0. MEV?
Maximal extractable value (MEV) refers to the maximum value that can be extracted from block production in excess of the standard block reward and gas fees by including, excluding, and changing the order of transactions in a block.
a) MEV, Always Here
The ordering of transactions in an Ethereum block is not bound by definite rules from the beginning, but can be freely modified according to miners’ preferences. Three examples are provided in the source code of the Geth client:
-
First: Sorting by Nonce only
-
Second: Sort by gas fee and Nonce (default option)
-
Third: Sort by owner, then sort by gas fee and Nonce
In fact, sorting is a completely open question, and miners are free to adjust it to capture bigger profits, which is the main topic of our discussion, MEV.
Long before MEV was called MEV, its alpha was continuously explored by miners. flashfish0x tells a story of MEV.
Before August 2020, Compound’s oracle feed was updated by a special oracle tx, so miners would monitor Mempool, looking for accounts that could be liquidated and arbitrage them with flashloans and other strategies. Since the arbitrage can only be successful if the arbitrage tx is executed right after the price update tx, and most of the miners (at that time) will randomly order the arbitrage tx with the same gas fee, the arbitrageur will send a trade with the same gas fee as the oracle price update tx, competing against other arbitrageurs for a random probability.
After August 11, 2020, Geth released a new version in which the first tx to reach the network after the oracle price update tx would be successfully arbitrated, so the speed of obtaining tx information was factored into the competition.
It didn’t last long, and on August 17, 2020, Compound switched to a more decentralized oracle service. The MEV race became a pure gas war. They tried to outbid everyone else for gas, until the clearing operation cannot capture any profit, or someone won.
The blockchain network has been such a dark forest from the beginning, where bots compete with unseen rivals for the opportunity to extract potential profits in an unknown environment.
b) MEV, Everywhere
Before formally interpreting the definition of MEV, we can look at some data on MEV so that we can visualize its presence and impact.
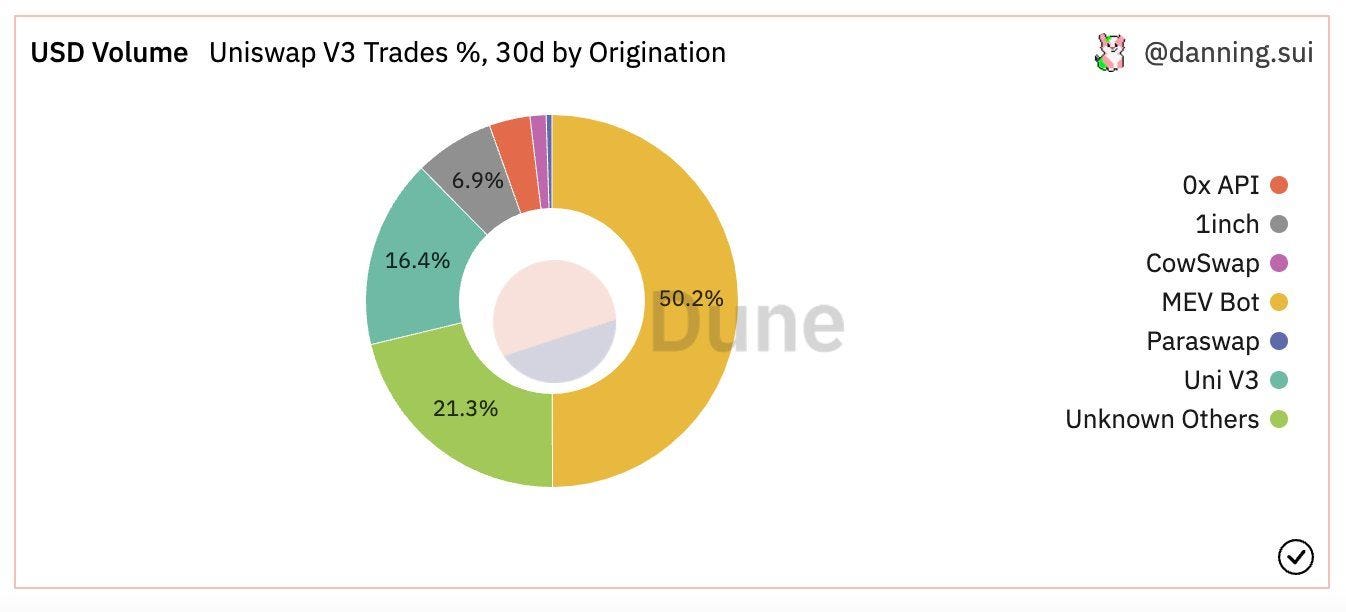
In May 2022, more than half of the volume on Uniswap are contributed by MEV bots, while less than 20% of the transactions come from Uniswap’s front-end.

Data from dex.guru also shows that a large portion of AMM trading volume on Ethereum are contributed by MEV bots.
MEV bots are dominant in the dark forest of the blockchain, and always dominate.
c) MEV Supply Chain
So how does an MEV activity come about?
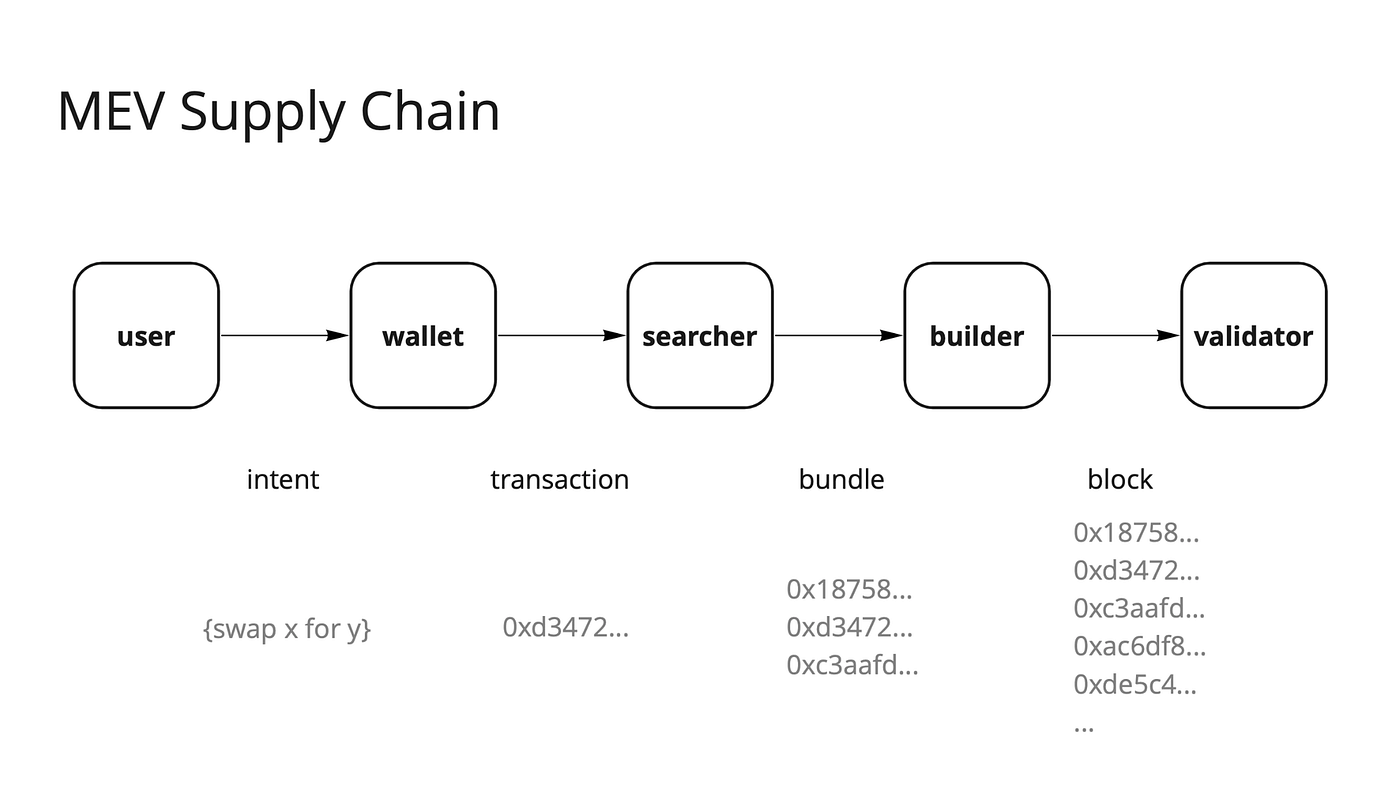
The life cycle of a tx in a crisis-ridden blockchain is as follows:
-
Birth: Ordinary users interact with the application based on intent, and the wallet and application interpret the intent into a tx, which is sent to a public tx pool and other systems waiting to be processed.
-
Growth: MEV searchers (who may be miners) pick out all profitable opportunities and try to capture MEV by sending transactions or deliberately sequencing transactions.
-
Mature: Miners in L1 (who in most cases will not be MEV searchers) or Sequencer in L2 aggregating transactions and producing blocks.
-
Death: The verifier (currently still a miner) verifies the block, and the transaction is officially confirmed.
MEV bots carry out on-chain activities at the whim of their owners, packaging tx and sending them to unsuspecting miners for block production. On the bright side, they are an important player in ensuring market stability and DApp activity; on the downside, they exploit the “average user” unequally with their inherent advantage (they monitor the entire Mempool).
d) Definition of MEV
The term MEV has two official interpretations:
-
Miner Extractable Value
-
Maximum Extractable Value.
When we combine the two explanations together, we get the easiest concept to understand: MEV is the maximum extractable value for miners, which is the incentive for inserting tx in a specific position in a block.
Personally, I think a more comprehensive definition of MEV refers to the maximum value that a miner/validator/bot/oracle/role other than a normal user can extract using extra information from the mining process. Roles that are not normal users (know code, know network mechanisms, know how to use MEV), and profit from their “privilege” to extract additional value, can actually be considered MEV in a broad sense:
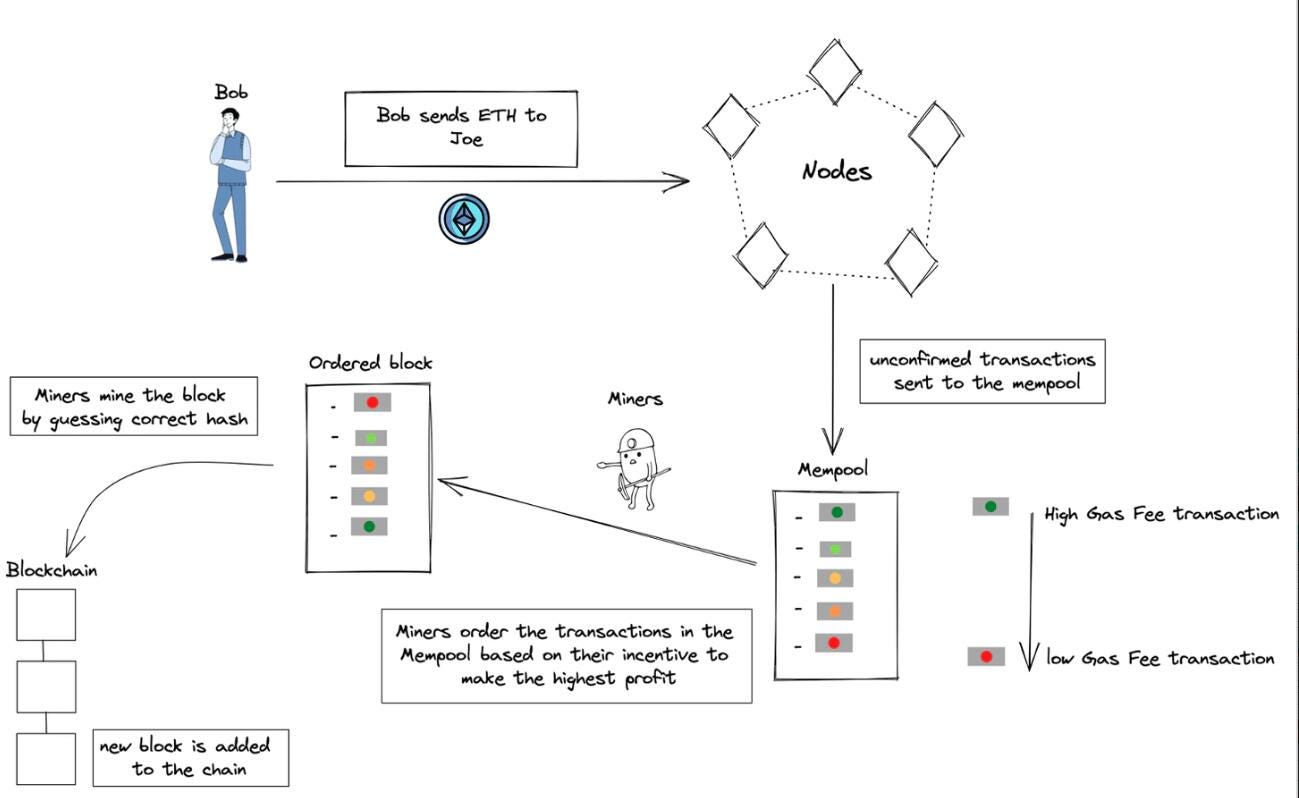
- A miner who is producing the next block: after seeing the transactions in Mempool, when it is his turn to produce the block (a very small probability), he can reorder the transactions in the block as he wishes (instead of the normal nonce and gas fee sorting) with new transactions, thus making a bigger extra profit in addition to the reward.
-
A user who understand the concept of MEV: use Flashbots Protect as tx pool to avoid being rugged by MEV bots and to get the advantage of prioritizing tx execution; monitor Mempool to arbitrage NFT and on-chain activity with flashside or the Compound clearing example in the previous section, with just the right amount of gas fee to allow unwitting miners to capture MEV for them; monitor Mempool to mint the latest NFT projects via mint.fun.
-
A ordinary user: woke up in the morning to buy ETH, but the first tx failed due to insufficient gas; the second tx was successful at noon but was rugged by the sandwich; stayed up late at night to mint a long-favored free mint NFT, but the trade was monitored by others just before it was sent out, and eventually it was not minted.
MEV extractors derive their additional profits from other transactions within the block (almost exactly what ordinary users send) and crowd out a portion of each block (despite the inelastic demand for gas fees, their transactions are usually the first in the block and do not directly affect user tx), so most MEVs are often seen as an implicit tax placed on users.
1. Difference in MEV
Here is a clear illustration of the MEV activity by 0xminion:
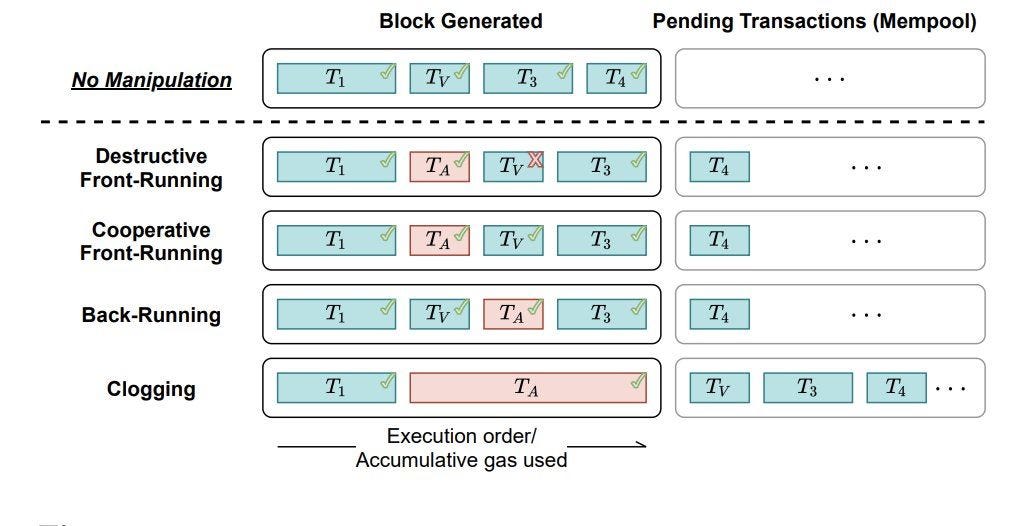
In terms of purpose, MEV can be divided into: various types of arbitrage, pure front running, sandwich attacks, etc.
Most of these operations will be arbitrage activities, which are basically initiated by bots that have made a lot of efforts to optimize the gas, for example, they usually have numerous tokens in their wallets, each with a small amount. This is mainly by using EIP-2200, when the user receives an ERC-20 token, if the token is in the wallet, it saves more gas than if it is not. Also they save gas by making the address have more zeros. Of course, the above arbitrage optimizations have little to do with MEV itself.
MEV itself can be divided into six main types:
a) Front Running
Front Running is an MEV bot that pays a slightly higher gas fee to execute a transaction before a Mempool transaction, such as swap tokens at a lower price.
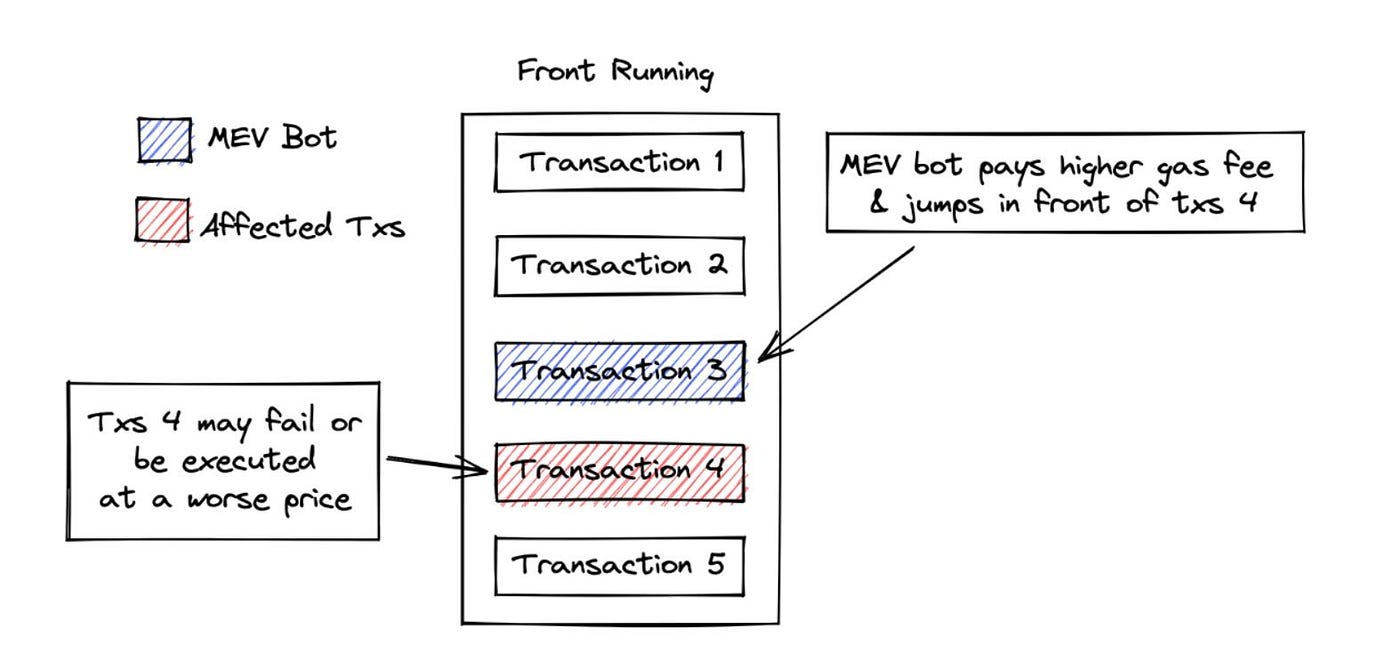
When such MEV activity does not cause subsequent “casualties”, it can be considered neutral (not benign because it is still mostly interjected); however, many times it usually causes subsequent transactions to fail or perform worse, and thus can be considered malicious.
There are currently many services that focus on improving the capture of such MEVs, such as bloXroute (similar to the mafia’s protection fee to provide faster and more private Mempool, thus speeding up tx validation efficiency and defending against external Front Running defense).
The heart of the matter is that these MEVs are a direct reflection of the information inequality between MEV catchers and ordinary users. However, it is not possible to reach a completely open, transparent, and uniform consensus on the way transactions are sorted and the algorithms used.
b) Back Running
Back Running is when a robot attempts a different arbitrage, liquidation, or trade after a tx has caused a significant price misalignment.
The most typical example of this type of MEV activity is the liquidation arbitrage operation we mentioned earlier, which can be considered benign overall, ensuring the stability and continued functioning of the market.
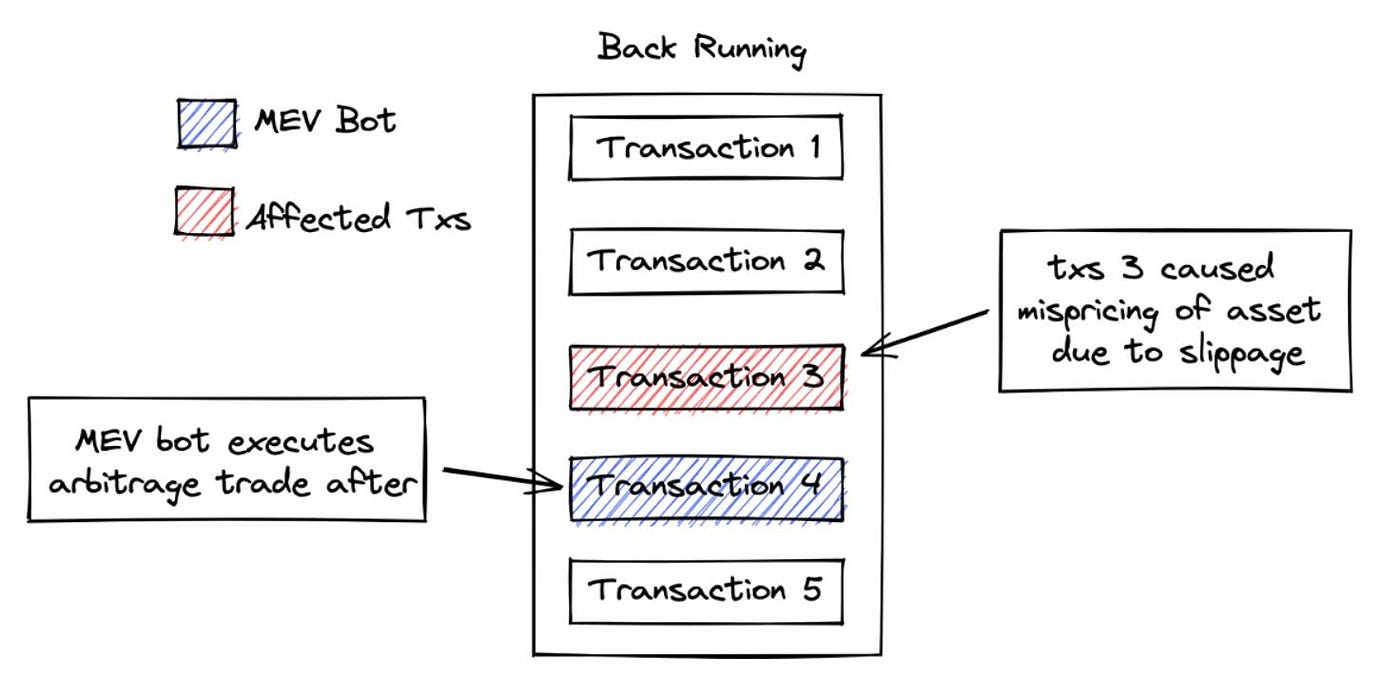
This kind of MEV activity is especially good on a network with a multi-chain architecture like Cosmos, because the network is very large and needs this kind of activity to keep the DeFi application running and efficient at all times.
c) Sandwich Attack
Sandwich Attack is a combination of the first two attacks, attacking a transaction in a back-and-forth manner. For example, the MEV bot places a buy order before the tx and a sell order after the tx, causing the user’s tx to execute at a worse price.

Such attacks can sometimes be very sophisticated and can do a lot of damage, as shown in the image below, which shows a bot sandwiching Curve’s users with 100 million DAIs:
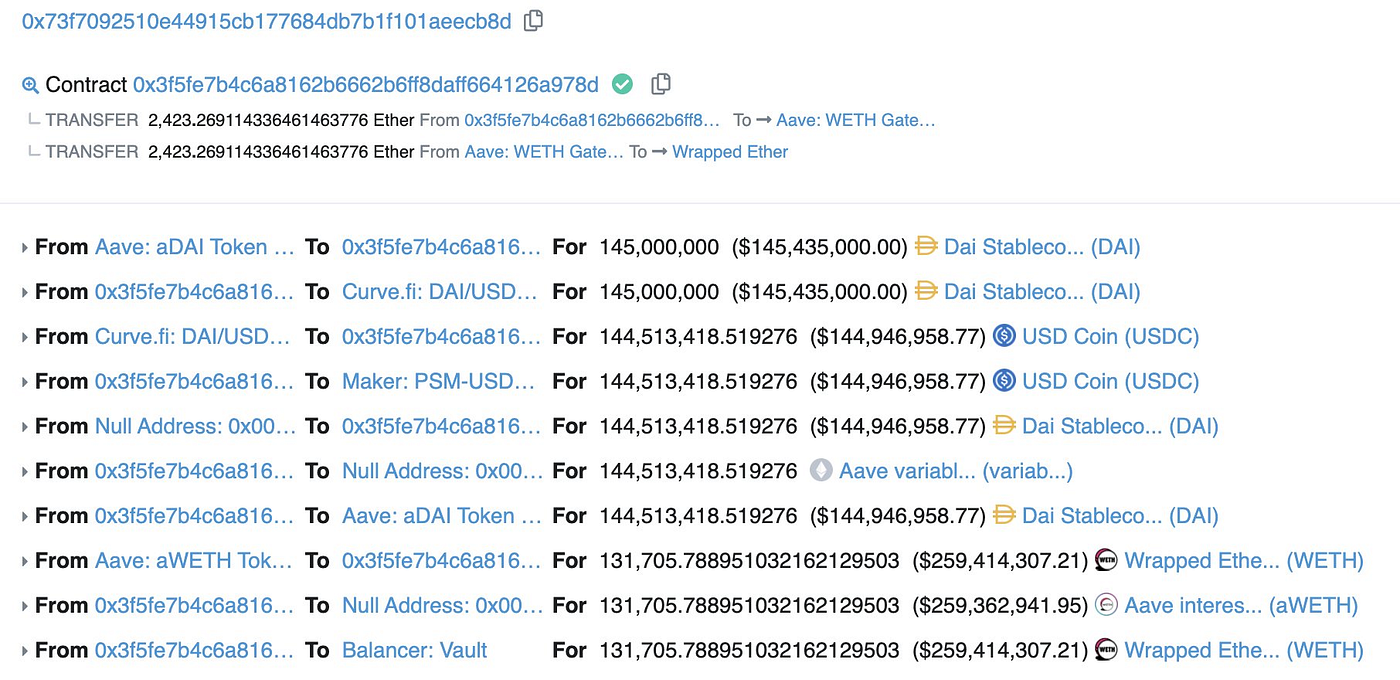
It can be generally perceived as pernicious, but somehow acts like a speedometer on the highway to spur users to use more sensible slippage, thereby enhancing the overall benefit of the network.
d) Time-Bandit Attack
A time thief attack is when, after a block has been generated, a miner re-mines the block causing the blockchain to reorg, while extracting value from the block he mined. This is the most pernicious form of MEV, invalidating user transactions. At the same time, it is rare, but it can happen.
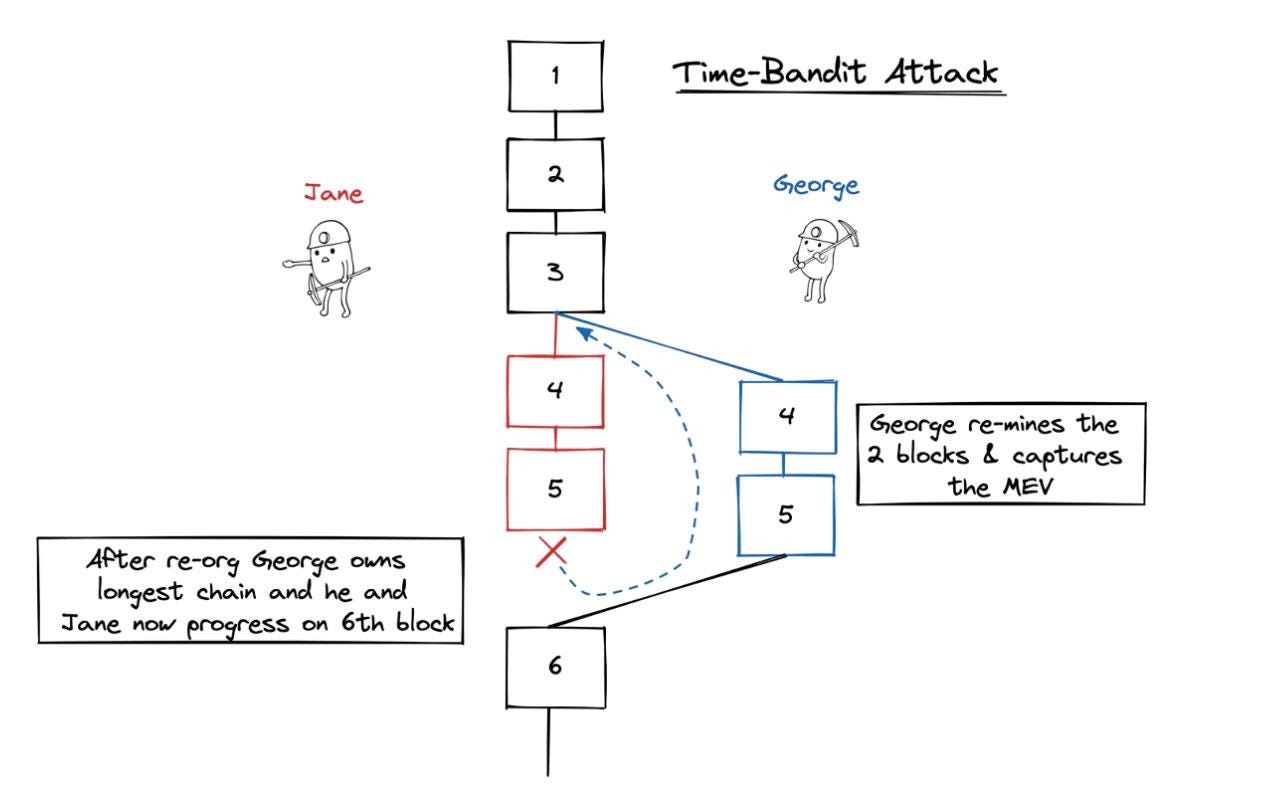
The blockchain network under Nakamoto consensus has very frequent block reorg (and high latency) due to the longest chain principle, so this kind of MEV is likely to be caught. In Tendermint or PoS ethernet, the occurrence of such MEVs will be greatly reduced.

The cool point about Time Thief MEV is: future events can affect the past (like including “future” transactions into blocks of the “past”).

However, under simple quantification, the expected payoff of such attacks is low, and they are rarely performed as they are condemned for deliberately destabilizing the blockchain network (e.g. Reorg-as-a-Service).
e) Clogging
The validity of any NFT, Asset, and Rollup transaction is actually guaranteed by purchasing a space in a block on the blockchain network. The following is the supply and demand in the blockchain block space market:
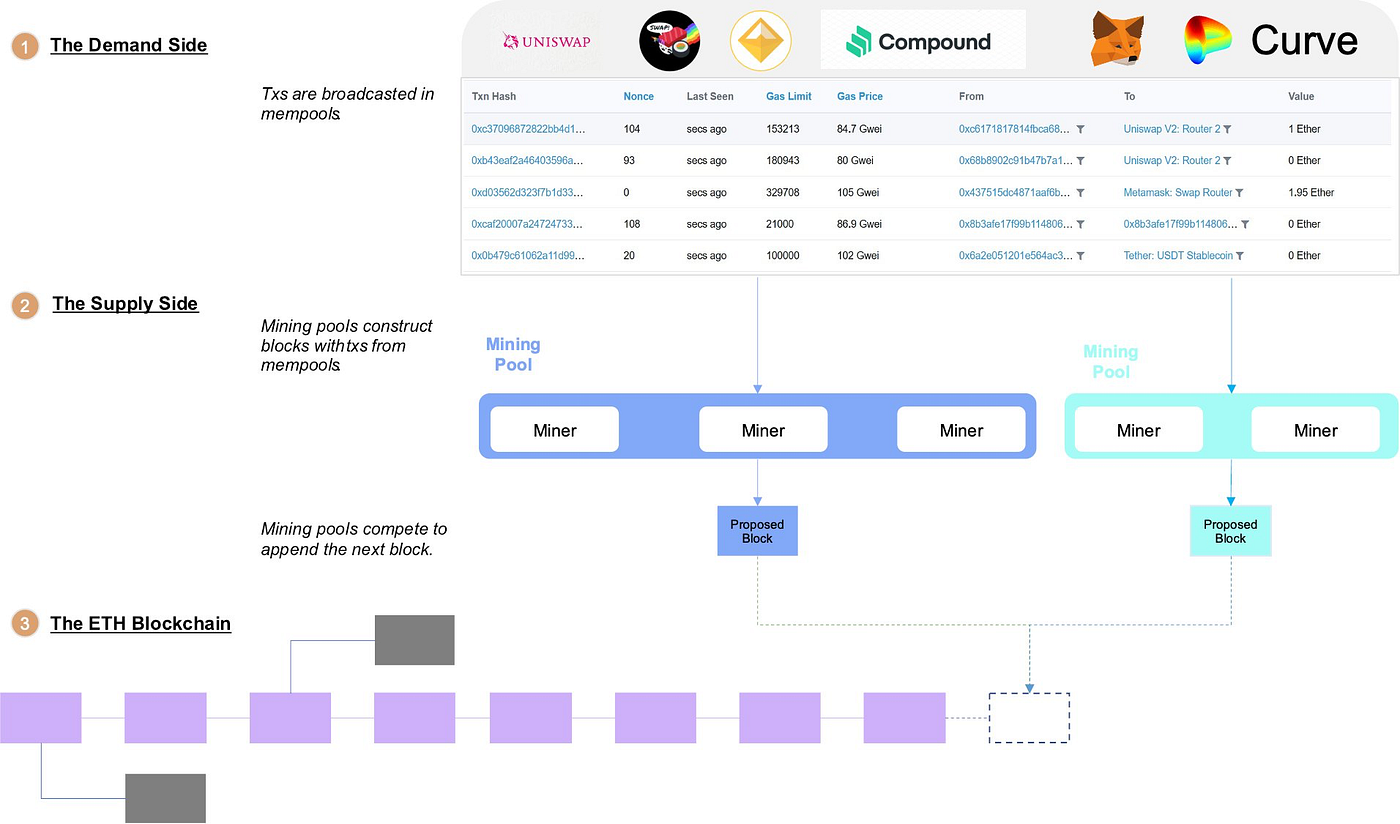
Clogging is the process of continuously monopolizing all the space in a block for winning a game such as Fomo3D.
Remember the Geth source code at the beginning? Clogging was created because about 70% of Ethereum miners sort their transactions based on the default gas fee sort.
But for now, because of the complete infrastructure, such as oracles and Rollup, which submit transactions rain or shine, it would be more expensive for MEV bots to do so during active network periods.
f) Non-Broadcast Transactions
The previous types of activity are basically initiated by MEV bots, not by block miners themselves.
Non-Broadcast Transactions are tx’s that are secretly submitted by the current miner, i.e. when the miner knows he can make a block, he instantly plugs some transactions into the block to capture the MEV.

About 2% of all transactions on Ethereum are generated in this way.
2. MEV, Good or Bad?
In the previous analysis we looked at the different types of MEVs, interspersed with our evaluation of each and our judgement of whether they are good or bad. So overall, are MEVs good or bad? What should we do about it? How do different networks respond to it in different ways?
Good and bad MEV:
-
Good MEV: Used for arbitrage clearing (Back Running), open and transparent markets (Flashbot, MEV Auction), and does not affect the network or other users.
-
Bad MEV: Used to extract value from other users (Sandwich Attack), sent privately and not broadcast (Time-Bandit Attack, Non-Broadcast Transactions), affects the normal operation of the network (Clogging).
MEVs seem to be a neutral player in terms of simple classification, but when considering the nature of MEVs (incentive to insert tx into blocks), this incentive is too large and can lead to chasing bad MEVs causing much more harm than good MEVs. In addition, MEVs also arise from the inequality of information and knowledge, where there is only equality and no equity in the blockchain network.
MEV is bad, and needs to be decreased.
3. MEV Decrease Strategy
Before discussing strategies for MEV, we need to be clear that information asymmetries and externalities cannot be completely eliminated in any context, but we can only deal with them in a better way.
a) Fix the MEV black market and its huge incentive
MEV is a black market (or dark forest) created by opaque information and knowledge, a black market that generates huge profits. It is through this lens that we will consider strategies to target the MEV.
The black market valuation of the entire world is about $180 million, and is a necessary evil that cannot be eliminated. The market for MEVs is also much larger than we can observe.
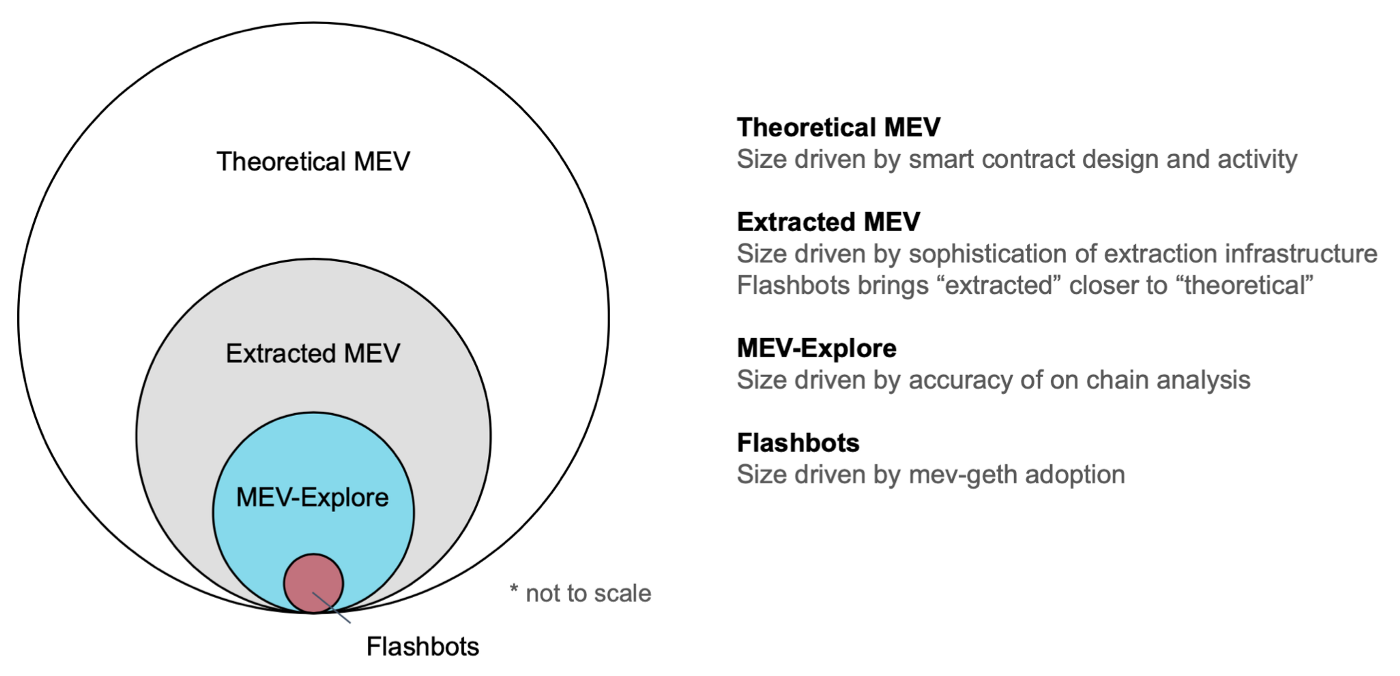
Since this black market is inevitable, why not expose it to the light of day and allow everyone to freely capture and protect their own MEV, so that the average user can create a synergy and weaken the MEV catcher against the user.
Flashbots has proposed the following five marketplace solutions to limit MEV extraction, thereby reducing the overall negative externalities of MEV:
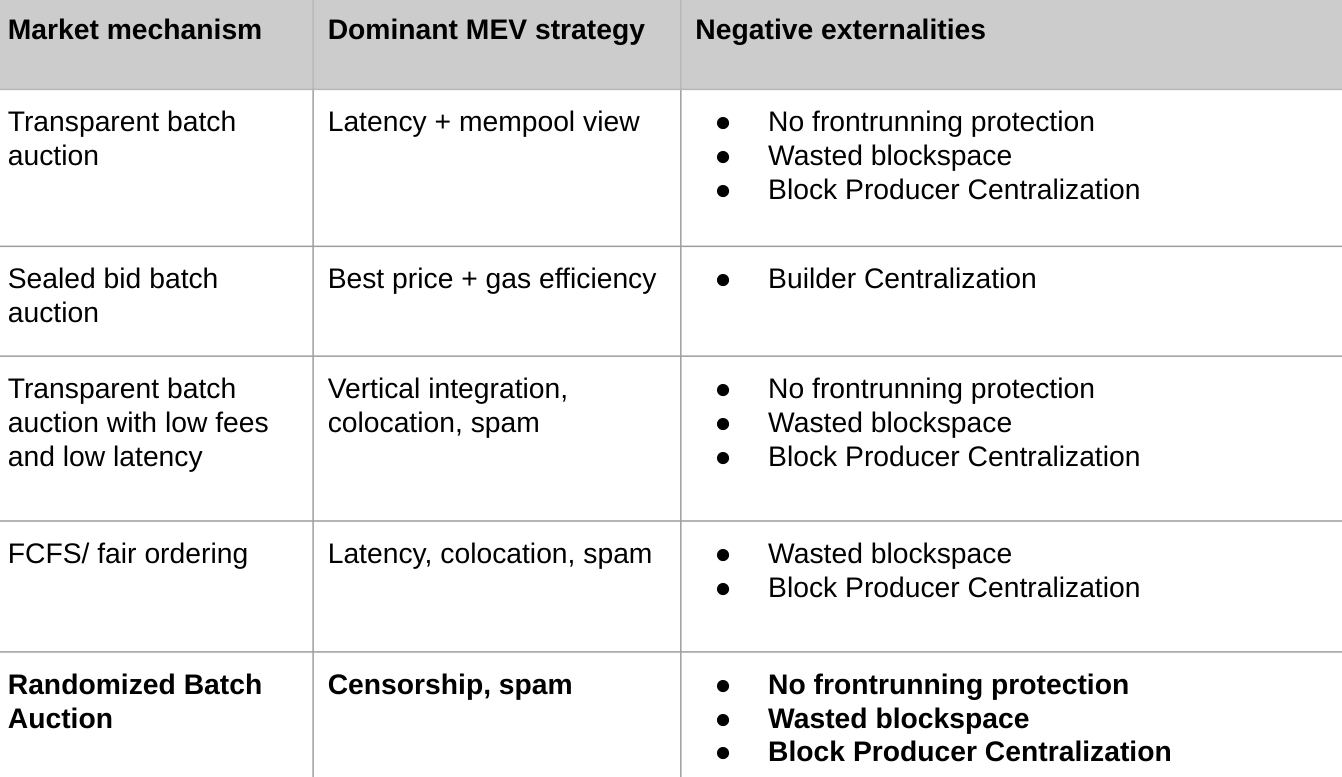
These MEV reduction schemes are actually similar, but the same drawback is that they may lead to wasted block space and centralization of block production.
b) Complexity of MEV: Scenario Difference
-
Single-chain scenario: Most of this paper is devoted to MEV in a single blockchain network, which in reality is an overly idealized analysis.
-
Cross-chain scenario: One blockchain network = one trust zone. In reality, there are countless blockchain networks with different mechanisms and different types of MEV, and these countless trust zones allow arbitrage between networks to exist everywhere. For example, even if Ethereum has no MEV at all, if there is an arbitrage opportunity on Cosmos, then a bridge verifier or cross-chain application bot can capture MEV on Cosmos, and eventually Ethereum becomes a victim of this MEV.
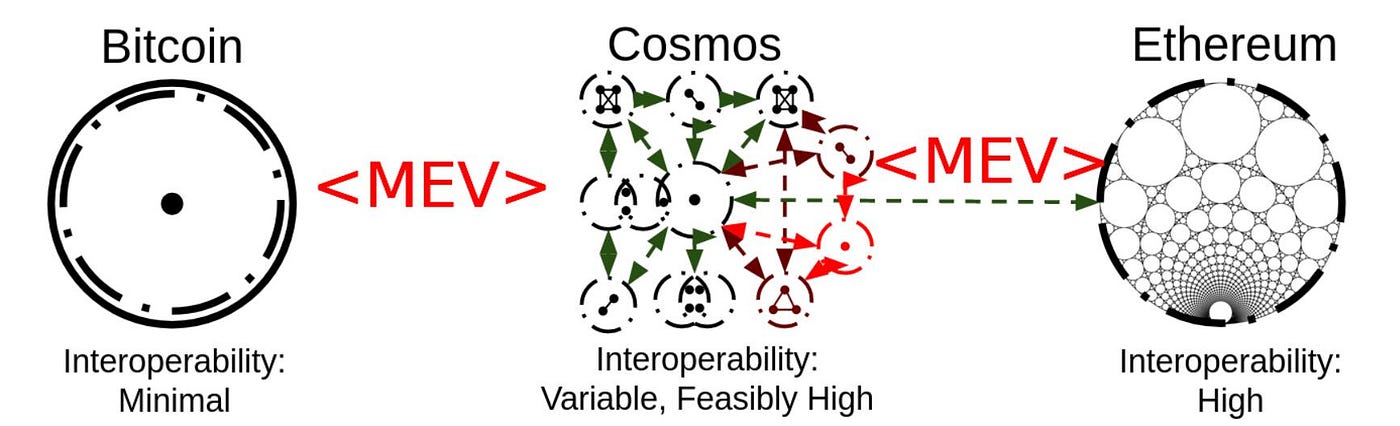
- Multi-chain scenarios: Examples of cross-chain scenarios can be seamlessly applied to Cosmos or Polkadot multi-chain architectures, where the presence of MEV is contagious.
b) Complexity of MEV: Network Architecture Difference
In our article exploring Rollup networks, we learned about the difference between a monolithic Layer1 and a Layer2 Rollup built on top of it.
1. Rollup
Rollup as an “enhanced smart contract” and a “centralized trusted blockchain network” both currently have a centralized block producing and sequencing mechanism, and therefore have different MEV performance. The current centralized Sequencer (i.e., only one node) results in all MEVs being captured by Rollup. As more and more liquidity and on-chain activity is transferred to L2, the revenue available to L1 miners (including MEV) is actually transferred to L2’s Sequencer.
Of course, the Rollup networks themselves are aware of and have solved this problem, and their fair ordering of tx reflects the treatment of MEV. Different Rollups have different strategies for MEV, which means completely different things to the network participants:
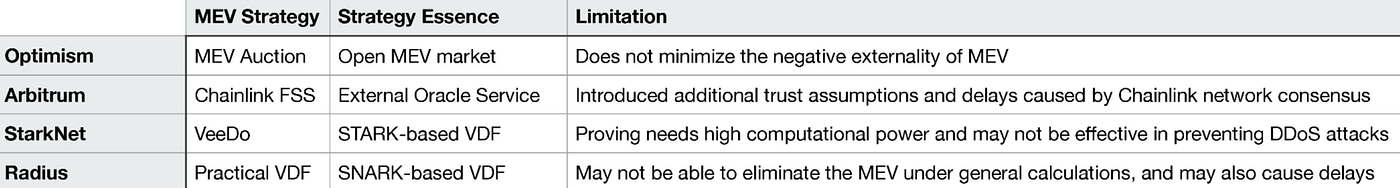
As L2 moves towards decentralization and modular blockchain implementations become more prevalent, the issue of MEV requires more research and thought. For example, the modularity landscape of Ethereum and Celestia will be different. Currently, Rollups on Ethereum are Secured Rollups, which simply build n two-way trusted cross-chain bridges (their job is to build such bridges), which are jointly settled on Ethereum, Whereas the Sovereign Rollup encouraged by Celestia is separate, with likely different DAs, and may require n² bridges or a protocol like IBC or XCM to fully connect. This creates a completely different MEV market and capture opportunity.
From the L2 MEV problem, we can also derive the L1 and L2 thinking about the value relationship, which will not be expanded in this paper.
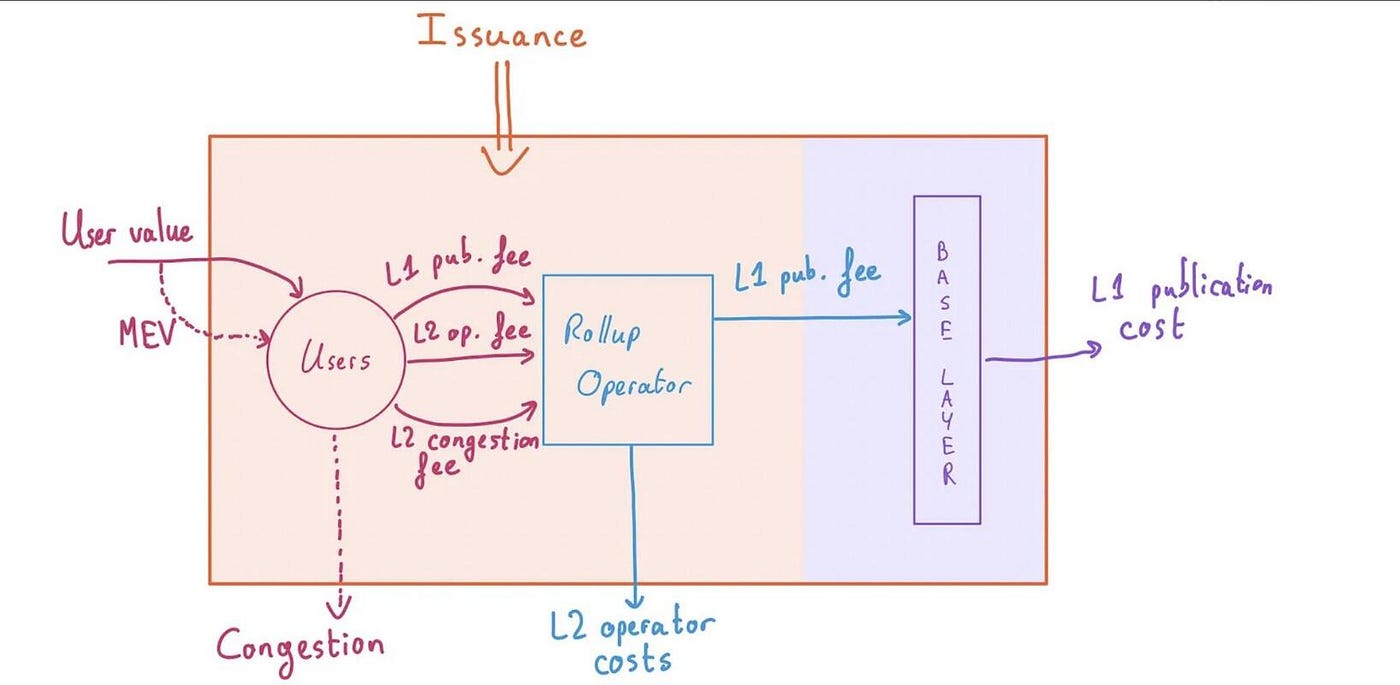
2. More centralized blockchain
To make it faster, Solana doesn’t have a public Mempool, but rather a Mempool via a Gulf Stream that only miners who are expected to be producing block can see (which is why it’s down…). This means that the MEV Bot has no way to capture MEV, only miners running a Validator and expecting a block to come out would theoretically have the opportunity to sort transactions or send new ones to capture MEV. But combined with the low profitability of Solana’s miners, this design actually results in lower income for miners. So now Jito Labs is making a client like Flashbot’s mev-geth to allow miners to auction off their block space, creating an open free market for MEV. Solana also has solutions for QUIC and per account fee market.
3. Conclusion
This article is only a superficial analysis of the topic of MEV, there are many interesting things not mentioned due to space (SGX, PBS, etc.), we recommend you to read more than 50 related links at the end of the article.
In an ideal network:
-
Anyone can send transactions (no censorship)
-
no spam
-
Very low fees(low fees)
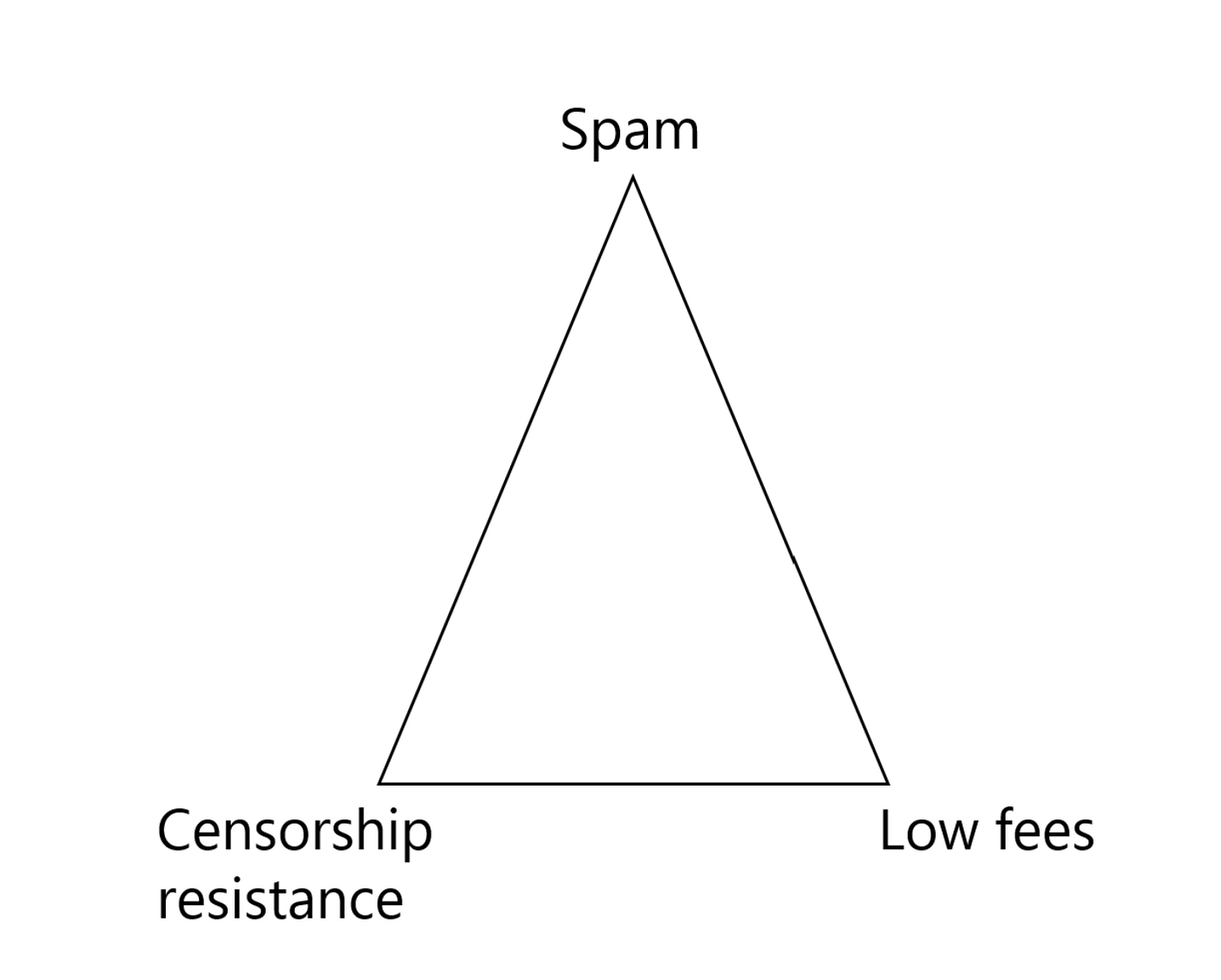
And the existence of MEV makes it impossible to reach the perfect state:
-
no spam + low fees: Web2-like censorship must exist.
-
no censorship + low fees: MEV Searcher will send spam and make normal transactions affected.
-
no censorship + no spam: You need a rate market to sort transactions, and you need higher gas to prioritize transactions.
But don’t worry too much, Web1 or Web2 or the real world haven’t solved the negative externalities of “MEV”. Web3’s various solutions have already done a great job. MEV has always been an open problem, and there is no completely correct solution.
So what do we in Web3 do?
-
L1/L2: Design with MEV in mind.
-
Miners: feel free to capture value, as this is a part of network game theory.
-
DApp Developers: Design applications with MEV concept in mind, and whether the mechanism will hurt the average user.
-
Users: Understand MEV, and try not to use networks or applications with inadequately designed MEV mechanisms.
-
Others: Encourage MEV research, participate in MEV discussions, Front run the crisis.
Links
0a:
0b:
0c:
0d:
1:
1a:
1b:
1c:
1e:
1d:
1f:
2:
2a:
2b:
3a:
3b:
4:
Not Included but Recommended to Read:
