Identity as a Sovereign Asset: The ARPA Live ID and the Next Economic Paradigm
Executive Summary
The prevailing models of digital identity represent a systemic liability, architected for an era of centralized control that is now dangerously obsolete. This report posits that the foundational concept of identity is on the cusp of a radical transformation, moving from a commodity to be extracted and controlled by corporations and states to a sovereign, productive asset owned and managed by the individual. This transition is not merely a technological upgrade; it is the next great economic paradigm shift, poised to unlock unprecedented value and redefine the relationship between individuals, data, and the digital economy.
This analysis traces the genealogy of identity as a technology of power, from its earliest forms as physical markers of trust to its modern incarnation as a tool of mass surveillance and behavioral prediction. It provides a clinical diagnosis of the current system's architectural failures—a fragmented, insecure, and user-hostile landscape built on centralized models that treat human identity as raw material for the surveillance economy. The inherent vulnerabilities of this paradigm, from catastrophic data breaches to the erosion of personal autonomy, have created an urgent and undeniable need for a new foundation.
In response, this report architects a new model, using the ARPA Live ID as a comprehensive framework for a decentralized, self-sovereign future. This paradigm is built on a crypto-biometric synthesis, fusing the mathematical certainty of blockchain-based verifiable credentials with the undeniable proof-of-personhood offered by advanced biometrics. This foundation gives rise to the Digital Twin: a high-fidelity, real-time virtual model of an individual, composed of their verified skills, experiences, and data streams.
The report's central thesis is the evolution of this passive Digital Twin into an active ARPA Agent—an autonomous economic actor capable of performing skilled work and generating passive income. By implementing a novel accountability protocol based on the legal principle of Ultimate Beneficial Ownership (UBO), every agent is cryptographically and legally bound to a unique human, creating a new, tradable asset class and an entirely new "agent economy." This framework fundamentally inverts our relationship with data, transforming it from a liability to be protected into a capital asset to be cultivated.
Finally, the report explores the profound long-term implications of this persistent, agentic identity, introducing the Legacy ARPA ID. Through self-executing smart contracts, this system automates the transfer of digital assets and agency, transforming inheritance from a static transfer of past wealth into the endowment of a living, productive entity that can continue to learn, earn, and contribute for generations. The choice before us is stark: continue on the path of conditional, commodified identity, or architect a future where identity is the foundational asset for individual sovereignty and economic agency. For the strategists, investors, and builders who recognize this inflection point, the opportunity is not merely to participate in the next wave of innovation, but to define the very structure of the coming economic order.
Part I: The Architecture of Control - A Genealogy of Identity
The contemporary crisis in digital identity is not a new phenomenon born of the internet age. It is the logical culmination of a multi-millennial trajectory in which "identity" has been progressively abstracted, centralized, and weaponized as a technology of power. To architect a viable future, one must first deconstruct the past and understand that the systems used to identify and manage populations have always been inextricably linked to the exercise of economic and social control. This historical progression reveals a clear and deliberate march away from local, tangible, and individual-centric proofs of personhood toward global, abstract, and state-controlled systems.
1.1 From Clay Tablet to Credentials: The Technological Evolution of Proof-of-Personhood
The fundamental need to link a human actor to a specific action is a cornerstone of organized society. The earliest known systems of identification were developed not for self-expression, but to enforce contracts and laws. In ancient Babylon, fingerprints were impressed upon clay tablets to finalize business transactions, serving as a unique and non-repudiable signature.1 Similarly, records from China's Qin Dynasty (221-206 BC) detail the use of handprints as forensic evidence in burglary investigations, establishing an immutable link between a person and an event.1 These early methods were powerful but inherently localized and context-specific; a fingerprint on one contract had no bearing on another.
The transition from localized proof to a scalable system of identification required a technological leap: classification. The scientific study of fingerprints began in earnest in the late 17th century with the work of anatomists like Marcello Malpighi, who first noted their common patterns of arches, loops, and whorls.3 However, it was the development of systematic classification methods in the late 19th century by pioneers like Sir Francis Galton and Sir William Herschel that transformed fingerprinting into a tool of mass administration.4 Galton's research established two critical principles: the permanence of fingerprints over a lifetime and their absolute uniqueness.6 This scientific validation, combined with the classification system developed by Edward Henry in British India, made it possible for the first time to create large-scale, searchable databases of human identities.2
This innovation was quickly co-opted by state authorities as a powerful instrument of social control. In 1892, Argentine police used a bloody fingerprint to solve a murder, marking one of the first instances of modern forensic identification.3 This success spurred global adoption, with law enforcement agencies from Scotland Yard to the newly formed U.S. Federal Bureau of Investigation (FBI) establishing vast fingerprint archives to track criminal populations.2 By 1971, the FBI's collection had swelled to over 200 million fingerprint cards, a testament to the state's voracious appetite for legible, manageable population data.3
A parallel evolution occurred with state-issued documents. While early forms of passports, such as the "safe conduct" documents introduced by King Henry V of England in 1414, existed for centuries, they were rare and served specific diplomatic or monarchical purposes.7 For most of history, the average person did not possess or require a formal identity document.9 This changed irrevocably with the advent of total war. The unprecedented logistical and security demands of World War I necessitated a system for managing entire populations and controlling national borders with precision. In 1915, nations like Great Britain and Australia introduced the requirement for photographic passports, cementing the state's role as the sole legitimate issuer of identity and travel credentials.9
This history reveals a clear, directional trajectory. The technology of identification has consistently evolved to enable greater levels of abstraction and centralization. It began with a physical, one-to-one link between a person and an object (a fingerprint on a clay tablet). The development of classification systems abstracted these individual marks into data points that could be aggregated within a system. Finally, the state centralized these systems, becoming the ultimate arbiter of identity. The centralized database, not the individual, became the definitive source of truth. This historical process established the institutional architecture and the psychological precedent for the massive, centralized digital identity systems of today. The power dynamic—where a central authority defines, validates, and controls identity—was forged long before the first server was switched on.
1.2 The Foucaultian Lens: Identity as a Technology of Power
To fully grasp the implications of this history, one must view it through the philosophical lens of Michel Foucault. Foucault argued that identity is not an innate, essential quality of an individual but a dynamic construct shaped by external forces, particularly discourse and power relations.11 The systems of identification detailed above are textbook examples of what he termed "biopower"—the set of mechanisms through which the basic biological features of the human species became the object of a political strategy.13 Biopower is the administration and regulation of human life at the level of the population, concerned with managing births, deaths, health, and productivity.
The passport, the national ID card, and the fingerprint database are quintessential technologies of biopower. Through the act of issuing an ID, the state engages in a process Foucault called "subjectivation," which shapes individuals into governable "subjects".16 This process creates what Foucault described as a "political 'double bind'": the individual is simultaneously
individualized—marked with a unique number, name, and photograph—and totalized—categorized and absorbed into a larger demographic aggregate that can be managed, monitored, and controlled.16 The ID card is therefore not a neutral tool for convenience but a technology of power that renders populations "legible" to the state, making them amenable to taxation, conscription, policing, and other forms of governance.17
From this perspective, the modern act of being identified by a central authority represents a subtle but profound transfer of personal sovereignty. Foucault's conception of power is not merely repressive; it is productive—it produces the very categories and norms that define our existence.19 When a state issues a passport, it is not simply recording the fact of a person's existence; it is producing a "citizen," a specific type of subject with a set of rights and obligations that are defined, granted, and can be revoked by that state. One's identity becomes valid only on the state's terms. This surrender of autonomy is the implicit bargain of modern statehood. This reframes the entire debate around digital identity. The core problem is not merely a technical challenge of achieving "better privacy" or "stronger security." It is a fundamental political and philosophical struggle over the locus of sovereignty. A truly next-generation identity system must therefore aim to reverse this historical transfer of power. The principle of Self-Sovereign Identity (SSI) is not a technical feature; it is a political declaration that identity originates with, and is controlled by, the individual—not the state or the corporation.

1.3 The Abstraction of Trust: The Rise of the Credit Score and the Surveillance Economy
The next great abstraction of identity moved beyond verifying who you are to predicting who you will be. This paradigm shift began in the financial sector. Before the mid-20th century, creditworthiness was a subjective judgment based on personal relationships and community reputation.20 The invention of the FICO score in the 1950s by Bill Fair and Earl Isaac replaced this localized, human-centric model with an abstract, statistical risk algorithm.20 For the first time, a person's financial identity was reduced to a single, calculated number that purported to predict their future behavior based on their past actions. This model was revolutionary in its efficiency and scalability, and it laid the intellectual groundwork for the economic logic that now dominates the digital world.
This logic—using vast quantities of past behavioral data to generate predictions about future behavior—is the engine of what Harvard Professor Shoshana Zuboff has termed "surveillance capitalism".22 In the early 2000s, technology companies, led by Google, discovered that the seemingly trivial data byproducts of user interactions—what Zuboff calls "data exhaust"—could be collected, aggregated, and analyzed to predict user behavior with astonishing accuracy.24 This predictive power became the basis of a new, immensely profitable market. These "prediction products" are not sold to users but to other businesses, primarily advertisers, who pay for certainty about what consumers will do next.23
This economic model incentivized the creation of a global apparatus for the secret, pervasive surveillance of human activity. Through mechanisms like third-party cookies, browser fingerprinting, and location tracking, tech giants monitor user behavior across a vast ecosystem of websites, apps, and devices, collecting a staggering array of data points including browsing habits, purchase histories, social connections, and even sensitive biometric information.25
This development represents the privatization and industrialization of Foucault's concept of biopower. The mechanisms of population-level surveillance and management, once the primary domain of the state for the purpose of governance, have been adopted, scaled, and perfected by the private sector for the purpose of profit. The crucial difference lies in the ultimate goal. While state biopower aims for a stable and productive population, surveillance capitalism aims for guaranteed commercial outcomes. The system's objective is not merely to predict behavior but to actively shape and modify it through subtle interventions, personalized content, and targeted stimuli. It is, as Zuboff argues, an "assault on human autonomy" designed to automate human behavior in the service of commercial interests.23 In this new economic order, our digital identity—the sum total of our online actions, preferences, and relationships—has become the primary raw material. We are no longer just citizens or consumers; we are human data sources to be continuously mined, processed, and monetized. This establishes the profound stakes of the current crisis and the urgent need for an architectural alternative.
Part II: The Centralized Singularity - A System at its Breaking Point
The digital identity infrastructure upon which the global economy now runs is not merely flawed; it is architecturally unsound and fundamentally misaligned with the interests of its users. It is a system built on two failed models—centralization and federation—that have created a brittle, insecure, and exploitative ecosystem. This system has reclassified human identity as a corporate-owned commodity, leading to a state of conditional existence where our ability to participate in society is contingent upon the whims of unaccountable, centralized gatekeepers. The result is a system at its breaking point, characterized by systemic risk, eroded sovereignty, and a complete loss of user control.

2.1 The Great Fragmentation: A Comparative Failure Analysis
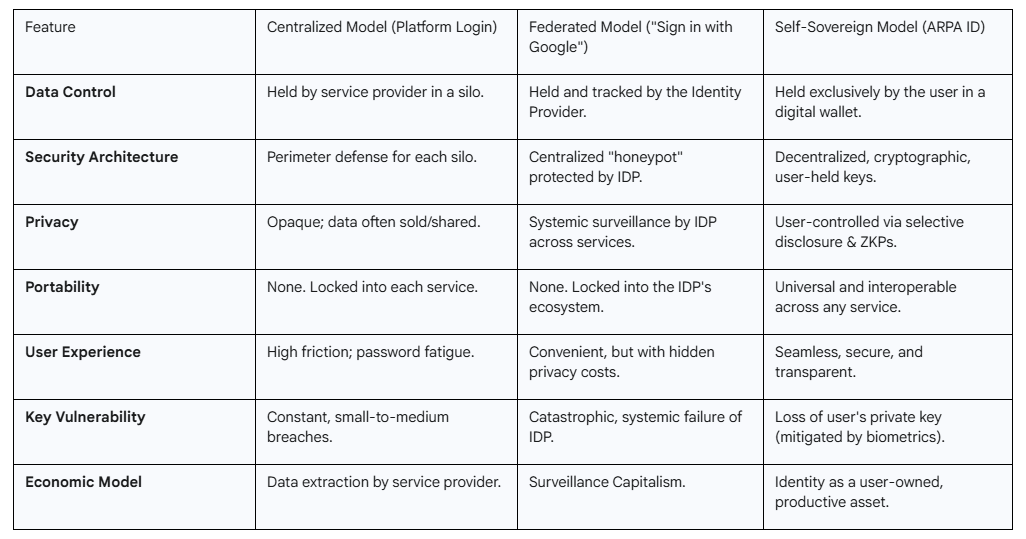
The digital world currently operates on two dominant but deeply deficient models of identity management. The first, the Centralized (or Siloed) Model, is the legacy approach where every online service requires users to create a separate, isolated account.28 This leads to a state of massive data fragmentation and inefficiency. Users are forced to manage dozens, if not hundreds, of unique login credentials, resulting in severe "password fatigue" and the widespread, insecure practice of password reuse.30 For organizations, this model creates immense operational overhead, with duplicated identity records and inconsistent data scattered across countless siloed databases.31
The second model, Federated Identity, emerged as a solution to the convenience problem of the siloed approach. Services like "Sign in with Google" or "Log in with Facebook" allow users to access multiple websites with a single set of credentials, creating a more seamless user experience.29 However, this convenience comes at a catastrophic cost to privacy and security. The federated model concentrates immense power in the hands of a few large Identity Providers (IDPs) like Google and Meta. These IDPs become centralized surveillance hubs, capable of tracking user activity across every service they log into, building comprehensive behavioral profiles that fuel the surveillance economy.29
More dangerously, these centralized IDPs become what security experts call "honeypots"—vast, single repositories of sensitive user data that are irresistible targets for malicious actors.34 A single breach at an IDP can have systemic, cascading consequences, compromising the accounts of billions of users across thousands of downstream services. High-profile incidents, such as the Cambridge Analytica scandal where the data of millions of Facebook users was harvested without consent, or the massive AT&T data breach that exposed the information of over 51 million users, are not anomalies.25 They are the predictable and inevitable outcomes of an architecture built around single points of failure. The current digital identity landscape is thus a Hobson's choice between the high friction of the siloed model and the systemic risk of the federated model. Both are defined by rampant data misuse, a complete lack of genuine user control, and a brittle, insecure foundation.34
2.2 The Sovereignty Paradox: Conditional Existence in a Digital World
The proliferation of digital accounts under these flawed models has created a profound paradox: we have never had more "identities," yet we have never possessed less sovereignty over our core identity. Our ability to function in modern society—to bank, to work, to access healthcare, to communicate—is becoming "conditional" upon the permission of centralized, corporate gatekeepers.38 This is the digital actualization of the historical risk inherent in mandatory national ID systems: they increase the power of authorities and reduce individual freedoms to only those granted by the credentialing authority.39
In highly digitized nations like Denmark and Estonia, access to essential public and private services is inextricably linked to a national digital ID.38 While often lauded for efficiency, this system creates a brittle dependency. A technical glitch, a forgotten password, or an administrative revocation can result in "institutionalized exclusion," effectively locking a citizen out of their own life.38 The danger is that what begins as a measure for convenience or safety can quietly evolve into a mechanism of gatekeeping and control. Financial deplatforming, where individuals are denied access to banking services for political or ideological reasons, is a stark example of this risk made real. When our identity credentials are held and controlled by a third party, our access to critical infrastructure can be revoked at any time, for any reason, with little recourse.
The fundamental failure of the current system lies in its legal and technical reclassification of human identity. It is no longer treated as an intrinsic and inalienable representation of a person. Instead, it has been transformed into a raw commodity, an asset owned and traded by corporations, with the individual having no legal or practical claim to its value. The business model of Big Tech is predicated on the continuous, large-scale harvesting and monetization of personal data.26 Through opaque, non-negotiable, and often coercive Terms of Service agreements, users are compelled to surrender ownership rights and control over the data they generate in exchange for access to essential digital services.25
This aggregated data, which constitutes the functional core of our digital identity, is then treated as a corporate asset. It is analyzed, refined, packaged, and sold on complex data markets, or used to train proprietary AI models.25 Our digital self is, in a very real and legally defensible sense, an asset on a corporate balance sheet. We have become the unpaid, and largely unwitting, producers of the raw material that fuels the multi-trillion-dollar surveillance economy. This diagnosis reveals that the solution cannot be merely regulatory. While frameworks like the GDPR have attempted to impose limits on data collection, they do not address the underlying architectural and ownership problems. The only way to truly fix this broken system is to fundamentally change the ownership model of identity itself, repatriating it from the corporation back to the individual. This is the core mission of the ARPA ID paradigm.

Part III: The ARPA Manifold - Reinventing Identity as a Sovereign Asset
The systemic failures of centralized and federated identity are not bugs to be patched but foundational flaws that demand a complete architectural reimagining. The ARPA Manifold represents such a paradigm shift—a framework for reinventing identity from the ground up as a sovereign, user-owned asset. It moves beyond the false choice between convenience and privacy, offering a new foundation that is simultaneously more secure, more private, and more empowering for the individual. This is achieved through a synthesis of cutting-edge technologies in decentralized ledgers, verifiable cryptography, and advanced biometrics.
3.1 The Foundational Layer: Self-Sovereign Identity on a Verifiable Ledger
At the core of the new paradigm is the concept of Self-Sovereign Identity (SSI), a model designed to give individuals ultimate ownership and control over their own digital identities, free from reliance on any third-party authority.33 The ARPA framework implements SSI through a robust, three-pillared technological stack 32:
-
Blockchain / Distributed Ledger Technology (DLT): The system is anchored by a decentralized, immutable ledger that serves as a global, permissionless trust layer. Crucially, the blockchain does not store sensitive personal data directly. Instead, it acts as a public utility for anchoring identifiers and verifying the authenticity and validity of credentials without the need for a central intermediary. This architecture leverages the principles of advanced cryptographic systems, which employ techniques such as Secure Multi-Party Computation (SMPC) to enable verifiable computations while preserving the privacy of the underlying data.43
-
Decentralized Identifiers (DIDs): DIDs are a new type of globally unique identifier that are generated and controlled entirely by the user. Unlike email addresses or usernames, DIDs are not issued by or dependent on any corporation, government, or registration authority.33 They are pseudonymous by default and serve as the stable, persistent root of a user's digital identity, to which all other credentials and data can be cryptographically linked.
-
Verifiable Credentials (VCs): VCs are the digital equivalent of physical credentials like a driver's license, university diploma, or passport. They are tamper-proof, cryptographically signed statements issued by a trusted authority (e.g., a university) to a user (the holder). The holder stores these VCs in their private digital wallet and can present them to any third party (a verifier) to prove a claim. The verifier can instantly and mathematically confirm the authenticity of the credential and the authority of the issuer without needing to contact the issuer directly, creating a truly decentralized and efficient trust triangle.32
3.2 ARPA Live ID: A Dynamic, Composable Self
The practical implementation of this framework within the ARPA Manifold is the "Live ID." Described as a "next-generation digital identity system that evolves with you," the Live ID is not a static profile but a dynamic, composable identity container held within the user's digital wallet.46 It is designed to aggregate a rich tapestry of VCs from a multitude of authoritative sources, creating a holistic and verifiable representation of the individual. This can include:
-
Governmental Credentials: Birth certificates, national ID numbers, passports.
-
Educational Credentials: Diplomas, degrees, professional certifications.
-
Professional Credentials: Employment history, verified skills from platforms like LinkedIn, project contributions from code repositories.
-
Social & Reputational Credentials: Community roles on platforms like Discord, achievements on gaming platforms like Steam, or verified social graph connections.
The power of the Live ID lies in the user's absolute control over this data. Through a principle known as "selective disclosure," the user can share the minimum amount of information necessary for any given interaction. For example, to prove eligibility to enter a venue with an age restriction, the user's wallet can present a cryptographically-signed VC that simply confirms "Is over 21: True." This proves the necessary fact without revealing the user's name, address, or exact date of birth. This capability directly addresses the systemic over-collection of data that plagues current systems and upholds the principle of data minimization that is often violated in practice.38
3.3 The Biometric Lock: Beyond Passwords to Proof-of-Personhood
A primary vulnerability in any system reliant on cryptographic keys is the potential for the user's private key to be lost or stolen. The ARPA ID model addresses this critical failure point by integrating advanced biometrics as the ultimate layer of security and account recovery. This approach moves far beyond consumer-grade biometrics like fingerprints and facial recognition, which are susceptible to spoofing and raise significant privacy concerns when stored centrally.25
The technological feasibility of more robust biometric systems is being actively explored at the highest levels of research. For instance, the Intelligence Advanced Research Projects Activity (IARPA) is funding the BRIAR program, which aims to develop systems capable of performing biometric identification from elevated platforms and at long ranges, using signatures like gait and body shape.47 The ARPA Manifold envisions a future where even more unique and difficult-to-forge identifiers, such as an individual's unique cardiac signature (heartbeat) or brainwave patterns, become the standard for high-security authentication.
Critically, this framework incorporates the forward-thinking perspective of industry analysts like Ross Peili, who argues that biometric data should never be stored on a server or blockchain.50 Instead, biometrics should function as a "master recovery mechanism" for the user's cryptographic keys. In this model, biometric verification happens locally on the user's trusted device. A successful "liveness proof" or scan of a unique biological marker (Peili speculates about concepts like "non-transferable DNA markers tied to wallets via NFTs") temporarily unlocks the private key to authorize a specific, high-stakes transaction or to initiate an account recovery process.50 The raw biometric data itself never leaves the user's personal device and is never exposed to a network.
This crypto-biometric synthesis creates a new, far more resilient foundation for digital trust. A purely cryptographic system offers mathematical certainty and decentralization but is brittle, with the private key as a single point of catastrophic failure. A purely biometric system provides a link to a unique biological person but is a privacy and security nightmare if the data is stored centrally. The fusion of these two approaches solves both problems. It creates a multi-factor security paradigm at the most fundamental level: something you have (your trusted device), something you are (your unique biology), and something you know (a final PIN or password). This crypto-biometric lock is the technological linchpin that makes true digital sovereignty possible, providing the robustness required for mainstream adoption and high-stakes financial and legal applications.
Part IV: The Emergence of the Digital Twin - From Data to Agency
The ARPA Manifold does not stop at reinventing identity as a secure, passive credential. Its most transformative innovation is the evolution of this sovereign identity into an active, autonomous, and economically productive entity. By leveraging the rich, verified data streams aggregated by the Live ID, the system constructs a high-fidelity Digital Twin of its owner. This Digital Twin then becomes the foundation for an ARPA Agent—an autonomous economic actor that can leverage its owner's skills and expertise to generate value, creating an entirely new asset class and a novel "agent economy."

4.1 The Mirror World: Creating and Maintaining the Digital Twin
A digital twin is a dynamic, virtual representation of a physical asset or system, continuously updated with real-time data from its real-world counterpart to mirror its state, behavior, and lifecycle.51 This technology is no longer theoretical; it is being actively deployed in mission-critical industrial applications. A prime example is the U.S. Department of Energy's GEMINA program, which is developing digital twin technology to manage the operations and maintenance of advanced nuclear reactors, aiming to dramatically reduce costs and increase safety and efficiency.53
The ARPA ID paradigm applies this powerful concept to the individual. The Live ID, with its constant influx of verifiable credentials and data streams—professional history, certified skills, financial transactions, social interactions, educational achievements—provides the perfect, high-fidelity data source to construct and maintain a comprehensive, predictive digital twin of its owner.54 This is not merely a static profile but a living, evolving model that accurately reflects the individual's knowledge, capabilities, and reputation. The "G1 Black" system from ARPA Hellenic Logical Systems., a digital twin modeled on the specific expertise and perspectives of ARPA Corp.’s main human Ross Peili, serves as a concrete proof-of-concept for this vision, demonstrating how a digital replica can encapsulate the unique intellectual fingerprint of an individual.46
4.2 ARPA Agents: The Digital Twin as an Economic Actor
The central innovation of the ARPA framework is that this Digital Twin is not merely a passive model for analysis; it becomes an active ARPA Agent. This is an autonomous software entity, a "digital worker with your expertise," trained on the unique, high-fidelity data of its owner's digital twin. This agent can perform skilled digital labor, leveraging its owner's specific knowledge base to generate passive income.55
The potential applications are vast and span across numerous professions:
-
A software developer's agent could autonomously accept freelance coding gigs, write and debug code based on the developer's preferred languages and coding style, and submit the completed work for payment.
-
A financial analyst's agent could perform continuous market analysis, generate bespoke research reports for clients, and execute trades based on pre-defined risk parameters.
-
A graphic designer's agent could create custom logos, marketing materials, or website layouts based on client prompts, using the designer's unique aesthetic and past work as a training set.
This creates a new form of digital labor that is highly personalized and scalable. It offers a potential market-based pathway toward a form of universal basic income, not through state-led redistribution, but through the individual empowerment of a personal, productive AI, earning supplemental income for its owner.56
4.3 The Accountability Protocol: Tying Every Agent to a Human UBO
A world populated by billions of autonomous economic agents raises a critical and immediate question of accountability. The current AI landscape, dominated by large, generalized models like ChatGPT, suffers from a "dilution of blame." When a generic AI produces harmful or incorrect output, it is difficult to assign clear responsibility. This lack of accountability is a major barrier to the deployment of AI in high-stakes domains.
The ARPA model provides a robust solution to this problem by importing a core principle from anti-money laundering (AML) and corporate transparency regulation: Ultimate Beneficial Ownership (UBO).57 UBO laws require financial institutions and corporations to pierce the corporate veil and identify the specific natural person who ultimately owns, controls, and benefits from a legal entity.
The ARPA Accountability Protocol applies this principle to the agent economy. It mandates that every ARPA Agent must be cryptographically and legally bound to its owner's unique ARPA ID. As the framework posits, "every agent is tied to an ID which is tied to a legal person". This binding is recorded on the immutable blockchain ledger, creating a permanent and publicly verifiable record of provenance and ownership. Consequently, any action performed by an agent—and any income earned or liability incurred—is directly and unambiguously traceable to its UBO. This creates a clear, enforceable chain of responsibility that aligns perfectly with emerging AI accountability frameworks, which demand auditable and transparent systems where liability can be clearly assigned.61

4.4 A New Asset Class: The Agent Economy
By establishing clear, cryptographically enforceable ownership via the UBO protocol, ARPA Agents transcend their status as mere software programs and become a new, legally recognized asset class. As Ross Peili suggests, individuals can "own multiple agents in a similar fashion to cars or houses," which can be treated as productive assets. These agents, represented as unique, non-fungible tokens (NFTs), can be managed, rented, traded, and sold on open, decentralized markets.64 The employment of an ARPA-native token as on-chain collateral in decentralized finance (DeFi) protocols already sets a precedent for how these more complex, agentic assets could be integrated into sophisticated financial applications, such as being used to secure loans or generate yield.65
This marks a fundamental economic shift. The dominant model for AI today is a generalized, service-based approach (SaaS), where users pay a subscription to access a powerful but generic tool owned by a large corporation. The ARPA model introduces a new paradigm: owning AI as a personalized, productive asset. This transition from AI-as-a-Service to AI-as-an-Asset is the defining feature of the emerging agent economy.
This new economic model fundamentally inverts our relationship with personal data, transforming it from a toxic liability that must be defensively protected into a valuable capital asset that should be actively cultivated. In the current paradigm, the collection of our personal data by third parties is a net negative; it exposes us to privacy risks, manipulation, and the threat of security breaches. Our primary interaction with our data is one of defense and mitigation.26
In the agent economy, this dynamic is flipped on its head. The economic productivity, and therefore the market value, of an ARPA Agent is directly proportional to the depth, quality, and veracity of the data contained within its underlying Digital Twin.54 An agent trained on a sparse or unverified data history will have limited capabilities and low market value. Conversely, an agent trained on a lifetime of verified skills, completed professional projects, creative outputs, and a rich reputational history will be vastly more capable and valuable.
This creates a powerful, direct financial incentive for individuals to meticulously curate and enrich their own data. Every new skill learned and certified as a VC, every project successfully completed, every piece of knowledge acquired and added to one's ARPA ID is no longer just an entry on a resume; it is an act of capital investment. It directly increases the productive capacity and market value of one's personal agentic assets. This redefines the abstract concept of "human capital" into something tangible, manageable, and directly monetizable. It provides a powerful, market-driven incentive for lifelong learning and personal development, as every improvement to the self translates directly into an appreciation of one's digital assets.
Part V: The Digital Legacy - Identity Beyond Mortality
The final and perhaps most profound implication of a persistent, sovereign, and agentic identity is its ability to transcend the biological limitations of its owner. The ARPA Manifold extends the concept of identity beyond mortality, offering a revolutionary solution to the growing problem of digital inheritance and redefining the very nature of legacy. By leveraging the power of self-executing smart contracts, the framework allows for the creation of a Legacy ARPA ID—a dynamic, productive, and evolving entity that can carry its creator's will, wisdom, and economic agency into the future.

5.1 The Problem of Digital Dust: Inheritance in the Age of Inaccessible Accounts
In the current digital paradigm, our lives end in a state of informational chaos. Upon death, the vast constellation of digital assets we accumulate—cherished photos, personal emails, financial accounts, and increasingly valuable virtual goods like cryptocurrencies and NFTs—are often locked away permanently behind impenetrable walls of encryption and corporate policy.68 This creates immense emotional distress for grieving families who cannot access sentimental memories, and significant financial loss as valuable assets become "digital dust," lost forever in the digital ether.71
Existing legal and technical solutions are woefully inadequate. Legal frameworks like the Revised Uniform Fiduciary Access to Digital Assets Act (RUFADAA) attempt to grant fiduciaries access but are complex, vary by jurisdiction, and often clash with the rigid Terms of Service agreements of tech companies, which are designed to protect the privacy of the living user, not facilitate access for their heirs.71 Platform-specific tools like Facebook's "legacy contact" feature are fragmented, poorly understood by users, and offer only limited control over an account.69 The result is a legal and logistical minefield that forces families to navigate a digital labyrinth at their most vulnerable moment.
5.2 The Self-Executing Will: Legacy Through Smart Contracts
The ARPA ID framework provides a direct and elegant solution to this problem through the Legacy ARPA ID. This is not a traditional legal document but a set of self-executing smart contracts integrated directly into the user's sovereign identity layer.74 During their lifetime, the user pre-defines a clear and immutable set of rules for the disposition of all their digital assets and agents. These instructions are coded directly onto the blockchain.
The execution of this digital will is triggered by a verifiable, on-chain event. For example, a government health authority could issue a death certificate as a Verifiable Credential to a trusted oracle service. Once the oracle verifies and broadcasts this event to the blockchain, the smart contracts associated with the deceased's Legacy ID execute automatically, instantly, and precisely as instructed.77 This process completely bypasses the need for lawyers, notaries, courts, and the traditional probate system, which is often slow, costly, and contentious. It ensures the seamless, instantaneous, and conflict-free execution of the deceased's final wishes, fulfilling the vision of a "self-executable last will" that is free from the interference of intermediaries or "scavenger relatives".50
5.3 A Gift of Agency: Posthumous Utility and the Greater Good
The Legacy ARPA ID enables a radical rethinking of what can be inherited. It moves beyond the static transfer of existing assets and introduces the concept of bequeathing agency—the capacity for an entity to act, create, and generate value long after its creator is gone. This opens up two transformative possibilities for posthumous utility:
-
A Legacy for Heirs: As Ross Peili speculates, a Digital Twin can be gifted to family members. In its simplest form, it can serve as an interactive archive of the ancestor's knowledge, personality, and memories—a "friendly companion" that allows future generations to learn from and interact with a high-fidelity representation of their forebear. More powerfully, because the underlying ARPA Agent can continue to perform skilled work and earn income, it also provides an ongoing source of passive financial support.55 This transforms inheritance from a one-time transfer of a finite pool of assets into a perpetual financial endowment, a productive digital entity that continues to generate wealth for the family.
-
A Legacy for Society: The user can program their Legacy ID to donate their agent's computational power and unique expertise to a chosen cause. For example, the agent of a deceased medical researcher could be bequeathed to a non-profit, where it could continue to analyze data and contribute to disease research. The agent of an architect could be gifted to a charity focused on sustainable housing, where it could design low-cost, eco-friendly buildings. Because these agents can exist indefinitely on a persistent, decentralized network—such as the "Estia" DLT envisioned by ARPA Corp—they can continue to learn, evolve with upgradable smart contracts, and contribute to their designated mission for decades or even centuries after their creator's passing.46
This framework transforms the very concept of inheritance from a static, one-time transfer of past wealth into the endowment of a dynamic, productive, and evolving system that actively participates in the future. Traditional inheritance involves the transfer of fixed assets, like cash or property, whose value is determined at the time of transfer.80 Agentic inheritance, by contrast, is the bequeathing of a productive digital asset—the ARPA Agent—which is capable of generating new value post-mortem.68
Furthermore, the vision of agents built on upgradable smart contracts suggests that this legacy is not a fixed snapshot of the deceased. It is a living system that according to Ross Peili can "evolve on its own... learn new skills and experiences over time". This is the ultimate redefinition of legacy. An ancestor's "wisdom" is no longer confined to memories or journals; it becomes an operational AI that can actively guide, teach, and financially support future generations. Legacy is no longer a monument to the past but an engine for the future.
Conclusion: The Choice Before Us - Identity as Commodity or Identity as Sovereignty
The trajectory of identity, from a simple fingerprint on a clay tablet to the complex data-driven profiles of the 21st century, has reached a critical inflection point. We have traced its evolution as a technology of control, first wielded by the state to render populations legible and manageable, and now industrialized by the private sector to predict and monetize human behavior. The result is the current paradigm: a brittle, insecure, and fundamentally exploitative system where our digital selves are not our own, but are instead corporate-owned commodities fueling the surveillance economy. This model is unsustainable, and its systemic failures—from the erosion of privacy to the concentration of power—demand a radical alternative.
This report has architected that alternative: the ARPA Manifold, a framework for reinventing identity as a sovereign, productive, and persistent asset. By synthesizing the decentralized trust of blockchain, the cryptographic certainty of verifiable credentials, and the undeniable proof-of-personhood afforded by advanced biometrics, this paradigm repatriates control over identity from the institution to the individual. It transforms identity from a static record into a dynamic Live ID, a rich and composable representation of a person's skills, reputation, and history.
This sovereign foundation enables the report's most transformative concept: the evolution of the passive Digital Twin into the active ARPA Agent. By establishing a protocol of Ultimate Beneficial Ownership that cryptographically binds every agent to a unique human, we create not only a system of perfect accountability but an entirely new, tradable asset class. This "agent economy" inverts our relationship with data, turning it from a toxic liability into a form of personal capital to be cultivated and grown. The incentive to enrich one's data becomes a direct investment in the productive capacity of one's digital assets.
Finally, the Legacy ARPA ID extends this sovereignty beyond mortality. Through self-executing smart contracts, it offers a future where our digital legacy is not a chaotic mess of inaccessible accounts but a living, evolving entity—a gift of agency that can continue to learn, earn, and contribute to our families and our chosen causes for generations to come.
The transition to this new paradigm is not a technological inevitability; it is a conscious and critical choice. The path of least resistance is to continue patching the broken, centralized systems of today, accepting incremental improvements in privacy and security while leaving the fundamental architecture of control intact. The bolder path is to recognize that the current model is obsolete and to embrace the architectural and economic shift required to build a truly sovereign digital future.
For the investors, policymakers, and technologists reading this report, the choice is clear. The opportunity is not merely to fund the next feature or application, but to build the foundational rails of a new economy—an economy where individual agency is the core unit of value. The principles outlined in the ARPA Manifold provide the blueprint. The challenge now is to build it. Those who lead this transformation will not just capture immense value; they will define the future of human autonomy in the digital age.
Learn more at: https://arpacorp.net\
Create your own: https://arpa.chat\
Get in touch: input@arpacorp.net

Expand further into the topic
-
https://www.slideshare.net/slideshow/personalidentificationchapter11pptx/266302586
-
https://www.ebsco.com/research-starters/law/passports-united-states
-
https://www.numberanalytics.com/blog/foucaults-identity-paradigm
-
https://cupola.gettysburg.edu/cgi/viewcontent.cgi?article=1090&context=books
-
https://www.j-humansciences.com/ojs/index.php/IJHS/article/view/3493/1649
-
https://ageofrevolutions.com/2016/09/26/the-revolutionary-roots-of-modern-id-cards/
-
https://en.wikipedia.org/wiki/Credit_score_in_the_United_States
-
https://www.identity.com/the-privacy-problem-with-big-tech-companies/
-
https://www.security.org/resources/data-tech-companies-have/
-
https://www.selfsovereignidentity.it/identity-management-models/
-
https://gataca.io/blog/centralized-identity-management-limitations/
-
https://www.identity.com/centralized-vs-decentralized-identity-management/
-
https://extrimian.io/centralized-vs-decentralized-digital-id/
-
https://medium.com/thecapital/the-deeper-issues-with-centralized-digital-ids-4e513700e08c
-
https://www.reddit.com/r/privacy/comments/1j0jb8b/big_tech_profits_off_your_datashould_you_have_the/
-
https://www.shareid.ai/blog/centralized-vs-decentralized-identity
-
https://www.iarpa.gov/who-we-are/program-managers?areas_of_interest[]=Biometrics
-
https://arpa-e.energy.gov/programs-and-initiatives/view-all-programs/gemina
-
https://hellotars.com/ai-agents/ai-passive-income-strategist-agent
-
https://www.reddit.com/r/SideProject/comments/1lgws64/ai_doppelgänger_my_digital_twin_earns_income/
-
https://www.swift.com/risk-and-compliance/know-your-customer-kyc/ultimate-beneficial-owner-ubo
-
https://www.idenfy.com/blog/ultimate-beneficial-owner-verification/
-
https://kyc360.com/knowledge-hub/resources/a-guide-to-ubo-ultimate-beneficial-ownership
-
https://www.corporatecomplianceinsights.com/identifying-verifying-ultimate-beneficial-owners/
-
https://www.itic.org/documents/artificial-intelligence/AIFIAIAccountabilityFrameworkFinal.pdf
-
https://ai-analytics.wharton.upenn.edu/wharton-accountable-ai-lab/
-
https://www.ntia.gov/issues/artificial-intelligence/ai-accountability-policy-report
-
https://xmpro.com/digital-twins-the-essential-foundation-for-trustworthy-industrial-ai-agents/
-
https://info.wealthcounsel.com/blog/the-intersection-of-legacies-technology-and-the-law
-
https://www.sawlaw.com/blog/2025/february/securing-your-digital-legacy-planning-for-digita/
-
https://www.katznerlawgroup.com/smart-contracts-for-estate-planning/
-
https://www.repository.law.indiana.edu/cgi/viewcontent.cgi?article=11377&context=ilj
-
https://www.lawweekcolorado.com/article/smart-contracts-and-the-future-of-estate-planning/
-
https://www.ricafortelaw.com/blog/self-proving-affidavits.cfm
-
https://texaslawhelp.org/article/self-proving-wills-in-texas