Learn the basics of Bitcoin transactions & tracking methods for law enforcement, including tools & techniques to enhance your investigations.
This ACFCS contributor report, initially published on July 17, 2024, by the Association of Certified Financial Crime Specialists (ACFCS), includes editing and content contributions from Brian Monroe, ACFCS VP of Content.
The skinny:
-
In this article by longtime fincrime fighter Ervin Zubic, head of blockquiry, he offers a practical guide to help law enforcement officers at all levels better understand the basics of how Bitcoin transactions work, explore manual tracking techniques, and highlight tools that can simplify illicit value tracking efforts.
-
As more officers encounter crypto in their work, understanding the basics of Bitcoin transactions and how they intersect with both the virtual and physical worlds will become an increasingly vital skill — including banks and crypto exchanges.
-
Banks are typically called the “on-road and off-road” of virtual value exchange transactions, meaning that if an investigator can build a strong enough case by following the blockchain and overcoming regional or jurisdictional hurdles, they could use subpoena powers to investigate, seize, and freeze assets in the real world.
How Bitcoin Can Help Track Down Criminals (HBO). Source: VICE News on YouTube.
Bitcoin has become a significant component of modern investigations, particularly when dealing with financial crime.
This article, inspired by my recent engagement with local law enforcement on a complex case involving Bitcoin and an investment scam, aims to demystify the cryptocurrency for officers new to its intricacies.
The case revolved around a sophisticated network where criminals used Bitcoin to defraud investors, promising high returns and then disappearing with the funds.
This presented a significant challenge for investigators, who initially struggled to trace the digital breadcrumbs. Through diligent analysis and the use of blockchain analytics tools, we managed to uncover the transaction paths and link them to real-world entities.
Many local law enforcement departments are still unable to handle cryptocurrency investigations effectively.
This does not imply a lack of capability — many departments are proficient — but the focus here is on providing foundational knowledge to those unfamiliar with cryptocurrency investigations.
As more officers encounter crypto in their work, understanding the basics of Bitcoin transactions and how they intersect with both the virtual and physical worlds will become an increasingly vital skill.
In this article, we’ll cover the basics of how Bitcoin transactions work, explore manual tracking techniques, and highlight tools that can simplify your tracking efforts.
By the end, you’ll have a solid understanding of Bitcoin transactions and be able to explain the underlying processes confidently. This knowledge will be invaluable if you need to testify, enabling you to go beyond merely stating, “We plug in the values, and the software tracks it.”
Additionally, you’ll develop the skills needed to identify and correct errors that the software might occasionally make, ensuring accuracy in your investigations.
In some cases, it could behoove an investigator to follow the money in a virtual world back to its connections in the real world, including brick-and-mortar banks and crypto exchanges.
Banks are typically called the “on-road and off-road” of virtual value exchange transactions, meaning that if an investigator can build a strong enough case by following the blockchain and overcoming regional or jurisdictional hurdles, they could use subpoena powers to investigate, seize, and freeze assets in the real world.
Understanding these dynamics will not only enhance your investigative skills but also empower you to leverage the full potential of blockchain analytics in your law enforcement efforts.
Bitcoin’s Role in Crime
Bitcoin’s transparency has paradoxically made it a tool for both legitimate and illicit purposes. Crypto scams extend beyond foreign nation-states like Russia, Iran, and North Korea or foreign money laundering and sanctions-busting networks. Street-level criminals use crypto transactions for various reasons, appearing in city, county, and state investigations. For example, in addition to high-profile investment frauds, crypto is prevalent in pig butchering scams where victims are groomed into fraudulent investments and business email compromise attacks where illicit payments are funneled via the Bitcoin blockchain. Common crypto scams include blackmail, sextortion, and ransomware, which are the most reported types, according to data analyzed from over 250,000 abuse reports. Today, Bitcoin is used in a wide range of criminal activities, from smaller-scale crimes like drug deals to large ransomware payments, all exploiting its perceived anonymity.

Major Cases and Rapid Resolutions
Bitcoin’s immutable ledger has enabled law enforcement to resolve significant cases swiftly, often in a matter of months rather than years. For example, in one landmark case, Michael Kane and Shane Hampton were sentenced to prison for manipulating cryptocurrency prices and committing securities fraud. They used an automated bot to place spoof and wash trades, fraudulently inflating the price of their token, Hydro, leading to millions in illicit profits. By meticulously tracing these fraudulent transactions on the blockchain, authorities could link the scheme back to the perpetrators and secure convictions.
Similarly, Remy St. Felix orchestrated a series of violent home invasion robberies across multiple states, targeting cryptocurrency owners. His crew used physical violence to force victims to drain their crypto accounts, stealing substantial amounts of digital currency. Investigators, leveraging blockchain analysis and traditional surveillance methods, unraveled the network, leading to the arrest and conviction of St. Felix and his co-conspirators. These examples highlight how blockchain technology, combined with diligent investigative work, can lead to the rapid resolution of complex crypto-related crimes.
Anti-Money Laundering (AML) Regulations
The global response to Bitcoin’s use in crime has led to the implementation of stringent Anti-Money Laundering (AML) regulations aimed at enhancing transparency and traceability of crypto transactions. The Financial Action Task Force (FATF) has provided guidelines that serve as a framework for these regulations. One key aspect of these guidelines is the Travel Rule, which mandates that crypto exchanges collect and share detailed transaction information. In the European Union, this will be enforced starting December 30, 2024, under the Markets in Crypto-Assets (MiCA) regulation. The Travel Rule requires that information such as the names, distributed ledger addresses, and account numbers of both the originator and beneficiary be included in each transaction, regardless of the amount. This presents challenges due to the pseudo-anonymous nature of Bitcoin, making it difficult to capture and share this information accurately. Consequently, international cooperation and advanced blockchain analytics tools are essential for effective enforcement, ensuring that AML measures can adapt to the complexities of the digital age.
Bitcoin Addresses Explained
A key concept in understanding Bitcoin transactions is cryptocurrency addresses. These are strings of letters and numbers functioning similarly to email addresses or bank account numbers, giving users the capability to exchange Bitcoins on the blockchain.
A Bitcoin address functions like an email address in that it allows you to send and receive Bitcoin. It is created from a public key and is formatted in a specific way (often using base58). However, a Bitcoin address is not the same as a wallet. A wallet is a digital tool that can manage multiple Bitcoin addresses along with their corresponding private keys.
Public and Private Keys
-
Public Key: Functions like a mailbox where anyone can send Bitcoin to you. It forms part of the Bitcoin address.
-
Private Key: A private key, acting like a password, unlocks the Bitcoin held at a specific address, enabling you to spend it. Possessing someone’s private key means having control over the Bitcoin at that address.
Different types of Bitcoin addresses have been developed over time, each with unique characteristics:
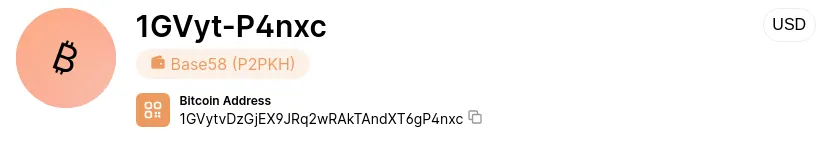
P2PKH Addresses (Starting with “1…”)
Pay-to-Public-Key-Hash (P2PKH) addresses are the original Bitcoin address type, introduced with Bitcoin’s launch in 2009. These addresses start with “1” and are 25–34 alphanumeric characters long, representing the hash of a recipient’s public key. They provide a way to send funds directly to the associated Bitcoin wallet.
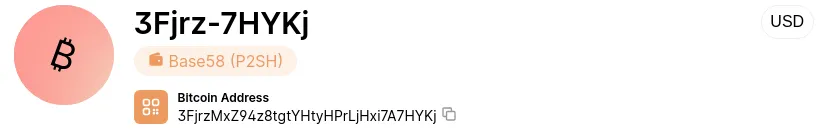
P2SH Addresses (Starting with “3…”)
Introduced in 2012, Pay-to-Script-Hash (P2SH) addresses start with “3” and allow users to send funds that can only be spent if certain customized rules are met. This enables more advanced transactions, such as multi-signature transactions requiring multiple private keys to validate.
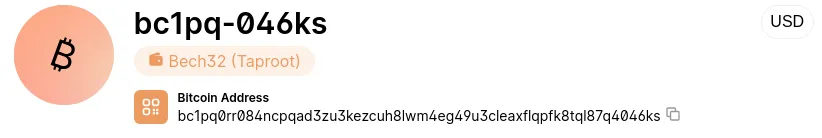
Bech32 Addresses (Starting with “bc1q…”)
The bech32 format, introduced in 2017, is a more efficient way to encode Bitcoin addresses. Prefixed with “bc1q,” these addresses help reduce network traffic by allowing more transactions per block. They are also case-insensitive, reducing user errors.

Taproot Addresses (Starting with “bc1p…”)
Adopted in 2021, Taproot addresses (starting with “bc1p”) enhance privacy by making all Bitcoin transactions look similar on the blockchain. They also improve efficiency by allowing the network to process more signatures in parallel and are case-insensitive like bech32 addresses.
Understanding these addressing schemes is crucial for law enforcement. It allows officers to interpret the complex yet immutable trail of activity on the blockchain and recognize various Bitcoin address formats, preventing critical evidence from being overlooked.
How Bitcoin Transactions Work
At its core, Bitcoin operates as a decentralized peer-to-peer electronic cash system without a centralized authority, like a bank, controlling the network. Instead, every Bitcoin transaction is recorded on a public ledger called the blockchain, organized in sequential batches known as blocks.
Bitcoin Transaction Basics: Inputs and Outputs
Every Bitcoin transaction is made up of inputs and outputs:
-
Inputs: The sender’s Bitcoin addresses and the amounts they want to transfer.
-
Outputs: The recipient’s addresses and the payment amounts.
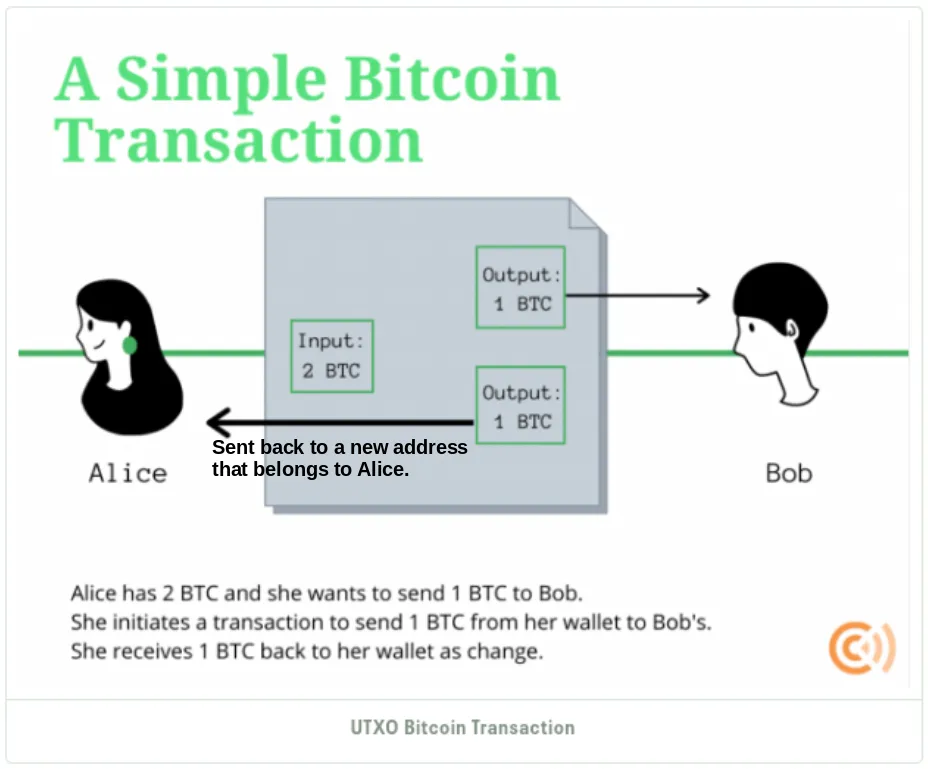
However, transactions are more complex than simply moving money from a sender to a receiver. They consume and re-allocate all the sender’s previous unspent transaction outputs (UTXO) when creating new transaction outputs.
Let’s say that Alice wants to send 1 BTC to Bob, her transaction doesn’t merely deduct 1 BTC from her Bitcoin address. Instead, it consumes all her UTXOs from previous transactions — say 2 BTC in this case. The transaction then creates two outputs: 1 BTC sent to Bob’s address and the remaining 1 BTC sent back to Alice as change.
Actual Bitcoin Transaction Example
Now let’s look what a similar transaction would look like if viewed via blockchain explorer. In our case we will use blockchain.com/explorer. Consider a transaction with the following inputs and outputs:
-
Input Addresses:
-
Address 1 (1Gw192…): 10.1 Bitcoin
-
Address 2 (1Fw7Wv…): 0.03 Bitcoin
-
Output Addresses:
-
Address 1 (1NXw4u…): 0.01 Bitcoin
-
Address 2 (16zy2q…): 10.03 Bitcoins
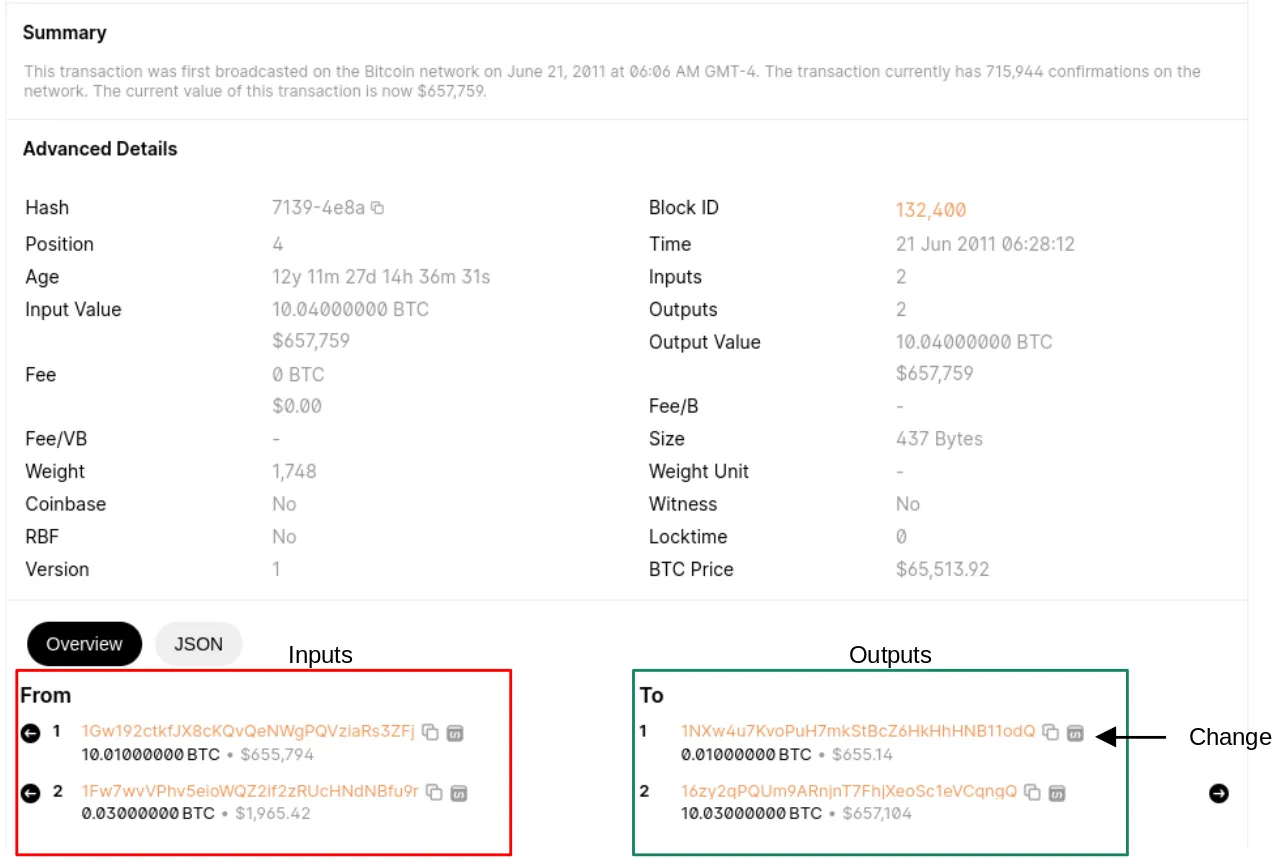
In this example, any single input could cover the amount sent to the first output address. However, both inputs combined are needed to cover the second output. This practice is commonly referred to as co-spending, where multiple inputs are used in a single transaction. This suggests the primary payment is to the second output address,16zy2q, and the first output address is likely the change address, 1NXw4u.
Following Bitcoin on the Blockchain
To help you get comfortable looking at the Bitcoin transaction lets look at few different examples using blockchain.com.
Example Bitcoin Transaction
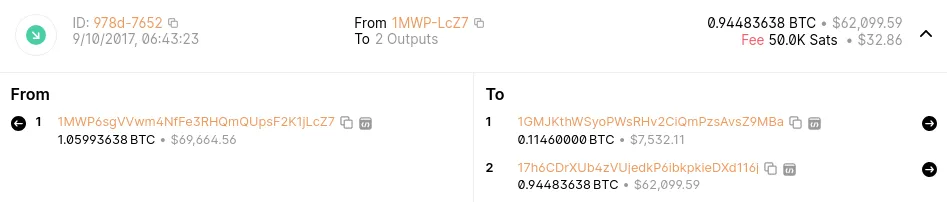
You can explore this transaction on blockchain.com by clicking on this link, which links to Bitcoin address 17H6CDXUbZVUJEDKP6IBKPKIEXDX116J.
-
At 6:43 AM on October 10th, 2017,
1MWP6Ssent a total of 1.05 BTC to17H6CD. -
The address
17H6CDthen received 0.944 BTC, while1GMJKreceived 0.1146 BTC.
One hour later, at 7:43 AM, 17H6CD sent 0.944 BTC to two addresses:
-
1HJAH3received 0.5186 BTC. -
136DCKreceived 0.42 BTC.
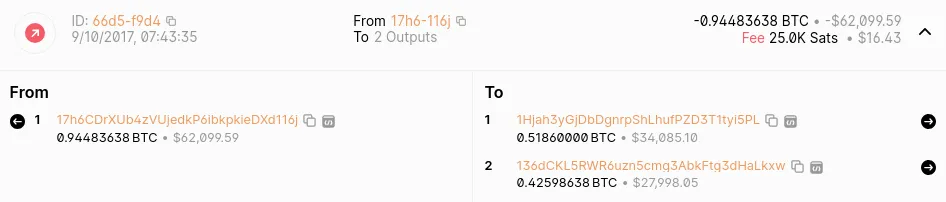
This breakdown helps us understand the activity of the 17H6CDXUbZVUJEDKP6IBKPKIEXDX116J address. Remember, when you send Bitcoin, you don’t just send the exact amount you want to transfer. Instead, the transaction consumes all available UTXOs (Unspent Transaction Outputs) from previous transactions, and any leftover amount is sent back to you as “change” to a new address. This is similar to paying with cash and receiving change back.
Identifying Change Addresses
Now let’s look at another transaction and see if we can figure out which address is a change address. To follow along, click this link, which resolves to transaction 03BA36A19BB7CB3EDE88DD4CCA78A9BED380524C8995A6A910E98F944EE91053 on blockchain.com. Here’s what you’ll see, three addresses are sending coin to two addresses:
-
Input Values:
-
1FKRSN(1 BTC) -
16SFXO(0.0999 BTC) -
1C3NQA(0.0789 BTC) -
Output Values:
-
19GMGG(0.0788 BTC) -
1PSKXK(2 BTC)
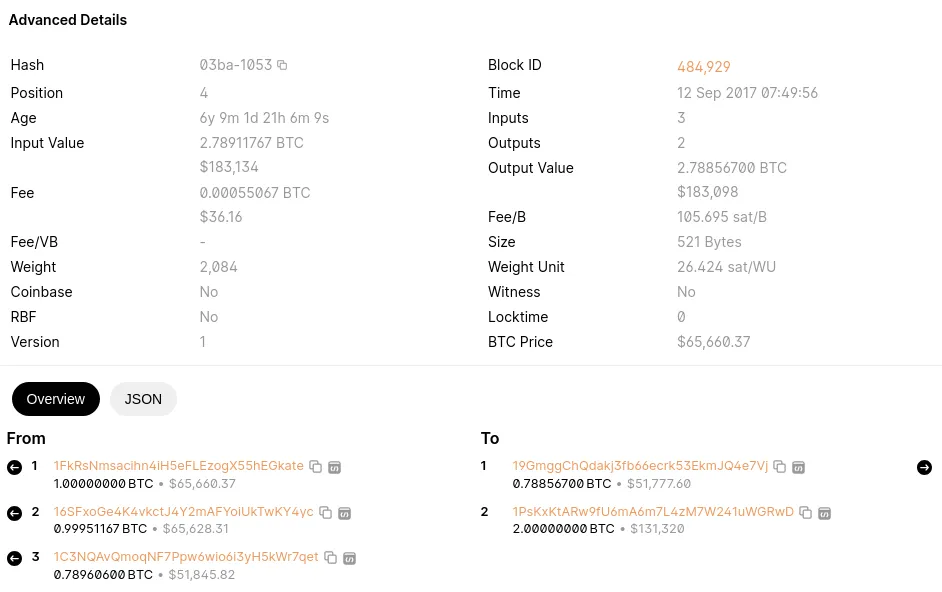
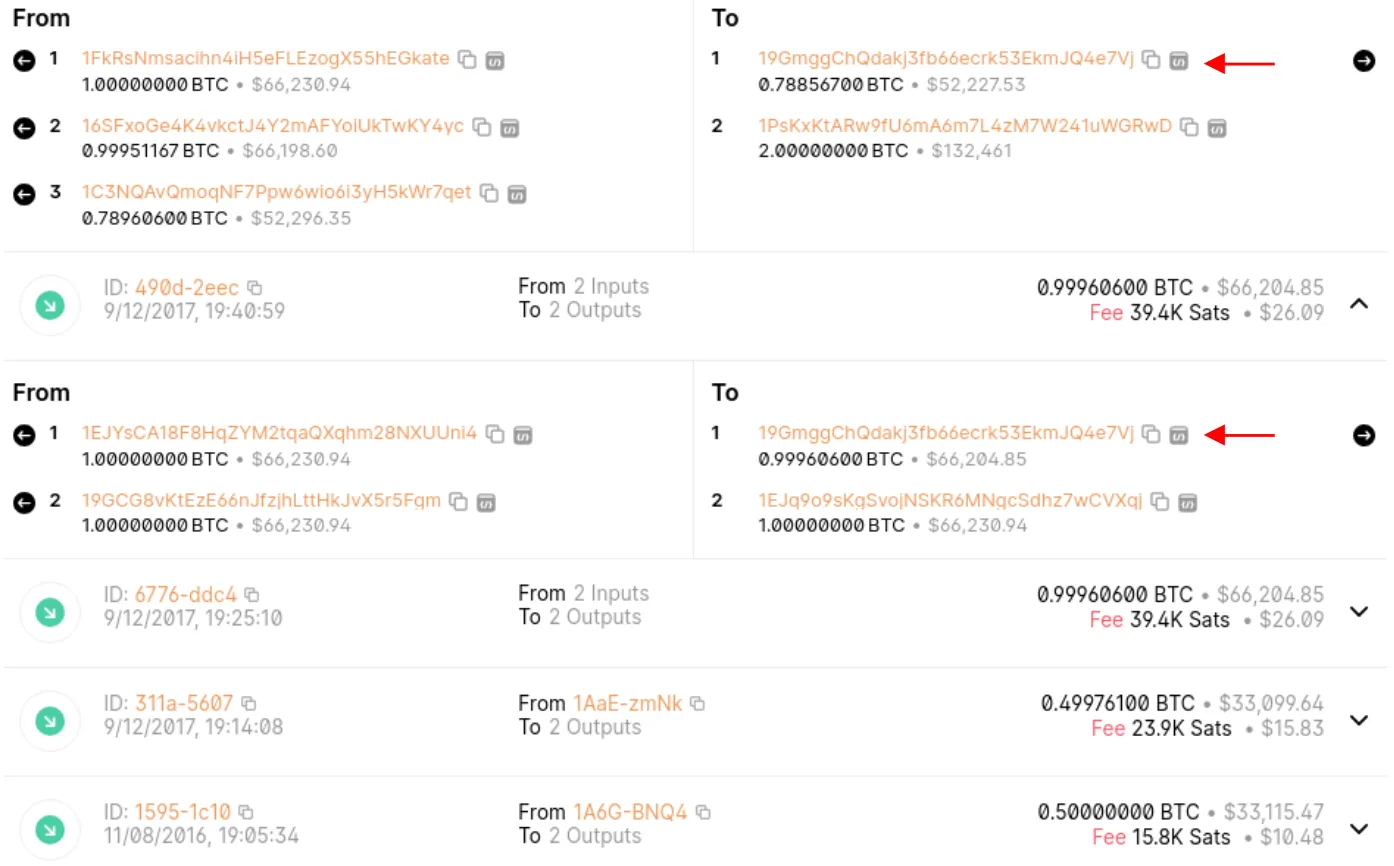
Why are three addresses sending Bitcoin to two addresses? Well, we can assume that 19GMGG is the change address because all three inputs were needed to pay for the 1PSKXK output. The remaining amount likely goes back as change to 19GMGG. If 19GMGG was the target recipient we would only need one address to pay our target recipient. So now we can assume that 1FKRSN, 16SFXO, 1C3NQ & 19GMGG likely belong to the same person or entity.
Clustering Addresses
Let’s continue and identify more addresses within the same cluster. If you’re following along on blockchain.com, click on the change address 19GMGG. This will display all the activity associated with 19GMGG. You should see a total of 8 transactions, with 5 showing Bitcoin flowing into 19GMGG. Incoming transactions are marked by a green arrow pointing down. Expand each incoming transaction to confirm that 19GMGG is the change address in all of them. Therefore, the following addresses belong to the same owner: 19GMGG, 1A6GHK, 1AAEIH, 1GC3RJ, 1CMBBD, 19GCG8, 1EJYSC, 1C3NQA, 16SFXO, 1FKRS.
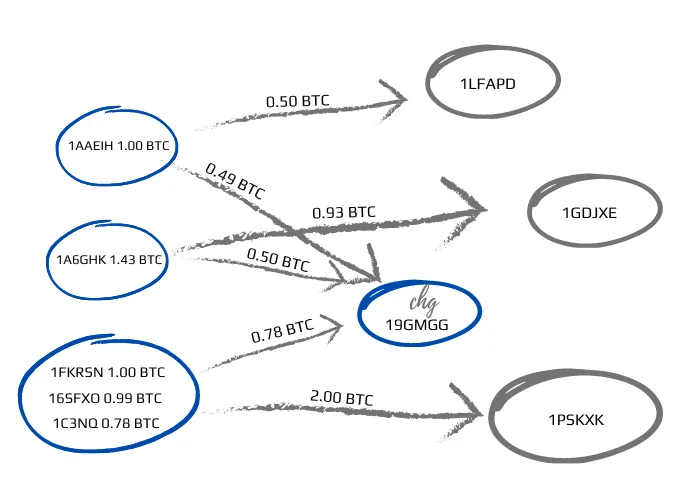
To illustrate the flow of money, let’s manually sketch out the transactions we reviewed. In this sketch, the change address is placed at the center, labeled “chg.” The blue circles represent addresses that belong to the same owner, forming a clustered group. To continue tracking the money, we would next focus on the gray circles, applying the same process to follow the transactions further.
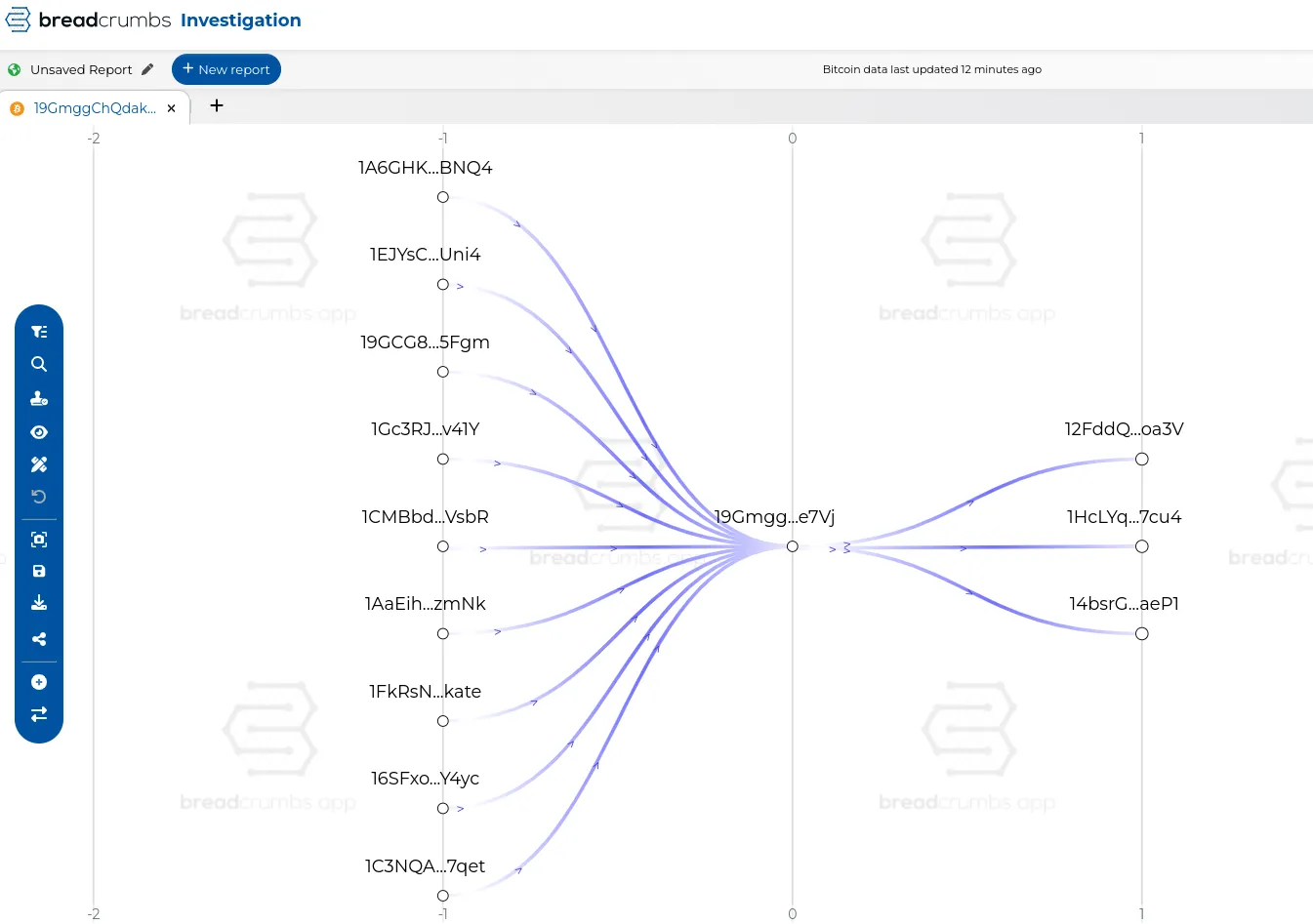
Thankfully, we do not have to manually track and cluster these addresses across multiple transactions. If we did, that would be very painful and time consuming. Advanced blockchain analytics tools like Chainalysis, TRM Labs, Elliptic, MetaSleuth, and breadcrumbs can simplify this process. These tools provide powerful visualizations and automated clustering algorithms, enabling you to quickly identify connections and patterns within the blockchain data. See example below, figure 12.
However, understanding the basics of Bitcoin transactions and being able to manually interpret blockchain data is crucial. It not only enhances your investigative skills but also ensures that you can verify and correct the outputs generated by these software tools. Embrace the power of blockchain analytics, and let these tools transform complex data into actionable intelligence, making your investigative process more efficient and effective.
Advanced Techniques
To elevate your investigative capabilities, integrating advanced techniques can provide deeper insights and uncover illicit activities with greater precision.
Use Blockchain Explorers
Blockchain explorers like blockchain.com are invaluable tools that provide detailed transaction histories and patterns. For instance, when using a blockchain explorer, you can trace the flow of funds through various addresses and identify red flags indicative of illicit activity. These include:
-
Use of Mixers: Mixers, or tumblers, are services that mix potentially identifiable cryptocurrency funds with others to obscure the trail back to the fund’s original source. If you notice transactions where large amounts are split into many small transactions and then recombined, this could be a sign of mixing.
-
Touching Sanctioned Wallet Addresses: If a transaction history shows connections with addresses known to be associated with sanctioned entities or individuals, this is a significant red flag. Regularly updating your list of such addresses and cross-referencing them during investigations is crucial.
-
Microstructuring: Similar to financial microstructuring, if transactions are split into many smaller ones needlessly (to avoid detection thresholds), it could indicate an attempt to evade monitoring systems.
For example, consider a case where a large amount of Bitcoin is transferred to an address, immediately split into numerous smaller transactions, passed through several intermediary addresses, and finally aggregated back into a single address. This pattern suggests attempts at obfuscating the original source of funds, likely pointing to illicit activity.
Cluster Analysis
Cluster analysis is another powerful technique, where repeatedly sending change back to the same addresses often indicates that these belong to the same user or entity. Investigators should also look for:
-
Recurrent Addresses: Regular use of certain addresses for receiving change might suggest these belong to the same person or entity, forming a cluster.
-
Temporal Patterns: Frequent transactions between a set of addresses within a short time frame could indicate coordinated activity.
-
Linking Wallets: By analyzing transaction histories, you might find patterns where multiple addresses are used in tandem, revealing a larger network of activity.
For example, a cluster analysis of addresses frequently interacting with known illicit addresses might show a web of transactions, highlighting a network of related entities engaged in money laundering.
Visualization Tools
Visualization tools that map out transaction flows can help investigators see patterns and relationships in complex transactions. Using tools like Chainalysis or TRM Labs, investigators can:
-
Identify Patterns: Look for circular patterns indicating mixing, star patterns suggesting a single point of control, or branching patterns showing funds being dispersed across many addresses.
-
Trace to Onroads and Offroads: Identify points where cryptocurrencies are exchanged for fiat currency (onroads) or vice versa (offroads), which often happen at exchanges or through OTC brokers. Following these can lead to identifying the perpetrators.
-
Tie Blockchain Addresses to Real Entities: Investigators can link blockchain addresses back to real-world entities by correlating transaction data with other digital footprints like email addresses used in exchanges, social media profiles, or IP addresses logged by service providers. For instance, past cases have successfully linked Bitcoin addresses to individuals by tracking email addresses used during registration on exchanges and cross-referencing with other public records.
Consider a scenario where investigators used a combination of blockchain analysis and traditional detective work to crack a case involving a Ponzi scheme. By following the digital trail, they identified the exchange where the scammers converted Bitcoin to cash, subpoenaed the exchange for account details, and linked those accounts to the scammers’ real identities through associated email addresses and IP logs.
By leveraging these advanced techniques, law enforcement and compliance teams can significantly enhance their ability to track, analyze, and ultimately dismantle illicit networks operating in the cryptocurrency space. Understanding the detailed transaction patterns, utilizing sophisticated tools for visualization, and combining blockchain analysis with traditional investigative methods are key strategies in modern financial crime investigations.
Key Terminology Explained
Here and back again, don’t bluster at clusters, learn to hash things out.
Address
- Imagine you have a special mailbox where people can send you money. This mailbox has a unique address made up of letters and numbers. In the world of cryptocurrency, an address is a digital version of that mailbox where you can send and receive digital money like Bitcoin. It’s like a mix between a home address and an email address.
Base58
- Base58 is a way of encoding data using a set of 58 characters (numbers and letters) that avoids easily confused characters like 0 (zero), O (capital o), I (capital i), and l (lowercase L). This makes it easier for people to read and transcribe Bitcoin addresses without making mistakes.
Block
- Think of a block as a page in a digital notebook. Each page records a list of all the transactions (like buying or selling something) that happened in a certain time frame. Every 10 minutes, a new page (block) is added to the notebook, creating a long chain of pages (blocks) called a blockchain.
Blockchain
- Blockchain is a special kind of digital record book that keeps track of all transactions of cryptocurrencies. Imagine a chain made up of lots of blocks, and each block contains a list of transactions. This record book is shared across many computers, so everyone has the same information, and it’s very hard to change anything without everyone noticing.
Block Explorer
- A block explorer is like a magical magnifying glass that lets you look at the digital notebook (blockchain). You can see all the details of each transaction, like who sent money to whom and when it happened. It’s like looking up the history of all transactions on a website.
Cluster
- A cluster is like a group of mailboxes that are all controlled by the same person or company. Chainalysis, a company that studies cryptocurrency, can figure out which mailboxes belong together. This helps them identify who is using those addresses on the blockchain.
Counterparty
- In any transaction, there are two sides. The counterparty is the other person or company you are dealing with. If you’re sending money to someone, they are the counterparty.
Crypto Exchange
- A crypto exchange is like an online marketplace where people can buy, sell, or trade different kinds of digital money, called cryptocurrencies, such as Bitcoin. It’s similar to a place where you exchange one type of money for another, like dollars for euros.
Crypto ATM
- A crypto ATM is like a regular ATM, but instead of giving you cash, it allows you to buy or sell cryptocurrencies using money. You can put in cash to buy digital money or sell digital money to get cash out.
Custodial Wallet
- Imagine you give your money to a bank, and they keep it safe for you. A custodial wallet is like that, but for digital money. A company or organization holds your cryptocurrency and the special keys needed to access it for you.
Hash
- A transaction hash (or ID) is a unique code, like a receipt number, that confirms a transaction was approved and recorded on the blockchain. It is often used to track and locate specific transactions.
Input
- The input is where the money is coming from in a transaction. It’s like the return address on a letter, showing where the money originally came from.
Multi-signature Transaction
- A multi-signature transaction is like a digital agreement that requires more than one person to sign off before it can happen. It’s like needing approval from multiple people to unlock a treasure chest. This adds extra security because no single person can make the transaction alone.
Output
- The output is where the money is going in a transaction. There can be many outputs, just like you can send copies of the same letter to multiple people.
Mining
- Mining is like solving a really hard puzzle. When someone solves the puzzle, they get to add a new page (block) to the digital notebook (blockchain) and earn some digital money as a reward.
Private Key
- A private key is like a super-secret password that lets you access your digital money. It’s very important to keep it safe because anyone who knows this key can spend your money.
Public Key
- A public key is like a digital address that people can use to send you money. It’s not secret, and you can share it with others. It’s used to create your digital mailbox address.
Transaction Hash
- A transaction hash is like a unique tracking number for a transaction. It helps you find and verify a specific transaction on the blockchain.
Transactions per Block
- Transactions per block refer to the number of cryptocurrency transactions that can be stored in one block on the blockchain. Think of a block as a page in a record book. This page can only hold a certain number of transactions before you need to start a new page, or block.
UTXO (Unspent Transaction Output)
- UTXO is like the leftover change you get after buying something. It shows how much digital money is left and can be used in future transactions.
Wallet
- A wallet is like a digital locker that holds all your private keys and addresses. It keeps your digital money safe and lets you manage where you send and receive it from.
Explore Next
If this article piqued your interest, don’t stop here! Dive deeper into the fascinating world of cryptocurrency investigations with Nick Furneaux’s book or explore certification options through reputable blockchain analytics companies I mentioned above.
To learn how to track the movement of assets using a blockchain analytics software, explore this hands-on guide to mastering MetaSleuth.
Unmask crypto money laundering with our new guide to OSINT and blockchain analytics. Read on…
Discover how blockchain is transforming industries on the Blockchain Insights Hub. Follow me on Twitter for real-time updates on the intersection of blockchain and cybersecurity. Subscribe now to get my exclusive report on the top blockchain security threats of 2024. Dive deeper into my blockchain insights on Mirror.xyz.