Discover crypto-native money laundering, the importance of KYC/AML, and common scams. Essential insights for AML officers and FCC experts in part two of our series.
As we journey deeper into the labyrinth of cryptocurrency crime, it becomes evident that the complexities and challenges extend far beyond initial perceptions. In part one, we navigated the tumultuous waters of cryptocurrency’s evolution and its exploitation for various illicit activities. Now, in part two, we delve into the intricate mechanisms of crypto-native money laundering, the pivotal role of KYC (Know Your Customer) and AML (Anti-Money Laundering) measures, and the ever-growing landscape of cryptocurrency scams. Through this exploration, we aim to unravel the sophisticated tactics employed by criminals and the relentless efforts of regulators and law enforcement to stay one step ahead. Prepare to uncover the hidden layers and the multifaceted nature of digital crime as we continue our comprehensive investigation into the underworld of cryptocurrency.
For a complete understanding of cryptocurrency’s use in crime, make sure to read part one of this series.
Crypto Money Laundering: How Criminals Exploit Cryptocurrency
Whether we are talking about on-chain crypto laundering or off-chain money laundering, the purpose of this activity remains the same: to transform illicit gains into seemingly legitimate funds. In the cryptocurrency world, cybercriminals often link this practice to hiding the proceeds of on-chain crimes, like darknet market dealings and ransomware attacks. However, using cryptocurrency to launder money now spans a broader array of illegal activities beyond what is typically considered a crypto crime. Let’s delve into the stages of money laundering and how they unfold in the cryptocurrency ecosystem.
Definition and Stages of Money Laundering
At its core, money laundering involves three key stages: placement, layering, and integration. Each stage uniquely transforms “dirty” money into “clean” money that can be freely used within the legitimate economy. Regarding on-chain (cryptocurrency activity), we often talk about Illicit wallets (crypto addresses) holding funds from exchange hacks, crypto scams, and darknet market transactions.

The crypto-native money laundering process starts when the above-mentioned elicit wallets start utilizing conversion services, such as centralized exchanges, DeFi platforms, gambling sites, mixers, and bridges, to facilitate the exchange of cryptocurrencies for fiat, other digital currencies, or various services. The one major benefit of blockchain transparency is our ability to conduct faster and more accurate tracing and analysis of such on-chain activities compared to traditional financial systems.
-
Placement is the initial introduction of illicit funds into the financial system. This stage is crucial as it provides the entry point for criminals to begin obscuring the origins of their money. In traditional finance, this might involve depositing cash into a bank. However, in the cryptocurrency world, placement can start when an illicit actor obtains cryptocurrency as a result of a successful hack, scam, or darknet market sale.
-
Layering entails constructing a convoluted network of transactions to conceal the illicit origins of the money. This can include moving funds through various accounts, currencies, or countries to create distance between the money and its illegal source. When it comes to cryptocurrency, layering is done when the illicit actor starts swapping one cryptocurrency for another, jumping from one blockchain to another, or using mixing services to obscure the true origin of the funds.
-
Integration is the final step, where the laundered money is reintroduced into the economy in a way that appears legitimate. This might involve investing in businesses, purchasing assets, or converting cryptocurrency into fiat currency using a cryptocurrency exchange.
Placement in Cryptocurrency
Aside from the placement we discussed above in the cryptocurrency ecosystem, placement often begins with converting cash or assets into cryptocurrency. This can be done through various means, such as cryptocurrency exchanges, peer-to-peer platforms, or Bitcoin ATMs. One of the significant advantages for criminals at this stage is the relative ease with which cryptocurrency can be acquired and transferred. Unlike traditional banking systems, which have rigorous Know Your Customer (KYC) and Anti-Money Laundering (AML) requirements, many cryptocurrency services still lack adequate oversight in some jurisdictions. This gap provides an opportunity for illicit actors to inject their dirty money into the digital financial system with minimal scrutiny.

To keep up-to-date with cryptocurrency regulations in various jurisdictions, bookmark the Atlantic Council’s Cryptocurrency Regulation Tracker.
Layering Techniques
Layering in the cryptocurrency world is a masterclass in obfuscation. Criminals employ several techniques to break the chain of transactions and disguise their money’s origins.
Division involves splitting large sums of cryptocurrency into smaller, less noticeable amounts. These smaller amounts are then transferred across multiple wallets, making it harder to trace the original source.
Transformation refers to converting one type of cryptocurrency into another. This can be done through decentralized exchanges or by using privacy coins like Monero, which offer enhanced anonymity features. By frequently changing the form of the currency, criminals add layers of complexity that can thwart blockchain analysis.
Attenuation is about creating distance. This involves conducting a series of transactions, often across different jurisdictions, or different blockchains to confuse the trail. Each transaction adds another layer that investigators must unravel, making it significantly more challenging to follow the money.
These layering techniques are particularly effective in the digital currency space, where transactions can be executed rapidly and across borders with ease.
Integration Methods
Integration is the final step in the laundering process, where criminals seek to legitimize their ill-gotten gains. Converting cryptocurrency back into fiat currency is a common method, but it comes with its own set of challenges.
Crypto-native Money Laundering Red Flags: Insights for Investigators and Compliance Managers
Let’s review some common crypto-native money laundering red flags that every financial crime investigator and compliance manager should know.
- Key red flags include frequent transactions just below reporting thresholds, which are often used to avoid scrutiny. For example, if a series of transactions repeatedly falls just under the $10,000 threshold, this could warrant a closer look as it could signal an attempt to evade mandatory reporting requirements. To understand crypto Travel Rule compliance and transaction thresholds, check out NOTABENE’s Crypto Travel Rule 101 Guide.

- Using multiple intermediary wallets to obscure fund origins is another common tactic. For instance, criminals might send funds through a web of personal wallets before reaching the final destination, adding layers of complexity to the transaction chain. This was evident in the Atomic Wallet exploit, where funds moved through countless wallets before integration.

- Consolidation wallets aggregate funds from multiple sources. Illicit actors often move funds through numerous intermediary wallets and then reconsolidate them in a single wallet before cashing out at an exchange. Observing funds flowing through several separate wallets and then combining into a single wallet may indicate an effort to evade detection.
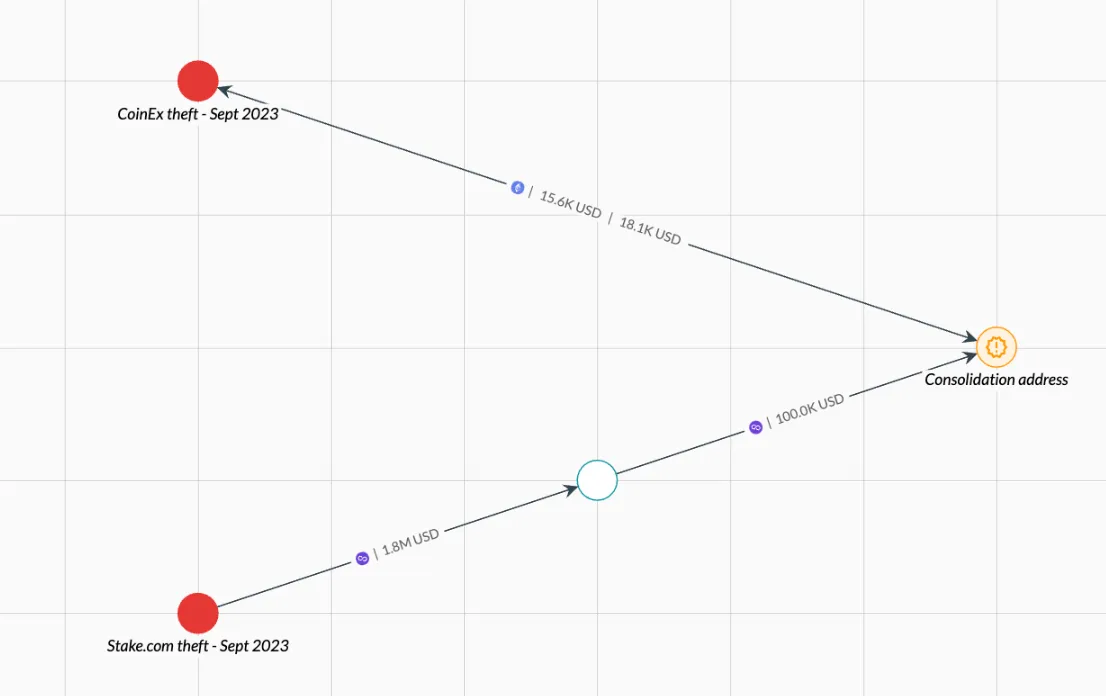
- High transaction volumes through unregulated OTC brokers also signal potential laundering. Over-the-counter (OTC) crypto brokers facilitate large, private trades, often offering better prices for high-volume transactions by connecting buyers and sellers directly through broker-dealer networks or trading desks, bypassing public order books. While most OTCs are legitimate, some lack proper KYC procedures and cater to laundering illicit funds. These shady OTCs operate globally and are challenging to identify, requiring both off-chain and on-chain intelligence.

- Suspiciously large fees paid to process transactions can indicate an urgent need to obfuscate funds quickly. For instance, following a prominent hack, hackers paid abnormally high fees to move their illicit gains through Tornado Cash, highlighting their prioritization of speed over cost. For instance, if the average fee over the past month is $5, a fee of $500 would be unusually high and warrant a closer look.

- Rounded transaction amounts and cross-chain transfers further complicate tracing efforts. Similarly, using cross-chain bridges to move assets across different blockchains can mask the true origin of funds, making it challenging for investigators to follow the money trail.

In addition to the red flags and techniques discussed, it’s crucial to understand how traditional money laundering methods adapt to blockchain. This adaptation expands the toolkit for both criminals and investigators. Monitoring financial flows for suspicious activity often relies on heuristics and thresholds, like those outlined in the Financial Action Task Force (FATF) ‘s Red Flag guidance. Furthermore, the Financial Crimes Enforcement Network (FinCEN) highlights that unusual surges in value flows and other atypical transaction patterns can indicate potential money laundering and sanctions evasion. Recognizing these patterns and understanding criminals’ evolving tactics enables investigators to pinpoint and combat illicit activities more effectively.
Strengthening Defenses: KYC, AML, and Blockchain Analytics in Crypto Compliance
In cryptocurrency’s vast, decentralized realm, compliance is the crucial barrier that maintains the balance between financial innovation and chaos. The significance of Know Your Customer (KYC) and Anti-Money Laundering (AML) measures cannot be underestimated. These regulations are the foundation of financial security, ensuring the cryptocurrency landscape remains a reliable and integral part of the global economy.
Importance of KYC and AML in Cryptocurrency
KYC and AML protocols are critical in defending against financial crimes. KYC ensures customer identities are verified, confirming they are who they claim to be. At the same time, AML encompasses a broader set of practices aimed at detecting and preventing money laundering activities. In the cryptocurrency sphere, these measures are vital due to the pseudonymous nature of digital transactions, which can otherwise provide a veil of secrecy for illicit actors.
Without stringent KYC and AML procedures, cryptocurrency platforms risk becoming conduits for money laundering, terrorist financing, and other criminal activities. Effective compliance protects the integrity of the financial system and builds trust among users, regulators, and the broader public.

