Introduction - What is MetaDock?
MetaDock is a free and incredibly helpful browser extension for Chrome & Chromium-based web browsers (like Brave). It is designed and published by the team at BlockSec, a well-respected blockchain and Web3 security company that offers a host of other, similarly impressive tools, which are generally focused on the more technical aspects of Web3 interfacing.
One such utility is Phalcon, which I will touch on in this article as well. For now though, you should know that MetaDock is very accessible and easy-to-use. Whether you are a veteran of the space, an aspiring security researcher looking for the secret weapon to make your life easier - or even if you are brand new to Web3 - I highly recommend you to check it out.
Personally (as is blatantly obvious) I am a huge fan. As a security researcher, it is arguably the best tool in my toolkit to date. I know - big words, right? No worries! I’ll prove it to you 😉
So, what does it do?

I'll be quick about this - as quick as possible, that is. There's quite a lot packed in. Here are some key features to get us started:
-
MetaDock enhances the most popular platforms we already use, such as Etherscan and the related *-scan family of block explorers - across a huge variety of networks. The extension integrates directly into these websites with embedded links to popular tools, such as:
-
Debank and NFTGo, providing radically simple connectors to quickly view the broader profile of any given Web3 wallet address.
-
Tenderly, DethCode, and Dedaub — a fantastic selection of developer tools offering their own host of features; namely, decompilation of smart contract code, transaction simulations, and deeper analysis of the components of a transaction or the code itself, i.e. debuggers, stack/function call tracing, etc.
-
BlockSec's own Phalcon, which I highly recommend, is a fantastic resource for breaking down more complicated transaction flows, particularly DeFi-centric activities such as on-chain swaps and even much more complex activities, such as MEV (Maximal Extractable Value) events/contract interactions.
-
There’s more! — but honestly, you should see for yourself; or at least follow along below, where I will be diving into some on-chain action for a demonstration!
-
After having all of these integrations readily available, I have not looked back since I initially installed the add-on. Even still, there are two features in particular that I feel truly make MetaDock stand out from the crowd. Amidst the embedded third-party tools, the BlockSec team have also implemented their own tooling, including:
-
an incredibly simple, yet robust charting tool to allow anyone to follow the complex flow of funds and events on-chain. While not an exhaustive study, it’s still a game-changing addition to any workflow.
-
cross-chain address, contract, and named-entity awareness which is extended to the integrated charting 😳 This has massively reduced the amount of browser-tab-hopping and bottomless rabbit-hole-following in my research.
You deserve this.
Okay, moving on 🙂
Installation
I will assume you are familiar with the process of installing a browser extension. Even if you aren't, no worries friend. It's as easy as navigating to the MetaDock website, or use this link to go straight to the Chrome web store where you can install it with the single click of a button.
You actually don't even need a Web3 wallet for this experience, so for brevity I am just going to abstain from diving any further into this topic. Of course, I'd be happy to help you out with that too, should you need. Feel free to reach out to me directly on Twitter, Telegram, or send me a friend request on Discord, if so 🙂
Ok, assuming you are locked & loaded, the only remaining tasks are:
-
Pin the addon to your browser toolbar for quick access (optional)
-
Find some suspicious (or just interesting) on-chain activity to dig into (not optional, we are committed - also, I didn’t plan this part out at all, so this will be fun!)
Alright, enough talk, let’s GO!
I’m going to pick an address at random, but we’ll use something from ChainAbuse, which is a great platform for reporting hacks/scams/phishing and other malicious activity in Web3. This will ensure that our adventure is interesting.
Disclaimer: I am not accusing anyone of anything, though I may express suspicion as we proceed. I am going into this without any prior knowledge, and whatever we discover will be what it is.
We’ll start here: 0xD06d13969cbDE1cD8B8514D1Cc9042cD768Dd891
(on Etherscan and here’s the report on ChainAbuse)

In this particular case, the report on this address has accused it of being a wallet-drainer, so let's start with something as basic as checking out the NFT view via Debank for this address.

Pretty damning! But, also not super interesting or revealing. Let's continue by heading back to the Etherscan page for this address, again — better yet, let's check out the transactions overview for that address:

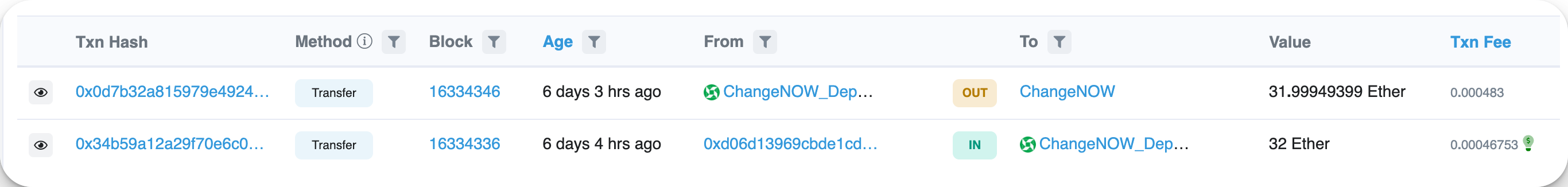
So here, there are a lot of the same transactions, all kind of repeating. It's mostly a bunch of Transfer From events, and otherwise we see some NFT sales. Then it slows down after the accused wallet-drainer transfers out from this address through an interchain swap service, which is pretty obviously an exit maneuver in an effort to make it hard to trace.
It's worth noting here that those green icons are none other than the MetaDock logo, indicating that these addresses have been labeled for us through the add-on, i.e., if you were to disable MetaDock, it would look more like this:

Let’s see if we can actually follow the transaction, knowing this move is meant to make the task more challenging. Here’s that destination address on-chain
0xAB77A1522c234B299E7E0998067FD10fE537b373
Here’s a screenshot of the address, which has actually been flagged as “Medium Risk” by MetaDock for us:

We can see that this is just an intermediary address used for deposits to the swap:
Hmm… I thought I would hold out on the really fun stuff, and honestly thought I could manage to draw this out a lot longer, but quite frankly, I am a little impatient.
Let’s just check out the funds flow feature now, shall we? 😈

Ok not exactly riveting, in fact if you check out that address which is represented on the far right here, you will see that we have effectively hit a dead-end.
Now, if I were really working a case here, I would not give up this fast; however, in this context I am far less inclined as it would mean annotating the remainder of the process and boring everyone with that. We have hardly even had a chance to see MetaDock in action yet though! So now, we’ll look at some more interesting examples, rather than attempting to follow the entire flow from one end to the other.
Let’s head back to the accused address on Etherscan, and take a look at the flow of funds, as observed through that address alone:

Yeah, that’s a lot more like it! In fact, it almost seems like we have a trail to follow. Below, I have zoomed-in a bit more on this huge overview. As you can start to see, it appears that there are some interesting or even suspicious destinations:


I should mention, not only are these graphs interactive in that you can click any node and pan the viewfinder in, out, and around the graph; but also, they are exportable by default as both SVG and PNG-formatted images. What’s really awesome though, is that the SVG-formatted exports are actually embedded with all of the visible information!
I will conclude the search here, but if you are looking for yourself, you might notice some peculiarly-named (ENS) addresses that have certainly interacted with the accused address. I am almost certain these are just MEV bots (not malicious), likely to have been scouting for sales that exceeded a certain percentage threshold set below the floor price of those punks. This makes sense, because the seller, if they really did steal those punks, would definitely by trying to sell them quickly so they could move the funds elsewhere, to try to wash them.
I hope you have enjoyed this brief adventure, and that it might have inspired you!
Closing notes, relevant links, and some more interesting images to show off MetaDock
-
There are also two campaigns currently underway by the MetaDock team, which you would probably be interested to know includes some prizes, and the opportunity to join the MetaDock whitelist 👀
Here are the links, on Galxe and SoQuest:








