Table of contents
1. Introduction
2. Wallet Attribution in Blockchain Investigations
-
Transaction-Based Attribution
-
Infrastructure / Interaction Attribution
-
Cross-Chain Attribution
-
Behavioral Attribution
3. The Role of OSINT in Blockchain Forensics
-
What is OSINT?
-
Why OSINT Matters in Blockchain Forensics
-
OSINT Sources for Blockchain Investigators
-
Challenges in Using OSINT for Blockchain Forensics
-
Best Practices for Investigators
4. Conclusion
1. Introduction
Tracing stolen funds on-chain is often the first step in an investigation, but it rarely tells the full story. Hackers and fraudsters move assets across multiple blockchains, making the flow complex but not impossible to follow. By tracking these transactions, investigators can build a map of how funds move, yet attribution is what truly transforms this data into intelligence. Attribution means connecting wallets and clusters of activity back to the entities operating them.
OSINT (Open-Source Intelligence) adds another crucial layer. Blockchain analysis shows how stolen funds move, and OSINT provides external context that can sometimes identify who is behind those wallets through linked communication channels, development activity, reused domains, or connected social media profiles. Investigators rely on attribution sources such as exchange records, public reports, and leaked data, and combine them with OSINT tools and techniques to connect wallets to real-world actors.
In this article, we’ll explore attribution techniques in blockchain forensics, the key sources investigators use, and the OSINT tools and methods that strengthen investigations. We’ll also highlight resources for analysts who want to advance their skills, supported by case studies that show how attribution and OSINT turn raw blockchain data into actionable intelligence.
2. Wallet Attribution in Blockchain Investigations
Attribution is the process of linking blockchain addresses to the entities or individuals operating them. In practice, this means going beyond simply tracing stolen funds to uncovering the connections that reveal common ownership or control. Hackers often spread assets across dozens or even hundreds of wallets, hoping to fragment their activity, but attribution techniques allow investigators to regroup these fragments into meaningful clusters.
Attribution is achieved through a mix of analytical techniques and intelligence sources. Some methods focus on transaction patterns and how wallets interact, others rely on infrastructure reuse, cross-chain behavior, or external intelligence such as exchange records and OSINT. In practice, investigators combine multiple approaches to build stronger attribution cases.

With this foundation in mind, we can look at the main categories in detail starting with transaction-based clustering, one of the most widely used techniques in blockchain forensics.
-Transaction-Based Attribution
One of the most common and effective approaches to wallet attribution is transaction-based clustering. This method groups wallets together by examining how they fund, send, and consolidate assets. Even when criminals scatter stolen funds across dozens of addresses, transaction flows often leave behind clear relationships that investigators can use to identify common ownership.
Common Input and Output Patterns -
A key technique in transaction-based clustering is analyzing how wallets interact through their inputs and outputs. This method works in two distinct ways when attackers move funds through centralized exchanges, and when they deliberately avoid them.
-
Multiple addresses sending funds into the same deposit wallet (CEX, broker, or laundering service).
-
Several wallets receiving funds from the same withdrawal batch.
-
Stolen funds from different hacks consolidated into a previously used wallet.
-
Assets split into multiple wallets and later recombined at one destination (exchange, OTC desk, broker).
-
Collector addresses in phishing scams that aggregate hundreds of victim inflows.
Example: The Inferno Drainer contract (0x000037bB05B2CeF17c6469f4BcDb198826Ce0000) illustrates how common input and output patterns enable attribution. Victim wallets from multiple phishing campaigns all funneled stolen assets into this same contract, which then forwarded the funds to attacker-controlled collector wallets. By observing the convergence of inflows and the redistribution of outputs, investigators were able to link separate scams back to the same malicious infrastructure.
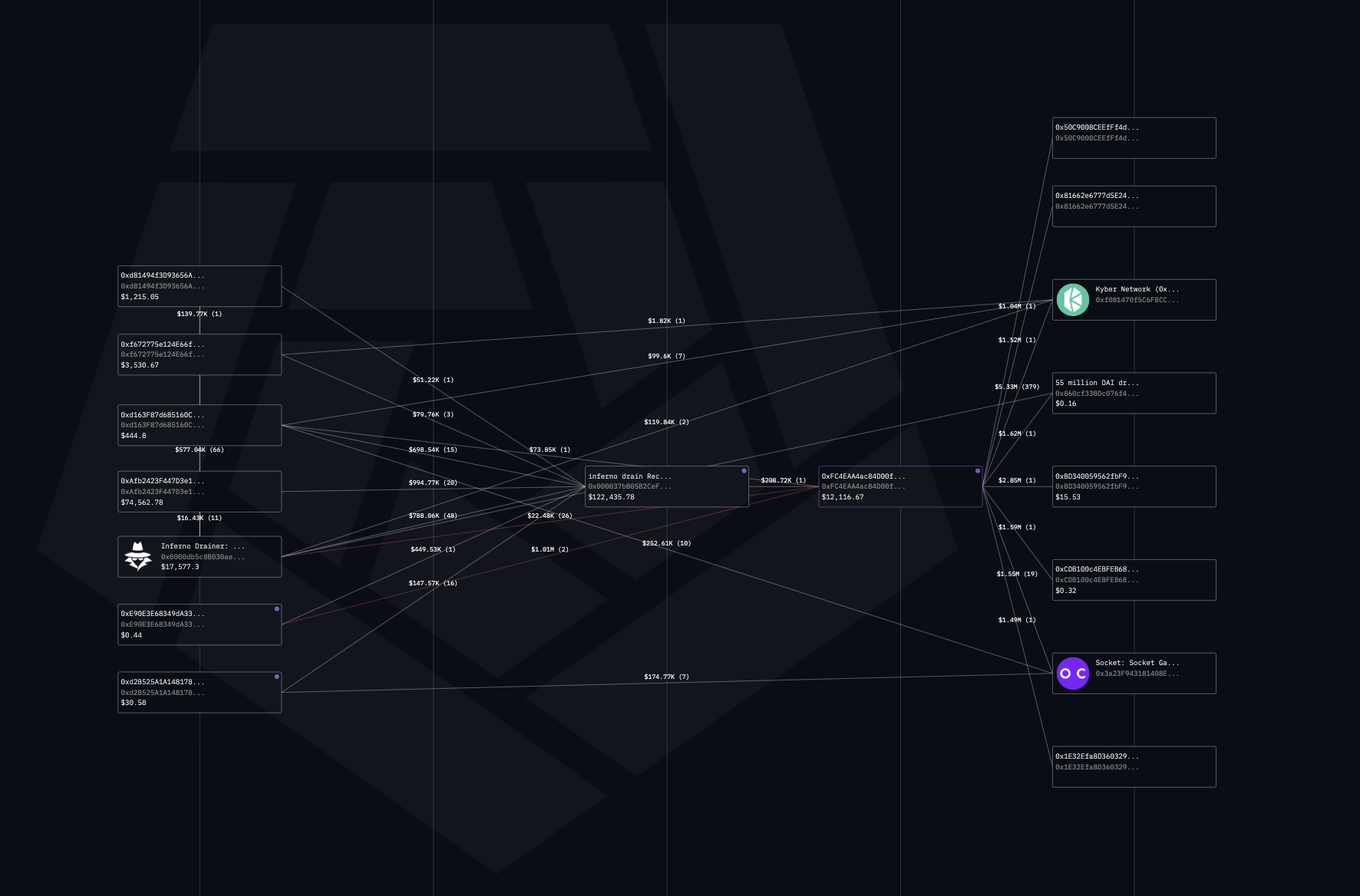
Gas-Fee or Funding Wallet Attribution -
Attackers often rely on a single wallet to distribute small amounts of native tokens (ETH, BNB, TRX, etc.) that enable transactions. Tracing these feeder wallets allows investigators to uncover clusters of attacker-controlled addresses
-
Multiple wallets topped up with identical gas amounts within a short timeframe.
