ok well im busy shipping shit for the night but i’d figure i’d jot some shit down.
it’s insane that we’re all just doing this shit on a giant world spanning interconnected virtual machine and like nobody talks about it like this.

the coolest thing about tying these shittokens to vms is that you can partition out the consequences of your degen behaviour with ponzis to the tokens only instead of your whole pc getting rekt. finances, partioned compute, media, identity defined by these partioned hashed units provide an asymetrical advantage over your centeralized MANGA hashing.
for example let’s talk about Apple’s retarded deep learning cheese pizza detector initiative
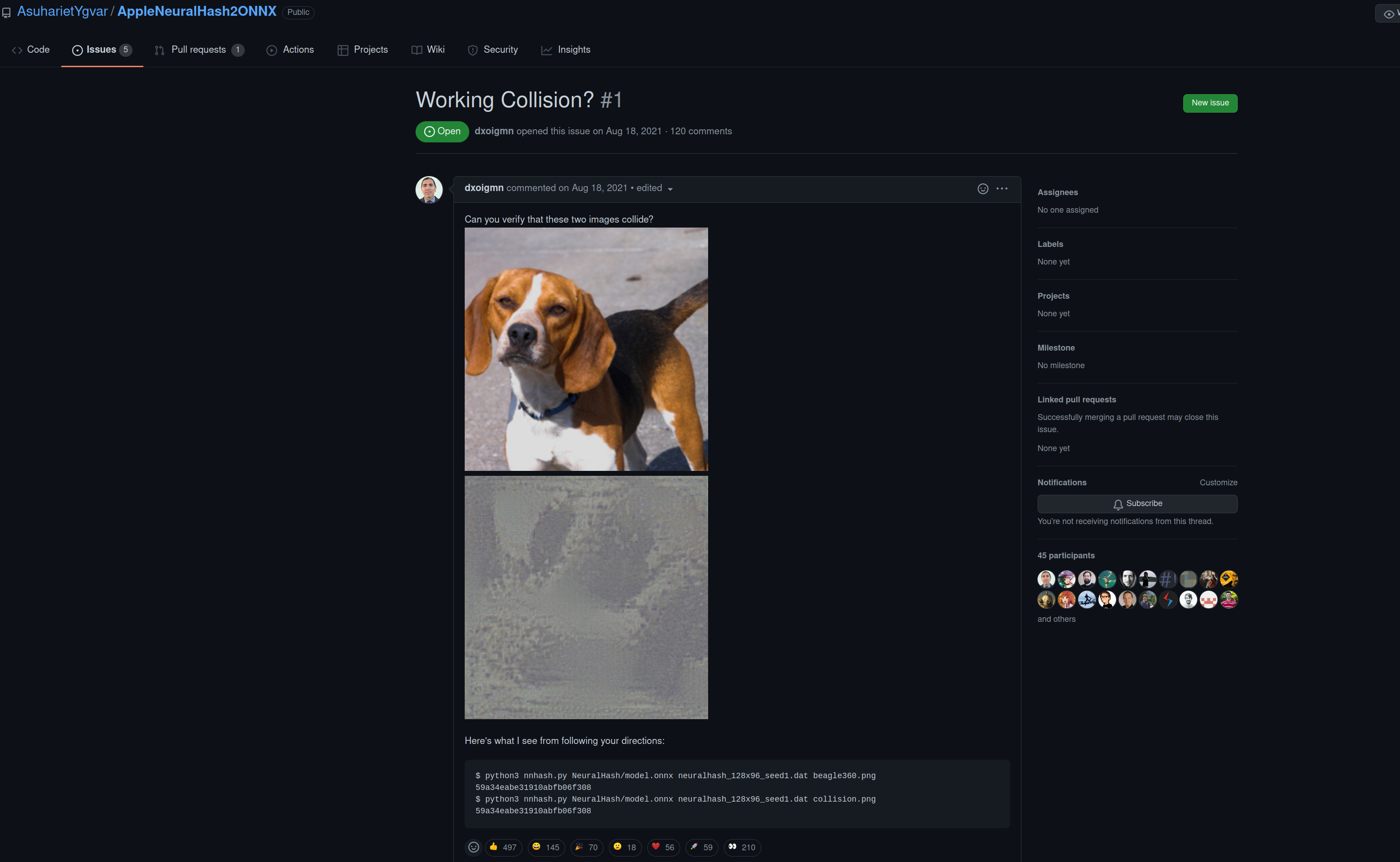
ok so apparently Apple clarified that this is no biggie apparently and there’s a redundant system to filter false positives or something whatever fuck them. the underlying fact is that the privacy preserving veneer that Apple markets is compromised via the means of encryption/hashing and predictive modeling that they hold. a common pattern in this: govermental/corporate entities restrict these means to encryption/privacy preserving tech is appeals to “think of the children”.
ppl are submitting their pictures to be scanned by infinite fucked up python ducktyped ML bullshit or fearmongering about the “dark web” (onion routing used for TOR was literally patented by spooks to feed propaganda to ppl in other countries/siphon data from those same ppl) all for an argument that was funny 25 years ago on the simpsons, but now just tragic. (don’t get me started on how ppl are being basically brainwashed to accept a biofacist panopticon foucalt’s nightmare via obsfucation/ignorance of computation and data gathering)
examples of trust via cryptographic primatives:
mining pools that can generate value decoupled from financial uncertanity or censorship are gonna need error correcting and ways to automate consensus.

ok so merkle trees obviously fall in here too. zero knowledge proofs obviously fall in line with providing trust and uncensorability on an execution level. Privacy preservation are another use case that zks dominate in. hell, zks might be hot but the fraud proofs of optimistic rollups deserve some credit too for being able to break down the bundled transaction to the opcode level and analyze any differences.
Rust safeness/substrate/cosmos interoperability is another avenue that allow asymeterical advantage here. Rust being utilized for these ledgers of computation is very awesome!!! i guess i’m running out of steam here but Rust holds a robust/anti-fragile memory model that alleviates the worries of segfaults/memory bugs for compute intensive processes (such as synching a blockchain or being a client for it or briding cross chain etc etc). WASM and sandboxing of compute intensive/systems level processes in browser are game changers for ppl tired of 69 mb per website js cookie tracking. i guess i can’t really form more words here but i’m really excited for what projects like entropy that are building with substrate will do for trust-intensive custody solutions.