Compliance Weaknesses and Their Exploitation
Despite the critical role of compliance, many cryptocurrency businesses fail to implement robust KYC and AML measures. Some platforms, driven by the ethos of decentralization and privacy, resist stringent regulation. Others may lack the resources or expertise to enforce comprehensive compliance frameworks.
These weaknesses are not lost on criminals. They exploit gaps in regulatory oversight, using platforms with lax KYC requirements to funnel illicit funds through the system. The lack of consistent global standards further complicates the situation, allowing bad actors to operate in jurisdictions with weaker enforcement.

Enhanced Due Diligence and Blockchain Analytics
To counter these vulnerabilities, enhanced due diligence (EDD) and advanced blockchain analytics have become indispensable tools. EDD involves thorough background checks and ongoing monitoring of high-risk customers, ensuring that suspicious activities are identified and addressed promptly.
Blockchain analytics tools have revolutionized compliance in the cryptocurrency space. These sophisticated technologies can trace transactions across multiple blockchains, identifying patterns and connections that human analysts might miss. By mapping the flow of funds, blockchain analytics can flag potentially illicit activities and provide valuable intelligence to law enforcement.
For instance, blockchain analytics can detect mixing services, commonly known as “mixers,” which are used to obscure the origins of cryptocurrency. Mixers break the transaction trail by pooling and redistributing funds, making it difficult to trace the original source. However, advanced analytics can often penetrate these layers of obfuscation, revealing the underlying criminal activity.
Products and Services with Heightened Money Laundering Risk
Certain products and services within the cryptocurrency ecosystem are particularly susceptible to money laundering. These include privacy coins, peer-to-peer exchanges, and decentralized finance (DeFi) platforms. Privacy coins such as Monero and Zcash offer advanced anonymity features, making them attractive to illicit actors. While fostering financial innovation, peer-to-peer exchanges and DeFi platforms often operate with minimal regulatory oversight, creating fertile ground for money laundering.
Mixers and Their Role in Cryptocurrency Crime
Mixers, also known as tumblers, play a pivotal role in cryptocurrency crime by providing a service designed to enhance anonymity. They mix various transactions, scrambling the trail and making it difficult for investigators to follow the money. While some users employ mixers for legitimate privacy concerns, their potential for misuse in money laundering and other illicit activities is significant.
For example, in April 2022, mixers peaked in popularity, processing over $1.5 billion in value. Despite a dip after sanctions in 2022, services like Tornado Cash have rebounded strongly, showing significant growth throughout 2023 and 2024. This resurgence aligns with the general increase in market activity, as noted in the Chainalysis 2024 Crypto Crime Report. Conversely, Samourai Wallet growth potential was cut short by the Department of Justice’s actions against its founders and CEO in April 2024.

Case Study: Tornado Cash
In a significant enforcement action, the U.S. Department of the Treasury’s Office of Foreign Assets Control (OFAC) sanctioned the virtual currency mixer Tornado Cash on August 8, 2022. Tornado Cash was implicated in laundering over $7 billion in virtual currency since its inception in 2019, including $455 million stolen by the North Korean Lazarus Group. Despite claims of privacy protection, Tornado Cash consistently failed to implement effective controls to prevent misuse by cyber criminals.

This case underscores the critical role of blockchain analytics and international cooperation in tracing illicit funds through complex laundering schemes. Authorities successfully disrupted Tornado Cash’s operations, highlighting the importance of rigorous compliance measures in the cryptocurrency industry. The action against Tornado Cash exemplifies the Treasury’s commitment to combating cybercrime and protecting the financial system from exploitation by malicious actors.
The takedown of Tornado Cash demonstrates the effectiveness of blockchain analytics in uncovering sophisticated laundering networks, ensuring that even well-hidden illicit activities can be exposed and prosecuted.
Crypto Con Artists: Unmasking Popular Scams in the Digital Currency World
Scammers swiftly adapt to emerging trends, and cryptocurrency is no exception. These scams target unsuspecting individuals by exploiting the novelty and complexity of digital currencies. Let’s delve into the various types of common cryptocurrency scams and examine their significant impact on consumers.
Overview and Typologies
In the rapidly expanding landscape of cryptocurrency, scams have evolved with ingenuity, exploiting the enthusiasm and naivety of investors. Here are some prevalent cryptocurrency scams that highlight the diverse strategies fraudsters employ.
Phishing Scams
Phishing scams involve fraudsters posing as legitimate entities to steal personal information. Victims receive fake emails or messages prompting them to click on malicious links, leading to compromised wallets or accounts.
The cryptocurrency phishing scammer known as Monkey Drainer has been active since late 2022, and is believed to have stolen up to $13 million in cryptocurrencies and NFTs during that time.