-
A feeder wallet using stolen funds from a previous hack to finance a new operation.
-
Gas supplied through Tornado Cash withdrawals or instant swap services like ChangeNOW, Exch, etc.
-
Private bridge funding where direct links are hidden, requiring manual time correlation to match deposits and withdrawals.
-
Funding patterns exposing entire clusters of child wallets that would otherwise appear unrelated.
Example: Gas-Fee Attribution in the WazirX Hack
During the WazirX hack of July 18, 2024, attribution was strengthened through gas-fee analysis. Investigators traced activity back to a test wallet, 0x6eedf92fb92dd68a270c3205e96dccc527728066, which had been active on July 10, 2024, eight days before the main incident. This wallet received six separate 0.1 ETH top-ups from Tornado Cash, which were used to fund test transactions involving SHIB tokens from the attacker’s multisig.
Peel Chains and Splitting Flows -
By mapping wallets as nodes and transactions as edges, investigators can visualize hidden relationships. Graph structures often expose clusters and laundering routes that aren’t obvious from raw transactions.
-
Wallets repeatedly interacting with the same collector or broker.
-
Convergence of multiple laundering paths into one endpoint.
-
Star-shaped patterns showing a single funding wallet supplying many children.
-
Long linear chains that highlight peel-style laundering.
-
Dense clusters around exploit contracts or drainer services.
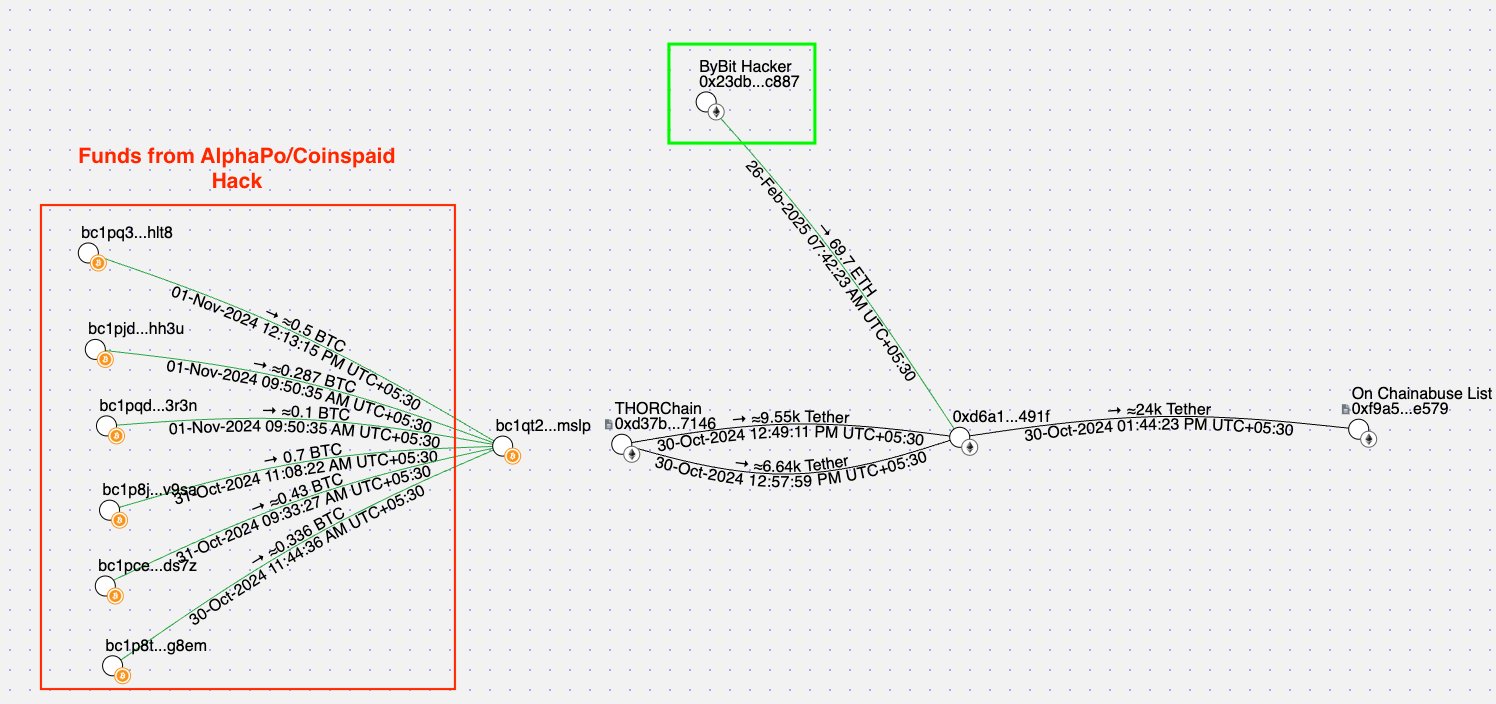
Example: A clear case of peel chain attribution was seen during the laundering of funds from the Bybit hack. Stolen assets were funneled through a consolidation address on Ethereum (0xd6a1643c40cc3dbe6e27c9281e8dfb135e30491f) before being moved into Bitcoin. One of the BTC addresses used in this laundering path
(bc1qt2wghg5xd346m06hmvrw0mnjwtfeeksagsmslp) was later linked to another BTC address (bc1qd5j8sd04hf4qem0x0ytl56w909nse4pgv9yt82) already associated with the AlphaPo/Coinspaid hack of 2023. This overlap revealed how the same laundering infrastructure was reused across multiple high-profile incidents, allowing investigators to connect the Bybit hack to past exploits.
Transaction Graph Analysis -
By mapping wallets as nodes and transactions as edges, investigators can visualize hidden relationships. Graph structures often expose clusters and laundering routes that aren’t obvious from raw transactions.
-
Wallets repeatedly interacting with the same collector or broker.
-
Convergence of multiple laundering paths into one endpoint.
-
Star-shaped patterns showing a single funding wallet supplying many children.
-
Long linear chains that highlight peel-style laundering.
-
Dense clusters around exploit contracts or drainer services.
Transaction-based attribution remains one of the most reliable methods in blockchain forensics. By analyzing inputs, outputs, feeder wallets, peel chains, and transaction graphs, investigators can uncover relationships that attackers try to conceal. Even when hackers rotate addresses or fragment funds, the way money moves leaves behind patterns that can be clustered into a coherent picture, turning scattered wallets into attributable networks.
- Infrastructure / Interaction Attribution
Hackers and scam operators often reuse the same infrastructure across multiple campaigns. Unlike transaction-based clustering, which focuses on flows of funds, infrastructure attribution looks at the technical components attackers depend on such as smart contracts, exploit code, approval mechanisms, and interaction patterns. Even if the wallets themselves change, the infrastructure often stays the same, leaving behind reliable attribution markers.
