1. Introduction
2. Advanced Techniques in Blockchain Forensics
-
Time-Based Transaction Correlation
-
Demixing & De-Anonymizing Privacy Protocols
-
Bridge Hopping
-
Large-Scale Data Analysis & Querying
-
Graph Analysis & Clustering
-
Pattern Recognition in Laundering
3. Additional Resources for Investigators
-
Tools and Platforms
-
Courses & Certifications
-
Communities and Collaboration
-
Continuous Learning & Reading
4. Conclusion
Introduction
Blockchain forensics has never been more challenging. What once involved tracing simple transfers between wallets has evolved into a high-stakes pursuit against adversaries who use every tool at their disposal to stay hidden. Today’s attackers rely on privacy pools, bridge-hopping, rapid swaps, and endless layers of micro-transactions designed to overwhelm even the most experienced analysts.
For investigators, this means the old methods are no longer enough. To uncover the truth, we must master advanced techniques that go beyond surface-level tracing and reveal the hidden structures behind illicit flows. These methods allow us to spot timing patterns that betray human behavior, pierce through mixers and privacy protocols, follow stolen assets as they jump across chains, process millions of transactions at scale, and uncover laundering hubs and behavioral signatures that repeat across cases.
At first glance, these approaches can seem daunting. They involve technical analysis, statistical reasoning, and handling complex datasets. But like every skill in this field, they are learnable through consistent practice. Every investigator who has reached this level started the same way: confused by the complexity, but determined to push forward until the patterns began to make sense.
This article is written to serve as a roadmap for that journey. By the end, you will not only understand what these advanced methods are, but also how they can be applied in real investigations. And because no investigator works alone, I’ve included a set of additional resources from tools and data platforms to communities and learning paths that can help you continue building these skills beyond this guide.
The work is not easy but neither is the fight against those who exploit this ecosystem. With the right techniques, persistence, and mindset, we can meet their complexity with clarity and bring light to even the darkest corners of the blockchain.
Advanced Techniques in Blockchain Forensics
Investigating modern crypto crimes requires more than basic tracing. Threat actors rely on advanced methods to conceal their tracks, and investigators must respond with equally sophisticated approaches. In this section, we will explore six advanced techniques that form the foundation of complex investigations. Each technique addresses a different challenge from timing analysis and privacy pools to cross-chain movements, data scale, network clustering, and laundering patterns.
These are the advanced topics we are covering in this article. If new techniques emerge in the future, I will update this work with the latest methods so it remains a reliable resource for investigators.
Together, these methods represent the next level of blockchain forensics, equipping investigators with the skills to uncover hidden flows and connect seemingly unrelated activities.
- Time-Based Transaction Correlation
Every blockchain transaction carries a timestamp. While many analysts focus only on sender, receiver, and amount, the when of a transaction can be just as important as the where. Timing analysis adds a powerful layer to blockchain forensics, revealing hidden patterns, connecting activity across chains, and restoring visibility where direct links are missing.
Why Time Matters -
Illicit actors rarely move funds at random. Their activity often follows recognizable patterns that investigators can uncover by looking closely at timestamps:
-
Operational routines: Transfers made at fixed intervals may reveal automated laundering scripts or disciplined operational behavior.
-
Reaction to incidents: Funds are often shifted within minutes of a protocol hack being announced, showing attackers are actively monitoring public channels and responding in real time.
-
Geographic hints: Repeated activity during specific hours can suggest the time zone or working habits of the operators.
By aligning blockchain transactions with incident timelines such as the disclosure of a vulnerability, the freezing of exchange withdrawals, or the deployment of a fix investigators can determine whether attackers are reacting in real time or executing pre-programmed automation.
Behavioral Insights from Time -
Timestamps often reveal more about an attacker than the transfers themselves. Laundering operations that follow strict schedules point to automation. Bursts of activity immediately after exploits indicate urgency and manual control.
Even when flows appear random, careful timing analysis can uncover hidden coordination. Two wallets moving funds within seconds of each other may be controlled by the same operator. A sudden pause in movements might align with a service outage, an exchange downtime, or even internal disputes within the attacker group. These subtle timing cues act as behavioral fingerprints that help investigators connect wallets and strengthen attribution.
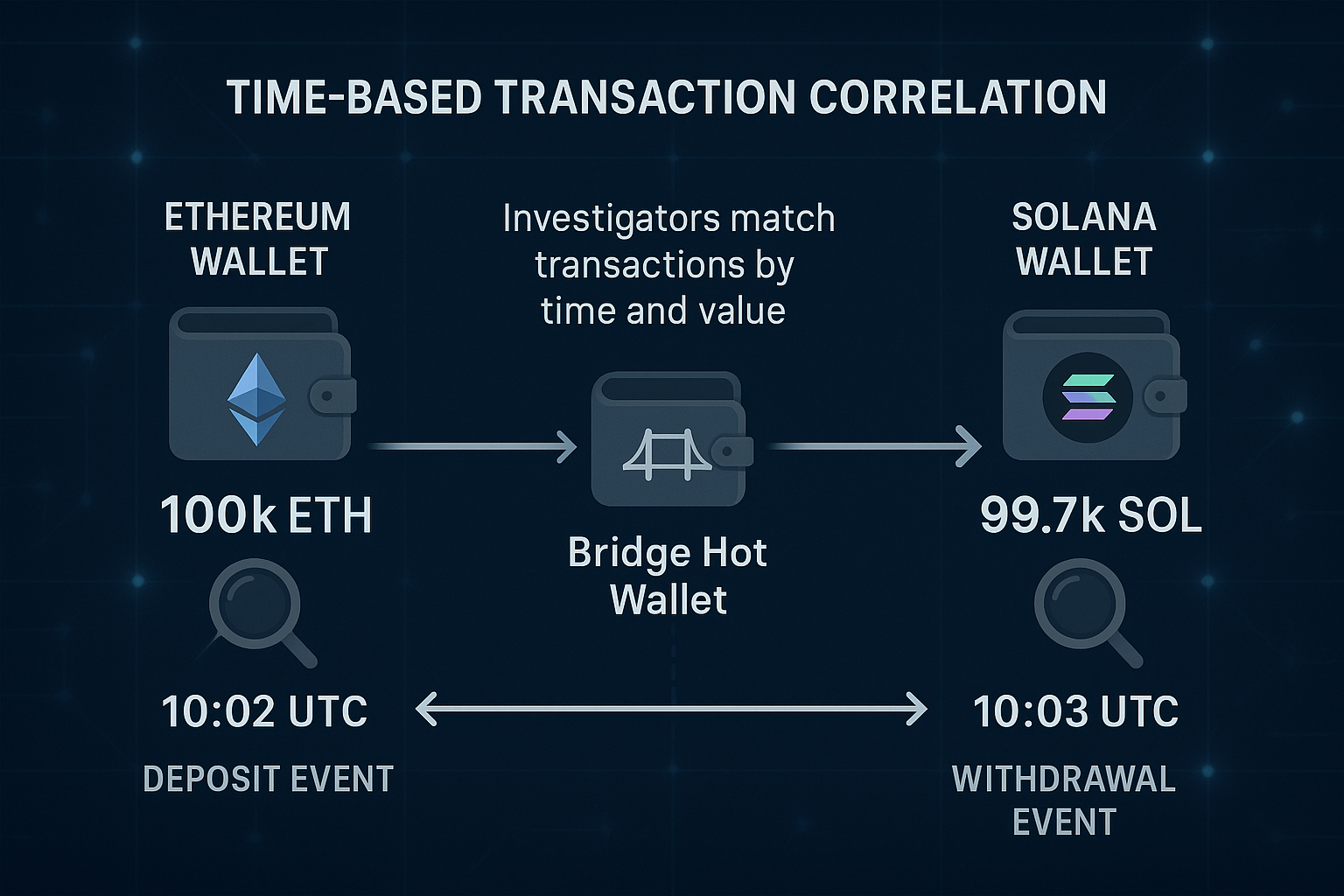
Cross-Chain Matching by Time Analysis Method -
Time-based analysis becomes even more valuable when tracing funds through platforms that do not provide transparent explorers. Services like eXch, RhinoFi, or ChangeNow allow users to swap or bridge assets instantly, but they operate as black boxes: deposits go in, withdrawals come out, and there is no public trail linking the two.
In such cases, investigators can reconstruct movements by treating time and value as forensic anchors:
-
Deposit event: Funds (e.g., $100k ETH) arrive in the platform’s hot wallet.
-
Withdrawal event: Within the same time window, an equivalent amount of another asset (e.g., SOL) leaves the hot wallet, slightly reduced by platform fees.
-
Correlation: By aligning the deposit and withdrawal on timestamp + value, investigators can reliably link the two events and trace funds across chains, even without a native explorer.
This method is especially effective with high-value transfers, since they stand out from regular user activity and are easier to match precisely. In practice, it turns timestamps and amounts into cross-chain fingerprints, restoring clarity in cases where attackers rely on opaque services to break investigative trails.
Value for Investigations -
Time-based transaction correlation transforms raw blockchain data into actionable intelligence. It allows investigators to:
-
Detect attacker routines and automation.
-
Identify context behind fund movements.
-
Reconstruct cross-chain transfers through opaque services.
Even when mixers, bridges, or instant exchanges obscure activity, time and value remain reliable anchors. For investigators, mastering this method adds a critical capability to the forensic toolkit one that can turn seemingly disconnected transactions into a coherent narrative of illicit activity.
Example: Time-Based Correlation in the Loopscale Exploit -
On April 26, 2025, attackers exploited the Loopscale protocol, stealing ~40,000 SOL worth $5.7 million. Almost immediately, they began laundering the funds across chains using ChangeNOW and Wormhole Bridge.
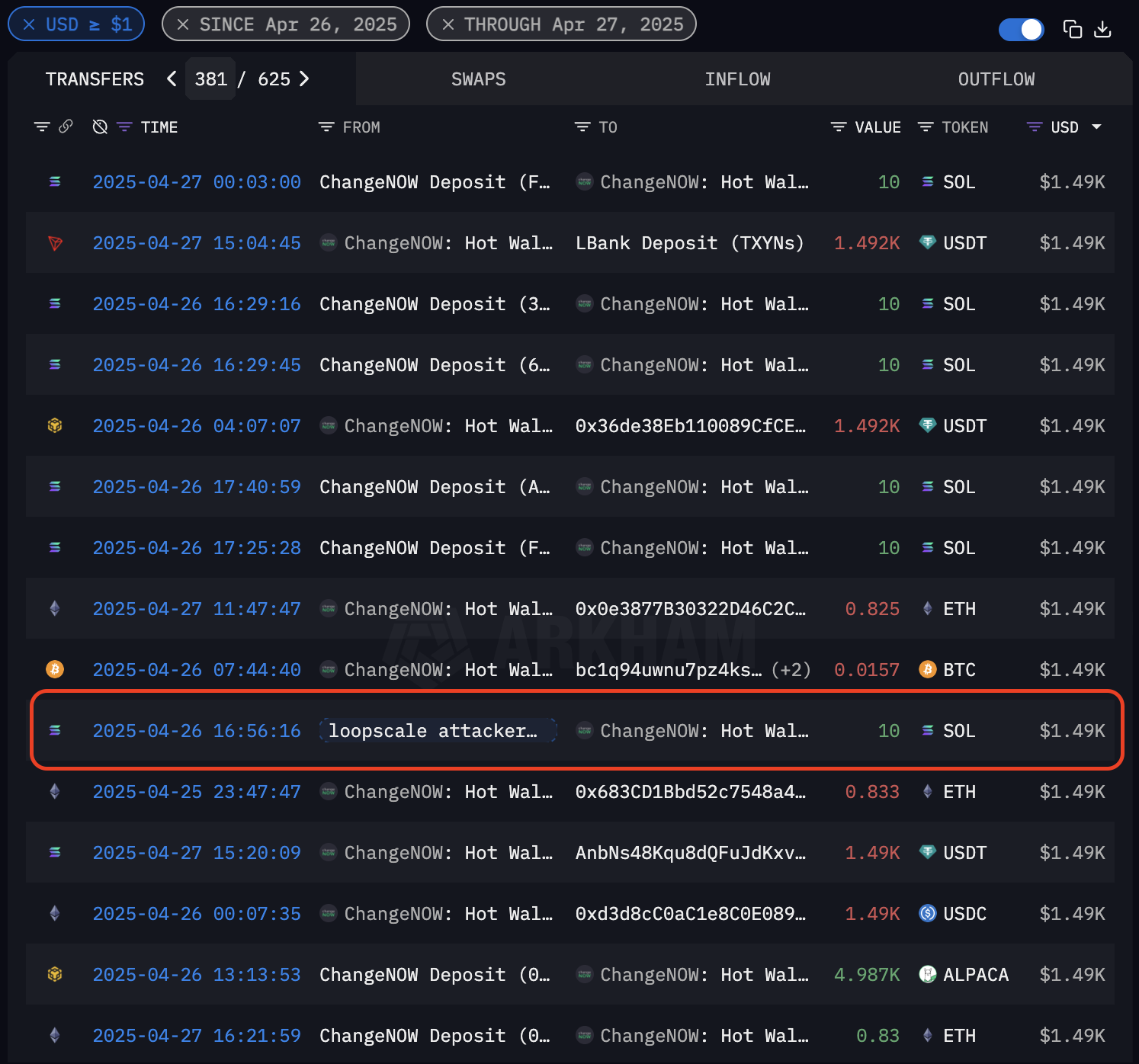
Step 1 — Deposit from Attacker Wallet to ChangeNOWAt 16:56:16 UTC, the attackers sent 10 SOL (~$1.49K) from the stolen Loopscale funds into the ChangeNOW deposit address CxcKoWP76vWP9W1sE8vFc89VAVox8LLLEAgCAPWx7E1e. This transfer is shown in below image, where the red box highlights the outgoing transaction, marking the exact time and amount correlation.
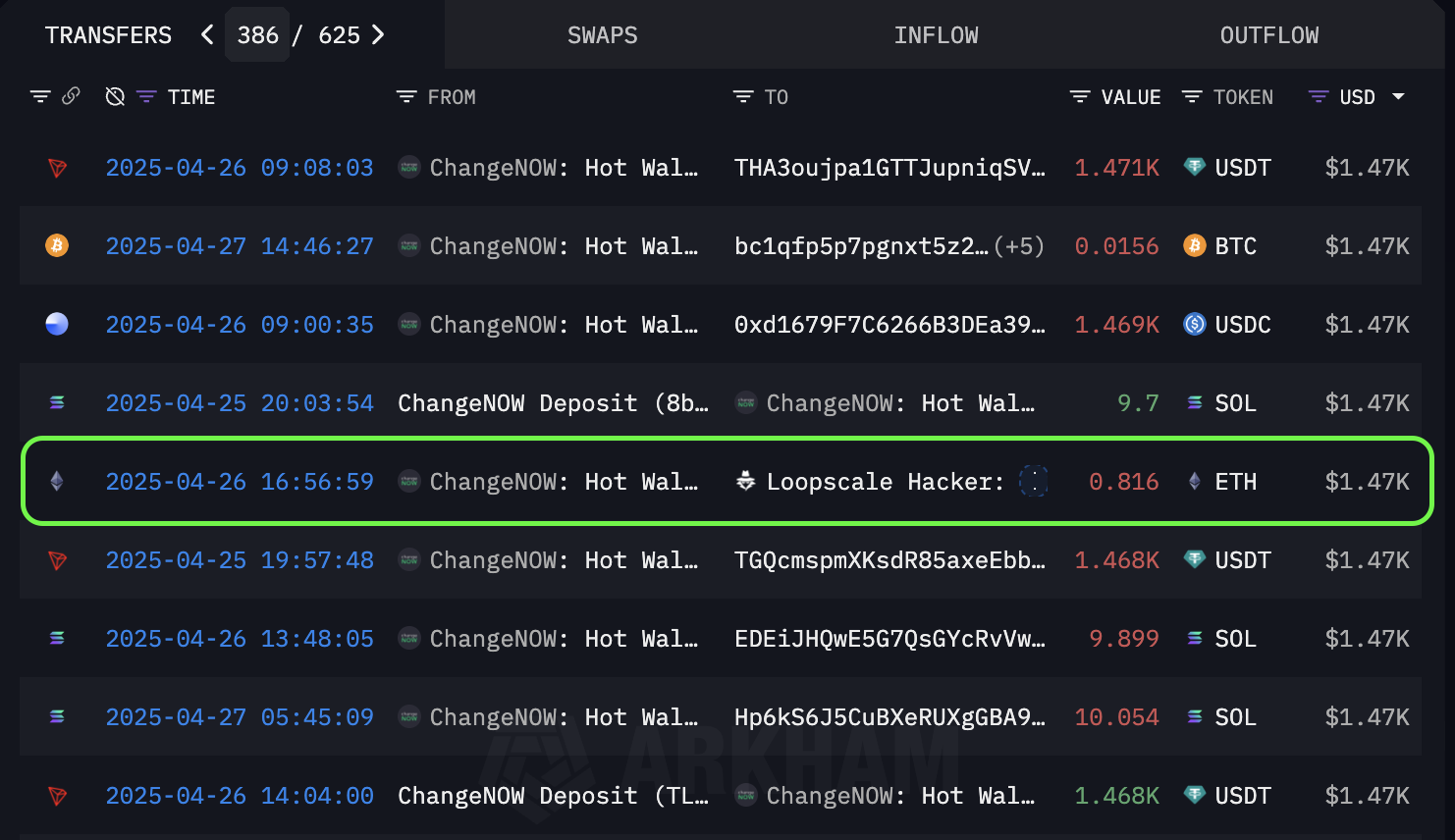
Step 2 — ETH Wallet ReceiptJust 43 seconds later, at 16:56:59 UTC, the attacker-controlled Ethereum wallet 0x05ff141699ae8D56B344550d893cFdAd4C60038c received 0.816 ETH (~$1.47K) from ChangeNOW. As shown in below image, the green-marked transaction confirms the ETH deposit, matching the Solana outflow in both timing and value.
Step 3 — Scaling Up Laundering With the Ethereum wallet now active, the attackers began bridging larger portions of the stolen SOL via Wormhole Bridge. The Wormhole explorer confirmed that these bridged funds landed in the same Ethereum wallet, proving it was the central laundering hub.
Why This Matters
This case demonstrates the power of time-based correlation:
-
Direct source: The 10 SOL originated directly from the Loopscale exploit funds.
-
Tight timing: Only 43 seconds separated the Solana deposit and the Ethereum receipt.
-
Visual confirmation: The linked images clearly show the red-boxed Solana outflow and the green-marked Ethereum inflow, helping investigators connect the dots.
-
Destination match: The same ETH wallet later received larger bridged amounts via Wormhole.
Even though the attackers used an instant exchange and a cross-chain bridge, the minute-level timing and visual confirmation exposed their laundering path across Solana and Ethereum.
White Hat Resolution
A few days later, Loopscale announced that the incident was resolved under a white-hat agreement. The attacker returned the majority of stolen funds in exchange for a negotiated bounty. By April 29, more than 19,000 SOL had been recovered in multiple tranches, reducing the overall loss to the protocol.
This shows how combining on-chain analysis with negotiated recovery efforts can lead to successful outcomes—even in major cross-chain exploits.
you can check out this thread for more information
- Demixing & De-Anonymizing Privacy Protocols
Privacy protocols like Tornado Cash, Railgun, and Wasabi were built to give users stronger financial privacy. In principle, they protect the right to transact without constant surveillance. But the same tools have also become critical laundering channels for stolen funds, exploited assets, and nation-state operations. This dual use creates one of the sharpest ethical debates in blockchain forensics: how to trace criminal abuse without undermining legitimate privacy.
For investigators, this means approaching demixing with caution. The goal is not to eliminate privacy but to identify and track illicit flows hidden within these systems. By analyzing timing, transaction sizes, withdrawal clustering, and behavioral patterns, investigators can sometimes pierce through the anonymity layer and reconnect funds to their broader laundering chains.
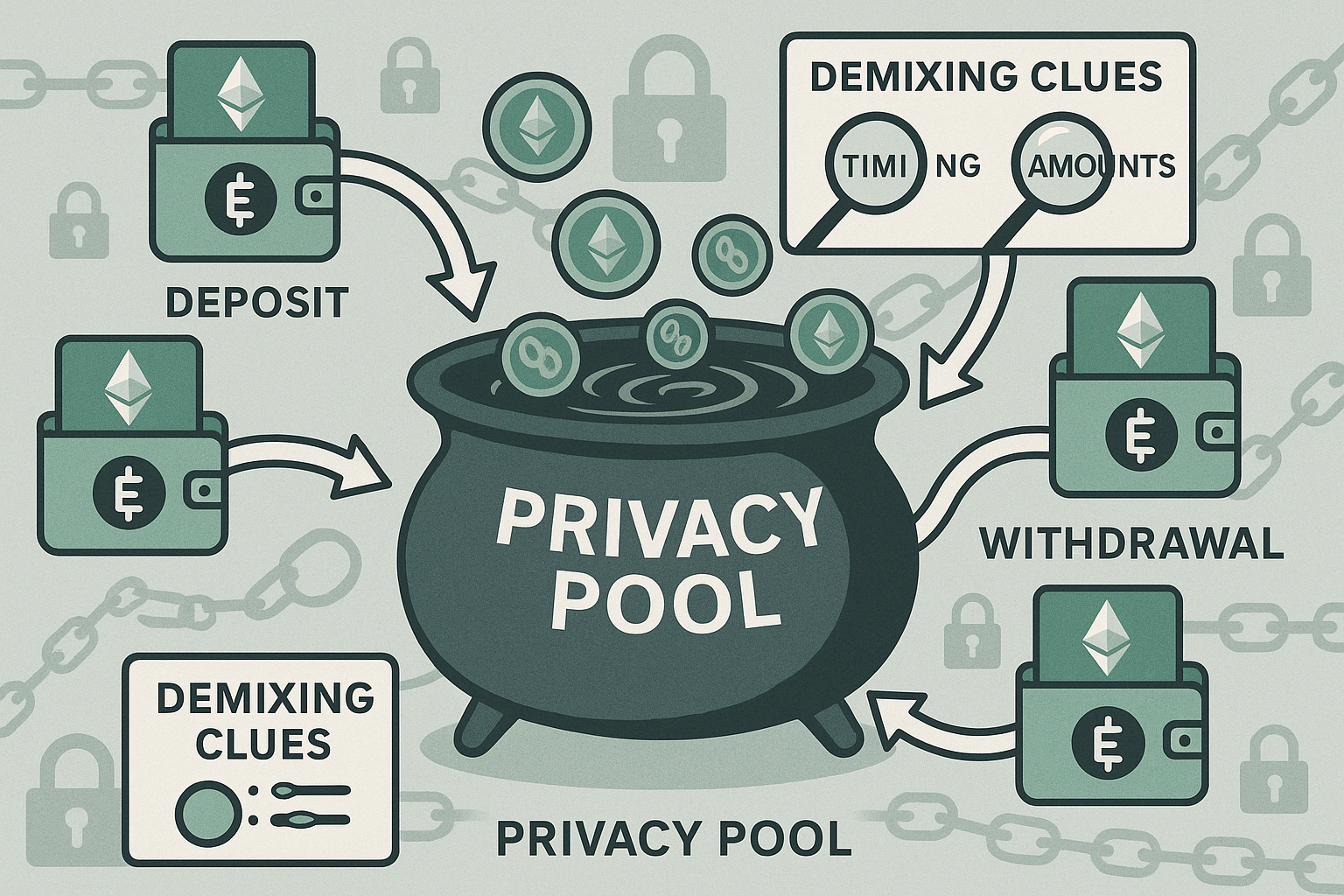
How Privacy Protocols Work -
Privacy protocols aim to break the visible trail of funds by severing the direct link between deposit and withdrawal. In practice, they use different mechanisms:
-
Mixer Pools (e.g., Tornado Cash): Users deposit crypto into a smart contract. Withdrawals are later made from the same pool to different addresses, with zero-knowledge proofs verifying ownership without revealing identity. (insert the external for more information)
-
Shielded Transactions (e.g., Railgun): Funds are moved into private pools where balances and transfers are hidden using zk-SNARKs, then re-emerge when unshielded.
-
CoinJoin Models (e.g., Wasabi): Multiple users combine their transactions into one large transaction, making it difficult to determine which input belongs to which output.
For everyday users, these tools offer privacy. For criminals, they offer cover. To investigate them, it’s essential to first understand how they operate only then can demixing analysis be applied effectively.
The Probabilistic Nature of Demixing -
Demixing is not about producing a perfect one-to-one match between deposits and withdrawals. Instead, it is a game of probability. Investigators use signals such as timing, transaction amounts, and behavioral patterns to estimate which deposits may correspond to which withdrawals.
The true accuracy emerges once funds leave the privacy pool and reach identifiable destinations, such as:
-
Centralized exchange (CEX) deposit addresses.
-
Cross-chain bridge contracts.
-
Known OTC brokers or laundering hubs.
By carefully tracking all destination addresses from privacy pools, investigators can narrow flows to their most likely outcomes. The more indicators that align similar amounts, overlapping time windows, repeated behaviors the stronger the probability that a mapping is correct.
This means demixing is less about achieving certainty inside the pool itself and more about linking exits to recognizable clusters downstream. Understanding this probabilistic nature is crucial to avoid overconfidence and to use demixing results responsibly in investigations.
Methods of Demixing Analysis -
Even though privacy protocols are designed to obscure flows, patterns often leak information that investigators can exploit. No single method guarantees certainty, but by combining multiple heuristics, analysts can narrow down likely mappings between deposits and withdrawals:
-
Timing Analysis: Matching deposits and withdrawals that occur within similar time windows. This is especially useful in Tornado Cash, where fixed pools limit value variation.
-
Value Fingerprinting: In mixers like Railgun, where users can deposit arbitrary amounts, distinctive values (e.g., 123.456 ETH) can act as fingerprints when they reappear on withdrawal. In Tornado Cash, deposits are limited to fixed denominations (0.1, 1, 10, 100 ETH), so value fingerprinting inside the pool is not possible. Instead, investigators look at how standardized withdrawals are consolidated later (e.g., multiple 10 ETH exits forming a unique 123.4 ETH exchange deposit).
-
Withdrawal Clustering: Grouping addresses that consistently withdraw in the same denominations or patterns, which often indicates they belong to the same operator or laundering script.
-
Gas Ratio Analysis: In Tornado Cash, attackers sometimes reuse the same gas ratio settings (gas limit and gas price) for both deposits and withdrawals, leaving a subtle but detectable fingerprint. While not conclusive on its own, when combined with timing and clustering, this method strengthens the probability of a link.
-
Linked Gas Wallets: Identifying the wallets that pay for withdrawal gas fees. Many attackers use repeat funding sources, and these fee wallets can sometimes be tied back to larger laundering clusters.
-
Statistical Heuristics: Using probability models to estimate which deposits are most likely linked to specific withdrawals. These methods often stack timing, value, gas patterns, and clustering together to produce confidence scores rather than hard matches.
Behavioral Insights from Privacy Use -
Attackers often assume that using privacy protocols makes them completely invisible. In reality, their behavior frequently leaks clues that can be just as revealing as technical signals.
-
Immediate Mixing After Hacks: Many attackers push stolen assets into Tornado Cash or Railgun within minutes of a theft. While this obscures the trail, it also shortens the analysis window and clearly signals that the funds are tied to the incident.
-
Repeated Withdrawal Patterns: Some groups consistently withdraw in fixed denominations (e.g., ten consecutive 10 ETH withdrawals), creating recognizable laundering “signatures.” Over time, these repeated behaviors can link multiple cases back to the same operators.
-
Chaining Privacy Tools: It is common to see attackers route funds through multiple privacy layers for example, Tornado → Railgun → CEX believing more layers equal more safety. Ironically, repeating the same sequence across cases creates a pattern that investigators can map.
-
Operational Timing: Even inside mixers, attackers often move funds at certain times of day that match their working hours or time zones, aligning with the insights discussed in time-based analysis.
By treating privacy use as a behavioral fingerprint, investigators can build attribution hypotheses that go beyond the technical limits of demixing. Each pattern on its own may be weak, but when combined, they paint a clearer picture of the laundering group’s style and habits.
Example: Privacy Pool Demixing of The WazirX Hack -
Privacy pools such as Tornado Cash are designed to break transaction linkages on-chain, making them a favored tool for laundering stolen funds. In the WazirX hack, attackers relied heavily on Tornado Cash as the first layer of obfuscation before layering additional privacy techniques across multiple ecosystems.
- Initial Obfuscation: Tornado Cash Deposits
Immediately after the exploit, the attackers transferred the entirety of the stolen funds into Tornado Cash. This move was not incremental but executed in a single wave, effectively severing the direct transaction trail from the compromised WazirX wallets.
The deposit chart of Tornado Cash activity during this window illustrates the concentration of inflows tied to the hack. For investigators, this deposit pattern serves as the anchor point: the last known on-chain location where the stolen funds can be directly attributed.
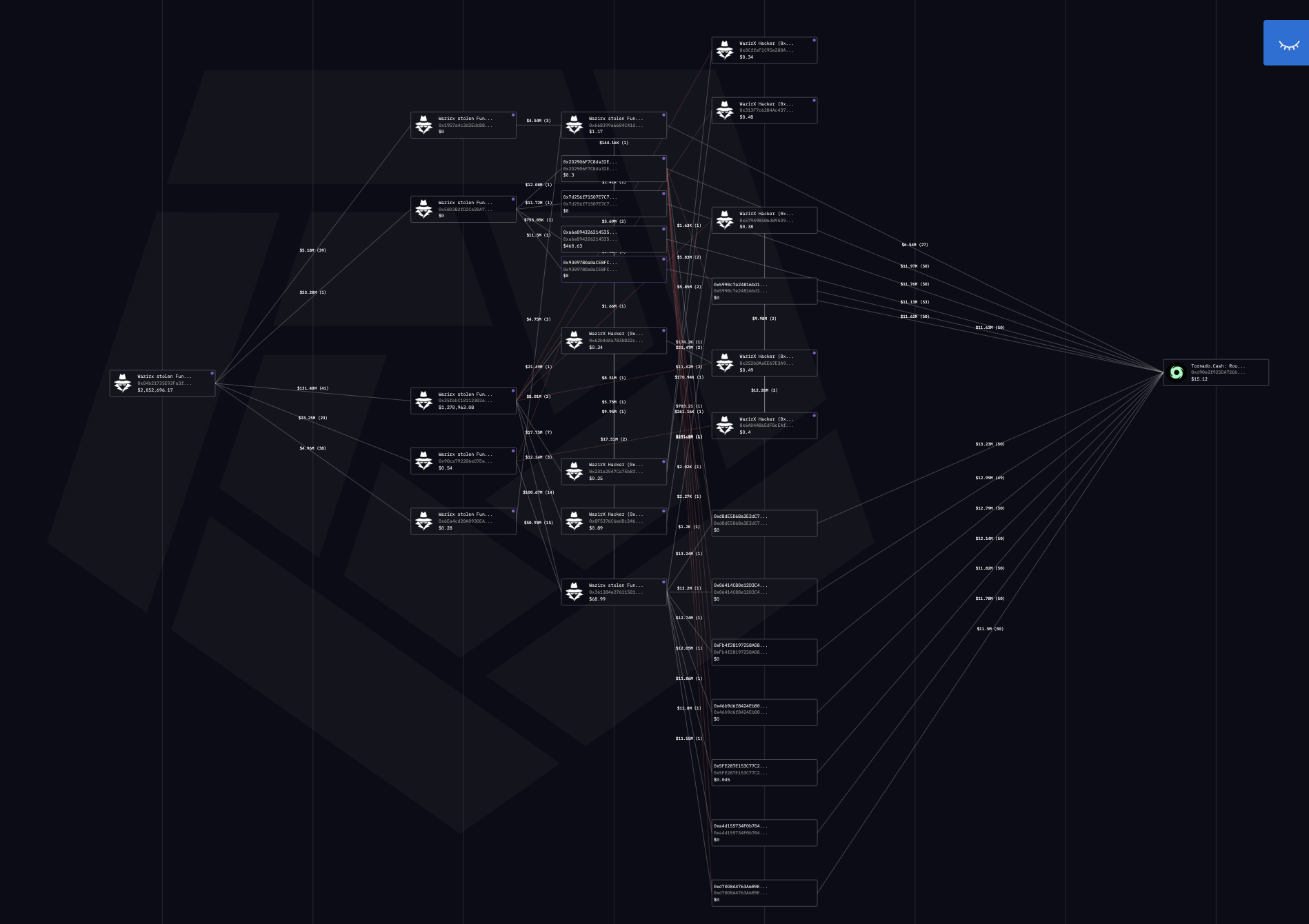
- Secondary Obfuscation: Cross-Asset Swaps
Shortly after their Tornado withdrawals, the attackers converted significant portions of ETH into Bitcoin through centralized and decentralized exchange platforms. This cross-asset laundering strategy created an additional hurdle for investigators, who now had to track flows across both Ethereum and Bitcoin ecosystems.
- Tertiary Obfuscation: CoinJoin Transactions
The laundered Bitcoin was subsequently pushed through CoinJoin transactions, a mixing method that combines inputs from multiple users into joint transactions. By fragmenting and recombining the BTC in thousands of micro-movements, the attackers created a highly complex transaction graph designed to frustrate linear tracing efforts.
- Final Off-Ramp: OTC Brokers
After layering through Tornado Cash, exchanges, and CoinJoin, the attackers funneled their Bitcoin into over-the-counter (OTC) brokers based in Southeast Asia. These brokers provided the cash-out mechanism, operating in less regulated environments where KYC and AML controls are weaker. This step marked the point of conversion from crypto to fiat, effectively monetizing the exploit.
Investigative Approach: Demixing in Practice
While such laundering chains are deliberately complex, investigators employ several methodologies to re-establish continuity:
-
Time-Based Correlation – Aligning Tornado deposits with withdrawals occurring within identifiable windows.
-
Denomination Analysis – Matching unique inflow and outflow amounts to reduce candidate sets of transactions.
-
Behavioral Patterning – Recognizing attacker habits, such as transaction timing, gas usage, or batching methods.
-
Cross-Chain Analysis – Extending investigation from Ethereum into Bitcoin, applying clustering and heuristic analysis to CoinJoin outputs.
-
Destination Monitoring – Flagging OTC addresses and brokers frequently linked to illicit cash-outs.
Lessons from the WazirX Case
The WazirX hack demonstrates how attackers layer multiple privacy mechanisms—Tornado Cash, asset swaps, CoinJoin, and OTC brokers—to complicate tracing. However, it also shows that each stage leaves forensic markers: timing gaps, denomination matches, withdrawal behaviors, or eventual clustering into known OTC channels.
The Tornado Cash deposit chart is not the end of the investigation but the starting point of demixing. From there, investigators must methodically reconstruct the flow through each layer, applying advanced techniques to peel back obfuscation.
Key takeaway: Privacy tools significantly increase complexity, but they rarely provide absolute anonymity. With systematic analysis, collaboration, and persistence, investigators can still map laundering chains even when attackers deploy multiple mixers across chains and assets.
- Bridge Hopping
Cross-chain bridges have become essential infrastructure in crypto, allowing assets to move seamlessly between ecosystems like Ethereum, Solana, BNB Chain, and Tron. But this same infrastructure has also become one of the most powerful laundering tools for attackers. By rapidly “hopping” funds across multiple chains, they can break investigative trails, exploit differences in address formats, and take advantage of weak or missing attribution on less-monitored networks.
For investigators, bridge hopping is one of the most difficult challenges in blockchain forensics. Unlike single-chain tracing, it requires understanding how wrapped assets, bridge contracts, and destination wallets interact across completely different systems. The complexity grows when attackers chain multiple hops together, turning a simple transfer into a maze of cross-chain movements.
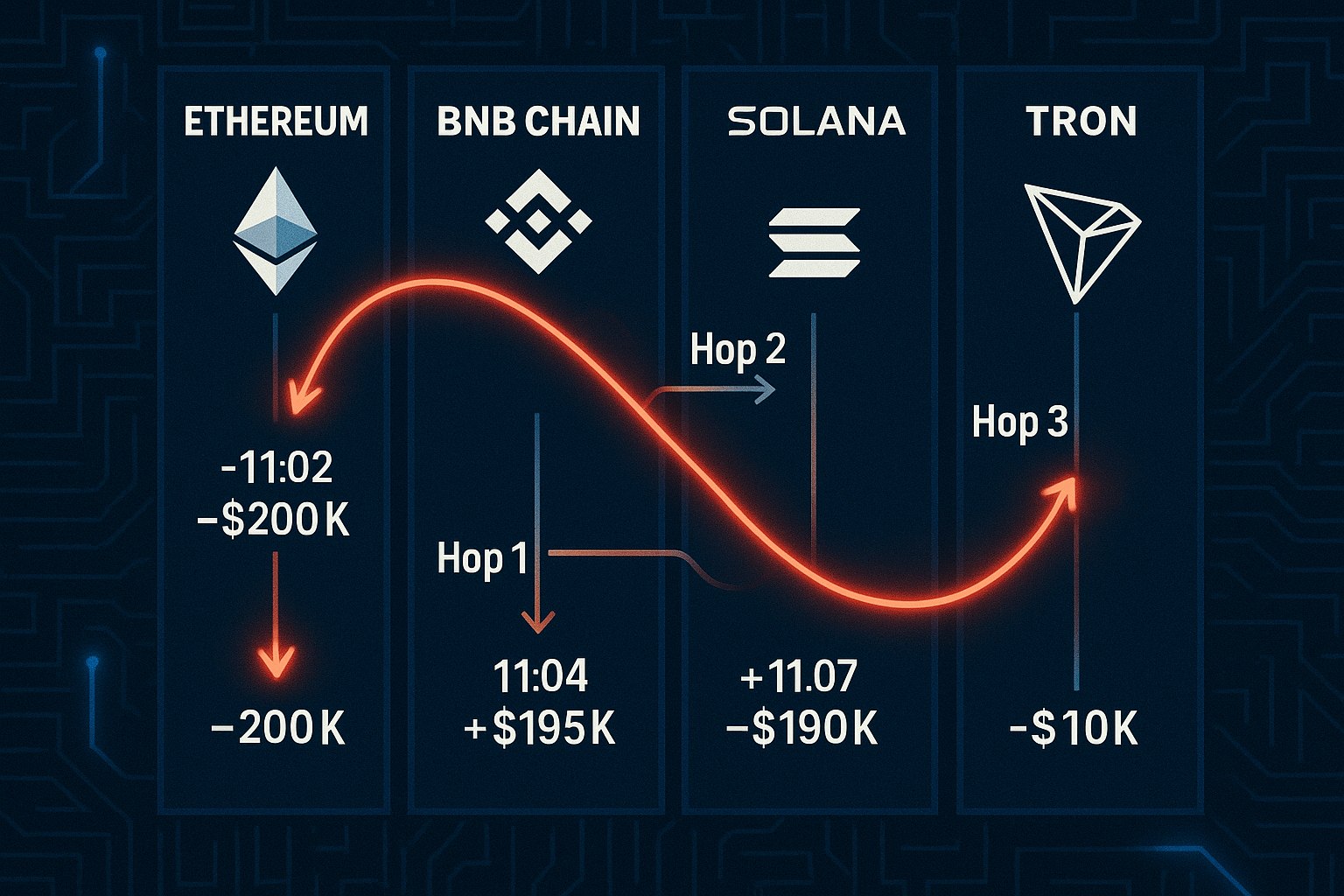
Why It Matters -
Bridge hopping is no longer an exception it has become the default laundering method for large-scale hacks. Attackers rely on it to:
-
Break continuity of on-chain visibility.
-
Convert assets into wrapped or synthetic versions that obscure their origins.
-
Exploit monitoring gaps on smaller or less-regulated chains.
-
Rapidly move funds before investigators or exchanges can react.
Without cross-chain attribution, investigators risk losing visibility at the very moment attackers attempt to cash out.
Methods of Bridge Hopping Analysis
Investigators can approach bridge hopping with a combination of techniques:
-
Tracking Bridge Contracts: Every cross-chain transfer passes through a bridge contract. By monitoring these, investigators can identify inbound and outbound addresses linked to the same transfer.
-
Wrapped Asset Mapping: When assets move across chains, they often reappear as wrapped tokens (e.g., ETH → wETH, renBTC → BTC on Ethereum, soETH on Solana). Mapping these correctly is critical to maintaining continuity.
-
Cross-Chain Matching by Time and Value: As explained earlier, deposits into a bridge on one chain often align closely in time and value with withdrawals on another, adjusted for fees. This remains one of the most reliable methods when explorers are unavailable.
-
Custom Data Pipelines via APIs: Many bridges (even some with limited transparency) expose APIs or event endpoints. Investigators can pull raw bridge data directly into their own systems, automate correlation, and even set up alerts for suspicious transfers. This becomes especially valuable when working with closed or semi-closed bridges where explorers don’t exist.
-
Program-Derived Addresses (PDAs): On chains like Solana, bridge systems create deterministic program addresses that can be mapped back to Ethereum origins, allowing attribution across ecosystems.
Automated Attribution Tools: Platforms like TRM Phoenix are specifically built to automate chain-hopping analysis, catching patterns that would otherwise be invisible to manual tracing.
Behavioral Insights from Bridge Use -
Even when attackers use bridges to obscure flows, their behavior often leaves recognizable patterns:
-
Rapid Multiple Hops: Many attackers believe safety comes from complexity. They push funds across three or four chains within minutes, creating the illusion of chaos. But repeating this tactic across multiple cases creates a laundering “signature” that investigators can learn to recognize.
-
Liquidity-Driven Decisions: Attackers usually select bridges with the deepest liquidity for the asset they are moving. For example, USDT launderers often prefer routes with high-stablecoin pools, which can help investigators predict likely exit points.
-
Chain Preferences: Different groups favor different ecosystems. Some consistently exit on Tron for USDT cash-outs, while others prefer Solana or BNB Chain. These preferences, when observed repeatedly, can become attribution signals tied to specific threat actors.
-
Partial Cash-outs: In some cases, attackers test the bridge with smaller amounts before moving larger sums. These trial transactions can serve as “breadcrumbs” linking the later, larger hops back to the same operators.
By treating bridge usage not just as a technical step but as a behavioral choice, investigators can add another layer of attribution to otherwise fragmented trails.
Value for Investigations -
Bridge hopping is one of the most challenging problems in blockchain forensics, but it is not a dead end. With the right approach, investigators can rebuild the flow of funds across chains and expose laundering trails that attackers assume are hidden.
By combining contract monitoring, time-value correlation, wrapped asset mapping, and custom data pipelines, investigators can maintain continuity of tracking even across opaque bridges. Behavioral patterns like rapid multi-hops, liquidity-driven choices, and repeated chain preferences add further context, helping link flows back to specific actors or groups.
For modern investigations, cross-chain attribution is no longer optional it is essential. Almost every major exploit today involves bridge hopping at some stage. Mastering this skill allows investigators to follow funds into less transparent ecosystems, identify cash-out points, and preserve visibility where criminals expect investigators to lose the trail.
Example: Bridge Hopping -
Bridge hopping is one of the most common laundering techniques attackers use to obscure stolen funds. Instead of moving assets in a straight line (hack → exchange), they deliberately pass funds through multiple cross-chain bridges in quick succession. The intent is to fragment the trail, make attribution harder, and exploit gaps in coverage between chains and platforms.
Case Study: Bybit Hack
A clear example of bridge hopping was seen in the Bybit hack. After draining a large volume of assets, the attackers funneled the majority of the stolen funds through cross-chain protocols such as Thorchain and eXch. By bouncing stolen tokens across different ecosystems, they attempted to sever investigative trails and confuse compliance teams monitoring a single network.
But bridge hopping leaves patterns:
-
Timing correlations – attackers often hop bridges rapidly within a tight time window.
-
Repetitive sequences – some criminals favor the same bridge order (e.g., ETH → BSC → Tron) across multiple hacks.
-
Denomination habits – attackers sometimes move the same chunk sizes across chains, leaving recognizable fingerprints.
Why This Matters for Investigators
By analyzing bridge hopping behavior, investigators can identify behavioral fingerprints of the attacker. These fingerprints allow:
-
Proactive monitoring – If the same wallet begins a similar bridge-hopping sequence in the future, investigators can flag it earlier.
-
Collaboration with bridge operators – Investigators can inform bridge teams to blocklist attacker-controlled wallets in real time.
-
Asset freezing – In certain cases, when investigators alert bridges and partner exchanges fast enough, parts of the stolen funds can be frozen mid-flow.
Key Takeaway: Bridge hopping may look chaotic, but it is not random. With enough data, investigators can recognize attacker tendencies across incidents. The Bybit hack showed how quickly funds can jump through Thorchain and eXch, but it also highlighted how cross-bridge analysis + operator collaboration can turn this laundering tactic into an opportunity for disruption.
- Large-Scale Data Analysis & Querying
Modern investigations don’t just involve a handful of wallets. Hacks, scams, and laundering operations often produce hundreds of thousands of transactions across multiple chains. Manually tracking these flows is impossible. To keep up, investigators must learn to work with large datasets using platforms and querying systems designed for scale.

Why It Matters -
Criminal actors rely on volume to hide their activity. Instead of moving funds in obvious chunks, they disperse assets across thousands of small transfers, cross-chain swaps, or automated scripts. This creates data noise that can overwhelm traditional block explorers or manual methods.
By leveraging large-scale querying, investigators can:
-
Identify laundering patterns hidden within huge volumes of transactions.
-
Detect anomalies in token flows, exchange deposits, or bridge usage.
-
Scale investigations to match the complexity of modern attacks.
Without these capabilities, critical signals risk being lost in the noise.
Methods of Large-Scale Analysis -
-
SQL Querying Platforms: Tools like Dune Analytics, Flipside Crypto, and Google BigQuery allow investigators to write queries that extract structured transaction data at scale. Instead of checking one wallet at a time, you can analyze entire pools of addresses or contracts in a single query.
-
Custom Dashboards: By building dashboards in platforms like Dune or Flipside, investigators can track flows visually, set alerts, and share results with others in real time.
-
Data Warehousing: For large investigations, raw blockchain data can be ingested into custom data warehouses, allowing advanced filtering, enrichment, and correlation with off-chain intelligence.
Automation & APIs: Many protocols and explorers provide APIs that can be used to automate repetitive data pulls. Investigators can build scripts to regularly extract data from bridge contracts, DEX pools, or CEX hot wallets.
Behavioral Insights from Scale -
Working with scale isn’t just about crunching numbers it also reveals behavior that isn’t visible in small samples. For example:
-
Peel Chains: Long transaction chains where attackers drip funds through thousands of small outputs.
-
Deposit Clustering: Multiple unrelated scams depositing into the same CEX wallet, revealing shared laundering hubs.
-
Timing Bursts: Large volumes of transactions hitting a bridge or mixer within short time windows, suggesting coordinated automation.
Value for Investigations -
Large-scale data analysis transforms investigations from reactive wallet tracing into proactive detection. Instead of chasing one address at a time, investigators can identify patterns, clusters, and anomalies across entire ecosystems.
This skill also makes investigators more independent: rather than relying solely on commercial tools, you can build and run your own analyses on open platforms. Forensic capability at scale ensures that no matter how much noise attackers generate, the real signals can still be uncovered.
Real-World Example: Bybit Hack – Tracking 30,000+ Transactions
A great demonstration of the power of large-scale data analysis comes from the Bybit hack, where stolen funds were laundered through Thorchain and eXch. In this case, over 30,000 transactions had to be tracked — an impossible task to complete manually.
Independent investigator Tayvano built a custom Dune dashboard to handle the scale. By writing SQL queries against blockchain datasets, the dashboard pulled every relevant transaction, organized them into structured tables, and visualized the flows. What would have taken months of manual work became an analysis that could be completed effectively and rapidly.
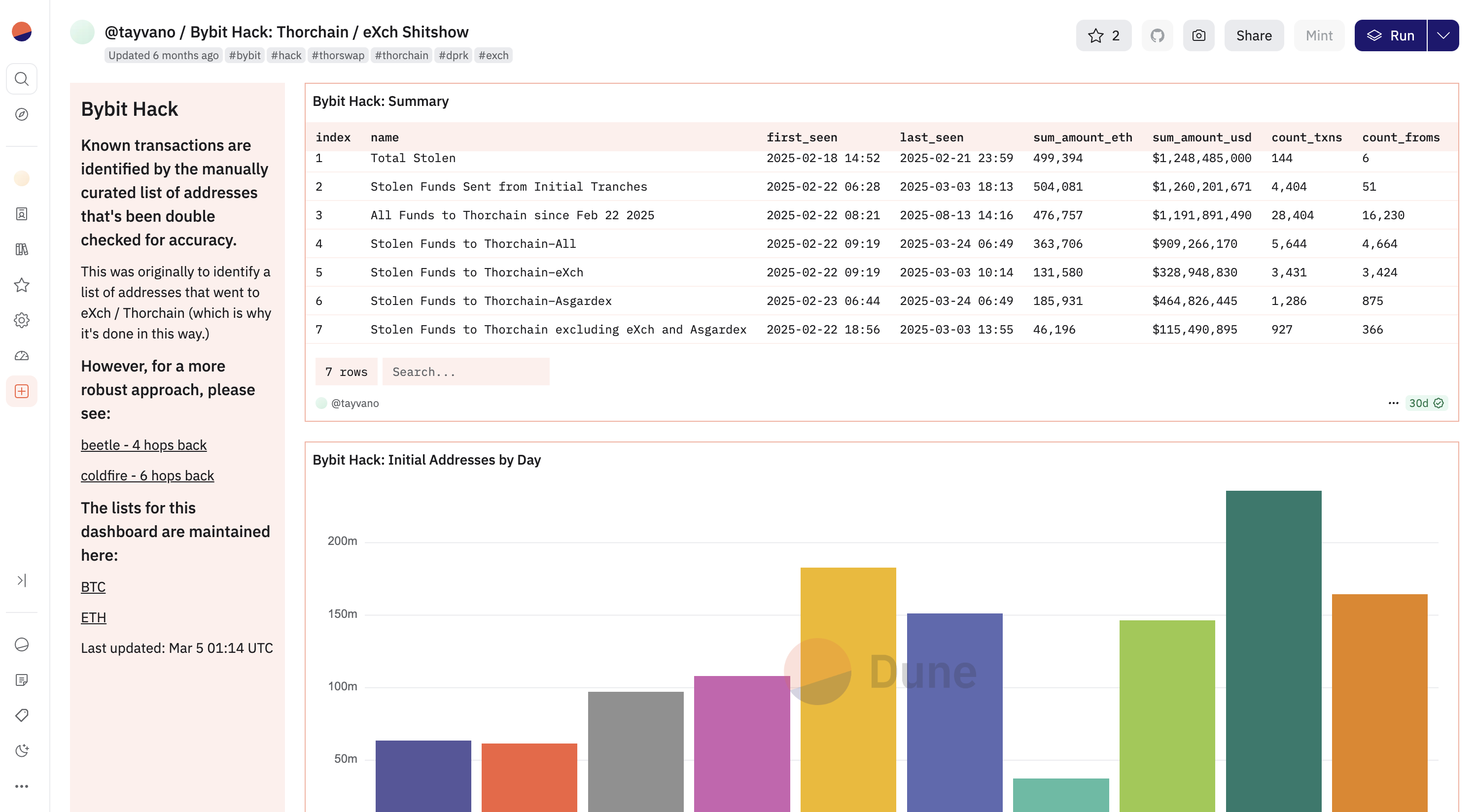
This example highlights why advanced data querying skills are critical in modern forensics:
-
They allow investigators to process massive transaction volumes without drowning in manual work.
-
They reveal laundering patterns (e.g., repeated Thorchain hops, clustered eXch withdrawals) that would otherwise be hidden.
-
They empower independent analysts to keep pace with large-scale hacks, even without access to expensive proprietary tools.
For investigators, this shows the practical value of mastering platforms like Dune, Flipside, or BigQuery. Advanced querying isn’t just a technical skill — it’s the difference between missing the big picture and exposing the full laundering chain.
- Graph Analysis & Clustering
At its core, the blockchain is a massive graph: wallets, contracts, and entities all connected by transactions. Investigators who learn to see the blockchain as a network rather than isolated transfers gain the ability to detect hidden structures, identify laundering hubs, and cluster related addresses into meaningful groups.
Graph analysis takes tracing beyond the “follow the money” approach. By modeling relationships at scale, investigators can uncover suspicious sub-networks, identify common funding sources, and detect behavioral overlaps that would remain invisible when looking at addresses one by one.
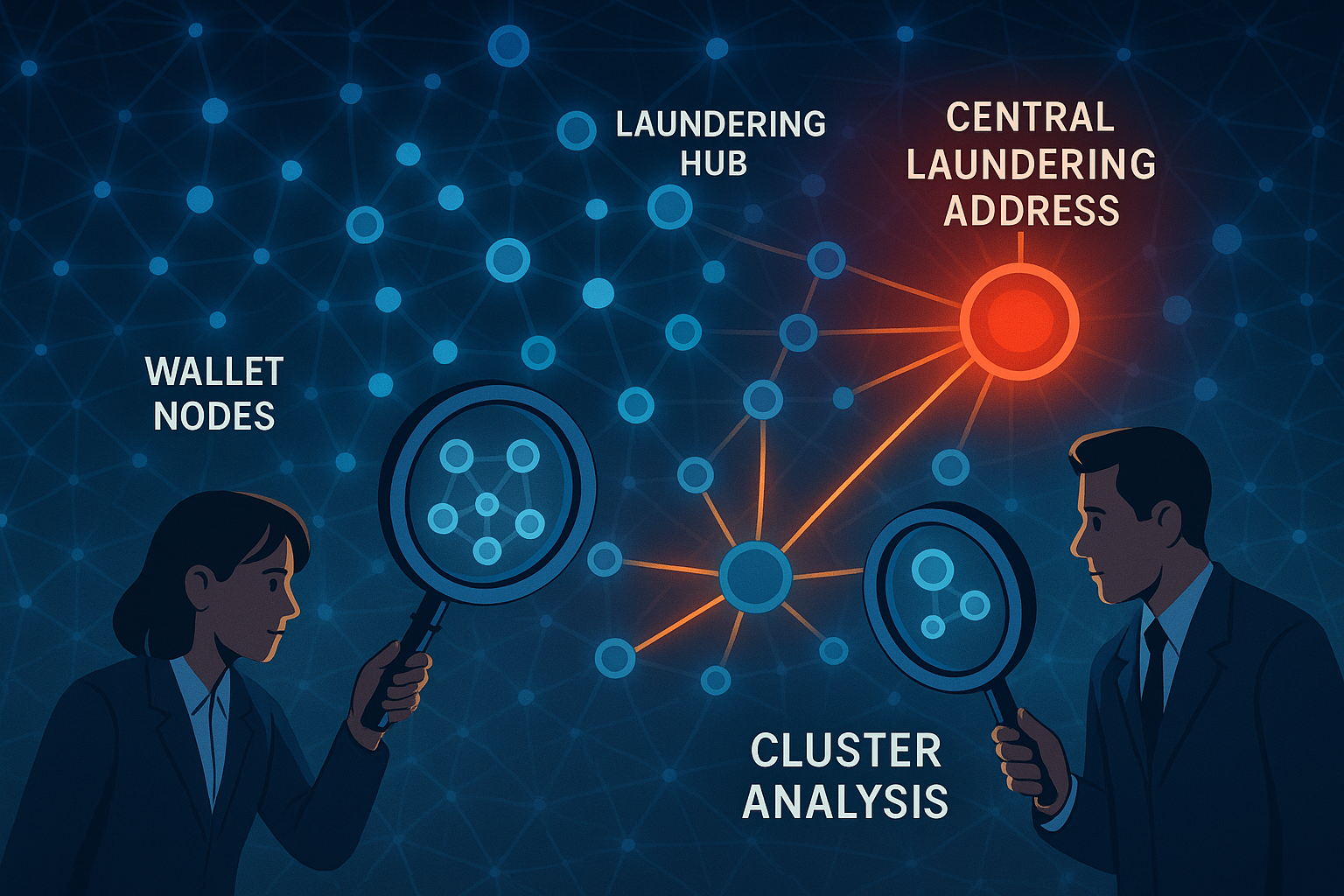
Why It Matters -
Attackers rarely operate through a single address. They control clusters of wallets deposit addresses, laundering intermediaries, cashout accounts that together form the infrastructure of their operations. Without graph analysis, investigators risk focusing only on one wallet and missing the broader network.
Clustering allows analysts to:
-
Link addresses controlled by the same entity.
-
Expose common collection points where stolen funds converge.
-
Detect laundering hubs that serve multiple scams or exploit groups.
-
Understand the relationships between attackers, intermediaries, and services.
This broader perspective often reveals that what looks like an isolated address is actually part of a larger ecosystem of crime.
Methods of Graph Analysis & Clustering -
-
Transaction Graphs: Mapping addresses as nodes and transactions as edges, then analyzing the flow of assets. Tools like Arkham, Breadcrumbs, Crystal, and MetaSleuth automate this process.
-
Heuristic Clustering: Grouping addresses likely controlled by the same actor based on shared patterns such as:
-
Spending from the same inputs.
-
Repeatedly paying gas from the same funding wallet.
-
Consolidating funds into common exit addresses.
-
-
Entity Resolution: Combining on-chain heuristics with off-chain intelligence (e.g., exchange deposit tags, leaked wallet clusters) to build bigger attribution maps.
-
Flow Analysis: Using graph algorithms (e.g., PageRank, connected components) to identify key nodes where multiple laundering paths intersect.
-
Visualization Tools: Investigators often rely on visual clustering tools (like Breadcrumbs or GraphSense) to simplify complex networks into interpretable structures.
Behavioral Insights from Graphs -
Graph analysis doesn’t just show transactions it shows how attackers think:
-
Star Networks: Many scams route funds from hundreds of victim wallets into a single central address before laundering, creating a star-like cluster.
-
Chain Splitters: Some actors deliberately fragment flows into dozens of micro-clusters, hoping to create noise. Ironically, the fragmentation itself can be a signature.
-
Service Reliance: Graphs often show attackers repeatedly using the same bridges, mixers, or CEX hot wallets across different operations, linking seemingly unrelated crimes.
-
Overlap Between Crimes: Two different fraud campaigns may appear unrelated until graph analysis reveals they share the same laundering hub or funding source.
Value for Investigations -
Graph analysis and clustering elevate investigations from address-level tracing to network-level understanding. They allow investigators to move from “this wallet stole funds” to “this entity controls hundreds of wallets, funnels assets through the same laundering hubs, and cashes out via specific exchanges.”
By mastering clustering, investigators can:
-
Attribute attacks to larger entities rather than isolated wallets.
-
Detect relationships between multiple crimes.
-
Build stronger cases that demonstrate organized activity, not just isolated transfers.
Forensic graphing transforms investigations into narratives, uncovering not just where funds went, but the structures and strategies behind criminal operations.
- Pattern Recognition in Laundering
While attackers try to appear random, laundering often follows repeated playbooks. Whether it’s consistent transaction sizes, reliance on the same services, or recurring fund flows, these patterns act like signatures. For investigators, learning to spot these repetitions is key to linking isolated cases to larger laundering networks.
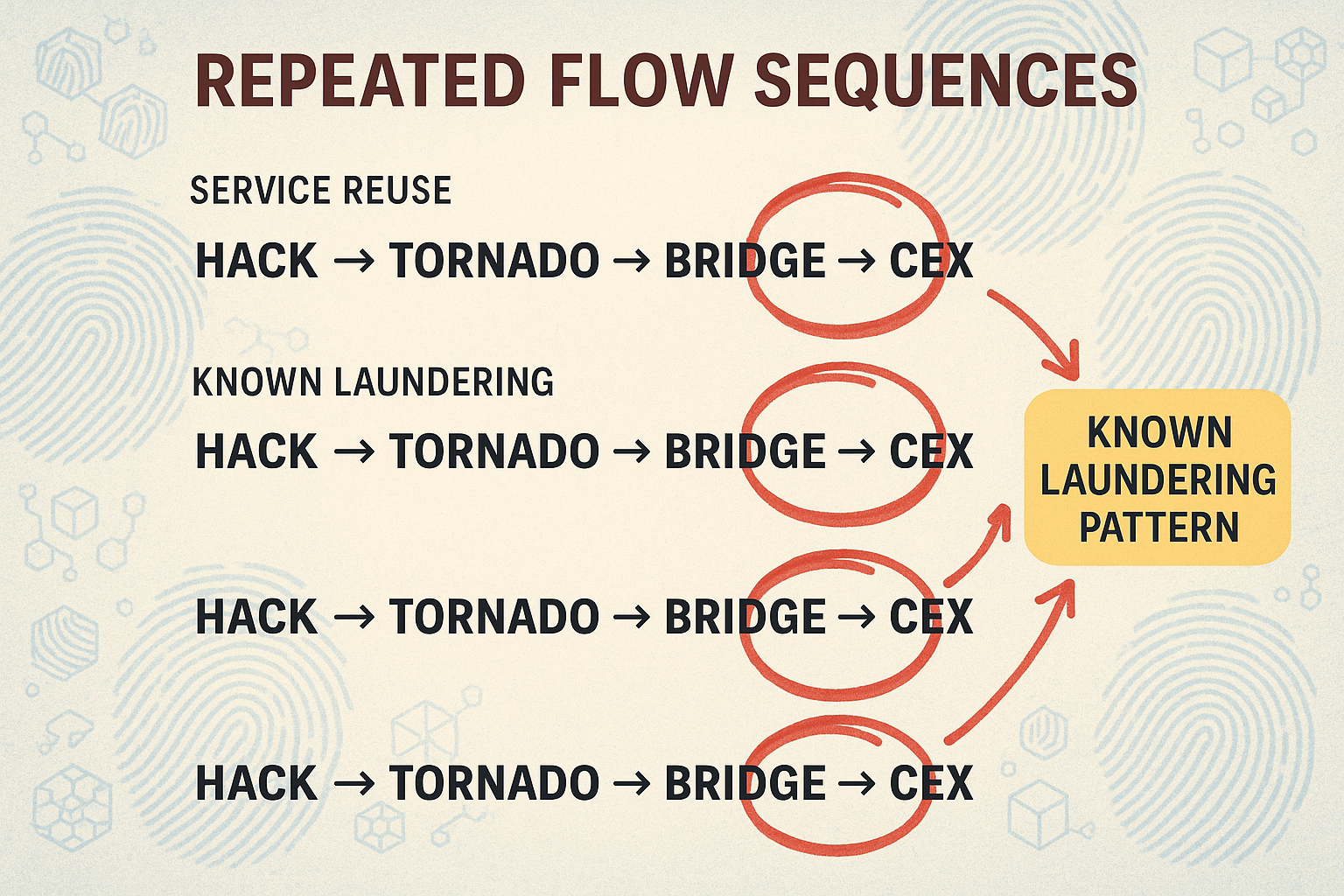
Why It Matters -
Most laundering is not unique it is recycled. Actors rely on strategies they know work, including:
-
Splitting transfers into fixed denominations.
-
Using the same bridges or mixers repeatedly.
-
Cycling assets through predictable sequences (e.g., ETH → USDT → Tron → CEX).
Recognizing these patterns allows investigators to:
-
Attribute new crimes more quickly.
-
Connect scams and hacks that use shared laundering infrastructure.
-
Shorten analysis time by focusing on known playbooks.
Methods of Pattern Recognition -
-
Transaction Structuring: Identifying repeating denominations (e.g., multiple 10 ETH withdrawals).
-
Service Reuse: Detecting reliance on the same bridges, mixers, or CEXs across different crimes.
-
Flow Sequences: Mapping repeated laundering routes such as Hack → Tornado → Bridge → CEX.
-
Behavioral Fingerprints: Attackers often test with small transfers before moving larger sums — a habit that becomes recognizable over time.
-
Cross-Case Analysis: Comparing laundering flows across multiple hacks to reveal shared operators.
-
Token Preferences: Certain groups consistently swap into the same assets (e.g., Tron USDT, DAI, or stablecoins with deep liquidity), creating identifiable preferences.
-
Timing Routines: Repeated laundering at specific hours or days (e.g., always moving funds during Asian market hours, or on weekends when compliance teams are slower).
-
Exchange Entry Patterns: Attackers often reuse the same deposit addresses at centralized exchanges — spotting these recurring entry points helps cluster multiple operations.
-
Chained Mixers/Bridges: Some groups repeatedly chain the same sequence of tools (e.g., Tornado → Railgun → Tron Bridge). Even if each step hides flows, the sequence itself becomes a recognizable pattern.
-
Dusting & Microtransactions: Repeated use of dust/micro amounts for probing wallets or testing flows before committing larger sums.
Behavioral Insights from Patterns -
Patterns expose more than just techniques they show how groups think. Some prefer speed over stealth, cashing out quickly. Others prioritize layering, hopping across multiple chains before consolidation. Repeatedly seeing the same behavior across cases is often enough to attribute activity to a specific group, even if wallets differ.
Value for Investigations -
Pattern recognition turns isolated transactions into threat intelligence. By building libraries of known laundering strategies, investigators can spot familiar fingerprints faster and strengthen attribution across cases.
In practice, this means moving from tracing single crimes to understanding the broader strategies of laundering groups an essential shift for anyone investigating at scale.
Real-World Example: Lazarus Group’s Recycled Laundering Patterns -
The North Korean Lazarus Group is one of the clearest cases where laundering patterns expose attribution. Despite targeting different protocols, Lazarus has consistently recycled the same laundering playbook across most of their hacks:
-
Initial Mixing: After exploits such as Ronin (2022), Harmony Horizon (2022), and Atomic Wallet (2023), stolen ETH was funneled through Tornado Cash in fixed denominations (often 100 ETH).
-
Layered Privacy Pools: In many cases, the group cycled funds through multiple rounds of Tornado Cash or chained different mixers together (e.g., Tornado → Railgun → Tornado). This layering added time delays but preserved the same general pattern.
-
Bridge Hopping: Funds were bridged into ecosystems like Tron or BNB Chain, converted into USDT or BUSD, and dispersed further.
-
Cashout Stage: The final step was routing funds through OTC brokers or Asian exchanges with weak controls, often the same ones used in earlier Lazarus operations.
Even with this extra layering, investigators found that the overall flow rarely changes: Tornado (repeated) → Bridge → Stablecoins → OTC/Exchange.
This repetition has become a strong fingerprint. When investigators see multiple rounds of Tornado usage followed by a Tron USDT bridge, it is treated as a high-confidence indicator of Lazarus involvement.
This example shows that pattern recognition allows investigators to:
-
Attribute hacks to the same group even when they add complexity with extra mixers.
-
Spot repeated cashout preferences across different incidents.
-
Anticipate future laundering flows once the pattern is known.
For investigators, Lazarus proves that even layered privacy pools and multi-hop bridges can’t fully hide patterns. Repetition always leaves behind recognizable fingerprints.
Advanced blockchain forensics requires more than just knowing how to read a transaction or use a tracing tool. It involves pattern recognition, contextual analysis, and the ability to adapt as adversaries evolve their methods. Techniques like time-based analysis, demixing of private pools, and cross-chain attribution are not one-time skills they demand constant practice, refinement, and real-world casework to master.
No investigator learns these overnight. It takes exposure to diverse cases, mistakes made along the way, and the discipline to compare notes with others in the field. As the ecosystem matures, so do the laundering strategies of bad actors making it essential that investigators continuously sharpen these advanced approaches.
Additional Resources for Investigators
No matter how skilled an investigator becomes, progress in blockchain forensics depends on access to the right resources. Tools change, laundering methods evolve, and investigative strategies that worked yesterday may be outdated tomorrow. This is why building and maintaining a strong library of resources is as important as mastering the techniques themselves.
Additional resources give investigators three crucial advantages:
-
Scalability – Automated platforms and dashboards allow analysts to track more cases in less time.
-
Collaboration – Investigator communities share intelligence, identify new laundering tactics, and pool knowledge across cases.
-
Professional Development – Courses and certifications provide structured learning paths, keeping skills sharp and credentials relevant.
In the following subsections, we’ll explore the key categories of resources that every investigator should know about tools and platforms, communities, training and courses, certifications, and continuous learning materials. Each of these adds another layer to an investigator’s toolkit, helping bridge the gap between theory and practice.
- Tools and Platforms
No single tool can solve every case. Each investigation demands a mix of raw data analysis, visualization, entity attribution, and sometimes even automated monitoring. That’s why building a toolkit tailored to different use cases is essential for investigators. Some tools are best for quick wallet lookups, others for large-scale fund flow visualization, and others for compliance-grade reporting.
To make this easier, I’ve compiled a curated sheet of tools organized by their primary use cases covering explorers, attribution platforms, visualization dashboards, monitoring systems, and more. This list is designed as a practical reference so investigators can quickly find the right tool for the right task.
📌 Note for beginners: Start with the free tools first like block explorers, open-source dashboards, or community alerts. They’ll give you the foundational skills you need before moving into commercial platforms, which are powerful but often costly.
- Courses & Certifications
While real-world investigations are the best teacher, formal training provides structure and credibility. Courses give investigators a guided learning path, while certifications validate those skills to employers, exchanges, and even law enforcement. Together, they ensure that investigators not only learn faster but are also recognized for their expertise.
Below are the main providers that dominate the space today:
TRM Academy
TRM offers a progressive training path from fundamentals to advanced specialization. All courses are online, self-paced, and include certificates of completion.
-
TRM Crypto Fundamentals Certification – Blockchain basics, wallets, mining, transactions, NFTs, and introduction to tracing.
-
TRM Certified Investigator – Core investigation workflows: tracing illicit funds, attribution, and identifying abuse vectors.
-
TRM Advanced Crypto Investigator – Deep dive into obfuscation, privacy tools, cross-chain laundering, and advanced casework.
-
TRM Crypto Compliance Specialist – For compliance teams: regulatory frameworks, monitoring, and risk assessment.
-
TRM Digital Forensics & Cryptocurrencies – Handling crypto evidence in forensic investigations.
-
TRM Crypto Seizure Specialist – Asset location, seizure, and recovery workflows for law enforcement.
Chainalysis Academy
Chainalysis provides certifications widely recognized across industry and government. These courses blend tool-based training with broader compliance and regulatory focus.
-
Cryptocurrency Fundamentals Certification (CCFC) – Intro to crypto, transactions, and AML basics.
-
Reactor Certification (CRC) – Hands-on tracing using Chainalysis Reactor.
-
KYT Certification (CKC) – Transaction monitoring and compliance workflows.
-
Asset Seizure Certification – Legal and practical aspects of seizing cryptocurrency.
-
Investigation Specialist Certification (CISC) – Advanced tracing with complex laundering methods.
-
Ethereum Investigations Certification (CEIC) – Focused on Ethereum, DeFi, and smart contracts.
-
Risk & Regulation Training (CRRT) – Regulatory frameworks and risk-based approaches.
Elliptic Learn
Elliptic focuses on compliance-driven training with certifications tied to its product suite.
-
Elliptic Learn – Certify – AML and cryptoasset fundamentals.
-
Product Certifications – Training for Elliptic Lens, Navigator, and other tools.
-
Specialist Investigator Certification – Advanced investigations using Elliptic’s Investigator platform.
Crystal Intelligence Training
Crystal’s courses blend theory with direct application in its Crystal Expert tool, covering both UTXO and EVM chains.
-
Crypto Fundamentals / Foundation Assessment – Intro to blockchain and crypto essentials.
-
UTXO-Based Blockchains Investigation Course – Bitcoin, Litecoin, and UTXO tracing methods.
-
EVM-Compatible Chains / Smart Contract Investigation – Ethereum, DeFi, smart contracts, and tracing.
-
Crypto Research & Investigation Specialist – Advanced training in visualization, OSINT, and case reporting.
-
Crypto Compliance Masterclass – AML frameworks, risk-based compliance, and regulation in crypto.
📌 Tip for learners: Choose one path and stick with it jumping between providers can be overwhelming. TRM and Chainalysis are the most recognized for investigations, while Elliptic and Crystal are excellent for compliance-heavy workflows. Beginners should start with fundamentals, earn their first certificate, and then build up to advanced courses as casework demands.
- Communities and Collaboration
Blockchain forensics is not a solo sport. While tools provide data, communities provide context, speed, and collective intelligence. Many of the biggest breakthroughs in crypto investigations come from collaboration—whether it’s independent researchers flagging stolen funds within minutes, or professional groups coordinating intelligence across incidents.
Why communities matter:
-
Real-time intelligence – Exploit alerts, suspicious wallet movements, and laundering patterns often surface in investigator communities long before they appear in official reports.
-
Cross-verification – Sharing findings with peers helps reduce mistakes and strengthen attribution.
-
Collective pressure – Public exposure of scams and hacks often forces exchanges, protocols, or law enforcement to take action.
Where to connect:
-
SEAL-ISAC – A structured threat-intelligence sharing network trusted by investigators and security professionals.
-
Independent Researchers – Figures like ZachXBT, Tayvano, Bax1337, FatManTerra, and others frequently share attribution work and wallet tracking in public threads.
-
Twitter/X, Telegram, and Discord – These channels host active investigator groups where new incidents, addresses, and laundering tactics are often shared in real time.
📌 Tip for beginners: Don’t just “lurk” in these communities—contribute. Even small findings, confirmations, or added context help the collective effort, and they’ll accelerate your learning curve as an investigator.
- Continuous Learning & Reading
In blockchain forensics, the ground is constantly shifting. New blockchains launch, DeFi protocols are exploited, laundering tactics evolve, and regulators adjust their frameworks. A method that worked six months ago may no longer apply today. For this reason, continuous learning is not optional—it is the foundation of becoming and remaining an effective investigator.
Why Continuous Learning Matters -
Unlike traditional finance, where fraud methods are relatively well understood, the crypto ecosystem is still experimental and fast-moving. Threat actors are often first movers, adopting new privacy pools, chain-hopping techniques, and social engineering scams before investigators even recognize them.
-
Adaptive Adversaries – Hackers constantly iterate. When Tornado Cash was sanctioned, attackers quickly shifted to other pools like Railgun, or stacked privacy layers with CoinJoin.
-
Cross-Chain Complexity – With the growth of Layer-2s, bridges, and interoperability protocols, stolen funds now move across multiple ecosystems within minutes. Without updated knowledge, investigators can easily lose the trail.
-
Tool Evolution – Forensic platforms themselves are evolving. TRM Phoenix, Arkham, and others roll out new features regularly. Staying sharp requir
Key Sources of Ongoing Knowledge
- Industry Reports & Blogs
TRM Labs, Chainalysis, Elliptic, Crystal Intelligence, CipherTrace and Zeroshadow publish regular threat intelligence reports and annual crime reviews. These outline how laundering patterns are evolving and highlight key case studies.
Example: Chainalysis’ annual Crypto Crime Report is widely read across law enforcement and compliance teams as a benchmark for illicit activity trends.
- Independent Investigators
Researchers like ZachXBT, Tayvano, Bax1337, WazzCrypto, and many others share investigations in real time. Their work often exposes laundering flows days or weeks before formal reports are published.
Independent blogs and X (Twitter) threads are goldmines for practical attribution methods and early warnings.
- Academic Research
Universities and research groups publish studies on transaction clustering, mixing heuristics, and cross-chain privacy challenges. While more theoretical, these works help shape the tools and methods investigators will use in the future.
Reading academic material sharpens technical understanding, especially around advanced privacy and cryptography topics.
- Case Study Reviews
Studying past hacks and laundering incidents is one of the most effective ways to build investigative intuition.
High-profile cases (e.g., Ronin, Harmony, Euler, Curve, FTX drainer campaigns) often reveal patterns attackers reuse in future exploits.
Replaying an old investigation step-by-step with today’s tools is a powerful training exercise.
Best Practices for Continuous Learning
-
Subscribe & Track – Sign up for newsletters, RSS feeds, and Telegram alert channels from forensic firms, independent researchers, and community groups.
-
Engage in Communities – Investigator collectives like SEAL-ISAC, CERT teams, and regional blockchain alliances provide real-time collaboration.
-
Hands-On Practice – Don’t just read—replicate. Load addresses from a published case into Arkham, Breadcrumbs, or MetaSleuth and practice rebuilding the fund flows.
-
Schedule Learning – Set aside time monthly or weekly to focus on one case study, one new tool, or one new academic paper. Treat it as professional development, not an afterthought.
-
Document & Share – Keep a private log of what you’ve learned (patterns, clusters, tagged wallets). Over time, this becomes your personal intelligence database.
The techniques outlined in the Advanced Blockchain Forensics section show what is possible with skill and methodology. But skill alone isn’t enough. Investigators need the right resources tools, communities, certifications, and continuous learning habits to apply those techniques at scale and keep pace with adversaries.
The landscape of crypto crime evolves daily: new exploits emerge, laundering routes shift, and novel obfuscation tactics appear. What remains constant is the need for investigators who are equipped, connected, and informed. Platforms provide the visibility, communities provide collaboration, certifications provide structure, and continuous learning ensures that no investigator falls behind.
In short, advanced techniques are the “how,” and additional resources are the “with what.” Together, they give you the capability to investigate effectively, respond quickly, and uncover truths that others might miss. For those committed to this field, investing in both skill and resources is what transforms curiosity into mastery.
Conclusion
The work presented here, covering both Advanced Blockchain Forensics Techniques and the Additional Resources that support them represents a step forward in documenting how investigators can respond to the growing complexity of crypto crime. From time-based correlation, clustering, and privacy pool demixing, to the use of bridge explorers, visualization platforms, attribution tools, and monitoring systems, this guide has outlined methods and resources that practitioners can use today to pursue truth on-chain.
But it is important to emphasize: this is not the final word. Blockchain forensics is an evolving field, where attackers continuously adapt and investigators must do the same. No single report, tool, or investigator holds all the answers. What matters most is the mindset of continuous learning, collaboration, and persistence.
This work is a small contribution from my side to that larger effort. I am not perfect, and I am still learning many things myself. Every case, every collaboration, and every failure adds another layer of understanding. My commitment is to continue sharing genuine learnings as they come whether through case studies, articles, or community discussions so that other investigators can benefit, improve, and contribute in turn.
None of this would have been possible without the support of the Ethereum Foundation, under the ETH Rangers Support Program. Their grant has provided the resources and time necessary to explore these techniques deeply and present them in a way that benefits the broader community. For that, I am sincerely grateful.
As we look ahead, the challenges in blockchain forensics will only grow more chains, more bridges, more privacy protocols, more creative laundering methods. But so will the capabilities of those who choose to investigate. If this guide helps even a handful of investigators sharpen their skills, uncover a laundering flow, or protect users from fraud, then it has served its purpose.
The fight against crypto crime is not a solo journey. It is a collective one. And this guide is just one more brick in a wall we are all building together.
Supported with a grant under the ETH Rangers Program by

Disclaimer : “ This article is intended for educational and informational purposes only. It does not constitute financial, legal, or cybersecurity advice. While every effort has been made to ensure accuracy, the crypto threat landscape evolves rapidly, and the information presented may not reflect the most current developments. Readers should conduct independent research and consult with qualified professionals before making decisions based on this content.
References to specific companies, platforms, or individuals are based on publicly available information and do not imply wrongdoing unless independently confirmed. The goal of this article is to raise awareness and encourage best practices for user safety and ecosystem security.”