Written by Bernardo Magri - Primev Chief Cryptographer
mev-commit empowers MEV actors to securely share transaction execution details through a p2p network
In Ethereum and other decentralized blockchains, users engage in a continuous auction for block space, attaching a "fee" amount to transactions to signify their willingness to pay a service provider for inclusion in a block. This auction persists throughout each block slot. mev-commit enhances this process by introducing a protocol where execution providers can issue credible commitments for inclusion and other execution needs in real-time, allowing users to have guarantees backed by provider stakes and reputation.
More specifically, mev-commit establishes a P2P network among mev actors, enabling the secure sharing of transaction execution details within Ethereum's proposer-builder separation (PBS) auction. This platform allows execution providers, such as rollup sequencers and Ethereum's block builders, to openly issue execution commitments to users in a decentralized network. While promoting transparency, this setup presents a risk: rival providers could leverage the shared execution details to deduce the value of competitors' blocks in comparison to their block bid. This delta serves as their profit margin, providing a strategic advantage in the bidding process.
Example Scenario:
-
Provider A constructs a block valued at 5.
-
Provider B constructs a block valued at 10.
-
If Provider B knows Provider A's underlying block value, it can strategically outbid A every time by simply bidding 5.1, rendering any higher bid from A economically unfeasible.
-
Without this knowledge, Provider B must employ a different bidding strategy that is not reliant on the knowledge of A's block value.
Currently, providers can query market bids from relays but lack real-time information about the transaction components that form a competitive block bid. One of mev-commit's objectives is to facilitate sharing the status of these transaction components over a P2P network to relevant parties without inadvertently leaking sensitive information.
Privacy Measures:
-
To counteract the risk of information leakage, MEV-Commit introduces a privacy-preserving commitment protocol.
-
This protocol allows parties to privately communicate execution commitment details during a specific block slot.
-
Other network participants can only view commitment details after the slot has concluded, maintaining third parties’ ability to ensure decentralized fund settlement.
By implementing these features, mev-commit successfully balances the need for open communication with the imperative for privacy and competitive integrity. We give an overview of the cryptographic protocol that allows for this setup below.
Protocol Overview
mev-commit integrates a protocol designed to safeguard the confidentiality of provider commitments while ensuring reliable communication within the network:
-
Providers signal their acceptance of a bid to the network through a non-interactive commitment scheme. This process involves committing to a bid that a user has previously broadcasted across the network.
Concurrently, the provider generates a time-lock puzzle embedding the commitment's opening information. This puzzle serves as a contingency, activating only if the provider fails to relay the opening information to the network after the slot is over—a scenario that might arise from malicious intent or a DoS attack on the provider.
-
To communicate a bid’s acceptance to a user, the provider encrypts the commitment's opening information using the user's public key, based on a specific public-key encryption (PKE) scheme. To prevent any association between the public key and the ciphertext, which could inadvertently disclose details about the accepted bid, it is imperative that the chosen PKE scheme is anonymous, as defined in [BBDP'01].
The protocol encapsulates the commitment process in a triple: , representing the non-interactive commitment, the time-lock puzzle, and the encrypted bid information, respectively. The provider authenticates this triple with their signature and broadcasts both the message and its signature across the gossip network. Subsequently, a settlement layer and then the user can retrieve the message from the network, completing the secure communication cycle.
This structured approach ensures that while the provider's commitments are securely communicated and verifiable, the privacy of the commitment details remains intact until the appropriate phase of the settlement process.
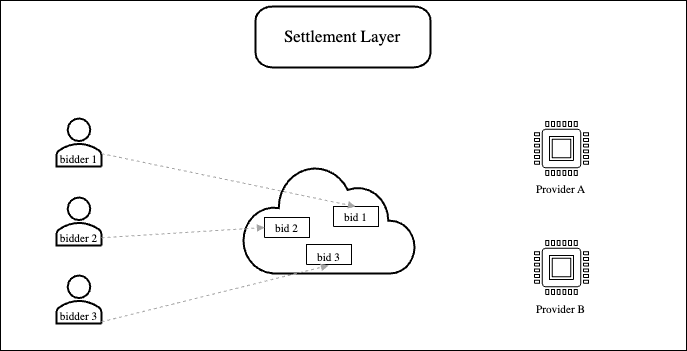
Figure 1: Users broadcast their bids to the gossip network so that providers can see all the bids.
In Figure 2 below, provider A accepted bid 1 from bidder 1. For that, provider A produces the non-interactive commitment and time-lock puzzle containing the information about the accepted bid. At the same time, provider A encrypts the accepted bid using the associated public-key of bidder 1. The non-interactive commitment, the time-lock puzzle, and the ciphertext are denoted by the triple that is signed by the provider (producing ) and broadcast to the gossip network. Eventually, the message is picked up by bidder 1 and the settlement layer.
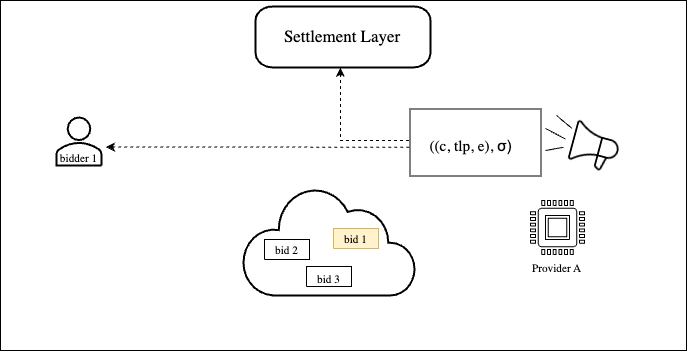
Figure 2: Provider A accepts a bid and broadcasts its privacy-preserving commitment.
Conclusion
We are excited to incorporate and leverage this simple yet effective cryptographic protocol for enabling privacy-preserving, real-time commitments over an open p2p network. We believe its applications will span beyond mev-commit, and it can become a standard for privacy-preserving commitments across domains. We plan to publish additional blog posts that delve into the use cases of this protocol in the latest research areas of Ethereum. Furthermore, we will explore future directions and potential enhancements and optimizations for the privacy-preserving commitment protocol.
We will be releasing more on mev-commit soon, including a live testnet that demonstrates its capabilities. Stay tuned for updates, and reach out to collaborate on how mev-commit can enhance your mev use cases.
This is the start of a series of writings from the Primev Cryptography Research team. We thank researchers across the ecosystem who have provided feedback on this post.