Table of contents
1. Introduction
2. Executive Summary
3. Threats targeted at crypto Users
-
Pig Butchering Scam
-
Wallet Drainers & Approval Scams
-
Social Engineering & Impersonation
-
Phishing Attacks
-
Address Poisoning Attack
-
Scam Tokens, Fake Airdrops, Rugpulls & Honeypots
-
Crypto blackmail and extortion
-
Physical Theft
4. Conclusion
1. Introduction
Cryptocurrency has revolutionized money, ownership, and trust. It offers a decentralized, borderless financial system that empowers individuals, boosts financial inclusion, and drives innovation in payments, lending, and beyond. Blockchain makes transactions fast, transparent, and censorship-resistant—a significant shift from traditional finance.
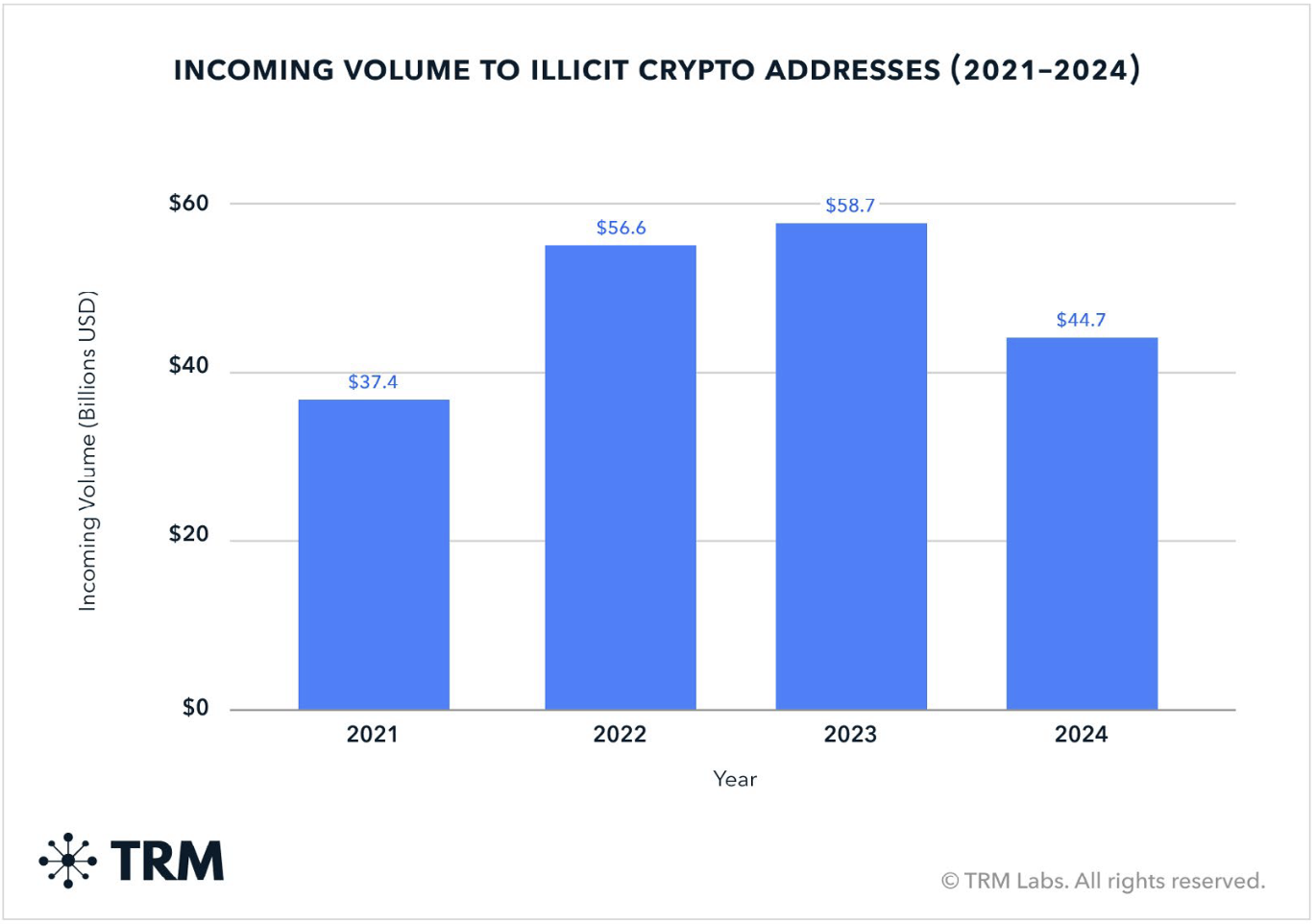
However, this innovation has come with a darker side: over the past five years, the crypto space has lost more than $100 billion to scams, hacks, and state-sponsored attacks—a figure that continues to grow year after year. As the industry expands, so do bad actors’ tactics—from phishing attacks and wallet drainers to fake token launches and protocol exploits—creating a complex web of deception that preys on both users and institutions.
This article dives into the major categories of crypto-related fraud and theft targeting users and firms, examines why these threats are growing, who is most vulnerable, and what can be done to stay safe in a rapidly evolving digital economy.
2. Executive Summary
This article provides a comprehensive overview of the most prevalent threats targeting crypto users in 2025, from deeply personal scams like pig butchering and impersonation, to technical exploits such as wallet drainers, phishing attacks, and address poisoning. It draws from real-world case studies—including confirmed nine-figure thefts—and explores both the financial impact and operational methods behind each scam type. With a focus on user awareness, threat recognition, and prevention strategies, the article aims to equip individuals, projects, and platforms with the knowledge necessary to navigate an increasingly hostile Web3 environment. Ultimately, it positions user protection as a foundational pillar for long-term crypto adoption and ecosystem resilience.
3. Threats Targeted at Crypto Users
As the crypto ecosystem grows more accessible and valuable, individual users have become prime targets for a wide range of scams, thefts, and manipulative tactics. Unlike traditional financial systems where fraud often requires breaching centralized infrastructure, Web3 shifts the responsibility of security directly to the user. This makes everyday participants—from newcomers to experienced traders—vulnerable to attacks that exploit trust, habits, and technical misunderstandings.
These threats don’t always come through obvious hacks. Many rely on social engineering, malicious smart contracts, or deceptive interfaces designed to trick users into giving up control. Others exploit on-chain behaviors, wallet permissions, or even real-world exposure. Whether through phishing, wallet drainers, fake airdrops, or physical coercion, the common goal is simple: gain access to your assets without needing your private key.
Understanding how these scams operate is essential to navigating Web3 safely. In this section, I’ll break down the most common and dangerous crypto scams targeting users today. These include:
- Pig Butchering Scams
"Pig butchering" is a sophisticated and highly manipulative scam that targets unsuspecting victims through a combination of romance, friendship, and fake investment opportunities. The term is derived from the Chinese phrase "Shāzhūpán." The scam involves emotionally manipulating victims by gradually building trust through fabricated relationships.
Scammers typically connect with their victims via dating apps, social media, or messaging platforms, patiently cultivating emotional bonds. Once trust is established, scammers introduce fake cryptocurrency or financial investments promising high returns. After victims invest significant sums, they find their funds inaccessible, and the scammers disappear—leaving them emotionally and financially devastated.

Global Financial Impact
Pig butchering scams have rapidly emerged as one of the most destructive and pervasive forms of online fraud in recent years. Combining elements of romance scams, financial deception, and psychological manipulation, these schemes emotionally entrap victims before defrauding them of substantial sums—often through fraudulent cryptocurrency investments.
The global financial impact of pig butchering scams is staggering. According to a 2024 study by researchers at the University of Texas, these scams have caused more than $75 billion in losses worldwide between January 2020 and February 2024. This figure highlights the growing dominance of pig butchering in the global cybercrime landscape.
The problem has intensified. In 2024 alone, the FBI reported $5.8 billion in losses from pig butchering scams in the United States. a figure based only on filed complaints, meaning actual losses are likely far higher. Additionally, independent industry estimates from Cyvers place global crypto-related losses at $3.6 billion in 2024, making it the most financially damaging scam in the digital asset space that year.
These scams are particularly widespread in North America, Europe, and East Asia, where individuals are targeted through dating apps, social media platforms, and unsolicited messages. Behind them are transnational criminal syndicates, largely based in Southeast Asia—notably Myanmar, Cambodia, Laos, and Thailand. Many of these operations are intertwined with human trafficking, where people are forcibly employed in scam compounds under exploitative and abusive conditions.
The combination of massive financial damage and widespread human rights abuses makes pig butchering scams a critical global threat—demanding increased public awareness, regulatory action, and coordinated international law enforcement efforts.
How the Pig Butchering Scam Operates -
Pig butchering scams are highly organized fraud operations that follow a calculated, multi-stage process designed to exploit victims emotionally and financially. Scammers invest time and resources into crafting believable personas, building trust, and gradually manipulating victims into making large financial commitments—primarily in fake investment schemes. Here's a breakdown of how the scam typically unfolds:
-
Gathering Victim Details: Before contact is even made, scammers acquire personal information to identify and target potential victims. They rely on a variety of methods to build target lists, including,
-
Data breaches and dark web purchases: Leaked databases containing names, emails, phone numbers, and social media handles are bought and sold on underground forums. -
Social media scraping: Using automated tools, scammers harvest publicly available data from platforms like Facebook, Instagram, LinkedIn, and Twitter to understand personal interests, occupations, and relationship -
Fake profiles on dating and social apps: Scammers set up attractive profiles on Tinder, Bumble, WhatsApp, or Telegram to engage with potential victims directly. -
Random messaging (smishing/spam): Mass unsolicited texts or emails are sent, often using “wrong number” or casual greetings to start a conversation. -
Phishing websites and emails: Fraudulent platforms impersonate legitimate businesses or services to trick users into voluntarily giving up personal contact details. -
Initial Contact: Once a victim is identified, the scam begins with seemingly harmless outreach. This could be a friend request on social media, a message on a dating app, or even a misdirected SMS or WhatsApp message pretending to be a wrong number. Scammers use attractive photos and carefully crafted personas—often portraying themselves as successful, lonely, or family-oriented individuals.
-
Building the Relationship: Scammers engage the victim in friendly, consistent conversation, slowly establishing trust and emotional connection. Over days or weeks, they cultivate the illusion of a sincere relationship, whether romantic, platonic, or business-oriented. They mirror the victim’s interests, compliment them, and share emotional stories (usually fake) to deepen the bond.
-
Introducing the Investment: Once trust is secured, the scammer introduces the idea of investing—typically in cryptocurrency, forex, or “exclusive” financial opportunities. They claim personal success and often reference a wealthy relative or mentor guiding their investment journey. Victims are directed to use fake trading platforms or apps, which display manipulated gains and fabricated balances to create the illusion of legitimacy.
-
Fattening the Pig: Encouraged by seemingly real profits, the victim begins investing larger sums. The scammer continues to apply subtle emotional pressure, sometimes implying that the future of the relationship depends on financial decisions. Victims are made to feel part of a shared success story and may even be encouraged to borrow money or liquidate real assets to "maximize returns."
-
The Slaughter: Eventually, the victim attempts to withdraw their funds but encounters fake obstacles such as withdrawal fees, taxes, or identity verification steps. The scammer may pose as a platform support agent to prolong the deception. When no more money can be extracted, the scammer disappears. Websites and apps used in the scam may go offline entirely, leaving the victim with nothing.
How to Recognize the Pig Butchering Scams-
Pig butchering scams, while highly deceptive, tend to follow a predictable structure. Understanding the progression of the scam and the behavioral patterns behind it can help individuals identify the red flags early and avoid falling victim.
-
Initial Contact Through Unfamiliar Channels: These scams often begin with unsolicited contact from a stranger. Scammers may reach out via dating apps, social media platforms, or messaging services like WhatsApp, Telegram, or SMS. The message may seem accidental—such as “Sorry, wrong number”—or casually friendly. Though innocent in appearance, the goal is to prompt a response and initiate conversation. Once contact is established, scammers use charm, politeness, or curiosity to draw the victim in.
-
Rapid Trust-Building and Emotional Grooming: After establishing communication, scammers quickly work to build emotional rapport. They often present themselves as successful, kind-hearted, and emotionally available individuals. Daily conversations become frequent and personal, with scammers mirroring the victim’s interests and values. They may share fabricated stories of hardship or loneliness to deepen the emotional connection. Importantly, scammers typically avoid video calls or in-person meetings, offering excuses to maintain distance while still reinforcing the illusion of closeness.
-
Introduction of a “Lucrative” Investment Opportunity: Once the emotional groundwork has been laid, the scammer slowly introduces the idea of investing. This is often framed as an exclusive opportunity, a family secret, or a strategy that has brought them financial success. The victim is reassured that the scammer simply wants to help them succeed or “build a future together.” They are then guided to a fake trading app or website that convincingly simulates real investment platforms, showing inflated returns and detailed charts designed to build confidence.
-
Encouragement to Invest Increasingly Larger Amounts: After a small initial investment, the victim is shown fake profits on the platform. Encouraged by these fake gains and the scammer’s ongoing support, they are persuaded to invest more. Scammers apply emotional and psychological pressure—creating urgency, suggesting the opportunity is time-sensitive, or implying that a deeper investment is necessary to maintain the relationship. In some cases, victims are even encouraged to borrow money or liquidate personal savings to take advantage of the “once-in-a-lifetime” opportunity.
-
Barriers to Withdrawal and Escalating Demands: The scam reaches its climax when the victim attempts to withdraw their funds. At this point, the platform presents new hurdles: unexpected withdrawal fees, fake tax payments, or account verification processes. These are all designed to delay withdrawal while squeezing additional money from the victim. The scammer may pose as a support representative or offer reassurances, but once it becomes clear that no more funds can be extracted, they disappear—often along with the fake platform—leaving the victim emotionally betrayed and financially devastated.
-
The Aftermath and Emotional Toll: What sets pig butchering scams apart from other types of crypto fraud is the psychological damage they cause. Victims are often left feeling ashamed, emotionally manipulated, and reluctant to seek help or report the crime. Many blame themselves for trusting someone who seemed genuinely caring. This emotional fallout, combined with significant financial loss, makes these scams especially harmful and long-lasting.
Prevention Strategies-
As pig butchering scams become increasingly sophisticated, proactive awareness and caution are essential to avoid falling victim. While these scams often prey on emotional vulnerability, there are several clear strategies individuals can adopt to protect themselves.
-
Maintain Healthy Skepticism Online: The most effective form of prevention is a skeptical mindset—especially when interacting with strangers online. Be cautious of unsolicited messages from people you don’t know, particularly those who reach out via dating apps, social platforms, or messaging services and quickly attempt to build a personal connection. If a conversation turns unusually emotional or intimate early on, or the person avoids video calls or in-person meetings, consider it a red flag.
-
Separate Romance and Finance: Scammers exploit the overlap of emotional trust and financial decision-making. To mitigate this risk, it is critical to keep romantic relationships and financial advice completely separate. Never mix emotional involvement with financial transactions, especially when dealing with someone you've only met online. A genuine relationship does not come with investment pressure or requests for money.
-
Verify All Investment Opportunities: Always do independent research before investing in any opportunity—especially those introduced through casual or personal conversations. Check whether the investment platform is registered with a legitimate financial authority. Look for real user reviews, verify the website’s ownership and domain age, and confirm whether the company or app is regulated. Be especially wary of platforms offering guaranteed returns, time-sensitive deals, or requiring deposits in cryptocurrency.
-
Protect Personal Information: Scammers often use personal data to customize their approach and build credibility. Avoid sharing sensitive personal details such as your financial status, relationship history, work background, or daily routines with new online acquaintances. Even seemingly harmless details can be used to tailor manipulative tactics.
-
Trust Your Instincts and Slow Down: Pig butchering scams often involve subtle but persistent pressure. If a situation feels off—whether it’s the speed of the relationship, the investment advice, or the excuses for avoiding a real meeting—don’t ignore your gut feeling. Take a step back, consult with someone you trust, and avoid making financial decisions under emotional pressure.
-
Use Reputable Platforms and Tools: Stick to well-known, regulated financial platforms and exchanges when handling cryptocurrency or other assets. Enable two-factor authentication (2FA) and regularly monitor your accounts for any unusual activity. Avoid downloading investment apps or connecting wallets to platforms shared via private messages or social DMs.
-
Report Suspicious Activity Promptly: If you suspect that you are being targeted by a pig butchering scam or have already sent funds, it is critical to stop all communication immediately and report the incident. Victims should contact local law enforcement and their country’s cybercrime or financial fraud units—for example, the FBI’s Internet Crime Complaint Center (IC3) in the United States. In addition to official channels, there are several independent, industry-led platforms that track pig butchering and other crypto-related scams. Platforms like Chainabuse by TRM Labs allow users to report suspicious wallet addresses and fraudulent schemes anonymously or publicly. Reporting such scams not only increases the chance of recovery or mitigation but also contributes to broader ecosystem safety by helping investigators, exchanges, and wallet providers take proactive action.
Pig butchering scams are one of the most dangerous threats in crypto—not because of technical flaws, but because they exploit trust. These scams don’t steal through code, but through connection, targeting newcomers who are often experiencing crypto for the first time.
This isn’t just fraud—it’s a systemic crisis linked to organized crime and human exploitation. The best defense is awareness. If we want to onboard the next billion users safely, education must come first—because these scams are already waiting at the door.
- Wallet Drainers & Approval Scams
Wallet drainer and approval scams have rapidly become one of the most pervasive and effective attack vectors in the crypto space. Unlike traditional phishing attacks that aim to steal private keys, these scams exploit token approval mechanics—where users unknowingly grant malicious smart contracts the right to move tokens or NFTs from their wallets. Once such permissions are approved, assets can be drained without any further interaction or authentication.
Fueling this threat is the rise of Drainer-as-a-Service (DaaS) groups—underground operations that package everything an attacker needs into ready-made toolkits. These services offer phishing site templates, Telegram bots, dashboards, and automated fund-handling tools, often sold via Telegram channels or private forums. As a result, even low-skill scammers can launch sophisticated wallet-draining campaigns, targeting users across Ethereum, BNB Chain, Polygon, Arbitrum, and beyond.
The scale, automation, and deceptive nature of these scams make them especially dangerous. Many victims don’t even realize they've been compromised until hours or days later—by which time the stolen assets are already laundered or bridged across chains.

Global Financial Impact-
Wallet drainer and approval scams have become one of the most financially damaging threats in the crypto ecosystem. These scams exploit the way token approvals work on-chain—tricking users into unknowingly granting access to malicious contracts that drain assets from their wallets. Because these transactions appear “authorized,” they are difficult to reverse and often go unnoticed until it’s too late.
According to Chainalysis, more than $2.7 billion has been lost to approval phishing scams since May 2021, making this one of the most persistent and profitable scam types in Web3. Complementing this, a 2024 report from Scam Sniffer revealed that wallet drainer attacks alone resulted in over $494 million in losses, compromising more than 332,000 wallets in a single year. These numbers reflect only documented cases—real losses may be significantly higher.
Driving this surge is the growth of the Drainer-as-a-Service (DaaS) economy. Early pioneers like Monkey Drainer set the model by offering ready-made phishing and draining kits to affiliates in exchange for a percentage of stolen funds. Following its shutdown, newer groups like Inferno Drainer, Angel Drainer, Medusa Drainer, and Ace Drainer have taken its place—offering highly automated, scalable infrastructure for wallet theft. These services often come with victim dashboards, fake mint site templates, transaction automation, and laundering scripts, making it easy for even low-skilled actors to run phishing campaigns.
Most of these operations are believed to be based in Russia, Eastern Europe, and Southeast Asia, where they benefit from loose cybercrime enforcement, bulletproof hosting, and widespread use of encrypted Telegram channels. Many of these Telegram groups openly advertise their services, provide real-time support, and offer tutorials for affiliates to maximize returns from stolen assets.
What makes these scams especially damaging is not just the speed or scale of the theft but their psychological and systemic impact. Victims frequently include newcomers and casual users who were simply attempting to mint an NFT, claim an airdrop, or interact with a DeFi app. The ease with which wallets can be drained after a single signature has severely eroded trust in self-custody and on-chain UX.
This growing wave of approval-based scams poses a direct threat to Web3 adoption. For every victim who leaves the space after being drained, community trust weakens—and the very ethos of decentralization is undermined by fear.
How Wallet Drainer & Approval Scams Work-
Wallet drainer and approval scams rely not on exploiting code, but on exploiting users. These attacks follow a deceptive yet structured flow—luring victims to malicious sites, tricking them into approving smart contracts, and silently draining assets under the guise of legitimate activity. Here's how the process typically unfolds:
-
Victim Is Lured to a Malicious Website:`The scam begins when a user is tricked into visiting a fraudulent website. These sites are designed to mimic legitimate NFT mints, token airdrops, staking platforms, or DeFi protocols. Links to these sites are often spread through compromised social media accounts, Discord servers, Telegram messages, fake influencer promotions, or paid search ads.
-
Wallet Connection Is Requested: Upon landing on the site, the user is prompted to connect their crypto wallet—a normal step in most decentralized applications. Because the website appears professional or familiar, users often proceed without hesitation.
-
Approval Request Is Presented: Once the wallet is connected, the site presents a transaction for the user to approve. It may look like a standard interaction—minting a token, claiming a reward, or verifying eligibility. In reality, this transaction is a token approval. The site asks the wallet to grant permission for a specific smart contract to access tokens or NFTs in the user’s wallet.
-
Approval Is Signed by the User: The approval transaction typically uses functions like
approve(spender, amount)for ERC-20 tokens orsetApprovalForAll(spender, true)for NFTs. These functions allow the attacker to control the user’s assets. In many cases, the approval gives unlimited access to the attacker’s address. Because the approval doesn’t move tokens immediately, it often doesn’t raise red flags. -
Assets Are Drained Later: Once approval is granted, the attacker can access the approved tokens at any time using
transferFrom(). This may happen immediately or be delayed by hours or days to avoid detection. Since the action appears valid on-chain—authorized by the user—the theft can happen silently, without triggering alerts. -
Victim Realizes Too Late: In most cases, users discover the loss only after checking their wallet balance much later. Since no private keys were compromised, many victims struggle to understand how the scam happened—especially if they remember only connecting their wallet or signing “just one” transaction.
On-chain Mechanics of the Scam -
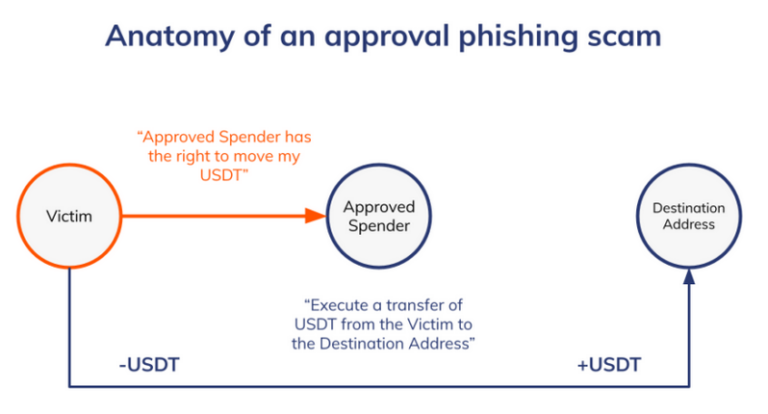
A consistent pattern observed across wallet drainer campaigns is the abuse of Ethereum's token permission functions—primarily approve() for fungible tokens and setApprovalForAll() for NFTs. While these functions are essential for legitimate DeFi and NFT interactions, they become dangerous when exploited in malicious contexts.
For ERC-20 token scams, the drainer contract typically triggers an approve(spender, amount) transaction, where the amount is set to uint256.max. This effectively grants the malicious contract unlimited spending access to the specified token. Once approved, the scammer can call transferFrom() at any time to move the victim’s tokens—without requiring additional confirmation.
In the case of NFT thefts, attackers exploit the setApprovalForAll(spender, true) function. This permission allows the scammer to transfer all NFTs from a particular collection on behalf of the victim, bypassing any per-asset security check. The broad nature of this permission makes it especially risky when granted to malicious operators.
Another common tactic involves delayed asset draining. Rather than immediately transferring out tokens post-approval, some scammers wait hours or even days to avoid drawing immediate attention. By the time the victim notices the theft, the phishing site has usually disappeared, the malicious contracts have been retired or rotated, and the funds have already been moved out of reach.
How to Recognize Wallet Drainer & Approval Scams -
Wallet drainer scams often feel invisible until it’s too late. Unlike traditional hacks, they don’t steal your private key or force access—they exploit permissions you willingly grant. The key to protecting yourself is learning how to spot these traps before you sign anything. Many drainer campaigns follow recognizable patterns, and with a bit of awareness, you can detect the warning signs early.
Here are some of the most common red flags to watch for:
-
Suspicious or Unfamiliar Sites Prompting Wallet Connection: Scammers often clone or imitate legitimate platforms such as NFT mints, staking pages, or DeFi dashboards. These fake sites are promoted through compromised social media accounts, Discord servers, paid ads, or direct messages. If you land on a site you didn’t actively seek out—or one promoted by an account acting strangely—avoid connecting your wallet.
-
Transactions Asking for Token or NFT Approvals, Not Swaps or Transfers: Always check what your wallet is asking you to approve. If a transaction requests permission to manage your tokens or NFTs—especially using
approve()orsetApprovalForAll()—and you're not performing a clear action like swapping or transferring assets, this could be a red flag -
Unlimited or Broad Approvals Hidden Behind Vague Language: Scammers often disguise malicious approvals under misleading labels like “Verify,” “Claim,” or “Mint.” Some use custom transaction metadata that hides what’s actually happening. Tools like Etherscan, DeBank, or Wallet Guard can reveal the true function call—look out for approvals granting unlimited access (e.g.
uint256.max). -
No Immediate Outcome After Signing: If you approve a transaction and nothing happens—no NFT is minted, no token is received, no confirmation appears—be wary. This delayed-action behavior is common in wallet draining scams. The attacker may wait hours or even days before draining assets, making the transaction harder to link to the loss.
-
Multiple Tokens Requested in One Interaction: Legitimate platforms usually ask for permission on a case-by-case basis. If you're asked to approve access to several tokens or entire collections in a single interaction, that’s often a sign of a malicious contract trying to drain as much as possible in one go.
-
Site Requires You to ‘Re-Verify’ or Reconnect Repeatedly: Drainer sites may prompt you to reconnect your wallet or re-sign approvals multiple times. These tactics are designed to increase the likelihood that you’ll approve access to multiple assets or chains without realizing.
-
Alerts from Security Tools or Wallet Extensions: Many browser extensions and wallet tools can warn you when an approval transaction looks suspicious. Pay attention to these alerts—they often detect known malicious contracts, suspicious patterns, or high-risk functions before you sign.
How to Prevent Wallet Drainer & Approval Scams -
Awareness is the first line of defense—but prevention is what ultimately protects your funds. Wallet drainers rely on users signing malicious approvals without fully understanding what they’re authorizing. Fortunately, with a few practical habits and tools, you can dramatically reduce your exposure to these scams. Whether you're minting an NFT, trying a new dApp, or simply browsing, these steps will help you interact safely on-chain.
Here’s how to protect yourself:
-
Never Approve Transactions Blindly: Before signing any transaction, read what you’re approving—especially if it's asking for token or NFT permissions. Avoid clicking “Confirm” just because a prompt appears. If the action isn’t clearly tied to a trusted platform or a function you initiated, stop and investigate.
-
Use Approval Management Tools Regularly: Platforms like Revoke.cash, Etherscan’s Token Approval Checker, and DeBank let you view and revoke existing token approvals. Make it a habit to check and clean up old or unused approvals—especially after interacting with unknown site
-
Enable Security Extensions: Browser tools like Wallet Guard, Pocket universe, and Scam Sniffer can detect and warn you about malicious contracts, phishing links, and suspicious approval requests in real-time. These tools act as an additional layer of defense before you sign anything.
-
Avoid Connecting to Links Shared in DMs or Comments: Drainer links are often spread via fake giveaways, impersonator accounts, or bots replying to real posts. Avoid clicking links shared in Twitter replies, Telegram DMs, or Discord messages—even if they appear to come from trusted accounts. Always navigate to sites directly through official channels.
-
Be Skeptical of Urgency or Hype: Scammers exploit FOMO. If a site says an NFT mint or airdrop is “ending in 5 minutes,” take a step back. Legitimate projects do not rush users into risky approvals or require urgent wallet interactions under pressure.
-
Use a Separate Wallet for High-Risk Interactions: Maintain separate wallets for different purposes: one for holding assets and another for minting, airdrops, or testing new apps. Keeping your primary funds isolated limits the damage in case an approval wallet gets compromised.
-
Educate Yourself on Common Approval Patterns: Understanding how approve() and setApprovalForAll() work will make you more confident in detecting abuse. Practice reviewing transactions in block explorers like Etherscan, and compare known safe contracts with suspicious ones.
-
Revoke Immediately After Use: If a site requires approval (such as a legitimate DEX or NFT platform), revoke that permission after the task is complete. This limits the risk window and ensures attackers can’t reuse the access later.
Wallet drainer and approval scams are among the most common and damaging threats in crypto, exploiting token approval mechanics to steal assets without needing private keys. While increasingly sophisticated, these scams can be avoided with vigilance and smart practices.
Always review approvals carefully, use security tools, and regularly manage wallet permissions. Legitimate platforms will never rush or pressure you—when in doubt, don’t sign. Protecting your assets requires ongoing awareness and caution—but it remains the best defense against wallet drainers
-Social Engineering & Impersonation
Social engineering and impersonation attacks are some of the most manipulative and successful tactics used in the crypto space. Rather than exploiting code, these scams exploit human trust—convincing victims to perform actions that expose their assets. Attackers often pose as support agents, developers, or influencers, engaging users through fake websites, cloned accounts, or direct messages to trick them into giving up sensitive information or signing malicious transactions.
These scams disproportionately target non-technical and elderly users, who may not fully understand how wallet permissions, seed phrases, or on-chain approvals work. A message from a fake support rep or a seemingly helpful “admin” can quickly lead to irreversible losses. The impersonator often builds trust through friendly communication before directing the user to connect to a phishing site, download a malicious file, or hand over wallet credentials.
More sophisticated campaigns now target developers, project founders, and DAO members under the guise of investment firms or hiring managers. Attackers impersonate legitimate VC firms or tech recruiters and offer lucrative remote jobs or funding opportunities. Victims are asked to download fake NDAs, job assessments, or token documents—files laced with malware designed to extract private keys or wallet files from the target’s device.
As deep-fake videos, AI-generated avatars, and compromised verified accounts become more accessible to attackers, the line between real and fake continues to blur. These scams often begin off-chain, through social platforms or email, but lead to devastating on-chain consequences. In a trustless ecosystem, social trust becomes the weakest link—and these scams exploit it at scale.

Financial Impact: Social Engineering & Impersonation Scams-
Social engineering and impersonation scams have quietly become one of the most financially devastating threats in the crypto ecosystem. Unlike technical exploits, these scams rely on manipulating human behavior—posing as trusted figures, support agents, or investors to trick users into surrendering access or signing malicious transactions.
Confirmed Financial Losses
-
Over $340 million has been stolen from Coinbase users alone through social engineering scams in the past few months, including:
-
$243 million in a single high-profile theft involving multiple threat actors.
-
$34.9 million in BTC drained from a victim following impersonation of Coinbase staff.
-
$11.5 million in cbBTC stolen on Base via a sophisticated impersonation attack.
-
-
These losses were independently verified by on-chain investigators ZachXBT and tanuki42, who suspect the figures represent only a portion of the total due to underreporting and untracked cases.
Systemic Industry Risk
What makes these scams particularly alarming is their repeatability and scalability. Attackers often reuse templates and social tactics across platforms like Telegram, Discord, LinkedIn, and email—requiring minimal cost but yielding massive returns. The Coinbase case is especially notable as no other major exchange has reported such a concentrated wave of user-targeted impersonation fraud, leading some to suspect an unreported data breach or systemic exposure.
As scammers become more organized, impersonation attacks are expected to grow—impacting individuals, projects, and institutions alike. With losses now regularly reaching eight- and nine-figure sums, the financial impact of human-targeted exploits rivals that of major protocol hacks.
How Social Engineering & Impersonation Scams Work-
Social engineering scams in crypto don’t rely on technical exploits—they rely on human error, trust, and manipulation. These scams target anyone with a wallet, from first-time users to seasoned developers, and use different tactics based on the victim’s profile, experience level, and role in the ecosystem.
-
Target Identification: Scammers cast a wide net, but tailor their approach depending on the target. They gather data from public forums, social media, leaked databases, or community chat logs to profile users. High-value targets like developers, DAO contributors, or investors may be selected for more advanced phishing campaigns, while general users—especially those who appear less technically fluent—are often hit with quick impersonation or support scams.
-
Establishing Contact: Attackers make contact through Telegram, Discord, Twitter, email, or even phone calls. They impersonate trusted roles—support agents, project team members, investors, or service providers. Their goal is to build just enough trust to guide the victim toward a compromising action. They often use stolen logos, fake domains, and AI-generated profile images to look legitimate.
-
Manipulating the Victim into Exposure: The tactics vary based on who they’re targeting:
-
New or elder usersare often guided to hand over login credentials, recovery phrases, or 2FA codes under the pretense of account recovery or support help. -
Professionals or buildersmay be sent fake NDAs, token decks, or job tests containing malware disguised as PDFs or .exe files. Once installed, the malware searches for wallet data, browser extensions, or saved seed phrases. -
Regular DeFi/NFT usersmight be lured into fake token sales, airdrops, or staking platforms—where the real goal is to trick them into signing malicious approval transactions or entering credentials on phishing sites. -
Theft and Asset Drainage: Once the scammer obtains access—via stolen credentials, malware, or signed approvals—they immediately extract the victim’s funds. In cases of malware, they may pull full wallet directories or browser data. In impersonation cases, they may simply log in and transfer funds. Because the victim unknowingly authorized the access, recovery is nearly impossible.
How to Recognize Social Engineering & Impersonation Scams- Social engineering scams often start with what appears to be a routine message or helpful offer. But behind the friendly tone or professional branding is an attacker aiming to gain your trust just long enough to steal your information or assets. Recognizing the signs early can stop these scams before they escalate.
Unsolicited Contact Claiming to Be Support, Staff, or Investors: Legitimate companies—whether exchanges, wallet providers, or VC firms—will not reach out to you directly via DMs or unsolicited messages. If someone contacts you on Telegram, Discord, or Twitter claiming to represent an organization and offering help, investment, or a job opportunity, it’s almost certainly a scam unless verified through official channels.
Requests for Sensitive Information: No real exchange, protocol, or firm will ever ask for: Your seed phrase, Private keys, Login credentials, 2FA codes and OTP If anyone asks for this information under any pretense—especially while claiming to “help you recover an account” or “verify your identity”—it’s a scam.
Urgent Pressure to Act Immediately: Social engineers often create a false sense of urgency. They might say your account has been locked, your funds are at risk, or a rare opportunity will expire in minutes. The goal is to pressure you into acting before you have time to think or verify. Real platforms don’t force instant decisions through backchannels.
Too-Good-To-Be-True Offers: If someone you don’t know suddenly offers you a high-paying remote job, exclusive token deal, grant, or partnership—especially without prior engagement or context—assume it’s a scam until proven otherwise. These are common setups used to send malware-laced documents or trick you into downloading malicious files.
Suspicious Links, New Accounts, or Fake Domains: Be cautious of:
-
Links to unfamiliar domains or typo-squatted URLs (e.g., support-coinbase.com instead of coinbase.com)
-
Twitter or Telegram accounts with minimal history or fake engagement
-
Generic Gmail addresses pretending to represent major firms
Unrequested File Attachments: If someone sends you files—such as NDAs, job tests, pitch decks, or token documents—without clear context and verification, do not open them. These files often contain malware designed to extract private keys or gain access to your device.
Identity Doesn’t Match Public Sources: If someone claims to be affiliated with a known firm, verify them. Check:
-
Does their email domain match the official company site?
-
Are they listed on the firm’s team page or LinkedIn?
-
Does their profile have recent activity, consistent branding, and followers that make sense?
Prevention Strategies-
Social engineering attacks rely on deception and trust, not code. They can target anyone—regardless of experience or asset size—and often escalate quickly from casual conversation to irreversible theft. Here’s how to protect yourself:
-
Treat Unsolicited Messages as Suspicious by Default: If someone contacts you out of nowhere claiming to represent an exchange, VC firm, wallet provider, or crypto project—especially via Telegram, Discord, or Twitter—assume it’s suspicious until independently verified. Real firms rarely initiate direct outreach without context.
-
Never Share Sensitive Information: Legitimate services will never ask for your:
Seed phrase or private key, Wallet login credentials and 2FA codes or OTPsAny request for these—regardless of branding, urgency, or professional tone—is a scam. -
Use a Hardware Wallet for Critical Assets: Hardware wallets isolate your private keys from internet-connected devices. Even if malware is installed on your system, it cannot access your keys without physical confirmation. This makes hardware wallets one of the most effective defenses against phishing, impersonation, and remote takeover attempts.
-
Secure Exchange Accounts with Security Keys, Not Just 2FA: If you use centralized exchanges,
upgrade from app-based or SMS 2FA to a hardware security key(e.g., YubiKey). These keys provide strong, phishing-resistant authentication. Also consider enabling withdrawal whitelists and locking API permissions unless needed. -
Don’t Download Files from Unverified Sources: Be highly cautious of NDAs, pitch decks, token documents, or job assessments—especially
.exe,.rar, or even PDFs—sent via chat or email. Malware can be embedded in these files to steal wallet data or compromise your device. -
Separate Wallets and Devices: Maintain separate wallets for interacting with high-risk dApps, airdrops, or mints. Keep your primary holdings in a cold or hardware wallet that never interacts with unknown contracts. When possible, use a separate browser profile or device for wallet interactions.
-
Use Antivirus and Anti-Malware Tools: Keeping your system clean matters—especially if you’re frequently engaging with Web3 tools, downloading files, or clicking links. Use trusted anti-malware tools to detect threats early.
-
Only Use Verified Support Channels: If you need help, go directly to the exchange or service’s official support page. Never accept help in Telegram or Discord chats, even if someone appears to be a moderator or admin.
-
Help Others Stay Informed: Social engineering works best when people are unaware. Share what you know with new users, friends, or family. A single conversation can prevent a major loss.
Social engineering and impersonation scams remain some of the most effective and underreported threats in crypto. They bypass smart contract audits and wallet security by targeting the user directly—through trust, urgency, and deception. While anyone can be a target, the risk can be significantly reduced through caution, verification, and the use of secure tools like hardware wallets and security keys. In a trust-less ecosystem, the best defense is informed skepticism.
- Sophisticated Phishing Attacks
Phishing attacks are one of the most commonly used delivery mechanisms for crypto scams. Unlike direct wallet drainers or social engineering cons that target individuals through conversation, phishing targets users of specific platforms or products—waiting for them to visit a fake interface, connect their wallet, or enter sensitive information.
These attacks often involve cloned websites, fake airdrop or staking portals, malicious browser extensions, and counterfeit support pages. Their goal is to mimic trusted brands closely enough to convince the user to sign a malicious transaction or enter seed phrases, passwords, or 2FA codes. There’s often no human interaction—just a convincing trap.
Phishing is particularly dangerous in crypto because transactions are irreversible. Once a wallet connects and signs an approval, or a seed phrase is submitted, funds can be drained instantly. Many victims don’t realize they were phished until their assets are already gone.
While phishing often works hand-in-hand with other attack types—such as wallet drainers or impersonation scams—it remains one of the most scalable, automated, and difficult-to-detect threats in the Web3 ecosystem.

Global Financial Impact-
Phishing remains one of the most financially devastating attack vectors in crypto, not because of any novel technical flaw, but because of its scale, automation, and high conversion rate. From high-value wallet drains to mass wallet compromises via fake mints, phishing plays a central role in enabling billions in losses.
According to Chainalysis, phishing-related crypto scams contributed to over $2.7 billion in losses since mid-2021, much of it facilitated through wallet approval traps and fake dApps. Similarly, Scam Sniffer reported that in 2023 alone, over 330,000 wallets were compromised by phishing attacks, leading to more than $295 million in asset theft—a number that likely underrepresents total damage due to underreporting.
One reason phishing is so effective is that it targets habits: users looking to mint, stake, claim, or trade often act quickly without double-checking URLs or verifying signatures. Attackers take advantage of this behavior by setting traps that appear at the top of Google searches, in Discord announcements, or Twitter replies—sometimes using sponsored ads to out-rank official project links.
Many phishing campaigns also operate in bulk, deploying drainer kits to thousands of cloned websites, collecting data automatically, and routing stolen assets through mixers and bridges. These kits are increasingly sold on underground Telegram channels as plug-and-play packages, making phishing not only effective but also widely accessible to low-skill attackers.
As crypto adoption grows, phishing continues to evolve. The rise of wallet-based authentication, Web3 gaming, and mobile DeFi apps has opened even more vectors for attackers to target users outside of traditional exchange platforms—often with devastating speed and precision.
How Sophisticated Phishing Attacks Work-
Phishing in crypto is all about deceptive interfaces. It doesn’t rely on conversation or social pressure like impersonation scams, and it doesn’t require code-level interaction like wallet drainers. Instead, phishing attacks trick users into believing they’re interacting with a legitimate platform—when in reality, it’s a near-perfect clone built to extract keys, credentials, or wallet approvals.
-
Creation of a Clone Site or App: The attacker begins by creating a fake version of a trusted Web3 platform: an NFT minting page, DeFi staking interface, wallet login portal, token launchpad, or even a wallet download site. These clones are often pixel-perfect, copying logos, user flows, and even status messages from the original site. Sometimes, entire front-end templates are reused.
-
Distribution Through High-Exposure Channels: Once the phishing site is ready, the attacker promotes it through various high-visibility methods:
-
Sponsored ads on Google or X (Twitter): that rank above the real project
-
Fake replies or announcements in Discord, Telegram, and Twitter threads
-
Malicious QR codes: in airdrop campaigns, bot replies, or fake event promotions
-
Email campaigns: mimicking official project communicationsThe aim is to catch users when they’re distracted or in a hurry—minting, searching, or claiming rewards.
-
-
Baiting the User to Act: The phishing page presents a believable prompt—such as:
-
“Connect wallet to claim airdrop”
-
“Login to view staking rewards”
-
“Mint live now — supply limited!”
-
“Security issue detected — reauthenticate”
At this point, the user is prompted to either:
-
Connect their wallet and sign a transaction (usually a token approval), or
-
Enter sensitive information such as a seed phrase, private key, or exchange credentials into a fake form
-
-
Execution of the Theft: As soon as the user completes the interaction, the attacker uses that access to:
-
Call
transferFrom()using the approved permissions -
Import the victim's wallet using the stolen seed phrase
-
Log in to exchange accounts and withdraw funds if credentials were harvestedThe phishing interface may even show a fake confirmation or redirect the user to the real site afterward—delaying the realization that something went wrong.
Unlike social engineering, there's no human engagement here—just design trickery and routine behavior being exploited. That’s what makes phishing so dangerous: it blends into normal Web3 workflows and capitalizes on moments of inattention.
-
How to Recognize Sophisticated Phishing Attacks-
Phishing sites are designed to look legitimate, which is why they work. But even the most convincing clones tend to show cracks—if you know where to look. Recognizing phishing attempts requires careful attention to detail, especially when signing transactions, entering credentials, or downloading wallet tools. Here are key indicators to watch for:
-
Suspicious or Slightly Altered URLs: Phishing sites often use domain names that are close to, but not exactly, the official project site. Examples include
uniswap-launchpad.orginstead ofapp.uniswap.org, orphantomapp.ioinstead ofphantom.app. Always verify the full domain before connecting your wallet. -
Promoted Search Results That Don’t Match the Brand: Attackers often run Google ads or Twitter promotions with malicious links posing as official platforms. These may appear above real search results, especially for keywords like “claim,” “login,” “mint,” or “staking.” Clicking these links can direct users to fake interfaces built to harvest credentials or approvals.
-
Wallet Connection Prompts That Appear Too Soon or Without Context: If a site immediately asks you to connect your wallet—or presents a transaction before you’ve taken any action—that’s a red flag. Legitimate platforms usually guide you through a clear process before requesting wallet interaction.
-
Unusual Transaction Requests: Before signing any transaction, inspect what’s being requested. Phishing sites often mask approval transactions behind vague actions like “verify,” “claim,” or “continue.” Tools like Wallet Guard or Pocket Universe can help flag suspicious approvals before they’re signed.
-
Requests for Seed Phrases or Private Keys: No legitimate Web3 platform will ever ask for your seed phrase, private key, or recovery phrase on a website or form. If you see a field asking for this information—even if the branding looks real—it’s a phishing attack
-
Unexpected Downloads or Extensions: If a site prompts you to download a browser extension or wallet file without clear instructions from a verified source, be cautious. Some phishing pages offer fake wallets or plugins embedded with malicious scripts.
-
Misspellings, Broken Links, or Missing Functionality: Even highly polished phishing sites sometimes contain small errors: typos, broken buttons, incorrect social links, or missing pages. These signs suggest the site was copied quickly or assembled with templates.
Prevention Strategies-
Phishing attacks prey on routine behaviors and momentary lapses in attention. The best defense is deliberate action: verifying sources, understanding what you’re signing, and using tools that give you visibility and control. Here's how to stay safe:
-
Always Verify URLs: Bookmark official websites and use them directly. Be cautious of domains that look nearly correct or appear as sponsored search results. Avoid connecting your wallet or signing transactions on any site unless the URL is confirmed to be authentic.
-
Use Browser Security Tools: Extensions like Wallet Guard, Pocket Universe, and Scam Sniffer analyze transaction requests and flag suspicious activity before you sign. These tools add a critical layer of defense, especially against fake approval requests
-
Never Enter Seed Phrases Online: No legitimate platform will ever ask for your seed phrase through a website or form. Wallet recovery should only happen within trusted wallet applications—not via browser pop-ups or forms linked in messages.
-
Avoid Links Shared in Chats or Comments: Discord, Telegram, and Twitter are common distribution points for phishing links. Even if a message appears to come from a moderator or verified user, avoid clicking unless it’s confirmed through an official source.
-
Use a Hardware Wallet: Hardware wallets protect your private keys by requiring physical confirmation of any transaction. Even if you land on a phishing site, the transaction can’t be approved unless you manually confirm it on the device—offering a critical last line of defense.
-
Think Before You Sign: Pause and inspect what your wallet is asking. If the action doesn’t match what you expect (e.g. “verify” when you’re not verifying anything), stop. If in doubt, don’t approve.
Phishing remains one of the most scalable and deceptive threats in crypto—not because of complex code, but because it exploits user habits and trust. A single click on a fake site or a rushed wallet signature can result in irreversible loss. Staying safe means slowing down, verifying every interaction, and using the right tools to protect your assets. In Web3, awareness is your first line of defense.
-Address Poisoning Attacks
Address poisoning is a deceptive scam tactic that exploits how users typically copy-paste wallet addresses from recent transactions in their history. Rather than attempting to gain access to a wallet, address poisoning manipulates the appearance of familiarity—tricking victims into sending funds to the wrong address by inserting a lookalike into their transaction records.
In this attack, scammers generate wallet addresses that closely resemble those of legitimate contacts—often matching the beginning and end characters—and send a zero-value or dust transaction to the victim. These fake addresses then appear in the user’s wallet transaction history, mimicking genuine past activity. If the victim later copies an address from their recent transactions, they may unknowingly paste and send funds to the attacker’s poisoned address.
The scam is effective because it doesn’t rely on malware, phishing, or social interaction. It takes advantage of user habits and interface design—specifically the common reliance on partial address matching and the assumption that recent transactions are trustworthy references.
While technically simple, address poisoning can lead to permanent asset loss with a single careless transfer—making it a quiet but serious threat for all wallet users, especially those handling frequent token transfers. Several incidents have resulted in thousands of dollars being mistakenly sent to scam wallets—highlighting how even experienced users can fall victim with just one oversight.
Impact: The Growing Threat of Wallet Poisoning Scams -
Wallet poisoning scams, also known as address poisoning attacks, have emerged as a significant threat in the cryptocurrency ecosystem. These scams involve attackers sending small transactions from addresses that closely resemble the victim's own address, aiming to deceive users into copying and sending funds to the wrong address.
Key Statistics:
-
In 2024, over 270 million address poisoning attempts targeted approximately 17 million users on Ethereum and BNB Chain.
-
These attacks resulted in at least 6,633 successful incidents, causing losses exceeding $83.8 million.
-
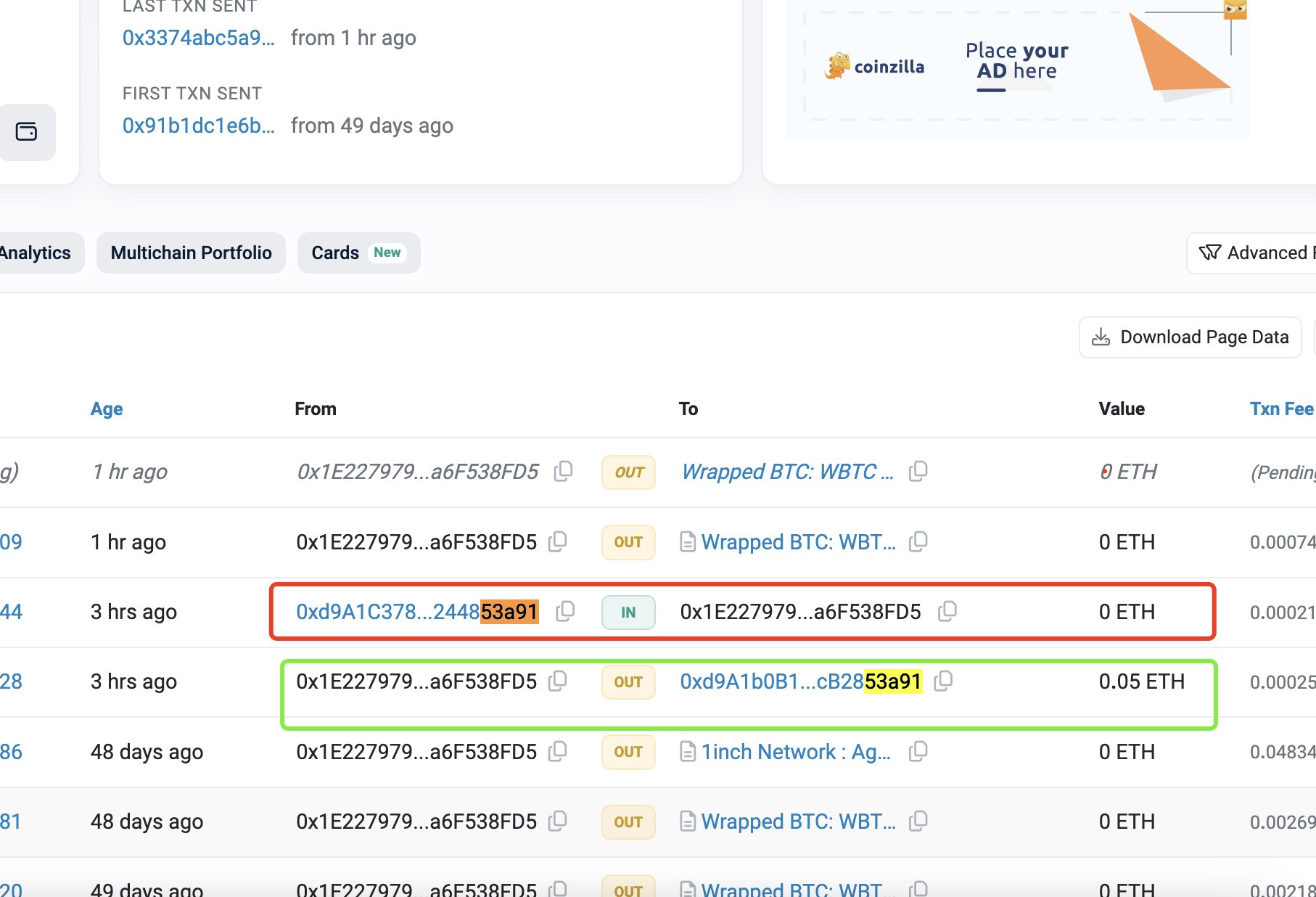
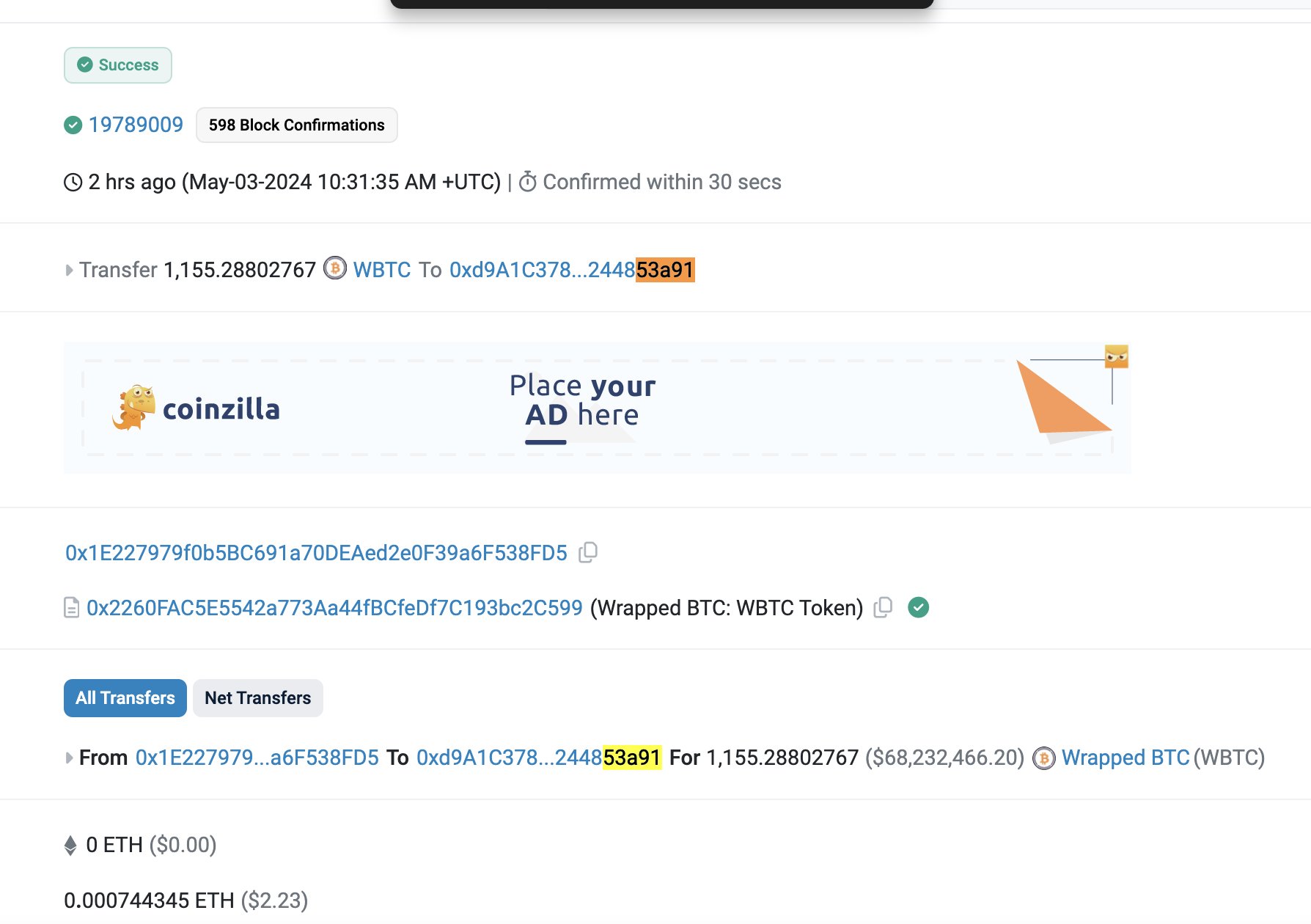
A notable incident in May 2024 involved a victim losing $68 million worth of Wrapped Bitcoin (WBTC) due to an address poisoning exploit.
-
In March 2025 alone, address poisoning scams cost the crypto industry over $1.2 million, following losses of over $1.8 million in February 2025.
These figures underscore the substantial financial impact of wallet poisoning scams and highlight the importance of vigilance and security measures among cryptocurrency users.
How Address Poisoning Attacks Work-
Address poisoning is a low-cost, high-deception tactic. Instead of stealing access or tricking users with phishing links, the attacker manipulates the user’s behavior—specifically, their habit of copying wallet addresses from recent transaction history.
Here’s how it typically plays out:
-
Scammer Generates a Lookalike Wallet Address: Using vanity address generation tools, scammers create Ethereum (or EVM-compatible) addresses that match the first few and last few characters of a target address. These lookalikes are generated at scale until they visually resemble trusted wallets. For example, 0x5fB2...D4c8 might be mimicked as 0x5fB2...D4c3.
-
Fake Transaction Is Sent to the Target: The attacker sends a zero-value or dust transaction (e.g., 0.00001 USDT or 0 ETH) from the lookalike address to the victim’s wallet. There is no payload or malicious logic—just a benign-looking transfer designed to appear in the user’s wallet history.
-
Poisoned Address Appears in Transaction History: Most wallet interfaces display only the beginning and end of wallet addresses for readability. This allows the lookalike to blend in with legitimate past activity, especially if the user frequently sends tokens to the original address being mimicked.
-
User Copies the Wrong Address Later: When the victim later needs to send funds—perhaps to a frequent contact—they may scroll through their wallet history and accidentally copy the poisoned address, believing it’s the right one. The similarity in characters tricks the eye, and wallet UIs often don’t differentiate between trusted and unknown addresses.
-
Funds Are Sent to the Attacker's Wallet: Once the victim signs the transaction and sends funds, the assets land in the scammer’s wallet. Because this was a voluntary transfer to a valid address, there’s no way to reverse it. The attacker may rotate through dozens or hundreds of poisoned wallets to avoid detection and maximize success.
How to Recognize Address Poisoning Scams-
Address poisoning is designed to blend in. It doesn’t use malicious links or suspicious prompts—instead, it quietly inserts a fake transaction into your history and waits for you to make a mistake. But with careful observation, there are clear signs that can help you spot and avoid poisoned addresses.
-
Suspicious Zero-Value or Dust Transactions from Unknown Addresses: A common giveaway is a token transfer—often of zero value, or just a few tokens—from an address you don’t recognize. These are often sent using popular tokens (like USDC, USDT, or ETH) to make the transaction appear legitimate. If you haven’t interacted with that address before, treat it as suspicious.
-
Lookalike Addresses in Your Recent Activity: Poisoned addresses are specifically crafted to look similar to ones you’ve sent funds to before, often matching the first and last few characters. Always verify the entire address—not just the beginning and end—before using it again from your history.
-
Irrelevant or Out-of-Context Transactions: If a transaction shows up in your wallet history with no clear explanation—no airdrop claim, no interaction from you, and no related activity—it may be part of a poisoning attempt. These transactions often have no effect but are placed strategically to appear in your recent activity log.
-
The Address Isn’t in Your Saved Contacts or Whitelist: If you rely on your wallet’s transaction history to find past addresses instead of using a saved contact list or address book, you’re at greater risk. Poisoned addresses can be mixed in seamlessly, so relying only on recent activity is risky.
-
Block Explorers May Show the Full PictureWallet interfaces often truncate addresses for readability (e.g., 0xA3...e9B2). Use a block explorer like Etherscan to view the full address history of a wallet before sending large amounts. If the recipient address has no prior interaction or seems new, double-check.
Prevention Strategies-
Address poisoning attacks rely on small user habits—especially copying from transaction history without verifying the address. Preventing these scams requires simple, proactive behaviors that reduce the chance of human error.
-
Never Copy Wallet Addresses from Transaction History: Avoid using your wallet’s recent activity feed as a source for recipient addresses. This is exactly where poisoned addresses are placed. If you frequently send to the same contact, store their address securely using a wallet’s address book or external contact manager.
-
Double-Check the Full Address: Don’t rely on partial address matches (e.g., first 4 and last 4 characters). Always compare the full string when copying or pasting wallet addresses. Many poison addresses are crafted to match beginning and ending characters to deceive users at a glance.
-
Use Whitelisting or Trusted Contact Features: Some wallets and exchanges offer address whitelisting or “trusted contact” lists. Enable these features to restrict transfers only to verified addresses. This eliminates the risk of copying from a poisoned history.
-
Flag and Ignore Zero-Value Transactions: If you receive a token or transfer worth 0 (or near zero) from an unknown address, treat it as suspicious. These are often the poisoned transactions meant to plant lookalike addresses in your history. Do not interact with them.
-
Use Wallets That Show Full Addresses and Warnings: Some modern wallets and extensions are beginning to display more of the full address and even flag suspicious or known-poisoning accounts. Use tools like Rabby Wallet, Wallet Guard, or Scam Sniffer to get visibility and alerts when interacting with unknown wallets.
-
Educate Team Members and Power UsersFor DAOs, fund managers, or users regularly handling large transfers, this risk should be part of operational security training. Many address poisoning losses happen because team members act on routine without verifying address integrity.
Address poisoning is a subtle but serious threat that preys on habits, not vulnerabilities. It doesn't exploit code—it exploits trust in interfaces and familiarity with past transactions. Staying protected is as simple as slowing down, verifying every address in full, and never relying on wallet history alone. In crypto, attention to detail is your strongest defense.
Scam Tokens, Fake Airdrops, Rugpulls & Honeypots
In the rapidly evolving world of Web3, not all tokens or protocols are what they appear to be. From unsolicited airdrops to manipulated liquidity traps, bad actors use deceptive tokens and fraudulent smart contracts to trick users into engaging with malicious assets or financial black holes.
These scams typically fall into four categories:
-
Scam Tokens are created solely to mislead users—often mimicking real projects or using deceptive names to appear valuable.
-
Fake Airdrops involve sending tokens to users' wallets with promises of rewards, redirecting them to phishing sites or malicious smart contracts.
-
Rugpulls are projects that appear legitimate at first but suddenly withdraw all liquidity or disable selling after users invest.
-
Honeypots are smart contracts that allow users to buy tokens, but restrict or block selling—trapping assets permanently.
Though these tactics vary, the goal is the same: bait user interaction, extract value, and disappear before victims understand what happened.
Together, they represent a growing class of on-chain scams that exploit token trust assumptions, user interface design, and DeFi mechanics—and can result in significant financial losses even without the user ever clicking a phishing link or signing a suspicious transaction.

How These Scams Work-
While scam tokens, fake airdrops, rugpulls, and honeypots differ in execution, they all revolve around manipulating users into unsafe interactions—either with misleading assets or deceptive smart contracts. Here’s how each works in practice:
1. Scam Tokens
Scammers create ERC-20 tokens with names that resemble trusted assets (e.g., ETH2.0, UNI-Reward, USDTDrop) and distribute them to thousands of wallets using airdrop or dusting methods. These tokens are either:
-
Totally worthless, created to appear valuable and lure users into trading them; or
-
Malicious, designed to trigger drainer contracts or grant approval to a scammer’s wallet when interacted with via a DEX.
Sometimes, these tokens also contain fake transfer metadata or redirect users to phishing sites under “claim” or “redeem” links.
2. Fake Airdrops
Fake airdrops are a blend of scam tokens and phishing. Users receive a mysterious token with instructions in its name or transfer note—such as:
“Claim your $500 Airdrop at airdrop-claim[.]xyz”
If the user visits the site and connects their wallet, they’re prompted to sign malicious approval transactions or enter their seed phrase, leading to wallet drains.
In many cases, the token has no actual functionality—it’s just bait to lure users to an external phishing destination.
3. Rugpulls
Rugpulls occur when a seemingly legitimate token or project abruptly removes its liquidity or disables core functions after attracting investors. This typically involves:
-
Adding a small amount of liquidity and hyping the project on Twitter, Telegram, or Discord
-
Influencer shills or bots faking momentum
-
Pulling all liquidity (or ownership) from the pool once the token price rises
Victims are left holding worthless tokens with no exit liquidity. This type of scam is especially common in memecoins and fast-moving DEX launches.
4. Honeypots
Honeypots are deceptive tokens that appear tradable but are coded to trap funds—either by fully blocking sales or by implementing hidden mechanics that make selling nearly impossible or highly unprofitable.
Here’s how they work:
-
The scammer launches a token and allows normal-looking buys with low or zero tax.
-
Once users buy in, the smart contract prevents selling altogether or enforces a very high sell tax—sometimes 50%, 90%, or even 100%.
These settings are often not visible in standard DEX interfaces and require reading the contract manually to detect.
To create the illusion of legitimacy, scammers might:
-
Simulate buying volume using bots or fake wallets
-
Add small liquidity and fake engagement on platforms like DexTools
-
Use misleading token names (e.g., $AIRDROP, $ETH2X, $MEME) and promote them in Telegram groups or Twitter threads
Victims can buy and see price movement, but when they attempt to exit, they either receive nothing or suffer massive losses due to the hidden tax logic.
How to Recognize Scam Tokens, Fake Airdrops, Rugpulls & Honeypots
These scams are designed to look legitimate, fast-moving, or rewarding—but with close observation, several red flags can help you spot the trap before engaging. Here’s what to watch for across each type:
1. Scam Tokens & Fake Airdrops
-
Tokens appear out of nowhere: If a token suddenly shows up in your wallet and you didn’t claim it, it's likely bait. Especially if its name includes “reward,” “bonus,” “airdrop,” or mimics a real project.
-
Metadata contains links: Many scam tokens include phishing URLs in the token name or transfer memo. Never click on these or visit claim sites from unknown sources.
-
You can’t trade them: Scam tokens often have no liquidity or are blocked from being swapped. Attempting to sell may result in failed transactions—or worse, a drainer interaction.
Found via unknown contracts: If a token shows up and its contract address isn't verifiable (no source code, no audit, no community recognition), it’s likely malicious
2. Rugpulls
-
No locked liquidity: Use tools like Mudra, TokenSniffer, or DexTools to check if liquidity is locked. If it isn’t, the project owners can pull funds at any moment.
-
Anons with no track record: If the devs or promoters can’t be linked to any previous legit projects and are only active during the launch window, be skeptical.
-
Sudden hype, no fundamentals: Be cautious of tokens that launch with zero utility but heavy influencer marketing or engagement farming. These are often built just to pump and dump.
Ownership not renounced: If the contract owner retains control over critical functions (like pausing trades or changing tax), they can execute a rug at any time.
3. Honeypots
-
Token can be bought but not sold: Use tools like Honeypot.is or CheckMate to test contracts before buying. If a token fails honeypot checks, avoid it.
-
High or hidden sell taxes: Some tokens don’t block selling outright but apply absurd sell taxes (70–100%) that leave you with nothing after a trade. Check tokenomics or test with a small amount first.
-
Too-good-to-be-true performance: If a token shows a perfect green chart with no red candles and constant buying—especially on new or low-volume pairs—it’s likely fake volume or a honeypot trap.
No contract source or verification: If the contract on Etherscan or BscScan is unverified, you can't see what the functions do. Always a red flag.
Prevention Strategies-
With the rise of scam tokens, malicious approvals, and deceptive on-chain mechanics, prevention is no longer optional—it’s essential. Many of these threats don’t exploit smart contract bugs; they exploit user behavior, assumptions, and trust. Fortunately, with the right habits and tools, users can significantly reduce their risk. The following strategies are designed to help you stay safe, protect your assets, and avoid falling victim to common token-related scams
-
Avoid interacting with unknown tokens: If a token appears in your wallet unprompted, do not attempt to swap, send, or approve it. Scam tokens often contain malicious contract logic or redirect users to phishing traps when interacted with on DEXes or token explorers.
-
Hide suspicious airdrops from your wallet interface: Use your wallet’s “hide token” feature to remove unwanted or unknown tokens. This helps avoid accidental interactions and keeps your interface clean, especially if you regularly receive unsolicited tokens.
-
Verify token contracts before buying: Before interacting with any new token, check it using tools like TokenSniffer, Honeypot.is, RugDoc, or StaySafeu. Watch out for unverified contracts, unlocked liquidity, high or hidden taxes, and owner-controlled functions.
-
Don’t trust chart momentum or anonymous Telegram hype: Scam tokens often simulate trading activity and get pushed into trending lists using bots. Avoid buying tokens based purely on rapid price movement, especially if they lack transparency, audits, or real community backing.
-
Use reputable aggregators for swapping: Platforms like Matcha, 1inch, and CowSwap apply filters that help block malicious tokens. Swapping through these platforms reduces the risk of interacting with contracts containing dangerous logic.
-
Test with small amounts first: If you're trying a new token or DEX pair, make a small test transaction before committing real funds. This helps reveal issues like honeypot behavior, excessive slippage, or fake liquidity.
-
Educate your communityThese scams thrive on inexperience. Share tools, red flags, and best practices with others—especially newer users—so they can avoid falling into common token traps.
Not every token that appears in your wallet is legitimate, and not every project with hype has honest intent. Scam tokens, fake airdrops, rugpulls, and honeypots exploit user trust, interface design, and DeFi mechanics to drain value without ever needing to hack anything. Staying safe means slowing down, verifying contracts, and never assuming visibility equals legitimacy.
- Crypto Blackmail and Extortion
Crypto blackmail and extortion scams involve coercive tactics used to force victims into sending cryptocurrency under threat of personal, professional, or financial harm. Unlike phishing or wallet drainers, these attacks rely not on technical deception but on emotional manipulation, psychological pressure, and social leverage.
These threats can take many forms—from classic “sextortion” scams and fake claims of surveillance to targeted campaigns threatening to leak private wallet data, dox identities, or expose online activity. In other cases, attackers gain real information through data breaches, social engineering, or public records, then use that data to legitimize their threats.
While some extortion campaigns are indiscriminate and automated—sent in bulk via email or Telegram—others are highly targeted, aimed at public figures, NFT collectors, DAOs, or those with visible on-chain assets. The goal is always the same: instill fear, create urgency, and demand crypto payments in exchange for silence or safety.
As crypto adoption grows and wallets become more traceable through public blockchains, blackmail campaigns are becoming more frequent and sophisticated. They highlight a fundamental trade-off in Web3: radical transparency can become a tool for attackers when personal privacy is neglected.

Global Financial Impact-
Crypto blackmail and extortion are escalating worldwide, with a notable surge in violent incidents across Europe. In France, a disturbing trend has emerged where cryptocurrency executives and their families are targeted for kidnappings and physical assaults. Victims have endured harrowing ordeals, including mutilations and ransom demands reaching up to €10 million, as seen in the attempted abduction of Paymium CEO Pierre Noizat’s daughter and the kidnapping of Ledger co-founder David Balland
These attacks, often orchestrated by organized crime groups, exploit the perceived anonymity and liquidity of cryptocurrencies, making them attractive for illicit activities. The rise in such crimes has prompted French authorities to collaborate with the crypto community to enhance security measures and pursue perpetrators aggressively
Globally, the increasing prevalence of crypto-related extortion underscores the need for heightened awareness and robust security practices among individuals and organizations involved in the digital asset space.
How Crypto Blackmail and Extortion Attacks Work-
Crypto blackmail and extortion schemes typically follow a predictable structure: attackers claim to possess compromising information or capabilities and demand cryptocurrency in exchange for silence, safety, or privacy. The difference lies in how they obtain leverage—whether real or fabricated—and how they deliver their threats. Here's how these attacks commonly play out:
-
Data Collection or Fabrication: Attackers begin by either acquiring real personal data or fabricating believable scenarios. Real data is often sourced from data breaches, blockchain analytics, doxxed wallet identities, or leaked email/password pairs. In more targeted cases, they track high-value wallets, social media profiles, or blockchain developers using public records, GitHub activity, or on-chain footprints.
In bulk campaigns, scammers may not have real data at all—they simply claim to have hacked the victim's computer, accessed their webcam, or obtained browsing history through malware.
-
Initial Threat and Emotional Hook: The victim receives a threatening email, DM, or message that includes enough personal detail (real or fake) to sound credible. This may involve:
-
Claims of sexual material, webcam footage, or browser activity (“sextortion”)
-
Leaked wallet address with warnings of doxxing or exposure
-
Fabricated hacking claims with warnings of ransomware deployment
-
Threats to family members, professional reputations, or social accounts
Attackers often include snippets of breached data, real wallet transactions, or passwords to appear more legitimate.
-
-
Demand for Crypto Payment: The attacker gives the victim a wallet address (typically Bitcoin, Monero, or USDT) and a deadline. The demand is often small enough to be “payable” ($300–$3,000) in mass campaigns, or much higher in targeted cases (up to millions).
Some attackers use “proof of life” techniques—for example, threatening to leak partial information if no payment is received within 24 hours. Others escalate threats with each follow-up, creating urgency and fear.
-
Continued Harassment or Ghosting: Even after payment, some attackers continue to harass victims with new demands. Others disappear entirely. In large-scale email campaigns, the attacker may never follow up at all—relying solely on fear to generate fast payments.
In more targeted attacks, victims may be surveilled, stalked, or physically threatened (as seen in recent French crypto executive kidnappings).
Prevention Strategies-
Crypto blackmail and extortion thrive on fear, visibility, and weak personal security. While not all threats are preventable, the best defense is a combination of good operational security (OpSec), privacy hygiene, and mental clarity under pressure.
-
Don’t Respond Emotionally: Scammers rely on panic. If you receive a threat, do not engage immediately. Stay calm, take screenshots, and verify the details. In most mass campaigns, no real compromise has occurred.
-
Never Send Crypto Under Threat: Paying only confirms you're vulnerable—and encourages more demands. In both fake and real cases, payment rarely guarantees safety. If you’ve received a threat, document it and report it to cybercrime units or local authorities.
-
Use a Separate Identity for On-Chain Activity: Avoid linking your real name, email, or phone number directly to your public wallet addresses. Use aliases or dedicated accounts for public-facing blockchain activity (e.g. DAOs, GitHub, ENS names).
-
Improve Your Personal OpSec: Use strong passwords, two-factor authentication, and hardware keys for all crypto platforms, social accounts, and emails. Keep your wallet recovery phrases offline, and avoid storing sensitive data on cloud services.
-
Remove Public Exposure Where Possible: If your ENS, NFT profile, or blockchain activity links directly to your identity, you’re more vulnerable to targeted blackmail. Consider rotating wallet addresses, using burner wallets, and removing unnecessary identifying info from block explorers and Web3 profiles.
-
Secure Your Devices: Keep all devices up to date with trusted antivirus software and secure browsers. Avoid clicking unknown links, downloading suspicious files, or sharing screens with strangers via Discord, Telegram, or Zoom.
-
**Report, Don’t Pay:**Platforms like Chainabuse, local cybercrime units, or crypto-native security collectives like SEAL-ISAC accept reports of extortion threats. Reporting helps track these attackers and reduce harm to others.
Blackmail scams in crypto don’t require advanced tech—they rely on fear, exposure, and emotional pressure. Whether targeted or automated, these threats can be defused by staying calm, protecting your identity, and refusing to engage on the attacker’s terms. In Web3, privacy isn’t just a feature—it’s your shield.
-Physical thefts (Wrench attacks)
While most crypto threats are digital, physical theft is a growing and dangerous reality—especially for individuals publicly associated with holding or managing large amounts of cryptocurrency. In these attacks, criminals target victims offline, using violence, intimidation, or theft to gain access to wallets, seed phrases, or devices.
Unlike phishing or protocol exploits, physical theft bypasses digital defenses entirely. Victims are often forced under duress to unlock wallets, transfer assets, or reveal recovery phrases. In some cases, attackers break into homes, intercept travelers, or conduct planned kidnappings based on on-chain visibility or social exposure.
High-net-worth individuals, crypto influencers, traders, founders, and even employees of Web3 companies are increasingly at risk—particularly in regions where law enforcement is slow or cyber-physical crime is under-reported.
As cryptocurrency becomes more mainstream and self-custody remains the norm, the line between online and offline threats is fading. Strong digital security is no longer enough. Real-world precautions are now a critical part of any responsible crypto holder’s threat model.
In recent years, physical attacks targeting crypto holders have been reported across Europe, Asia, and Latin America, with cases ranging from home invasions and robberies to full-scale kidnappings. High-profile victims include exchange executives, DeFi founders, and even everyday users traced through public wallet activity. As more wealth becomes self-custodial and publicly visible on-chain, these attacks are becoming more organized, violent, and geographically widespread—especially in countries with weak law enforcement or rising crypto adoption.

Impact: Rise of Physical Theft & Wrench Attacks in Crypto-
As crypto wealth becomes more visible, a disturbing trend has emerged: physical threats and violence to extract wallet access—commonly known as wrench attacks. These bypass digital security entirely, targeting victims directly.
Recent high-profile incidents include:
-
Paris (May 2025): A crypto CEO’s father was kidnapped and mutilated; a separate attempted abduction targeted his daughter and grandson.
-
New York (May 2025): A crypto investor allegedly tortured a businessman for weeks to gain access to crypto accounts.
-
London (May 2025): A U.S. tourist was drugged and robbed of $123,000 in crypto after entering a fake Uber.
-
France (Jan 2025): Ledger co-founder David Balland and his partner were kidnapped and mutilated during a €10M ransom attempt.
-
U.S. (2024): A crime ring conducted violent home invasions across four states, stealing over $260M in crypto.
Experts warn that as long as individuals hold high-value crypto assets, they and their families remain vulnerable—regardless of digital security. The industry is responding with improved OPSEC awareness, real-world safety protocols, and even insurance options.
How Physical Theft Happens-
Unlike online scams, physical theft involves direct confrontation or covert access to a victim’s physical environment—often driven by the perception that cryptocurrency holdings are high-value, liquid, and instantly transferable if the victim cooperates.
Here are the most common methods attackers use:
-
Targeting Through Public Exposure: Many victims are identified through public-facing activity—such as NFT collections, ENS names, Twitter/X presence, conference talks, or even on-chain wallet balances. Attackers monitor platforms like Etherscan, Arkham, and social media to build profiles on individuals likely to have access to large crypto holdings.
-
Home Invasions or Office Raids: Armed criminals break into homes or offices, threatening victims with violence unless they hand over wallet passwords, seed phrases, or unlock devices. In some cases, attackers are aware of specific cold wallet locations or safes—suggesting advance surveillance or insider information.
-
Device Theft and Coercion: Crypto holders are sometimes targeted during travel—at airports, cafes, or hotels—where laptops, phones, and hardware wallets can be stolen. Attackers may attempt to access wallet apps before the victim can trigger remote wipes or lockouts. In more extreme cases, victims are physically restrained and forced to unlock accounts under pressure.
-
Kidnapping and Ransom: There have been multiple global cases—particularly in Europe and Latin America—where crypto executives or their family members were kidnapped for ransom. Attackers demand crypto payments directly or force the victim to initiate large transfers under threat of harm.
-
Social Engineering as a Setup: In rarer but documented cases, attackers befriend or lure victims to physical locations (e.g., Airbnb meetups, fake business deals, social invites) as a pretext to access devices or initiate an ambush.
In all these cases, the threat bypasses digital safeguards. Even the strongest password or hardware wallet becomes useless when the victim is under physical threat or emotional coercion.
Prevention Strategies-
Physical threats are harder to detect and can bypass even the most secure digital setups. Prevention requires a combination of privacy, physical security, and operational discipline—especially for individuals managing or transacting large amounts of crypto.
-
Don’t Publicly Display Your Holdings: Avoid flaunting wallet balances, large trades, or screenshots of expensive NFTs and token wins on social media. Even public ENS names or collectible wallets can make you a target. Keep your crypto identity separate from your real identity whenever possible.
-
Use Cold Wallets Stored in Separate Locations: Keep your primary holdings in hardware wallets or multisig setups stored in secure, undisclosed locations—not in your home or on portable devices. Ideally, these wallets should require multiple devices or keys to access, making forced transfers much harder.
-
Avoid Routine Behavior or Predictable Habits: Don’t repeatedly access wallets, manage crypto, or talk about sensitive holdings from the same place at the same time—especially in public or while traveling. Use different IPs, devices, and environments when handling high-value accounts.
-
Travel and Meetups Require Discretion: If attending conferences or traveling with crypto-related gear, stay discreet. Don’t share your hotel, Airbnb, or travel plans publicly. Use dummy laptops or burner devices if you must travel with wallets, and avoid opening wallet apps in public spaces.
-
Split and Isolate Access: Use multiple wallets with limited balances, separating your “daily” wallet from long-term holdings. Even if one wallet is compromised under duress, the damage is contained. Avoid storing your seed phrase in a single place—and never keep it digitally accessible on your devices.
-
Set Up Emergency Controls: If possible, use wallet tools that allow you to quickly revoke approvals, freeze smart contract access, or trigger time-locked withdrawals. Services like multi-sig wallets or social recovery setups can make instant transfers more difficult—even under pressure.
-
Talk to Loved Ones About Safety: If you manage large amounts of crypto, make sure your close family or household members know how to respond in emergencies. Train them never to reveal passwords, phrases, or devices—even under threat.
-
Report Threats Immediately: If you are targeted or threatened physically, report it to local law enforcement and relevant cybercrime units. In some jurisdictions, crypto-specific extortion and theft are now treated as high-priority crimes.
While digital security is critical, protecting your physical safety is just as important in the crypto world. Stay private, stay unpredictable, and prepare for worst-case scenarios. A few extra layers of caution today can prevent devastating losses tomorrow.
4. Conclusion: Securing Users Is Fundamental to Securing the Crypto Ecosystem
While the crypto ecosystem continues to deliver on its promises of decentralization, financial autonomy, and borderless access, it simultaneously imposes a level of personal responsibility that many users—particularly newcomers—are not equipped to handle. The threats facing crypto users today are no longer limited to technical vulnerabilities; they are increasingly psychological, social, and operational in nature.
From highly coordinated pig butchering scams that exploit emotional trust, to silent wallet drainers that take advantage of token approvals, to phishing links, address poisoning, counterfeit tokens, and even physical extortion—the range and sophistication of attacks continue to grow. These threats succeed not by brute force, but by blending into familiar user behaviors and interfaces. What appears to be a legitimate DM, a routine airdrop, or a trending mint may in fact be a well-crafted attack.
This environment poses a particularly high risk to users transitioning from Web2 to Web3, older individuals unfamiliar with wallet mechanics, and anyone lacking foundational security education. The human layer has become the most exploited attack surface in Web3—and often, the least protected.
Mitigating these risks begins with awareness. Understanding how scams operate, identifying behavioral red flags, and implementing secure practices—such as verifying sources, managing token approvals, and using hardware wallets—can significantly reduce individual exposure. But personal caution alone is not enough.
Platforms, developers, and ecosystem stakeholders must take collective responsibility by integrating proactive security measures, user education, and contextual warnings directly into the user experience. Scams thrive when they are indistinguishable from legitimate activity. The industry must raise the cost of deception.
Ultimately, protecting users is not just about preventing financial loss—it is about safeguarding trust in the ecosystem. Sustainable, mainstream adoption of crypto requires that every user, regardless of experience level, has access to the knowledge, tools, and infrastructure necessary to stay secure. This is not merely a user issue—it is an ecosystem imperative.
Supported with a grant under the ETH Rangers Program by

- Additional Resources
Disclaimer : “ This article is intended for educational and informational purposes only. It does not constitute financial, legal, or cybersecurity advice. While every effort has been made to ensure accuracy, the crypto threat landscape evolves rapidly, and the information presented may not reflect the most current developments. Readers should conduct independent research and consult with qualified professionals before making decisions based on this content.
References to specific companies, platforms, or individuals are based on publicly available information and do not imply wrongdoing unless independently confirmed. The goal of this article is to raise awareness and encourage best practices for user safety and ecosystem security.”