Discover how blockchain is used to trace ransomware payments, uncover threat actor infrastructure, and disrupt cybercriminal networks.
2024 has been marked by several high-profile ransomware cases and investigations, underscoring the growing sophistication, aggression, and unpredictability of ransomware attackers. While final figures for the year are still pending, early reports reveal a dramatic surge in ransomware payments, reaching unprecedented levels. In the first half of the year alone, victims collectively paid an astonishing $459.8 million to cybercriminals. Among these incidents, the largest publicly disclosed ransom was a staggering $75 million, paid by an undisclosed Fortune 50 company to the Dark Angels ransomware group.
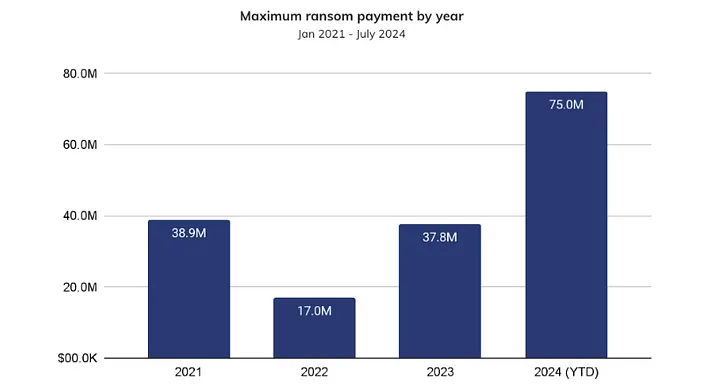
Interestingly, despite a 27.27% year-over-year decline in the number of ransomware payment events, the median ransom payment soared from less than $199,000 in early 2023 to $1.5 million by June 2024. This shift highlights a troubling trend: ransomware gangs are increasingly targeting larger organizations and critical infrastructure providers, focusing their efforts on high-profile attacks that yield significantly higher payouts.
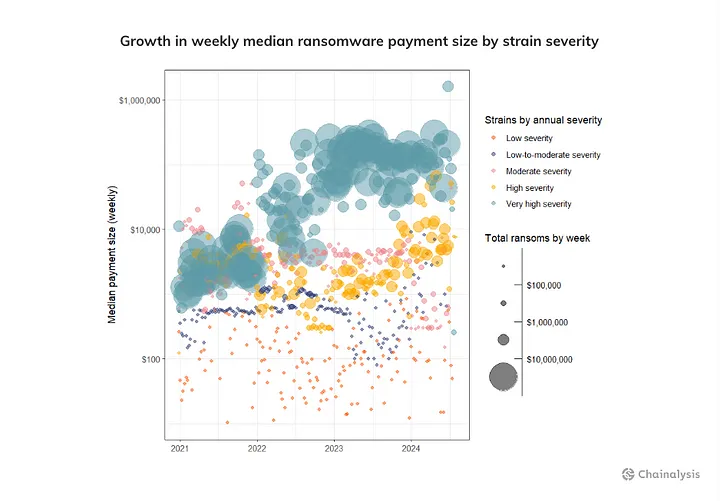
These developments emphasize the urgent need for robust cybersecurity measures and innovative solutions. Blockchain technology offers a powerful tool in the fight against ransomware, leveraging its transparency to trace payments, uncover threat actor infrastructure, and disrupt criminal operations. By employing blockchain analytics, we can illuminate the financial and operational structures of these cybercriminals, aiding efforts to mitigate their impact.
This article explores how blockchain analytics can track ransomware payments, identify the infrastructure supporting threat actors, and ultimately disrupt their operations. At the end of this article, you’ll find a link to Blockchain Investigations Hub a comprehensive library featuring articles and videos on tracking cryptocurrency movements through mixers, bridges, and swaps.
Understanding Ransomware Operations
Delivery
Ransomware is distributed through a variety of vectors, much like generic malware. Modern ransomware campaigns demonstrate increasing sophistication in leveraging existing infrastructure for propagation. For example, the Akira ransomware group, active since March 2023, has targeted over 250 entities across sectors like government, education, and critical infrastructure. Akira operators have notably exploited compromised VPN credentials to infiltrate networks. Similarly, the Cl0p ransomware gang recently exploited vulnerabilities in MOVEit Transfer software, impacting numerous organizations globally. These attacks underscore the evolving tactics of ransomware groups as they capitalize on pre-existing infrastructures to enhance their reach and impact.
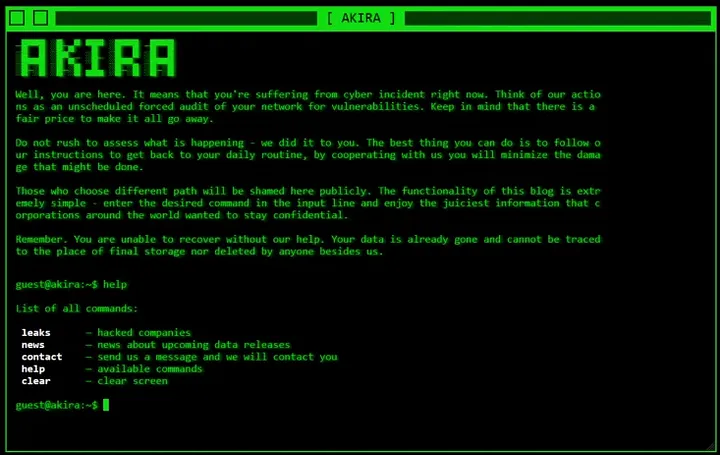
Execution
Once ransomware gains a foothold on a victim’s system, it operates silently, encrypting files deemed valuable, such as documents and images. Following encryption, the ransomware presents a ransom note detailing payment instructions, typically involving Bitcoin. For example, the BlackCat/ALPHV ransomware group is known for its cross-platform capabilities, employing advanced encryption techniques to maximize damage. Ransom notes often include guidance on acquiring Bitcoin and transferring it to designated wallets. This seamless operation and clear instructions contribute to ransomware’s devastating effectiveness.

Payment
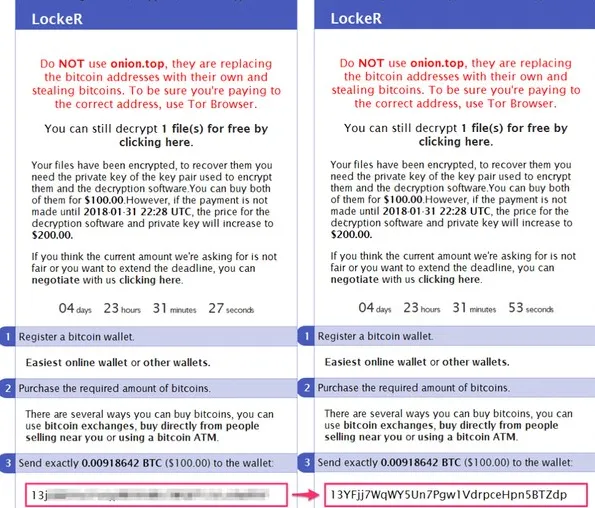
Ransomware payments typically involve Bitcoin due to its wide availability and perceived anonymity. To streamline operations, many ransomware groups generate unique wallet addresses for each victim, simplifying payment tracking and verification. However, some groups opt to reuse wallet addresses, which can complicate the identification of specific payments and may introduce challenges for victims seeking decryption after payment. Regardless of the approach, the trend in ransomware operations shows increasing ransom demands, particularly from campaigns targeting high-profile organizations and critical infrastructure, often leading to multimillion-dollar payouts. These dynamics underscore the need for enhanced tracking mechanisms to disrupt these financial flows.
Liquidation
After receiving ransom payments, ransomware operators often launder the funds through mixers to obfuscate the Bitcoin trails. Mixers intermix flows from multiple sources, making it difficult to trace funds back to specific wallets. Once sufficiently anonymized, the Bitcoin is deposited into exchange wallets and converted into fiat currencies. Law enforcement agencies often rely on blockchain analytics to identify these patterns and trace funds to their eventual cash-out points.
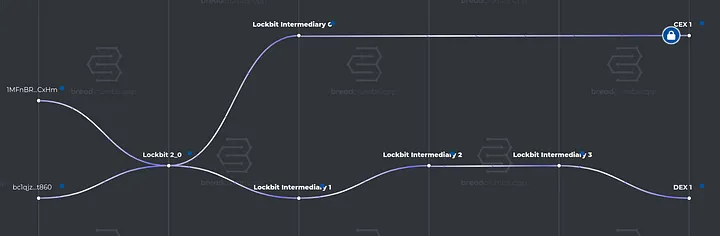
Infrastructure
Infrastructure plays a critical role in supporting ransomware operations, enabling threat actors to carry out attacks efficiently and evade detection. Ransomware groups often rely on bulletproof hosting services to host their malware, command-and-control servers, and dark web portals. These hosting providers offer features such as privacy-focused configurations, fast-flux DNS, and resistance to takedown requests, ensuring uninterrupted operations. This infrastructure is integral for ransomware campaigns, as it supports both the execution and extortion phases.

By breaking down these stages, we gain a clearer understanding of how ransomware operates, from infiltration to payment and liquidation. This knowledge is essential for developing effective countermeasures and leveraging blockchain technology to disrupt these malicious activities.
The Role of Blockchain in Ransomware Investigations
Blockchain technology, with its immutable and transparent transaction records, plays a pivotal role in ransomware investigations. Threat actors leverage blockchain primarily due to its ability to facilitate pseudonymous payments, with Bitcoin being the most commonly requested cryptocurrency. Bitcoin’s liquidity and widespread acceptance make it the preferred choice, though some groups have started requesting Monero for enhanced privacy.
Victims often turn to centralized exchanges and platforms like LocalCoinSwap and the now-defunct LocalBitcoins, which facilitated cash transactions. These platforms appeal to victims who may feel embarrassed or distrust online brokers, offering a more personal option along with seller guidance to help complete ransom payments.
A Yalishanda advertisement on the Exploit Forum highlights their new FastFlux panel with features designed for privacy, security, and evading detection. Source: Recorded Future.
Despite the efforts of ransomware operators to obscure their tracks using mixers, aggregation wallets, and cross-chain swaps, blockchain analytics tools have enabled investigators to trace payment flows effectively. By analyzing these trails, investigators can identify the financial infrastructure supporting ransomware operations, offering critical insights into the global reach and operational tactics of threat actors.
For example, historical trends have shown centralized exchanges like BTC-E, Bitzlato and Chatex served as major cash-out points for ransomware groups until their eventual shutdown. Such cases underscore the value of blockchain transparency in combating ransomware threats.
To learn how to track cryptocurrency through mixing services, watch the video below.
Methodology: Tracking Ransomware Payments
Data Collection
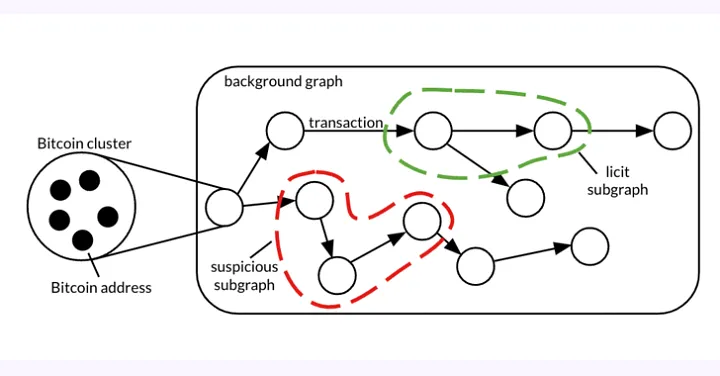
Tracking ransomware payments begins with identifying ransom deposit addresses, which are extracted from both real and synthetic victim methodologies. Real victim data is gathered from reports on public forums, Google searches and specialized platforms, where ransom notes provide Bitcoin wallet addresses. For synthetic victims, researchers execute ransomware binaries in sandbox environments such to simulate infections and extract ransom addresses from memory dumps or visible text in ransom notes. These seed addresses act as starting points for identifying additional addresses linked to ransomware operations. By leveraging clustering techniques and machine learning, investigators can expand their analysis, linking wallets with similar transaction patterns and uncovering broader financial networks.
Visualization and Graph Analysis
Blockchain analysis tools like Chainalysis and BlockSec allow investigators to create transaction graphs. These graphs illustrate payment flows, highlighting intermediary wallets and eventual cash-out points. By clustering addresses and analyzing transaction patterns, investigators can identify key entities within the ransomware’s financial network. Advanced techniques, such as detecting patterns in ransom demands (e.g., fixed amounts like 0.5 BTC) or movement to aggregation wallets, further refine tracking efforts.
