Some time ago @RareSkills_io on Twitter posted a fun gas puzzle called Mint150.
The goal of this puzzle is to mint 150 #NFTs for yourself in one transaction while staying under a certain gas limit.
Smart contract code: https://t.co/TLGP8W1LbY
Test code: https://t.co/CPXHadkgNX
Rules are simple:
-
You may not create more accounts. You may only use the attacker account.
-
Since the mint has to be done in one transaction, everything should be implemented in the constructor.
-
You may not modify the victim contract
Let's go over the implementation👇
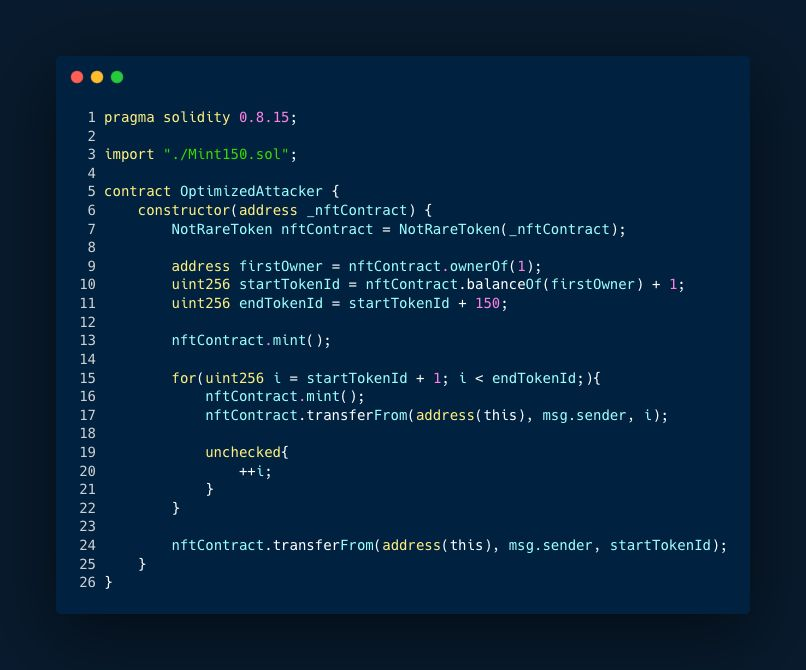
Line 7 initializes ERC721 which we have to exploit.
Lines 9-11 determine which token IDs will be minted. This is required since the test performs a random number of mints during setup to prevent test fitting. We can determine loop bounds after we get our initial token ID.
The goal of the loop is to mint and transfer 150 tokens. Because our account starts with a token balance of zero, minting and transferring a token immediately changes our balance from 0 to 1 and then back to 0. Because of the way the SSTORE opcode works, this uses a lot of gas. SSTORE is expensive, and the price is determined by a variety of factors.
Here is the cost breakdown:
-
If the value of the slot changes from 0 to any non-zero value, the cost is 20000
-
If the value of the slot changes from 1 to any non-zero value, the cost is 5000
-
If the value of the slot changes from any non-zero value to 0, the cost is 5000
In our situation, this means that each time the loop iterates, we will have to pay 25000 gas for updating our balance from 0 to 1 and then back to 0.
One clever approach we may do is to "premint" 1 #NFT before the loop, which will cause our balance to switch between 1 and 2 in the loop. Gas cost will significantly drop as a result. Premint is on line 13.
Line 15 - 22 is our loop that mints and transfers 150 tokens from the contracts to the initial caller account.
Line 24 transfers preminted NFT and that’s it.
Additionally, the reentrancy attack with the callback function onERC721Received on ERC 721 can be used to solve this challenge since Mint150 contract uses _safeMint and has no reentrancy guard.
However, the onERC721Received callback won’t be triggered if the mint function is called from the constructor, since the method which checks if the caller is a contract (EXTCODESIZE) returns 0 if it is called from the constructor of a contract.
To work around the EXTCODESIZE problem, deploy a new contract from the Attacker contract.
The biggest take from this puzzle is to understand how SSTORE opcode works and how to use it to your advantage.