Address poisoning is a rising threat in the crypto world. Learn how these scams work, the different types of attacks, and how to protect your digital assets from falling into the wrong hands.
This article is also published on my Medium page.
Crypto has definitely shaken things up in the finance world, no doubt about it. The whole decentralized, secure, transparent way of moving money around is becoming a game-changer. However, as with any groundbreaking technology, its complexity also creates opportunities for illicit actors to exploit vulnerabilities. One such threat rapidly gaining traction is address poisoning — a scam that preys on our reliance on the seemingly innocuous practice of copy-pasting addresses.
At its core, address poisoning is a cunning scheme in which attackers send tiny transactions from addresses crafted to mimic yours or your recipient’s. These minuscule amounts of cryptocurrency are designed to blend seamlessly into your transaction history, setting a trap for the unsuspecting user.
Cryptocurrency Addresses: The Achilles’ Heel of Copy-Pasting?
Cryptocurrency addresses are long, complex strings of characters that blend numbers and letters in a seemingly random fashion. While secure, these hexadecimal addresses are nearly impossible for anyone to memorize or manually enter without making mistakes. As a result, most of us have relied on the copy-and-paste functionality to ensure accuracy when transferring funds.
However, this convenience comes with a caveat. Wallet interfaces often display only a few characters of an address, making it challenging to distinguish between legitimate and malicious addresses at a glance. This shortcoming plays right into the hands of address poisoning scammers, who can craft addresses that appear strikingly similar to your own or your recipient’s.
Anatomy of a Crypto Scam: How Address Poisoning Unfolds
The process of address poisoning is deceptively simple yet remarkably effective. First, scammers monitor transactions involving popular cryptocurrencies, such as Bitcoin and Ethereum, or stablecoins like USDC or DAI. When they detect a transfer involving a potential target, they swing into action.
Learn how to use Python to monitor blockchain transaction. Read on…
Using specialized tools, scammers generate what are known as “vanity addresses” —addresses designed to resemble your or your recipient’s address. With these addresses in hand, the scammers send a minuscule amount of cryptocurrency, often less than a penny’s worth, to your wallet. This transaction appears innocuous, but it sets the stage for their deception.
With this poisoned transaction now in your transaction history, the trap is set. The scammers patiently wait for the moment when you accidentally copy the malicious address instead of your own or your intended recipient’s. And when you make that simple mistake, you unwittingly send your hard-earned cryptocurrency directly into the scammer’s waiting hands.
That’s the whole deal. I hope you did not start reading expecting something more sophisticated. But read on to learn how it’s done and how to spot it.
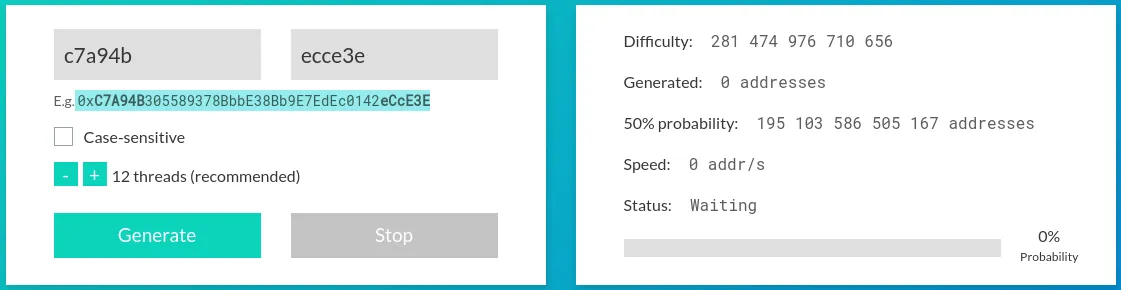
For example, I’m using vanity-eth.tk to create a custom address that matches the first 6 and last 6 characters of my target wallet — 0xC7a94b4960a48F7A0518999Ff24766A2F9eCCe3E. The new vanity address I generated is 0xC7A94B305589378BbbE38Bb9E7EdEc0142eCcE3E. Most wallets abbreviate these long strings, so they’d display as 0xC7a94b…eCCe3E for the target, and 0xC7A94B…eCcE3E for the malicious vanity address. See how deceptively similar those look? It’s the perfect trap to trick you into pasting the wrong one when sending funds.
The Many Faces of Address Poisoning: Fake Tokens, Zero-Value, and Dust Attacks
While the core concept remains the same, address poisoning attacks have evolved into several distinct variants, each with its unique twist.
Fake Token Attacks: In these scams, the transaction appears to involve a legitimate cryptocurrency token, but upon closer inspection, the contract address associated with the token is fake. This deception can make the transaction appear legitimate at first glance, increasing the chances of you falling for the scam.

Zero-Value Attacks: As the name suggests, these attacks involve sending zero-value transactions to your wallet. While these transactions may seem harmless, they serve the sole purpose of populating your transaction history with the scammer’s malicious address, setting the stage for potential future mishaps.
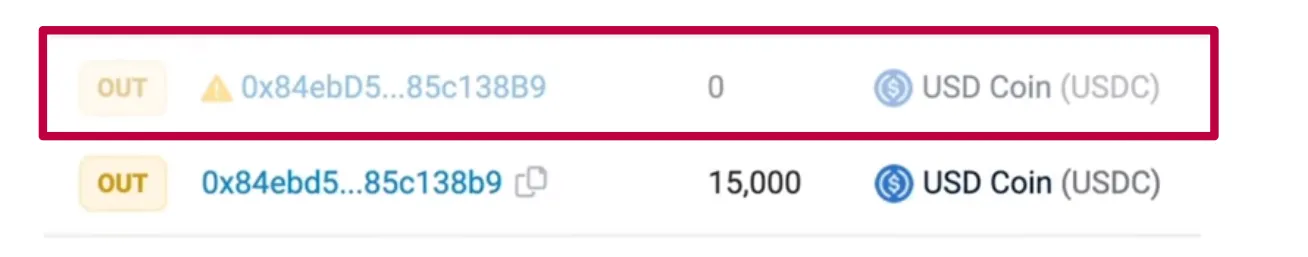
Figure 5. This image shows two transaction records where the top entry, highlighted in red, exemplifies a zero-value address poisoning attack with an outgoing transfer labeled “OUT” from an address “0x84ebD5…85c138B9” involving 0 units of USD Coin, contrasting with a legitimate transaction of 15,000 USDC below it.
Dust Transfer Attacks: Perhaps the most insidious variant, dust transfer attacks involve sending tiny amounts of legitimate cryptocurrency from an address that closely resembles one of your historical transactions. This tactic exploits your tendency to recognize addresses by their first and last few characters, increasing the likelihood of mistaking the scammer’s address for a legitimate one.
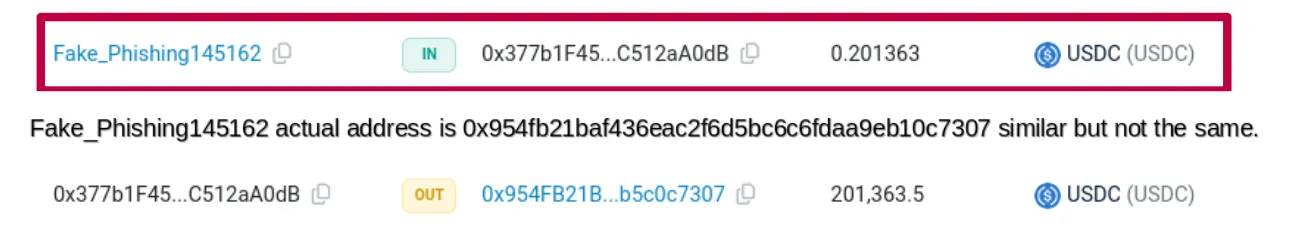
The Devastating Impact of Address Poisoning: Millions Lost, No Recourse
The consequences of falling victim to an address poisoning scam can be devastating. Recently, CertiK identified a cryptocurrency trader who lost $69.3 million of Bitcoin to an address poisoning scam. Because blockchain transactions cannot be altered, funds mistakenly sent to the wrong address are usually irretrievable, with very limited recovery options.
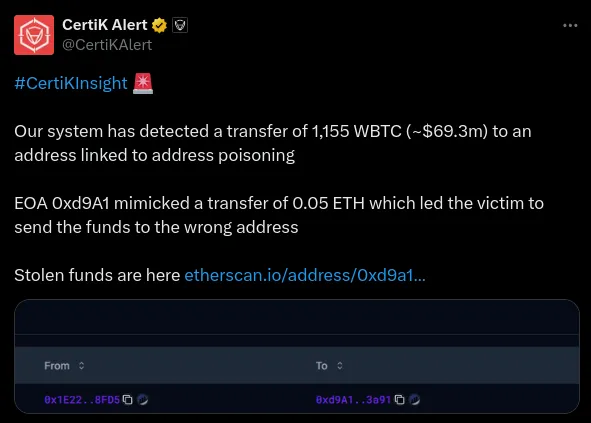
As more people adopt cryptocurrencies, the incidence of address poisoning scams is expected to rise, exposing more users to the risk of losing their valuable digital assets. This reality underscores the urgent need for heightened awareness and proactive measures to combat this insidious form of cyber-attack.
Shielding Your Crypto: Essential Steps to Thwart Address Poisoning Attacks
While address poisoning scams are undoubtedly a cause for concern, there are steps you can take to mitigate the risks and safeguard your cryptocurrency. One of the most apparent practices is to meticulously double-check every character of an address before pasting it into a transaction.
Some wallets have integrated tools that help validate addresses, such as checksum verification, which can provide an additional layer of security. Also, whenever possible, confirm the address with the intended recipient, either verbally or through a secure channel, to ensure its authenticity.
Finally, always remain alert and treat any unsolicited transactions cautiously, whether small or large. Reporting suspicious activity to the relevant wallet provider or authorities can also help raise awareness and potentially thwart future address poisoning attempts.
Summing Up: The Future of Crypto Security Against Address Poisoning
As the cryptocurrency ecosystem evolves, address poisoning scams serve as a sobering reminder that vigilance and caution are paramount in protecting one’s digital assets. While the convenience of copy-and-pasting addresses is undeniable, it is a small price to pay to ensure the security of your hard-earned cryptocurrency.
Looking ahead, developing more robust address validation tools and increasing education will play a crucial role in mitigating the threat posed by address poisoning scams. By staying informed, exercising due diligence, and adopting best practices, you can confidently navigate the world of cryptocurrencies without falling prey to these insidious attacks.
Thanks for reading. Catch you next time…
Explore Next
Think Web3 offers privacy? Think again! This is one article every cryptocurrency user must read. Read on…
Discover how blockchain is transforming industries on the Blockchain Insights Hub. Follow me on Twitter for real-time updates on the intersection of blockchain and cybersecurity. Subscribe now to get my exclusive report on the top blockchain security threats of 2024. Dive deeper into my blockchain insights on Medium.