Linking Payments to Infrastructure
Ransomware payments often fund operational infrastructure, such as servers or dark web portals. These services, frequently provided by bulletproof hosting providers, offer features like privacy and anonymization, ensuring uninterrupted operations. For instance, providers like Yalishanda and volhav are known to host critical ransomware infrastructure, including malware command-and-control servers and extortion sites. Understanding these links provides critical context for investigators.
Here’s an example involving the Bitcoin address we obtained from a service called volhav. Volhav operates as a provider of bulletproof hosting and offers access to virtual (VPS/VDS) servers in data centers, catering to clients in the criminal underground. The individual behind this service, who goes by the same username, “volhav,” is reportedly known for offering servers that can be used for a variety of illicit purposes, including malware distribution, spam campaigns, DDoS attacks, port scanning, and activities flagged by Spamhaus.

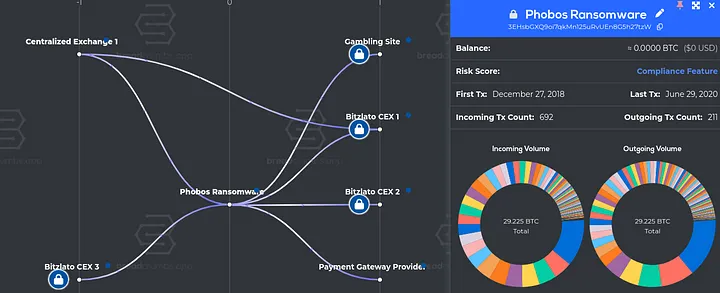
Now, let’s explore an example of what we uncover when we begin graphing and clustering the movement of funds originating from the Bitcoin address 1EdeJDwix3K5GoPoQjiPsgreH2b7Lss4ie.
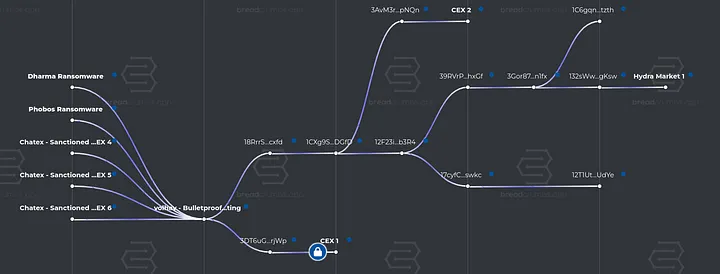
As shown in the image above, mapping and clustering the flow of funds from the wallet associated with “volhav” reveals key insights. We can trace their income sources to malware groups such as Phobos and Dharma, their interactions with darknet markets, and their cash-out points through both sanctioned and non-sanctioned centralized exchanges.
Tools and Techniques for Blockchain Forensics
Blockchain forensics employs specialized tools such as TRM Labs, Elliptic, and Blockchain Intelligence Group to investigate cryptocurrency transactions and uncover illicit activity. These tools offer capabilities like address clustering, tagging, and transaction filtering, which are essential for tracing the flow of funds. Clustering helps link wallets controlled by the same entity, while tagging provides critical context about addresses associated with specific activities, such as ransomware operations or money laundering. Furthermore, these tools enable analysts to identify financial patterns, uncover intermediary wallets, and trace payments to service providers like bulletproof hosting or darknet marketplaces. By leveraging these techniques, investigators can gain deeper insights into the operational dependencies and financial infrastructure of threat actors.
Final Thoughts
Blockchain technology presents a double-edged sword for ransomware actors. While it offers a mechanism for anonymous payments, its inherent transparency allows investigators to trace transactions and reveal hidden networks. By utilizing advanced analytics and specialized tools, we can disrupt ransomware operations and reduce their impact.
If you’re interested in learning how to track cryptocurrency movements, explore my article and video library, which includes modules on:
-
Tracking Cryptocurrency Through Mixers
-
Tracking Cryptocurrency Through Chain-Hopping
-
Tracking Cryptocurrency Through Swaps
-
Using Blockchain to Track Ransomware Threat Actors
Explore Next
Discover how blockchain is transforming industries on the Blockchain Insights Hub. Follow me on Twitter for real-time updates on the intersection of blockchain and cybersecurity. Subscribe now to get my exclusive report on the top blockchain security threats of 2024. Dive deeper into my blockchain insights on Medium.