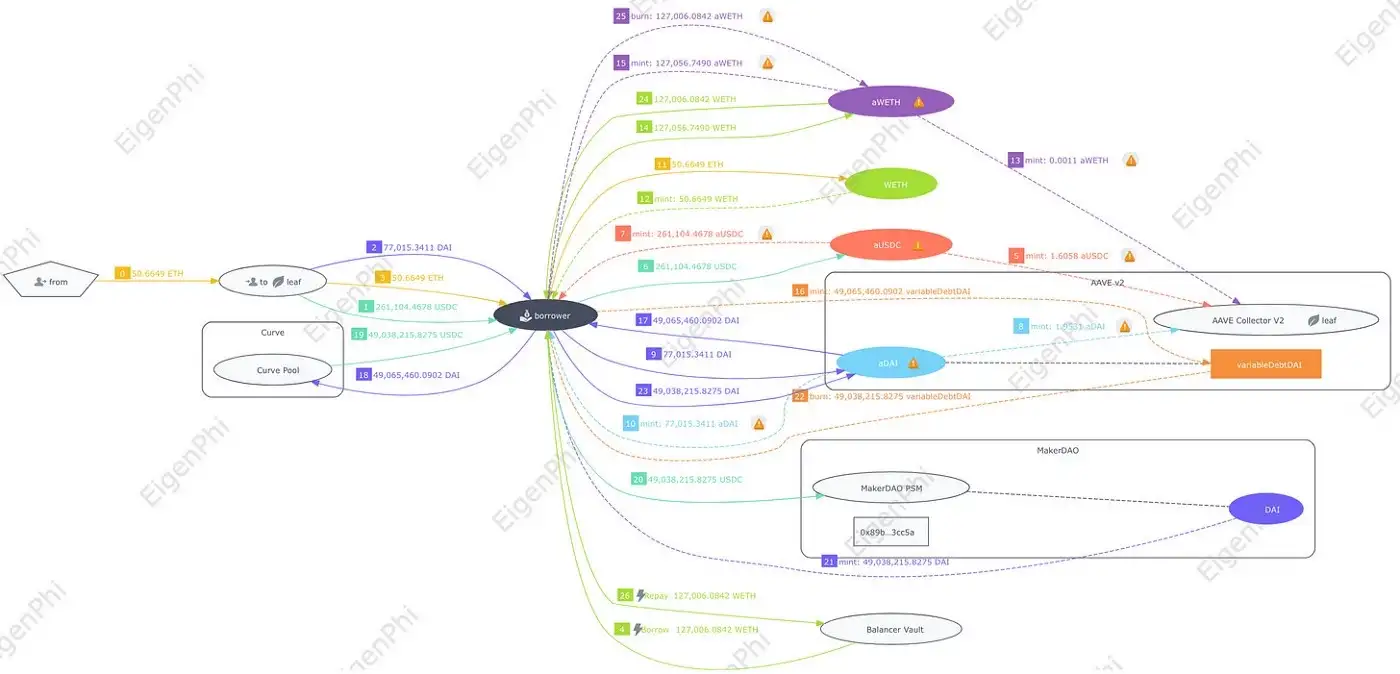
The detailed steps explanation:
Step 0–4: From address and MEV Bot transferred their own token: 50.6649 ETH, 77,015.34 DAI, 261,104.4678 USDC, and flash-loaned 127,006 WETH to borrower.
Step 5–14: the borrower address saved all the tokens to AAVE as collateral and acquired aToken provided by AAVE.
Step 15,16: the borrower borrowed 49,065,460 DAI from AAVE and received the corresponding debt token.
Step 17,18: the borrower swapped 49,065,460 DAI for 49,038,215 USDC in the Curve pool, finishing raising the USDC exchange price. This is the crucial step of the whole attack.
Step 19–22: the borrower saved the USDC to MakerDAO and received the same amount, 49,038,215, of DAI, then it paid back the DAI to AAVE to pay part of the debt generated from borrowing the DAI.
Step 23–25: the borrower took out most of the WETH collateral and paid back the 127,006 WETH flash loan.
The MEV Bot suffered a loss of 27,244 $DAI due to paying the debt of 49,065,460 DAI with 49,038,215 DAI.
Victim Transaction
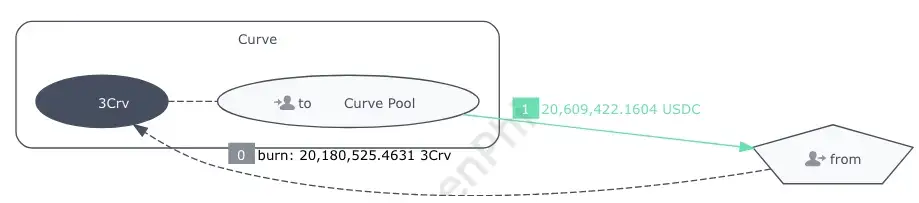
In this transaction, the victim’s EOA took out the liquidity by burning 3Crv for USDC.
Eventually, this whale lost 8.052563 ETH, computed by the revenue of the attacker.
Backrun of the Sandwich
In this transaction, using a flash loan, the MEV BOT borrowed WETH and put into AAVE as collateral to borrow USDC, then it swapped the USDC to CurveLP at a high price to complete the sandwich attack, getting a large amount of DAI. After repaying the debts and miners’ tips, the attacker finally raked profit.
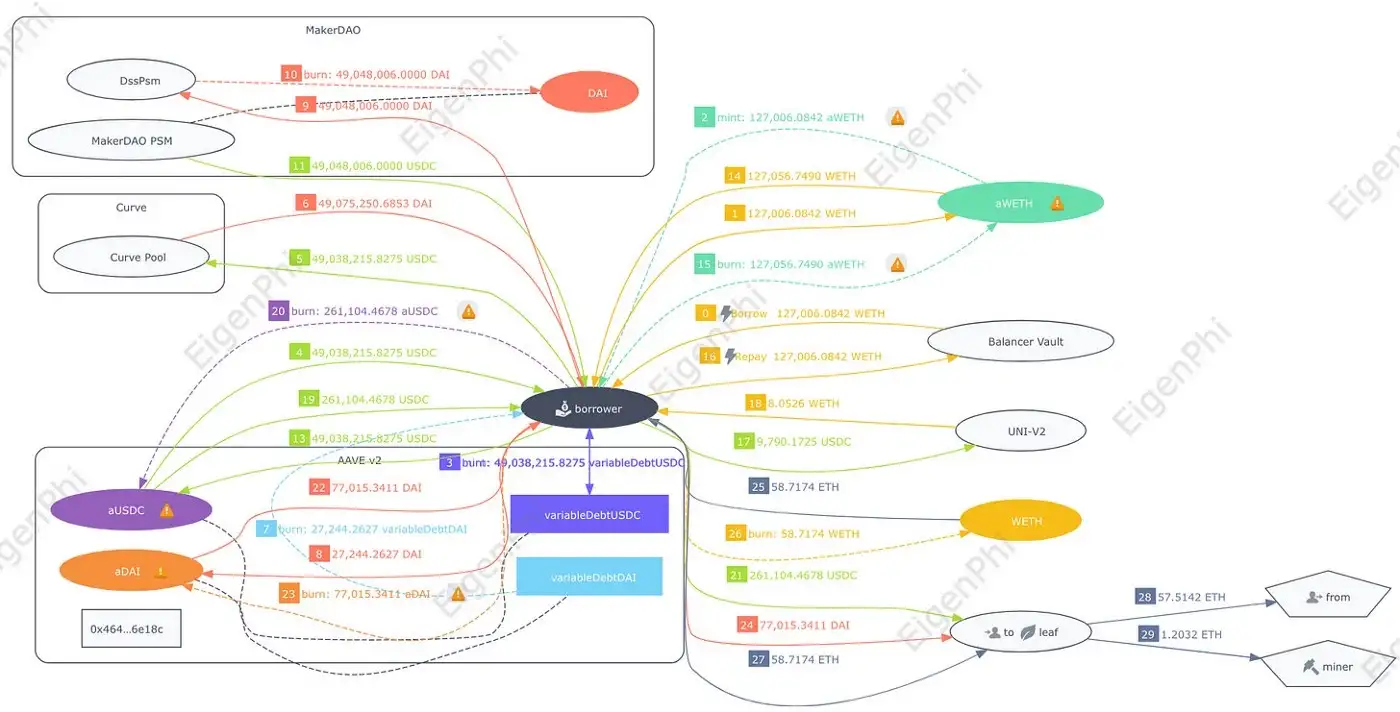
The detailed steps explanation:
Step 0,1,2: The borrower flash-loaned 127,006.0842 WETH from Balancer and saved to AAVE as collateral, receiving aWETH.
Step 3,4: The borrower borrowed 49,038,215.8275 USDC from AAVE and received the dept token.
Step 5,6: The borrower swapped the loaned 49,038,215.8275 USDC for 49,075,250.685 DAI in the Curve pool.
Step 7,8: The borrower returned the 27,244 $DAI debt to AAVE and burnt the debt DAI token from the front-running.
Step 9, 10, 11: The borrower returned the left 49,048,006 DAI to MakerDAO and withdrew 49,048,006 USDC.
Step 12, 13: The borrower paid back 49,038,215.8275 USDC to AAVE to eliminate the debt generated in Step 3 and 4. (In the figure, step 12 is overlapped with step 3.)
Step 14, 15: The borrower burned 127,056.749 aWETH, which is the total of the flash loan and its original position, and took out the WETH.
Step 16: The borrower returned the flash-loaned 127,006.0842 WETH.
Step 17, 18: The borrower swapped the left 9,790.1725 USDC for 8.0526 WETH in the Uniswap V2 pool.
Step 19–24: The borrower took out the collateralized 77,015.34 DAI and 261,104.4678 USDC from AAVE and transferred them back to the MEV Bot.
Step 25–27: The borrower exchanged the left 58.717445 WETH as ETH and transferred it back to the MEV Bot. At this moment, the MEV Bot has repaid all the debt of the front-running transaction and retrieved all the positions, eventually getting a revenue of 8.0525 ETH (58.7174–50.6649).
Step 28: The MEV Bot transferred 57.514216 ETH to the from address.
Step 29: The MEV Bot paid 1.203229 ETH as miner tips.
Profit and Loss Summary
In the end, the attacker profited 6.82 ETH, worth $8,267.
Asset Utilization Efficiency
Let’s do some calculations.
Attacker’s position: 50.6649 ETH($60,642), 77,015.34 DAI, 261,104.4678 USDC,$338,119 in total.
Flash loan: 127006.0842 WETH = $153,907,408.
Curve pool attacking fund: 49,065,460 DAI
Collateral on AAVE: $338,119 + $153,907,408 = $154,245,527
Left debt after the frontrun: 27,244 DAI
Debt to Position rate: 27,244/338,119 = 8%.
This attack’s asset utilization efficiency is not ideal. The fund attacking the Curve pool was 49M DAI, accounting for 31.8% of the collateral amount: $154.2M. The flash loan was paid back by using the withdrawn WETH. After the front-running transaction, the left debt only accounted for 8% of the collateralized assets. At the end of the day, the flash loan was used as a bridging loan, not leveraged position.
But this attack has largely reached the maximum of the MEV, which can be inducted from the calculations below.
The victim’s actual swap amount: 20,609,422.1640 USDC.
The min_amount parameter set by the victim: 20,609,403.453298 USDC.
The difference is 18.71 USDC. And the attacker’s two swaps on the Curve pool increased by 9,790.1725 USDC as a surplus.
The Attacker’s MO and Victim History
To manage attacks like this, the attacker is equipped with three skills:
-
Possessing a thorough comprehension of the Curve liquidity pool’s algorithms.
-
Monitoring the changes in the mempools of Ethereum to locate the large stablecoin transaction orders on Uniswap, Curve, Dodo, and Balancer.
-
Developing smart contracts that can rapidly compute the cost and benefit of sandwich attacking and implement the actual squeeze.
Wonder how much damage this attacker has done? We compile this year’s sandwich data till Oct 19 and make the table below.
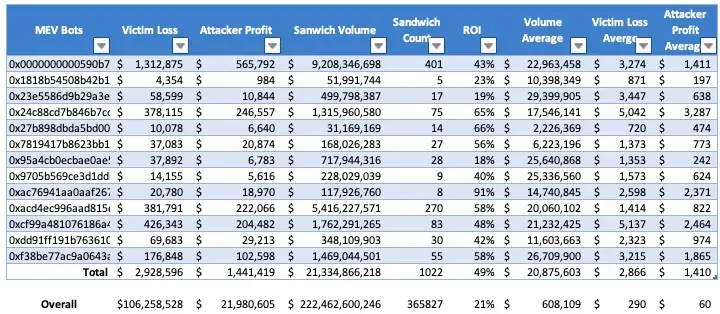
The last row of the table is the overall sandwich data during this period.
Here are some facts.
-
13 MEV Bots have been used by this attacker, and only this attacker to squeeze whales 1,022 times till Oct 19, causing a victim loss of $2.93M, raking $1.44M profit for the attacker.
-
The total ROI of the attacker, 49%, is much higher than the general ROI of sandwiches, 21%. And 6 out of 13 of the MEV Bots have an ROI of over 50%. So this attacker is really good at what it has been doing.
-
The average victim loss per sandwich by the attacker is $2,866, almost 10 times of the overall average loss: $290.
-
The average profit per sandwich by the attacker is $1,410, 23.5 times of the overall average profit: $60.
-
The average volume per sandwich is $20.1M, 33 times of the overall average volume: $608K. This is a clear indicator that the sandwiches done by this attacker have been targeting whales and their hefty swaps. Please be noted that a flash loan’s amount is not counted as the transaction’s volume.
-
The earliest attack can be traced back to May 30 of this year.
We can also check the data from the victim’s side.
We have gathered a spreadsheet of the victims suffering sandwich attacks from the attacker 0xf48. Here are some facts. The data’s deadline here is Oct 19.
-
In total, there are 744 victims losing $2.93M to the attacker on 1022.
-
8 victims have been clasped 6 or more times by the attacker.
-
The victim who suffered the most, 22 times and a loss of over $170K, is a Uniswap V3 liquidity provider.
-
58 victims have been deprived of more than $10K by the attacker and its MEV Bots.
You may want to find out how many of these 1,022 sandwiches involve flash loans. It’s a pretty big topic, and we will present you the results once finishing crunching the numbers.
Conclusion
It’s no doubt that the attacker 0xf48 has been taking to cooking sandwiches like a duck to water in these pools, in which, however, this duck poses severe threats to the whales doing trading. **We strongly advise whale trades to take special precautions while trading large amounts of assets by harnessing ****Flash Bots Protect RPC point **or CoW Swap. Just don’t go out there swimming naked.
Although the attacker has been using flash loans as aid, luckily, it does not utilize these loans’ full potential, at least not in the transaction this post analyzed employing a $153.9M flash loan.
The posts below demonstrate how searchers use flash loans for arbitrages.
Follow us via these to dig more hidden wisdom of DeFi:
