1. What is a Proxy
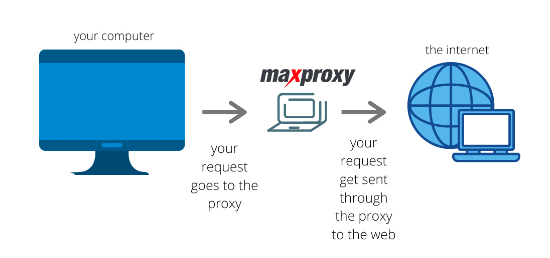
Proxy is a network proxy technology that can establish a virtual connection between the client and the target network. By using a proxy, a client can access resources on other networks when in fact, the client does so through a proxy server. The proxy server intercepts the client's request and sends the request to the target network. After receiving the response from the target network, the proxy server returns the result to the client.
The advantage of using proxy technology is that it can improve the access speed and security of the client. The proxy server can cache the content of the visited web pages so that it can respond quickly when the client sees it the next time. Client requests can also be reviewed and filtered to prevent clients from accessing unsafe or illegal content.
Some standard proxy software can be built on the server, such as squid, TinyProxy, socks5, etc., to provide proxy services. Users can use a proxy to access the network by setting the IP address and port number of the proxy server. For example, by selecting the IP address and port number of the proxy server in the browser, resources on the network can be accessed through the proxy server.
Forward ProxyProxy means that the client accesses other network resources through the proxy server so that the server sees the access of the proxy server without knowing the client's existence so that the client can obtain the effect of anonymity.
Reverse ProxyProxy means that the proxy server initiates a request to the target server on behalf of the client. The target server sees the request of the proxy server without knowing the client's existence, so the client can also obtain the anonymous effect. Reverse ProxyProxy is often used in scenarios such as load balancing and caching.
In short, forward ProxyProxy and reverse ProxyProxy a proxy technology that can improve the access speed and security of the client and provide the effect of anonymous access.
Second, the characteristics of ProxyProxy.
Proxy technology can provide anonymity, high availability, caching function, transit service, and management and control capabilities.
Anonymity refers to establishing a virtual network connection between the client and the target network, thereby hiding the source address of the client and the absolute address of the target server. This can protect the client's security and prevent the client's address from being leaked and attacked.
High availability means that the proxy server can load multiple servers and distribute traffic to multiple servers according to specific rules, thereby improving the system's availability. This method is often used in website load balancing and server clusters.
The caching function means that the proxy server can cache the website's static resources and directly provide the cached resources when the user visits next time without having to request the target server. This can reduce network requests and response time and improve website access speed. Usually, proxy software such as squid can realize the caching function.
When A visits B, it usually communicates through a fixed-line. A cannot access B normally if there is a problem with the line between A and B. And C can access B, and A can access C at this time. C can deploy itself as a proxy application to provide A with a proxy server. In this way, A can successfully access B through C, which may be used in scenarios such as game acceleration, GitHub acceleration, and scientific Internet access.
After the proxy server provides the transit service, if the service is open to the outside world, everyone can use it, then authentication is required to control the user. This is because the user's IP is floating, and if the visitor's identity is not determined through authentication, it is impossible to control the user. Therefore, authentication is very important when it comes to surfing the Internet safely, and it is possible to know who is using the proxy server. In addition to providing authentication, a qualified proxy server should also be able to record access logs and provide some management and control services. For example, the proxy server can provide multiple authentication methods such as basic, NTLM, Kerberos, and token. For example, the squid application can provide a basic authentication mode. In addition, as a middleman, the proxy server can also decrypt the traffic and perform content control, and set some control capabilities. For example, the squid application can provide some control functions, while the intermediary control of the Burp Suite proxy mode can provide more control capabilities. During the user's use, the proxy server should also record relevant logs to trace the access records and locate problems conveniently.
Many ideas were put forward the first time I wrote an article, but the writing could have been better. This situation is like dealing with every writing test before the college entrance examination. The thinking is very divergent, so that the language could be better. Although I have a lot of ideas, I can't write them out. I have racked my brains. In addition, many friends asked if there is any good Proxy merchant to recommend. I usually use several software such as MaxProxy, NetNut, and GeoSurf, which are very stable and easy to use. Everyone chooses the appropriate software according to their own needs, don't blindly follow the trend.