Rug Pulls
Rug pulls occur when developers of a cryptocurrency project suddenly withdraw all funds, leaving investors with worthless tokens. This scam typically targets decentralized finance (DeFi) projects and newly launched cryptocurrencies.
Founded in 2017, Thodex was a Turkish crypto exchange that vanished in April 2021, taking over $2 billion of investors’ funds. CEO Faruk Fatih Özer claimed cyberattacks forced the shutdown before disappearing. Turkey investigated Özer for fraud, arrested dozens of employees, and seized the firm’s assets. Interpol issued a red notice, and Özer was arrested in Albania in September 2022. About 90% of rug pull losses in 2021 were linked to Thodex. Prosecutors seek 40,564-year sentences for Özer and others involved, with over 2,000 complainants.

Pump and Dump Schemes
In pump-and-dump schemes, scammers boost the price of a cryptocurrency with false or misleading information. When the price peaks, they sell their holdings, causing the value to crash and leaving other investors with substantial losses.
On September 30, 2022, the SEC charged Arbitrade Ltd., Cryptobontix Inc., and their leaders for a pump-and-dump scheme with the cryptocurrency Dignity (DIG). They falsely claimed to have secured $10 billion in gold to back each DIG token, artificially inflating its value.

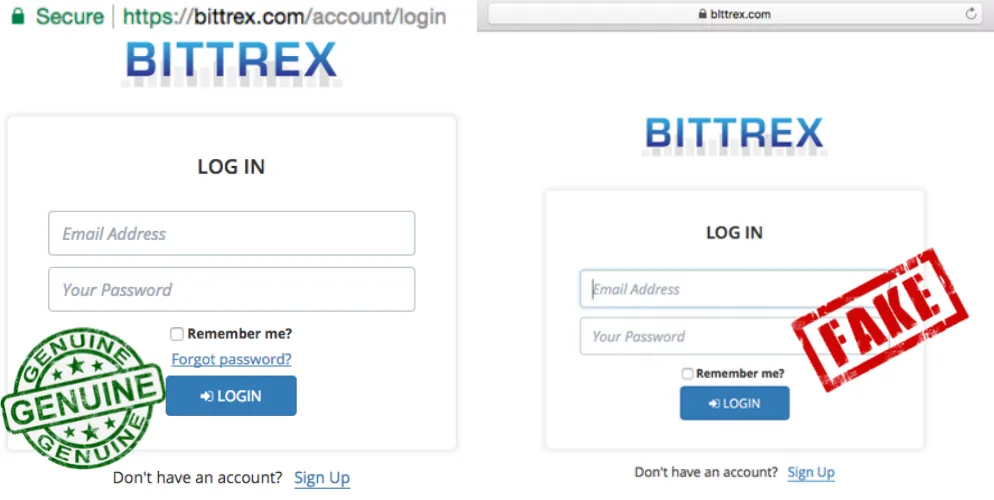
Fake Exchanges
Fake exchanges lure victims by offering attractive rates and services. Once users deposit their funds, the scam operators disappear, taking the money with them.
In 2017, South Korean authorities uncovered BitKRX, a notorious fake cryptocurrency exchange. Named to mimic Korea Exchange (KRX), BitKRX exploited KRX’s reputation to lure investors. Many believed BitKRX was run by KRX, but when they tried to access their funds, they found their money had vanished.
Ponzi Schemes
Ponzi schemes promise substantial returns with minimal risk. Early investors are paid with the funds of newer investors, creating an illusion of profitability until the scheme collapses, resulting in substantial losses for participants.
PlusToken was one of the largest Ponzi schemes in the crypto world. Promising 10–30% monthly returns, it lured over 3 million investors, mainly from China, South Korea, and Japan, using the Chinese app WeChat. The scheme focused on crypto education and a wallet service, convincing investors to buy its token, PlusToken. After a year, the PlusToken team shut down the scheme in 2019, escaping with over $3 billion in cryptocurrencies.

Impersonation Scams
In impersonation scams, fraudsters pose as celebrities or influencers, promising to multiply the cryptocurrency sent to them. Victims are convinced by the seeming legitimacy and urgency, leading to significant financial losses.
In one example, emails were sent to potential victims, offering a $600 return on a $100 deposit. These emails include PDFs promoting Elon Musk’s fake investment platform or inviting recipients to a “community” with an ad featuring Melinda and Bill Gates. The PDFs link to fraudulent news sites.
Malware Scams
Malware scams involve software designed to infiltrate victims’ devices, stealing sensitive information or cryptocurrency. These scams often come disguised as legitimate applications or software updates.

Fake Initial Coin Offerings (ICOs)
Fake ICOs promise groundbreaking projects and high returns. Investors buy tokens in these supposed startups, only for the operators to vanish with the funds raised.
Pincoin, a Vietnamese cryptocurrency, raised about $870 million from 32,000 investors. Instead of cash returns, investors were given a new token called iFan. The team behind Pincoin then disappeared, taking all the invested money with them.

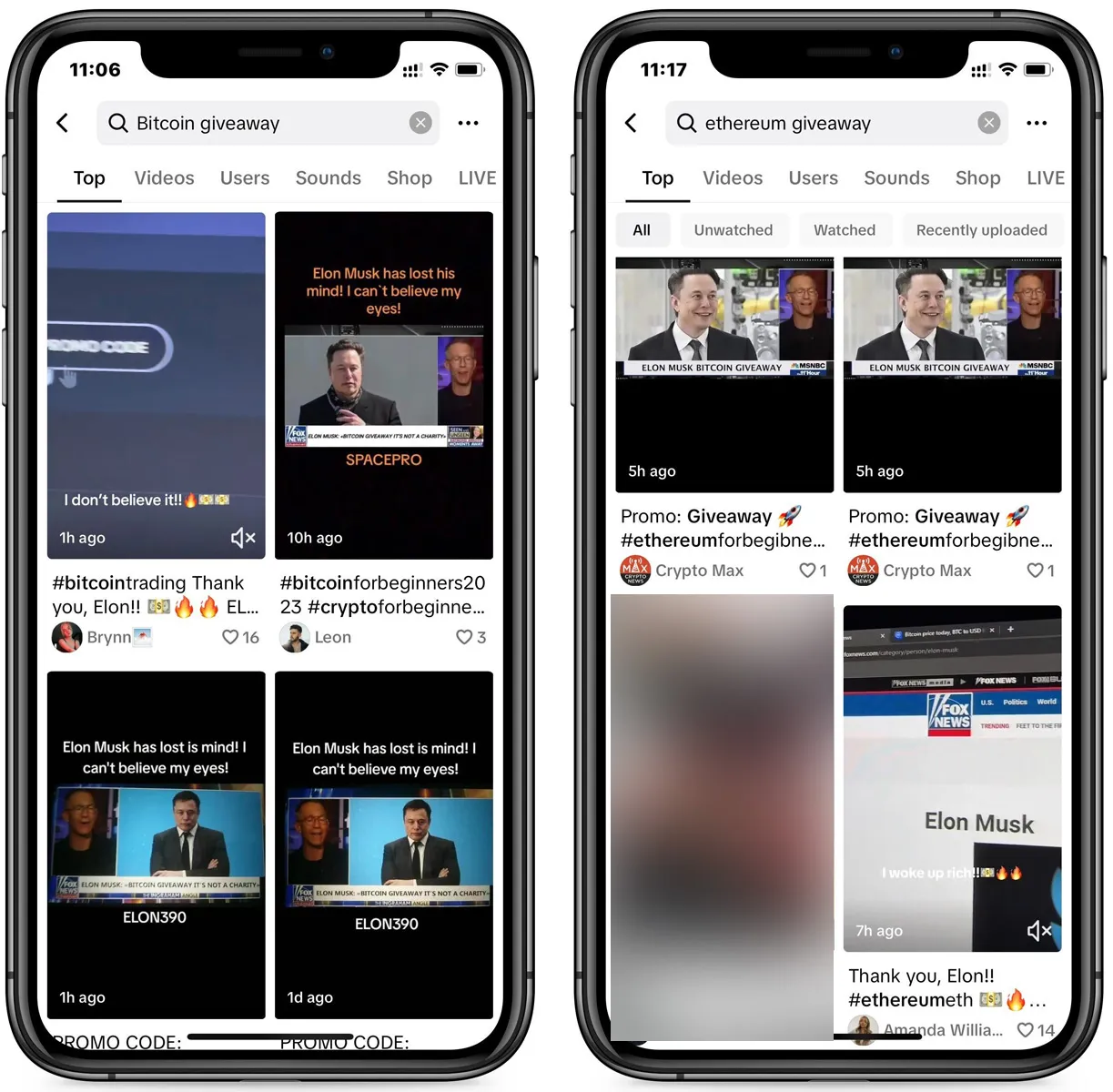
Social Media Cryptocurrency Giveaway Scams
In these scams, fraudsters hijack social media accounts or create fake profiles, promising to double any cryptocurrency sent to them. The allure of easy money draws in many victims who never see their funds again.
Scammers are exploiting TikTok’s popularity with fake cryptocurrency giveaways. These videos, posted hourly, often feature deep fake clips of Elon Musk being interviewed, promoting the scams. Some videos are more basic, showing how to log in to a website and enter a promo code to receive free Bitcoin.
Employment Offers and Fraudulent Employees
Scammers pose as legitimate companies offering high-paying remote jobs. Once hired, they request sensitive information or upfront fees for “training,” disappearing afterward.
Scammers pose as recruiters, posting attractive jobs online or contacting individuals with resumes posted on employment sites. Victims fill out a fake application that requests excessive personal information. Scammers conduct professional-sounding interviews via email or video calls to collect more details. They offer job positions, requesting additional personal and bank information. Occasionally, they ask for payments for training or office equipment, promising reimbursement after work starts.

Romance Scams
Romance scams exploit emotional vulnerability. Fraudsters build an online relationship with the victim, eventually requesting money for urgent expenses, travel, or medical bills, often insisting on cryptocurrency payments. These scams can cause both severe financial and emotional distress.
If you’re unfamiliar with Pig Butchering scams and do no feel like reading my article above, I highly recommend watching “Pig Butchering Scams: Last Week Tonight with John Oliver.”
Source: Pig Butchering Scams: Last Week Tonight with John Oliver (HBO), Last Week Tonight on YouTube.
Major Scam Themes and Their Impact on Consumers
The common thread in these scams is their ability to exploit trust, urgency, and the perceived anonymity of cryptocurrency. Victims often face not just financial loss but also emotional distress and a breach of trust. The anonymous nature of cryptocurrency transactions makes the recovery of funds nearly impossible, compounding the impact on consumers.
Case Study: Bitconnect
Bitconnect is a prime example of one of the most infamous cryptocurrency scams ever. Marketed as a high-yield investment through its “lending program,” Bitconnect enticed investors with promises of substantial returns using a supposedly proprietary trading algorithm. In reality, Bitconnect was a classic Ponzi scheme, where returns to earlier investors were paid using funds from new investors, creating a deceptive appearance of profitability. The scheme unraveled in 2018, leading to a massive loss of $2.4 billion for investors. This case highlights the necessity for vigilant due diligence and robust regulatory measures to protect against similar fraudulent schemes in the cryptocurrency space.