Drainer and Exploit Contracts -
-
Phishing operations often rely on smart contract drainers (e.g., Inferno Drainer, Monkey Drainer).
-
Thousands of victim wallets may approve the same contract, making it a natural attribution anchor.
-
Even when operators cycle through new collector wallets, the consistent use of one drainer contract ties the activity together.
Malicious Approvals and Interactions -
-
Victims tricked into approving malicious spenders (ERC-20 approvals, NFT approvals) create repeatable patterns.
-
Dozens or hundreds of approvals to the same malicious contract suggest a single campaign or operator.
-
Attribution is possible by mapping all wallets that interact with the same spender or contract function.
Exploit Code Reuse -
-
Hackers often reuse the same exploit contracts or payloads across multiple attacks.
-
When the same exploit bytecode appears in different incidents, it strongly suggests either the same group or a shared toolkit.
-
Linking these exploit deployments helps cluster wallets across hacks that would otherwise look unconnected.
Deployment Wallets and Contract Funding -
-
Many malicious contracts are deployed and funded by the same developer wallet.
-
By tracing deployment addresses, investigators can attribute multiple malicious contracts even across different campaigns to the same actor or group.
Note: Infrastructure and interaction attribution often overlaps with smart contract development and auditing, which can be highly technical. This section is simplified to remain understandable for investigators without a coding background. The goal is not to explain contract bytecode, but to highlight how repeated use of the same malicious contracts, approvals, or exploit infrastructure creates attribution opportunities.
- Cross-Chain Attribution
Hackers rarely keep stolen funds on a single blockchain. To increase complexity and reduce the risk of seizure, they often move assets across multiple chains using bridges, swap services, and stablecoins. This process, known as bridge hopping, creates attribution opportunities because the same actors typically reuse preferred cross-chain routes. By analyzing how assets move between ecosystems, investigators can connect wallets across chains and attribute them to the same operators.
Cross-chain attribution focuses on identifying how funds leave one chain, how they appear on the next, and which addresses or services consistently act as the connection points.
Bridging and Stablecoin Laundering -
-
Stolen ETH often converted into USDT or USDC, then bridged to chains like Tron or BNB Chain where liquidity is high.
-
Stablecoins serve as the preferred medium for laundering because they’re easily off-ramped.
-
Investigators can connect wallets by observing which addresses repeatedly receive bridged stablecoins after hacks.
Repeated Use of Specific Bridges -
-
Groups often reuse the same bridges (e.g., Allbridge, Multichain, THORChain, Wormhole) across incidents.
-
Even when wallet addresses change, the consistent infrastructure choice forms an attribution fingerprint.
-
Monitoring bridge inflows and outflows helps investigators match source chain wallets with destination chain recipients.
Wrapped Assets and Synthetic Tokens -
-
Launderers often rely on wrapped assets (wETH, wBTC, bridged USDC).
-
By tracing these wrappers, analysts can follow stolen assets even after they move into different ecosystems.
-
Patterns emerge when wrapped assets repeatedly land in the same destination wallets or exchanges.
Convergence at OTC Brokers and Cash-Out Points -
-
Multiple hacks often converge at the same OTC broker addresses especially on Tron USDT, which is a popular endpoint.
-
Repeated convergence at these off-chain liquidity providers shows shared ownership or group-level laundering.
-
Linking new inflows to these endpoints can attribute fresh hacks to known actors.
Timing Correlation in Private or Semi-Private Bridges -
-
Privacy-oriented bridges (e.g., anonymized swaps or semi-private protocols) obscure direct links.
-
Investigators use time-based analysis: matching deposit timestamps on one chain with withdrawals on another chain that occur within tight windows.
-
While not deterministic on its own, this method strengthens attribution when combined with behavioral or infrastructure evidence.
Example: Lazarus Group and Yicong Wang
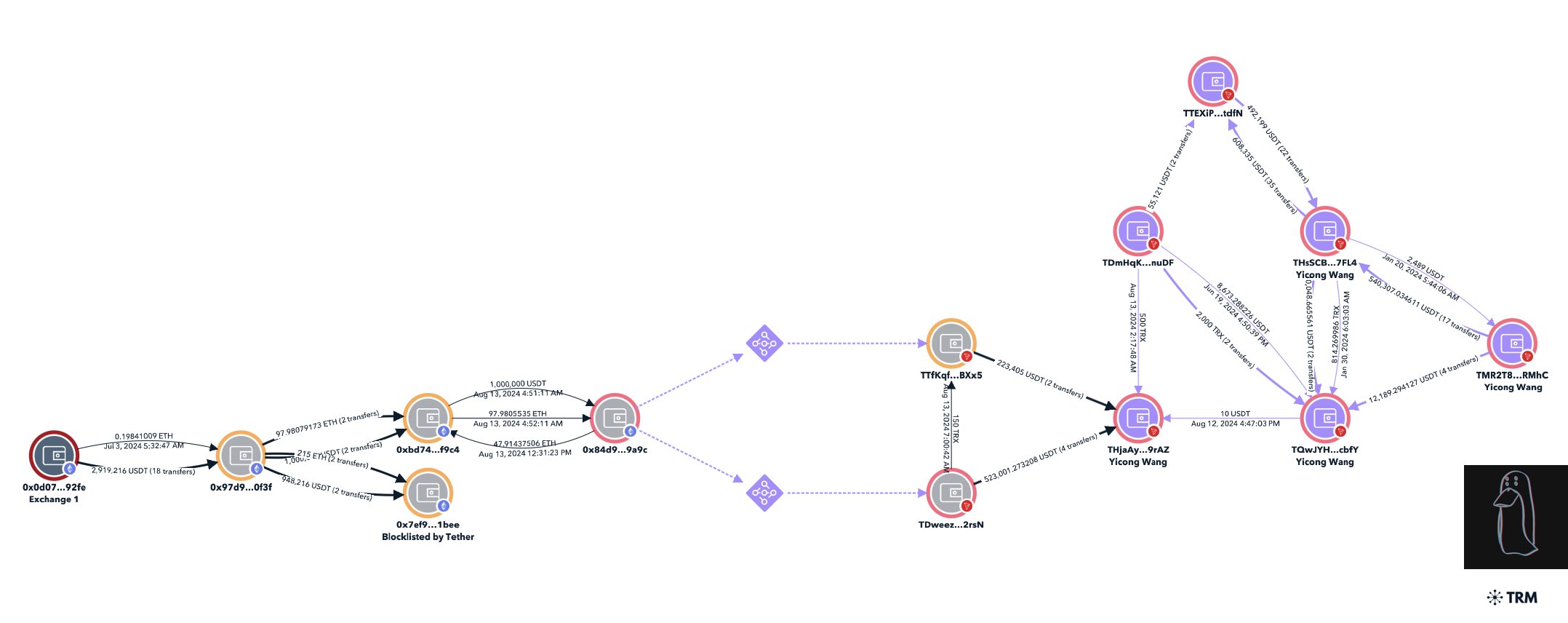
A strong demonstration of cross-chain attribution comes from the Lazarus Group laundering stolen funds with the help of OTC trader Yicong Wang. As first documented by ZachXBT (October 2024), funds from the Alex Labs exploit (May 2024) and the Irys phishing attack (July 2024) were laundered across Ethereum and Tron using privacy protocols and bridge hopping.
-
Ethereum Layering: Funds from both hacks were deposited into privacy protocol contracts, then withdrawn into fresh wallets. This fragmented the trail but preserved timing and amount patterns investigators could align.
-
Bridge Hopping: On August 13, 2024, commingled ETH from both incidents was bridged to a Tron address linked to Wang. Matching deposits and withdrawals across chains exposed the cross-chain movement.
-
Tron Laundering: Blacklisted Ethereum wallets later transferred hundreds of thousands of USDT into Wang’s known Tron wallets, tying the activity to his OTC operations.
By applying transaction matching, timing correlation, and multi-chain analysis, investigators connected more than $17 million in stolen funds across Ethereum and Tron.
Credit: Investigation originally reported by ZachXBT
Key Takeaway: Cross-chain attribution shows that even when criminals hide behind bridge hopping, the flows are rarely random. Consistent bridge choices, stablecoin destinations, and repeated convergence at OTC brokers create fingerprints that investigators can track across ecosystems.
Cross-chain attribution relies heavily on analyzing bridge hopping following how assets move between chains through swaps, stablecoins, and wrapped tokens. Before attributing any wallet using this method, investigators must carefully analyze bridge transactions, since even small mistakes in timing or transaction matching can redirect an entire case toward the wrong actor. Precision in mapping bridge flows is critical, as cross-chain missteps can create false connections and undermine attribution.
Investigator’s Note: Cross-chain attribution can be challenging because privacy bridges and synthetic tokens obscure direct connections. In some cases, it’s impossible to tie funds to a group at the first hop. But as funds move further, patterns of reused bridges, convergence points, and stablecoin recipients on other chains often reveal the operators. This makes long-term monitoring across ecosystems a critical part of attribution.
- Behavioral Attribution
Attackers can rotate wallets, bridge across chains, and scatter funds, but they often leave behind behavioral fingerprints that persist across incidents. These recurring patterns act like a digital signature. Just as individuals have unique handwriting or routines, hackers have consistent preferences in how they move funds, what tools they use, and when they transact. By analyzing these behavioral and transactional habits, investigators can cluster wallets and link new activity to known groups even without direct infrastructure or CEX data.
Timing Habits -
-
Consistent Hours: Transactions executed within the same daily time windows often reflect the attacker’s timezone.
-
Operational Rhythms: Some groups always move funds late at night (their local time) to avoid exchange monitoring.
-
Batch Activity: Laundering operations may occur in bursts — e.g., a series of transfers every 10 minutes, revealing automation.
Stablecoin and Asset Preferences -
-
Many actors consistently convert stolen assets into USDT, especially on Tron, because of its liquidity and OTC access.
-
Some prefer DAI or USDC depending on their exit markets.
-
By tracking consistent stablecoin choices, investigators can cluster seemingly unrelated hacks.
Protocol and Route Choices -
-
Attackers develop habits around DEXs and bridges.
-
Example: Always swapping through Uniswap v3, then bridging via Multichain.
-
Some groups prefer Curve pools for large stablecoin swaps due to deep liquidity.
-
Repeated reliance on the same route builds a strong attribution fingerprint.
Fixed Denominations and Transaction Style -
-
Privacy mixers like Tornado Cash encourage withdrawals in set denominations (1 ETH, 10 ETH, 100 ETH).
-
Some actors always use the same denomination (e.g., 10 ETH), creating a pattern.
-
Peel chains often move near-identical amounts step by step, another behavioral tell.
Cash-Out Consistency -
-
Different hacks often converge at the same OTC brokers or laundering endpoints.
-
For example, funds from multiple campaigns may ultimately land at the same Tron USDT broker wallet, linking them together.
Behavioral attribution highlights that while wallets can be replaced, habits are much harder to hide. Timing patterns, stablecoin preferences, and repeated laundering routes often act as fingerprints that tie operations together. Still, these signals should always be cross-checked with other attribution methods to avoid false connections, ensuring that behavioral clues strengthen investigations rather than mislead them.
The Role of OSINT in Blockchain Forensics
- What is OSINT?
Open-Source Intelligence (OSINT) is the practice of collecting, analyzing, and interpreting information from publicly available sources. Unlike classified or proprietary intelligence, OSINT relies on data that anyone can access if they know where to look and how to connect the dots.

In the context of blockchain forensics, OSINT includes everything from social media posts, online forums, and domain records to leaked databases, GitHub repositories, or news reports. These sources often contain fragments of information wallet addresses shared in a Telegram channel, phishing domains embedding deposit addresses, or developer activity tied to GitHub commits that, when cross-referenced with on-chain data, provide critical attribution clues.
At its core, OSINT transforms open data into actionable intelligence. For blockchain investigators, this means bridging the gap between pseudonymous wallet addresses and real-world actors, helping to uncover scams, track illicit funds, and identify threat networks.
- Why OSINT Matters in Blockchain Forensics
Blockchain forensics alone can map the flow of funds across addresses, exchanges, and protocols, but it often stops short of revealing the people or organizations behind those transactions. This limitation exists because blockchains are pseudonymous by design wallet addresses serve as identifiers, but they carry no inherent link to a real-world identity. That is where OSINT becomes indispensable.
OSINT matters because it provides the missing context. Threat actors frequently leave digital footprints in open sources, whether intentionally or through operational mistakes. A scammer might post a deposit address on Twitter to promote a token presale, register a phishing domain that embeds their wallet, or reuse the same username across Telegram and GitHub. Each of these traces can be collected, verified, and connected to on-chain evidence, enabling investigators to move from what happened on the blockchain to who made it happen.
Beyond attribution, OSINT also strengthens the credibility and impact of forensic findings. A report showing only wallet flows might illustrate technical skill, but a report enriched with OSINT screenshots of posts, domain records, exchange announcements provides a compelling story that regulators, journalists, or law enforcement can act upon. In short, OSINT turns blockchain forensics into a comprehensive investigative discipline, bridging the gap between pseudonymous ledgers and real-world accountability.
- OSINT Sources for Blockchain Investigators
Open-Source Intelligence (OSINT) is only as powerful as the sources an investigator can identify, access, and interpret. In blockchain forensics, different types of open data serve different roles some provide direct wallet leads, while others give supporting context that strengthens attribution. Below is a breakdown of the most important OSINT sources investigators rely on.
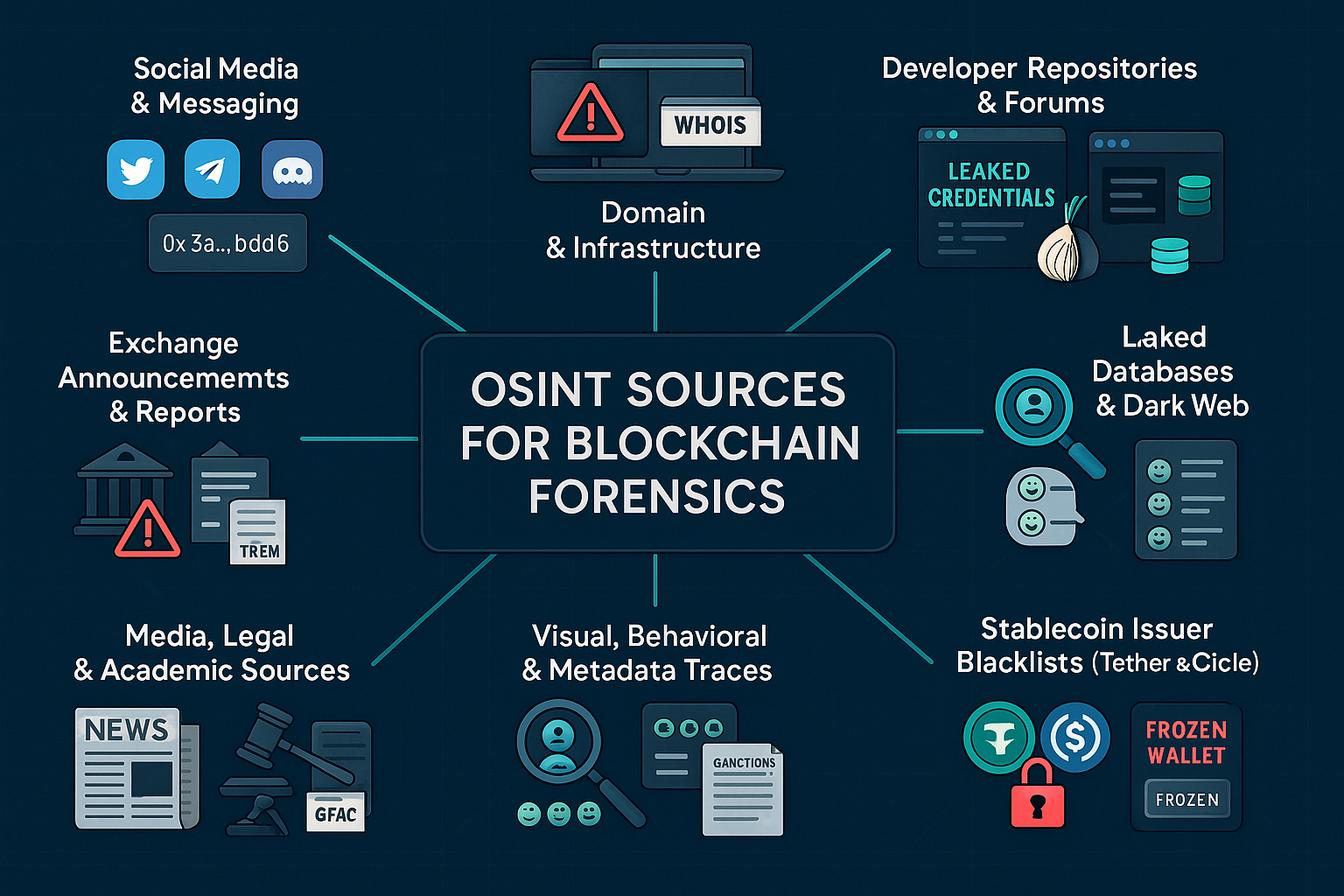
Social Media and Messaging Platforms -
Social networks and messaging apps are among the richest sources of attribution clues. Threat actors frequently expose themselves here, either out of necessity or carelessness. For investigators, these platforms often provide the first breadcrumbs that can be tied back to on-chain activity.
-
Twitter/X – Commonly used for token presale promotions, NFT shills, and scam campaigns. Investigators often find wallet addresses directly posted in threads or replies. Even after deletion, archived posts and screenshots can remain valuable evidence.
-
Telegram & Discord – While these platforms are widely used for managing legitimate crypto communities, they are also major hubs for scam groups. Many wallet drainers actively promote their services on Telegram, sharing proof-of-work screenshots, service prices, or even customer testimonials. Presale addresses, phishing links, and laundering instructions are also frequently dropped in group chats.
-
Reddit, TikTok, YouTube – Scammers often run cross-platform promotions, embedding deposit addresses in video overlays or description boxes to attract victims.
-
AI-Powered Search Tools – Platforms like Perplexity or other AI-driven engines can be useful for quickly surfacing mentions of wallet addresses, usernames, or scam campaigns across publicly available data. While these should never replace manual verification, they can accelerate discovery of sources that might otherwise be missed.
Practical Tip:
-
Always archive posts and collect metadata (username, date/time, group/channel links) before cross-referencing them with on-chain data.
-
Paste suspicious wallet addresses into social media search bars or AI search tools to check for past mentions. Sometimes you’ll uncover Telegram group promotions, Reddit threads, or scam reports tied to the same wallet.
-
Keep in mind that neither a single social mention nor an AI-surfaced hit is enough for strong attribution. Use these as leads to investigate further your skill as an investigator lies in proving connections with multiple corroborating data points.
Domain and Infrastructure Records -
Web infrastructure is another critical OSINT layer for blockchain investigations. Phishing campaigns, scam websites, and malicious infrastructure often reveal wallet addresses or operational details that can be directly tied to illicit activity.
-
WHOIS Records – Even when partially redacted, domain registration dates, hosting providers, and reused email addresses can establish patterns across multiple scam sites. Investigators often find the same operator running dozens of domains from a single hosting account.
-
DNS & SSL Certificates – DNS history and SSL fingerprints can link domains together. Threat actors often recycle SSL certificates across multiple scam sites, which becomes a strong attribution signal when several fake airdrop or drainer sites share the same certificate.
-
Phishing Websites – Many scams embed wallet addresses directly into their HTML or JavaScript, allowing investigators to pivot straight from the website to on-chain tracing. Even if the site is quickly taken down, the address remains on-chain.
-
Tools & Monitoring – Public OSINT tools make this work much easier. Platforms like urlscan.io, RiskIQ, SecurityTrails, and DomainTools allow investigators to map infrastructure connections quickly. There are also Telegram channels and bots dedicated to monitoring domain changes. Site Sentry, for example, alerts investigators when phishing sites or scam front ends update or switch infrastructure, providing early warnings of new impersonation scams.
Practical Tip:
-
Always use domain archival tools (e.g., Wayback Machine, urlscan.io) to capture snapshots before takedown.
-
Track infrastructure changes with monitoring bots front-end updates often signal active scam operations.
-
Treat impersonation scams seriously: fake domains mimicking exchanges, wallets, or projects are some of the most common ways victims are lured into draining schemes.
Developer Repositories and Community Forums -
Technical communities can unintentionally leak valuable breadcrumbs that help investigators attribute on-chain activity. Many scam projects begin with developers or promoters leaving traces in open repositories, forums, or blogs.
-
GitHub – Developers may inadvertently commit test wallets, API keys, or identifiers into code repositories. In rug pulls or malicious smart contracts, analyzing the GitHub repo linked to the project can reveal the true authors or connected accounts. Investigators have also seen scammers reuse the same GitHub handle across multiple fraudulent projects.
-
Examining Threat Actor Repositories – Looking at confirmed repositories tied to nation-state groups or cybercrime actors (such as DPRK IT workers) can uncover broader networks.
-
These repos may show repeated coding styles, reused infrastructure, or links to partner accounts.
-
In some cases, the same actor manages multiple identities across different repositories and platforms, which becomes clear once code commits, usernames, or email addresses are compared.
-
This method is particularly useful for identifying when sanctioned groups are quietly operating under new aliases.
-
-
Bitcointalk & Crypto Forums – Still active in the crypto underground, these forums host project announcements, presale promotions, and scam accusations. Threads often contain wallet addresses, contract deployments, or transaction hashes that can be cross-referenced on-chain. Many early rug pulls left their first footprints here.
-
Medium & Substack – Fraudulent projects often publish “official” guides and how-to posts with wallet addresses embedded. These blogs serve as public records of the addresses used to solicit funds and can later be matched with scam activity on-chain.
-
Other Dev/Community Spaces – Even smaller platforms like GitLab, Notion, or Telegram-linked developer hubs can leak operational details. Documentation files sometimes expose contract deployer wallets or infrastructure ties.
Practical Tip: Always cross-validate any wallet or domain reference you find in these spaces with blockchain activity. A GitHub commit or forum post may point to an address, but only transaction analysis can prove it was actively used in fraud. Repositories connected to known actors (like DPRK IT workers) are particularly valuable, but they require careful pattern recognition and correlation to avoid false positives.
Leaked Databases and Dark Web Markets -
While more sensitive to use, leaked data and darknet forums can provide high-value attribution leads when carefully and ethically handled. These sources often contain identifiers emails, usernames, or wallet addresses that connect pseudonymous blockchain activity to real-world actors.
-
Credential Dumps – Exposed email-password pairs from data breaches can sometimes be linked to centralized exchange accounts or crypto services later abused by threat actors. For example, a leaked Gmail address reused on a Binance account may appear in blockchain withdrawal patterns.
-
Dark Web Forums & Marketplaces – Fraudsters frequently advertise stolen accounts, SIM swaps, malware logs, or “crypto cashout services.” Wallet addresses posted in these forums often overlap with laundering flows seen on-chain. Monitoring these spaces helps investigators understand attacker infrastructure and cashout methods.
-
Paste Sites – Public paste platforms like Pastebin, Ghostbin, or AnonFiles occasionally host dumps of wallet lists, scam kits, or domain infrastructure. These are often tied to phishing campaigns or sold “turnkey” scam operations.
-
Breached Data Sources – Some platforms aggregate leaked or breached data in searchable formats, giving investigators access to identifiers that can be pivoted into blockchain investigations:
-
Have I Been Pwned (HIBP) – Free service to check if an email has appeared in a breach.
-
Dehashed – Paid OSINT tool to query emails, usernames, IPs, and domains across leaked datasets.
-
Intelligence X – Search engine indexing leaked data, darknet sites, and paste dumps.
-
BreachForums / successor marketplaces – Known hubs for trading breach data and crypto accounts. (⚠️ Investigators must use extreme caution here.)
-
Practical Tip:
-
Always operate with strict OPSEC (segregated machines, VPNs, anonymization) when accessing dark web sources.
-
Treat leaked data as correlation points, not conclusions. A reused email or handle should be validated with on-chain evidence before attribution.
-
Use legal and ethical channels wherever possible—for example, HIBP or Dehashed provide compliant access without direct interaction with criminals.
Exchange Announcements and Public Reports -
Crypto exchanges and industry security groups routinely publish valuable intelligence that investigators can leverage. These sources often contain pre-verified data points—such as confirmed hacked wallets or frozen funds—that can strengthen attribution when layered with on-chain analysis.
-
CEX Announcements – Major exchanges like Binance, Coinbase, Kraken, and OKX frequently issue alerts when freezing funds tied to hacks or scams. These announcements sometimes list specific wallet addresses or transaction hashes. For example, Binance has repeatedly published updates when seizing or freezing assets linked to Lazarus Group exploits.
-
Security Firms & Community Projects – Industry players such as TRM Labs, Elliptic, SlowMist, and PeckShield regularly publish reports containing tagged wallets, laundering typologies, and incident analysis. Independent investigators like ZachXBT also share highly detailed breakdowns of scams and hacks, which often become starting points for broader forensic inquiries.
-
Public Databases & Reporting Platforms – Crowdsourced and semi-formal databases such as Chainabuse, ScamSniffer, CoinHolmes, and SEAL-ISAC aggregate community-reported scams, tagged addresses, and incident reports. These repositories act as early-warning systems for emerging threats and can provide pivot points for investigations.
Practical Tip:
-
Treat all external tags as enrichment, not proof. While exchange announcements are usually reliable, third-party reports may contain errors or outdated information.
-
Always cross-validate tagged addresses against blockchain transaction activity before including them in an investigation report.
-
Use these reports to save time: instead of reinventing the wheel, build on confirmed intelligence and expand the investigation into new directions.
Visual, Behavioral, and Metadata Traces -
Some of the most subtle but often powerful OSINT comes from analyzing human behavior. Even sophisticated actors frequently reuse digital patterns that can be connected across platforms and wallet activity.
-
Reused Handles & Avatars – Many actors recycle the same usernames, display names, or profile pictures across Telegram, Discord, Twitter, GitHub, and even darknet forums. Identifying these overlaps can link multiple identities to a single operator.
-
Activity Timing – The timestamps of posts, messages, or commits often align with wallet transaction activity. This can suggest a threat actor’s likely time zone or working hours, which is especially valuable when combined with other attribution clues (e.g., DPRK activity patterns).
-
Language & Style – Writing patterns such as repeated spelling errors, preferred emojis, catchphrases, or meme usage can help cluster accounts that claim to be separate identities. Linguistic analysis (stylometry) is particularly useful when scammers operate multiple personas.
-
Metadata from Files & Images – Sometimes, images, PDFs, or documents shared by actors retain hidden EXIF data, timestamps, or software tags. These details can reveal creation tools, time zones, or even device fingerprints.
Practical Tip:
-
Treat behavioral and metadata traces as supporting evidence, not conclusive proof. A reused handle or matching posting time may suggest a link, but attribution requires corroboration with on-chain flows or stronger OSINT.
-
When layered with blockchain evidence such as matching wallet activity patternsthese subtle traces become powerful in building strong attribution cases.
Media & News Sources -
Traditional OSINT remains a critical complement to blockchain investigations. While most attribution happens online, journalism, legal records, and academic research often provide authoritative data points that strengthen an investigator’s case.
-
News Reports – Journalists covering major hacks, scams, or exchange breaches frequently include wallet addresses shared by victims, exchanges, or regulators. For example, outlets like Reuters or Coindesk often publish official addresses tied to Lazarus Group exploits or large-scale rug pulls. These can serve as pivot points for deeper forensic analysis.
-
Court Documents & Sanctions Lists – Legal filings, indictments, and sanctions notices (e.g., OFAC, Europol, DOJ, UN reports) sometimes reveal previously unknown wallet addresses, aliases, or infrastructure used by suspects. These sources carry high credibility and are invaluable for attribution in compliance-driven investigations.
-
Academic Papers & Research – Universities and blockchain research groups occasionally release datasets on laundering methods, darknet wallets, or mixing techniques. These studies provide structured intelligence that investigators can incorporate into casework or use to validate trends.
Practical Tip:
-
Use structured archiving for these materials. Court filings and sanctions data, in particular, should be stored and indexed for long-term use, as they often become reference points in future cases.
-
Treat media reports as secondary confirmation always cross-validate published addresses and claims with blockchain transaction data before attribution.
Public Blacklists and Threat Feeds -
Another critical OSINT source for blockchain investigators is the growing ecosystem of public blacklists, threat feeds, and crowdsourced reporting platforms. These services aggregate wallet addresses linked to scams, phishing campaigns, hacks, and sanctioned entities, often updated in near real time. They are especially valuable for early warning and enrichment, helping investigators pivot quickly into on-chain analysis.
-
Community Platforms – Services like Chainabuse, ScamSniffer, and CryptoScamDB allow users to submit and share reports of suspicious addresses. These platforms crowdsource intelligence from victims and independent investigators, providing quick visibility into emerging scams.
-
Industry Threat Feeds – Professional intelligence providers such as MistTrack, Crystal, TRM Labs, SlowMist, and CipherTrace maintain structured feeds of tagged wallets associated with hacks, laundering, darknet markets, or ransomware. These are often integrated into compliance workflows for exchanges and investigators.
-
Sanctions and Government Lists – Official datasets such as the OFAC SDN list, Europol notices, and UN sanctions updates frequently include wallet addresses tied to nation-state APTs, cybercriminal groups, and money laundering networks. These addresses are among the highest-confidence attribution signals.
-
Exchange-Shared Feeds – Some centralized exchanges (e.g., Binance, Coinbase) occasionally publish wallet addresses they have frozen following hacks. These addresses are quickly mirrored in threat feeds and become strong pivot points for tracing laundering flows.
Practical Tip:
-
Blacklists and feeds are excellent starting points, but they are not infallible. False positives, outdated tags, and misattributions are common.
-
Always treat them as leads, not conclusions every tagged address should be independently validated through blockchain transaction analysis before being used in an investigation report.
-
Combining multiple feeds increases coverage but also raises noise; filtering and verification are critical parts of the investigator’s craft.
Stablecoin Issuer Blacklists (Tether & Circle) -
Stablecoin issuers provide a unique layer of OSINT because, unlike decentralized protocols, they retain centralized control over their tokens. Both Tether (USDT) and Circle (USDC) actively freeze wallets engaged in illicit activity, creating high-value attribution points for investigators.
-
Tether (USDT) – Tether frequently blacklists wallets tied to hacks, scams, ransomware, darknet markets, and sanctioned entities. Once frozen, these wallets can no longer move USDT, but their on-chain history remains visible, providing investigators with confirmed illicit clusters to map.
-
Circle (USDC) – Circle operates similarly, working closely with regulators, compliance teams, and law enforcement to freeze wallets linked to criminal activity or sanctions violations. These freezes are often publicly visible on-chain and are usually mirrored in compliance threat feeds.
-
Investigative Value – When an issuer blacklists an address, it provides an external validation signal that illicit activity has been confirmed at a compliance or regulatory level. Investigators can pivot from these frozen wallets to trace associated laundering networks, related addresses, and cross-chain transfers.
Practical Tip:
-
Monitor issuer blacklists in real time new freezes often correlate with ongoing investigations or emerging threats.
-
Treat them as high-confidence enrichment points, but remember that issuer freezes only confirm illicit use of the frozen wallet, not every address in its wider cluster.
-
Combine issuer data with feeds and on-chain tracing to expose broader laundering ecosystems.
OSINT is one of the most powerful allies in blockchain forensics, but it requires careful handling. The blockchain itself gives you facts immutable records of transactions. OSINT provides the context the human, technical, and behavioral signals that transform those facts into actionable intelligence. When combined, they allow investigators to move beyond tracing coins to understanding the actors, networks, and motives behind illicit activity.
However, OSINT is rarely conclusive on its own. A single leaked credential, a Telegram post, or a blacklist tag should not define attribution without corroboration. The strength of an investigation lies in triangulation: cross-validating multiple OSINT sources against blockchain evidence until the connections are undeniable.
- Challenges in Using OSINT for Blockchain Forensics
While OSINT is an invaluable tool in blockchain investigations, it comes with significant challenges that investigators must recognize and manage. Without careful handling, these limitations can lead to weak conclusions, misattribution, or even compromised investigations.
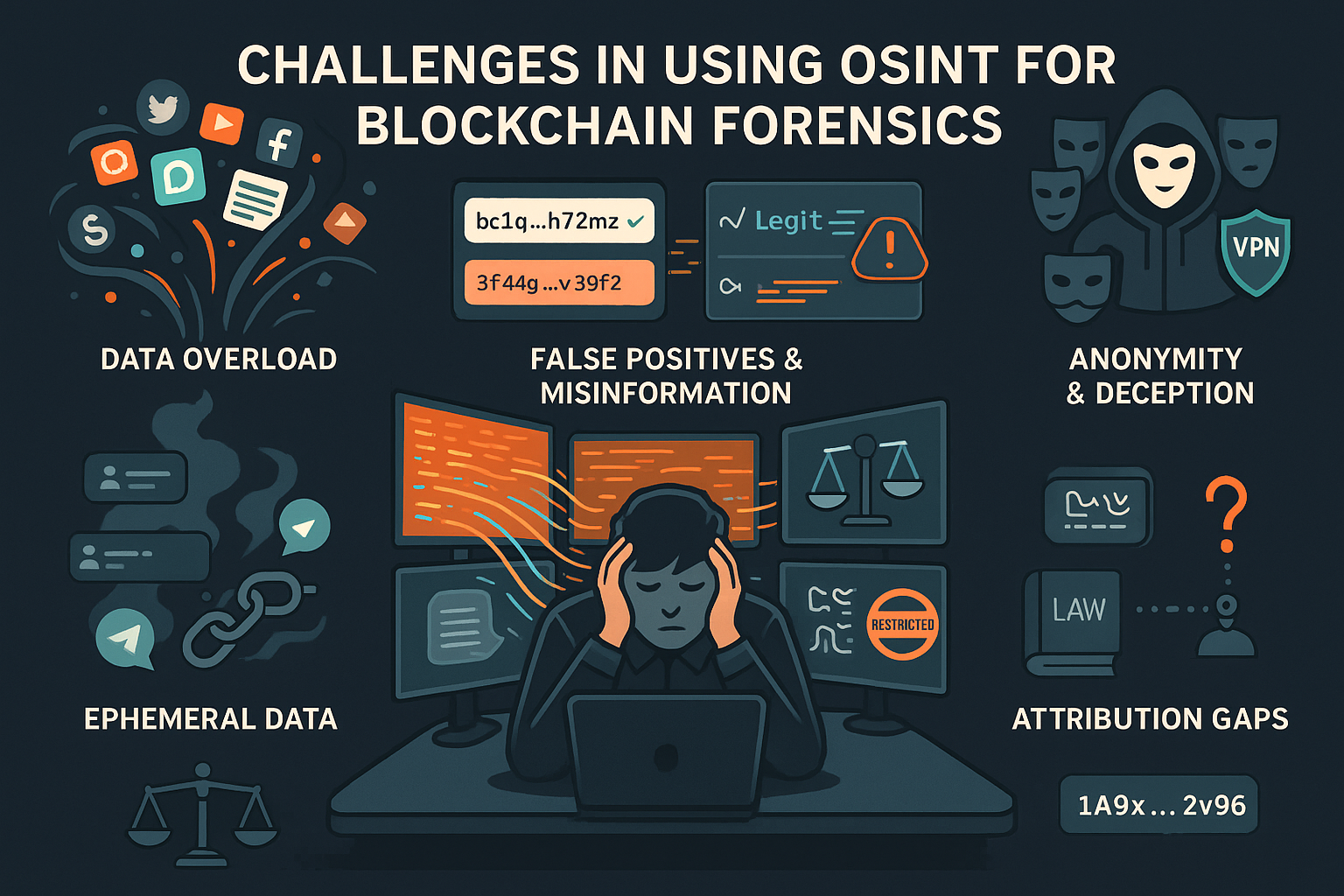
-
Data Overload – The sheer volume of information available is both a strength and a weakness. Social media chatter, domain records, leaked datasets, and threat feeds generate an enormous flow of signals. Many of these are irrelevant, outdated, or misleading. Investigators must spend considerable effort filtering noise from useful intelligence, often requiring experience, structured workflows, and automated tools to stay efficient.