Case Study: $SQUID Token
The $SQUID token serves as a prominent example of the notorious “pump and dump” crypto scam. Drawing inspiration from the popular Netflix series “Squid Game,” $SQUID was marketed as a play-to-earn cryptocurrency, promising its use in a forthcoming video game based on the show. The token’s price skyrocketed to an astounding $2,861, only to collapse to $0 in a matter of seconds. This sudden drop, known as a “rug pull,” occurred when the developers cashed out their tokens, siphoning off $3.3 million from the liquidity pool. Following the scam, the developers vanished, erasing their online presence and leaving investors with significant losses. Despite the initial hype and significant investments, the $SQUID token debacle highlights the importance of caution and due diligence in the unpredictable cryptocurrency market.

Case Study: OneCoin and the ‘Cryptoqueen’
OneCoin, founded in 2014 by Ruja Ignatova and known as the “Cryptoqueen,” is one of the largest cryptocurrency scams. Marketed as a revolutionary cryptocurrency, OneCoin defrauded investors of approximately $4 billion. Ignatova promised a “Bitcoin killer,” luring millions with the prospect of high returns. However, OneCoins were worthless, and investors were left empty-handed. Ignatova disappeared in 2017, and her co-founder, Karl Sebastian Greenwood, was sentenced to 20 years in prison. Ignatova remains on the FBI’s Ten Most Wanted list, accused of multiple fraud charges.
Navigating the Crypto Crime Landscape: Challenges and Strategies for Financial Professionals
As we wrap up our exploration of cryptocurrency crime, let’s reflect on the journey. Part one delved into the dark origins of cryptocurrency, tracing back to Silk Road and Bitcoin’s illicit beginnings. We covered sanction evasion, terrorist financing, child sex abuse material, malware, ransomware, cryptojacking, and darknet markets. Each case study highlighted the evolving tactics of criminals and the relentless efforts of law enforcement to counter these threats.
In part two, we delved deeper into the complexities of crypto-native money laundering, detailing the stages of placement, layering, and integration within the digital currency ecosystem. We emphasized the crucial role of KYC and AML measures in the ongoing battle between regulators and illicit actors. Additionally, we explored various cryptocurrency scams, from IRS impersonations to elaborate investment schemes, each preying on unsuspecting individuals.
Together, these two parts offer a detailed view of cryptocurrency crime’s complexities. The digital frontier, while innovative, also harbors illicit activities due to its anonymity and decentralization, attracting both legitimate users and criminals.
Despite challenges, hope persists with advanced blockchain analytics, compliance measures, and global cooperation proving effective. The takedown of platforms like Silk Road, Hydra Market and many others shows the battle is tough but winnable. The future of cryptocurrency depends on balancing innovation with regulation. Vigilance and adaptability are crucial for financial crime professionals. Our mission: harness cryptocurrency’s potential while combating misuse for a safer financial system.
Explore Next
Master Bitcoin Basics: A comprehensive guide to understanding Bitcoin transactions, manual tracking methods, and tools for tracing illicit value across both virtual and physical spaces. Read on…
Discover how blockchain is transforming industries on the Blockchain Insights Hub. Follow me on Twitter for real-time updates on the intersection of blockchain and cybersecurity. Subscribe now to get my exclusive report on the top blockchain security threats of 2024. Dive deeper into my blockchain insights on Mirror.xyz.