-
False Positives & Misinformation – Public blacklists, community-driven reporting platforms, and forum posts frequently contain inaccuracies. Some wallets may be incorrectly tagged as malicious, while others may have been used for illicit activity years ago but are now dormant. Treating such entries as conclusive evidence risks serious misattribution. OSINT should guide inquiry, not dictate final attribution without corroborating on-chain data.
-
Anonymity & Deception – Threat actors are skilled at concealing their identities. They use VPNs, burner devices, fake personas, and compartmentalized accounts to mislead investigators. In some cases, they deliberately plant false OSINT trails such as spoofed domains or fake social media handles—to confuse attribution. Recognizing deception requires experience, critical analysis, and validation across multiple independent sources.
-
Ephemeral Data – Much of the open-source data investigators rely on is temporary. Tweets are deleted, Telegram groups vanish, domains expire, and GitHub repositories are taken down. If evidence is not captured immediately through screenshots, archives, or monitoring tools, it may be lost forever, weakening future attribution efforts.
-
Legal & Ethical Boundaries – Not all OSINT sources are equally safe or lawful to use. Handling breached data, darknet forums, or credential dumps requires strict OPSEC and a clear understanding of legal constraints. Investigators must balance the value of intelligence against the risks of violating privacy, terms of service, or compliance frameworks. Staying within ethical boundaries ensures credibility and protects the integrity of an investigation.
-
Attribution Gaps – Perhaps the most fundamental limitation is that OSINT alone cannot provide proof of wallet ownership. At best, it builds circumstantial connections linking a Twitter account, GitHub repo, or domain to a wallet address. Without validation through blockchain analysis, OSINT can only suggest, not confirm, control over funds. Strong attribution demands a combination of on-chain forensics + OSINT + corroborating signals.
- Best Practices for Investigators
To overcome the challenges of using OSINT in blockchain forensics, investigators need to adopt disciplined methods, strong verification habits, and secure operational practices. The goal is not just to collect intelligence but to transform it into reliable, defensible, and actionable evidence.

-
Correlate with On-Chain Evidence – OSINT signals are most powerful when paired with blockchain data. Always confirm whether a wallet address, domain, or username that appears in open sources has measurable links to the funds or activities under investigation.
-
Archive Aggressively – Because open-source data is ephemeral, capture everything: screenshots of posts, Telegram messages, domain lookups, GitHub commits, and site snapshots. Organize your evidence into timestamped archives for future reference or legal use.
-
Cross-Verify Across Sources – A single clue rarely proves attribution. Strong cases are built by triangulating multiple independent signals: e.g., a wallet found on a phishing site, mentioned in a Telegram group, and later frozen by Tether. The more overlaps, the stronger the confidence.
-
Stay Aware of False Positives – Treat blacklist entries and crowdsourced reports as leads, not conclusions. Validate all tags through independent analysis before citing them in reports.
-
Maintain OPSEC – When working with darknet forums, leaked data, or threat actor communities, protect yourself with isolated work environments, VPNs, and anonymization tools. Compromised OPSEC can endanger both the investigator and the investigation.
-
Leverage Monitoring Tools – Automate where possible. Tools like urlscan.io, Site Sentry, Telegram alert bots, and blacklist monitors can notify you when domains change, new phishing kits appear, or wallets are added to sanction lists. Early awareness is often critical.
-
Think Like an Adversary – Many scams succeed because actors take shortcuts. They reuse usernames, recycle code, or operate on predictable schedules. Investigators who approach analysis with an adversarial mindset often spot these mistakes first.
-
Collaborate with Communities – No investigator can cover the entire threat landscape alone. Networks like SEAL-ISAC, Chainabuse, and independent investigator groups provide shared intelligence and peer validation. Collaboration strengthens individual investigations.
-
Document Methodology – A solid investigation is not just about findings, but also about showing how those findings were reached. Clear documentation of sources, pivots, and validation steps ensures credibility when presenting results to exchanges, regulators, or the wider community.
OSINT is a powerful complement to blockchain forensics, providing the context needed to move from tracing transactions to attributing actors. While it comes with challenges such as false positives, deception, and legal boundaries disciplined practices like cross-validation, archiving, OPSEC, and collaboration help ensure accuracy. Used responsibly, OSINT transforms raw on-chain data into actionable intelligence, making investigations more effective and credible.
Conclusion
Attribution and OSINT are the twin pillars of blockchain forensics. On-chain analysis shows where funds move, but attribution reveals who controls the wallets, and OSINT adds the external context that turns pseudonymous addresses into meaningful intelligence. Together, they allow investigators to connect scattered transactions, reused infrastructure, and human behavior into cohesive cases that expose the actors behind hacks, scams, and laundering operations.
This article has walked through the practical techniques of attribution from transaction clustering and infrastructure reuse to cross-chain analysis and behavioral fingerprinting and shown how OSINT sources and tools strengthen those findings. Used in combination, these methods transform raw blockchain data into actionable insights that support enforcement, protect users, and hold bad actors accountable.
For new investigators, the most important lesson is this: you cannot learn these skills in a single day. Blockchain forensics requires patience, discipline, and practice. Every case is different, and every investigation teaches something new. Mistakes, dead ends, and false positives are part of the process but with persistence, anyone can grow into a capable investigator.
To future investigators: document your work, validate across sources, share with trusted communities, and never stop refining your methods. This article is just one piece a starting point to show the path of how investigations work. The rest comes from experience, practice, and the willingness to learn. With time, discipline, and collaboration, you can become one of the successful investigators pushing this field forward.
“ In blockchain forensics, the tools will guide you - but only persistence, practice, and curiosity will turn you into an investigator. ”
Supported with a grant under the ETH Rangers Program by

Disclaimer : “ This article is intended for educational and informational purposes only. It does not constitute financial, legal, or cybersecurity advice. While every effort has been made to ensure accuracy, the crypto threat landscape evolves rapidly, and the information presented may not reflect the most current developments. Readers should conduct independent research and consult with qualified professionals before making decisions based on this content.
References to specific companies, platforms, or individuals are based on publicly available information and do not imply wrongdoing unless independently confirmed. The goal of this article is to raise awareness and encourage best practices for user safety and ecosystem security.”