The internet is now highly utilized globally for education, healthcare, business opportunities, etc. Phones are connecting to the internet, allowing global communication and TV has largely now shifted to being an app (Netflix for example) that one can access via their internet connection. There are five components to the web.
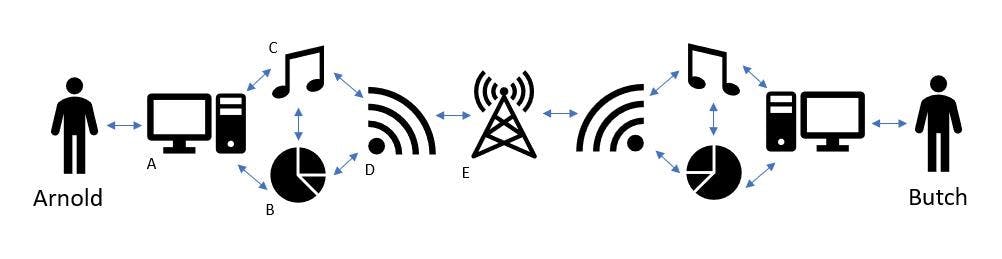
Components
Physical
Physical is the hardware that is needed for the internet; usually a laptop, TV and a phone. However, there is a hidden layer.
Data
Whenever a person interacts with the physical component, moves a mouse, touches a keyboard, speaks into a phone, turns on their TV data is generated. This data is structured and stored within the physical. There will be an estimated 175 zettabytes of data needed to be stored by 2025 (1). Google, Amazon, Microsoft, and Facebook currently collectively store at least 1.2 zettabytes in their physical components (data storage systems) (2). This data is analyzed by each of these companies adding an additional layer to the physical components (computing systems).
Applications
One way in which people on the internet interact with data is in the form of applications. Well known application examples are the search engine of Google or Facebook's social media app.
Internet
Once the data is generated, people want to communicate with other people about it. The sending of this data from person to person, is the foundation of the internet. There are different ways in which this data is structured to make it legible for the person on the other side, such as IP addresses.
Transport
Structuring is just one part of sending data, the other aspect is the actual infrastructure needed to do so. Fiber networks, cables able to send data to and from parts of the world at high speeds, span throughout our world. Satellite systems, such as Starlink, are also able to transport this data.
Issues with Web2
Physical
In North Korea the physical components that people are able to purchase easily are heavily modified so that North Korea can control what data their population has access to and easily access the data that the population creates (3). This control of the physical layer is able to be replicated in other parts of the world and likely has.
Lenovo, HP Inc and Dell have over 50% of the global PC market share (4). Microsoft has strategic alliances and partnerships with each of these companies, increasing the reach of Microsoft to at least 50% of PCs in terms of hardware. The operating systems installed on the physical layers of computers are around 90% of the time from Microsoft (5).
Data
If you have used the physical layer large tech companies of Google, Microsoft, Apple (phones and computers) or If you have interacted with applications like search engines (Google, Yahoo) or applications like Facebook it is likely that your data is stored in one of their data centers. Once the data is stored, these companies are able to monetize off your data. Potential revenue sources includes selling it to advertisers, governments, or other entities interested in using it. These companies themselves have made some of the most sophisticated artificial intelligence systems in the world (such as Google Translate). People can access these AI's however they have not been paid for the use of their data.
Applications
Google and Meta (Facebook) alone have influence on greater than 70% of internet traffic, the remaining 30% is shared by all other apps and sites (7). If you search- lawsuits Google or lawsuits Facebook you can see just how many lawsuits these companies are in. The lawsuits range from privacy infringements, to theft of intellectual property, to discrimination, to genocide, to damaging youth's health, etc. Again, these companies control 70% of the internet, that's around 70% of the world's data transmissions...
The expansion of Google Chrome (8).
The Expansion of Facebook (8).
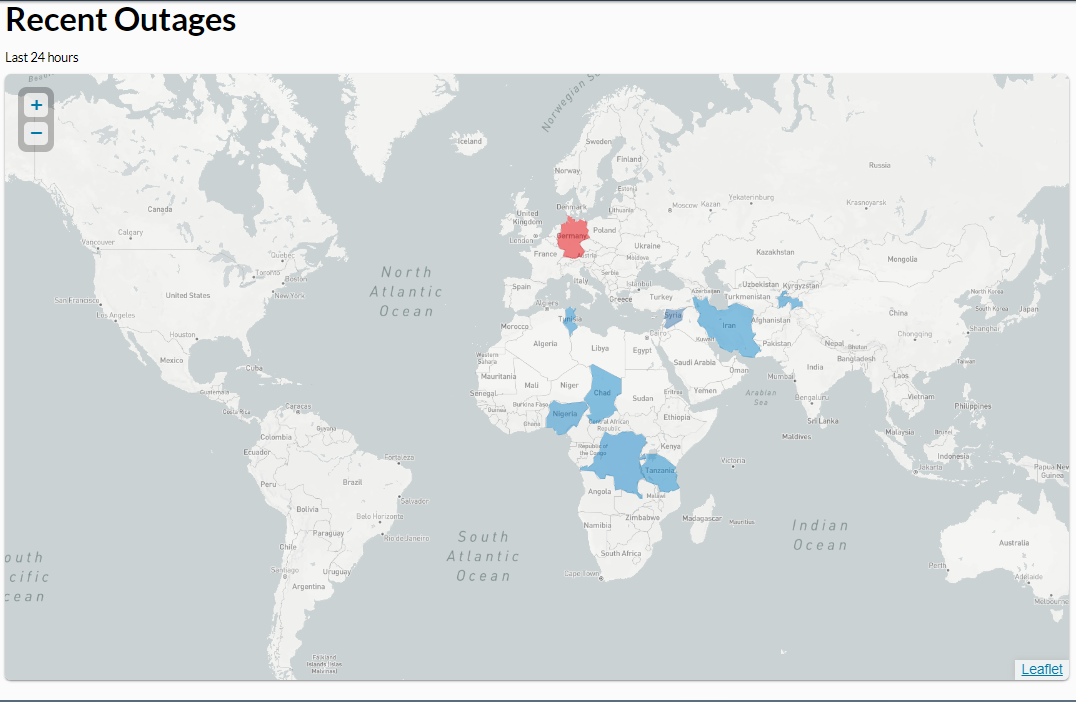
Applications have regularly occurring outages and or delays. Big tech giants like Microsoft, Reddit and Snapchat are also subject to these outages.
Internet
Between 2018 and 2020 there were anywhere from 155-213 government-induced internet shutdowns in 25-33 different countries (10). We hear stories of the great Chinese firewall, but the reality is all over the world individuals are being censored and having surveillance placed upon them by governments (11).
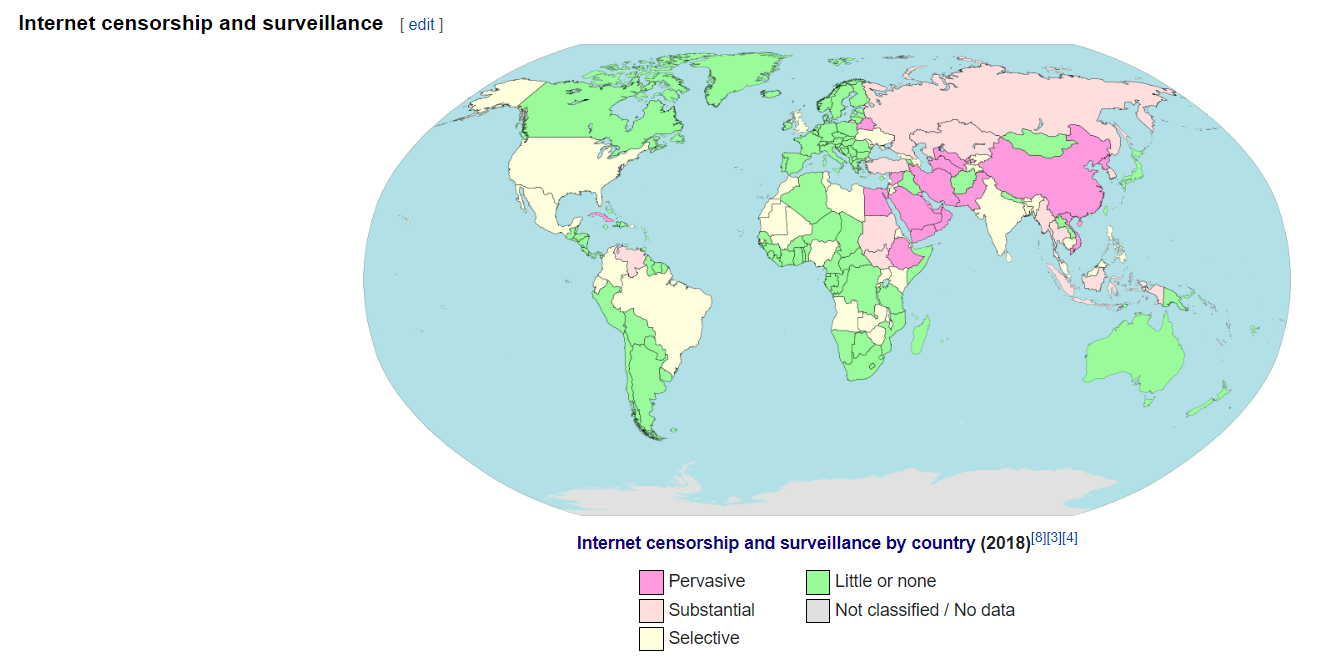
The level of internet censorship ranges from short term blackouts and disruptions, to persistent multi-month or multi- year blackouts and disruptions, to somewhat restrictive long-term controls with disruption surges, to highly restrictive long-term structural controls (13). On average an internet outage costs per person anywhere from USD $0.06-$2.36 per day (14). To give one example, in 2022 to today (6/19/22), Russia's internet outage has cost them USD $6,770,000,000 (15).
One company, Level 3 (acquired by Lumen Technologies), handles sending data to and from (through IP addresses and ASes) just under 80% of the conventional internet (17). This company has been accused of wiretapping Google, Yahoo, and a German Internet Exchange Point on behalf of the National Security Administration of the US (17). Other major companies in this domain (IP addresses and ASes) manage a slight percentage in comparison to Level 3 (such as Cogent, Global Telecom and Technology, TeliaSonera International Carrier, NTT Communications, Tata Communications, Telecom Italia Sparkle). However, they have been caught up in similar legal ordeals. Such as TeliaSonera collaborating with certain dictatorships, allowing them to spy on their citizens, and in 2012 they were investigated for bribery and money laundering in Uzbekistan (17).
Transport
A complex system of fiber cables, satellites, receivers and transmitters transports data globally. Rodents often represent a more practical threat to these systems than cyber attackers (18, 19). Though signal jamming can still take place by entities, including governments. There are many different businesses involved in transport.
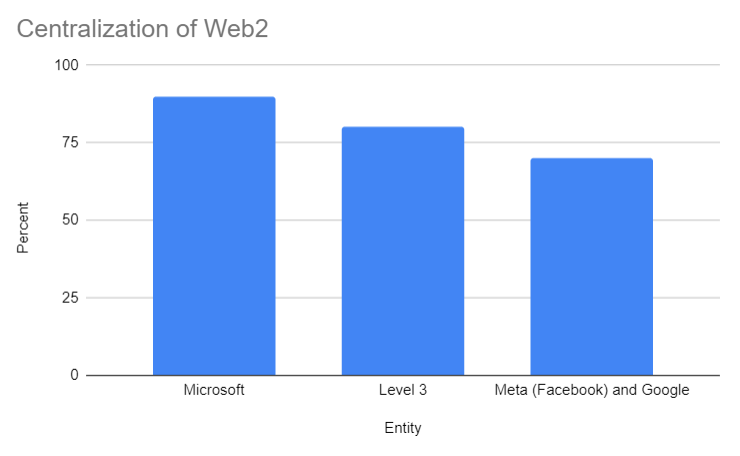
Centralization of the Web
4 companies are able to access and utilize anywhere from 70-90% of data on the internet. This creates a dangerous level of centralization. These companies are able to influence governments to individuals in the way they access, interact with and transmit data. Governments can block the data being transmitted and cater it to their liking for the population, which is already done globally. Allowing corporations and governments to control the flow of data allows select individuals to have disproportionate power as compared to the rest of the population. If the top apps were to pay you for the data you generate when using them (Google, Facebook, Twitter, Amazon, etc.), you'd get around $2,000 a year (20). At the same time it would take the average Facebook user alone being paid over $1,000 a year to stop using Facebook (21).
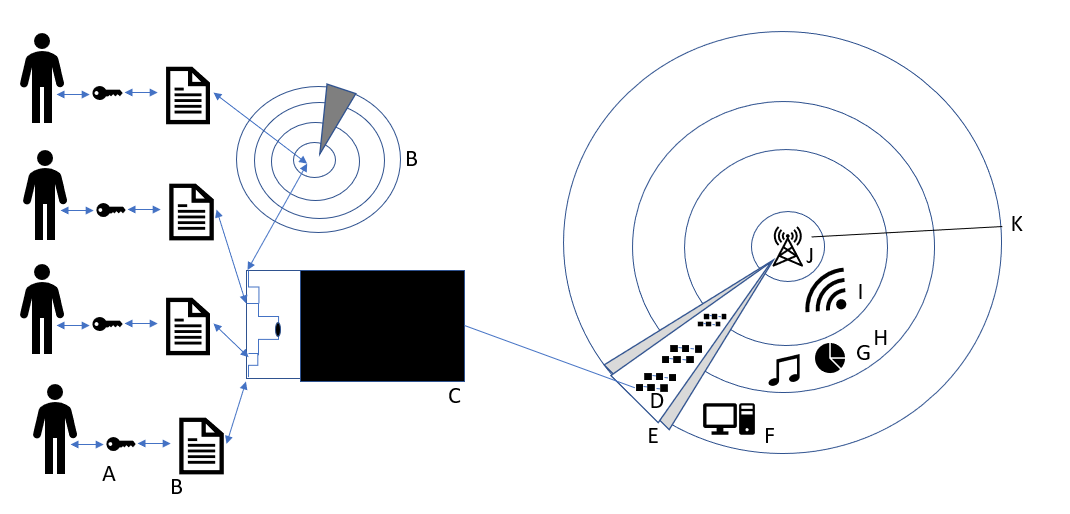
When the internet started, the intention was to build a common decentralized network with equal participation, that communicated peer to peer without relying on a single intermediary. Along with that an important consideration was that computers must be interoperable among dissimilar systems, so that more devices could be a part of the network (22). Problems with centralization have arisen, however it's not too late to alter course, large parts of the world are still not connected to the web.
Progression of people being connected to the web until 2012 (8)
Web3
The components of Web3 are a wallet, smart contracts, blocks, blockchains, indexers, physical, data, apps, internet, transmission, AI and machine learning.
Wallet
The frontend of Web3 can be viewed through any browser (for example type in https://uniswap.org/). However, in order to do anything that changes web3 a wallet needs to be used. A wallet is a combination of a public and a private key. Keys are hashed so the resulting output looks similar to "0x2D237B830B6dC666439b963B2C0871E3e7f6C020" publicly. Hashing is the process of transforming characters (letters or numbers) into another value (can play with hashing here: (23)). In order to read on web3 the wallet needs to be unlocked by a person. A person unlocks their wallet with their private key (like a password unlocks an account). In order to write on web3 (carry out a transaction), a signature needs to be used. The person signs a new write, with a digital signature. Anyone can have a million wallets, each one of these wallets can be anonymous (not able to be traced back to a specific person).
Smart Contracts
A smart contract is a program that runs on the blockchain and defines the logic behind transactions. Smart contracts are written in high level languages (such as solidity, vyper, rust, etc.). Anyone should be able to view the smart contracts as they are open source. Once smart contracts are written they are compiled into bytecode so they can be executed.
There are four different layers where smart contracts operate the data layer, system layer, function layer, and execution layer.
The execution layer is code that is regularly needing to be updated, such as the frontend of the website. These updates do not alter functionality of web3. The function layer is how people do transactions on web3. The function layer can be updated by adding a new smart contract that adds a new component of functionality. Once a transaction is set in motion, the system layer relays that transaction to the rest of the network. System layer is about the network level and are smart contracts around participation incentives, encryption, anonymity, consensus mechanism or network permissions. Changes to system layer can be done, however this results in splits in the network (those who agree to the update vs those that don't agree with it). Due to this, system properties are only conditionally immutable (immutable on the condition that everyone agrees with everything that has been done thus far). The conditions are of interest to users, investors and regulators and have to be published upfront ideally within the first whitepaper. The data layer is any data that is stored on the blockchain, after a few blocks of confirmation this layer is considered to be immutable.
Blocks
Once a person triggers a transaction through a smart contract and their wallet, computers that are part of the network pick their transaction to include in the block. Transactions are prioritized based upon the amount of transaction fees paid, the ones that have paid the highest transaction fees are picked first (gas). The pooled transactions (mempool) are paired together until only one remains (merkle tree). Each pair gets hashed until the only hash that remains is the final one, the merkle root. In the case of Bitcoin this process is repeated every 10 minutes. The merkle root is stored in the blockchain and holds not only the transactions that were paired in that block but all the transactions that have occured in the blockchain, as the previous merkle root is paired in each new block. The entirety of the record of these transactions is 400 GB for Bitcoin, however all computers computing in the blockchain don't need to store the entirety of this data, they only need to know the previous merkle roots (these roots are often provided by mining pools). As the entirety of transactions on a blockchain are distributed across many computers, it is called a distributed ledger (Distributed Ledger Technology (DLT)). In order to know if a transaction is valid, computers look at the past transactions. It's near impossible to do a false transaction as it would completely change the merkle root.
In order to change the difficulty of mining a new block to the point where a new block is only mined around every 10 minutes, a nonce needs to be used. A nonce is a random number that needs to be included for the hash to be successful. The difficulty is changed every 2,016 blocks (roughly two weeks) based upon the timing it has been taking to mine blocks.
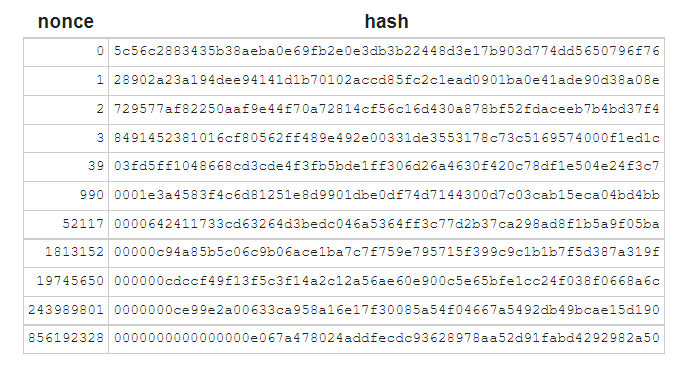
Currently computers need to try around 30 trillion times before they are able to come up with a successful hash. If a computer tried a new hash every second, it would take 30 trillion seconds or 900,000 years (three times longer than the existence of humans on this earth (24)). When a successful hash is found it is broadcast to the rest of the computers participating in the network. These computers back check the hash and if 51% of the computing power agrees that it is successful this block is added to the blockchain. Several other components are added into block details such as the blockchain version (version 0.01, 0.02 etc.), the block height number: how far away numerically the block is from the first block, timestamp: time and date, target in bits: network target. Once these details are included and the computers in the network achieve 51% consensus that it is a successful hash, the computer that found that hash is rewarded tokens (Bitcoins are rewarded for the Bitcoin blockchain). The token distribution event is called a coinbase. Along with that they receive the transaction fees for the transactions they included in that block. Most cases these rewards are distributed across a mining pool (pool of computers). A mining pool increases the chances of finding a successful hash by pooling together computing power.
Proof of Stake
Proof of work is energy intensive, one of the ways in which the efficiency of this system has been improved is through proof of stake. In proof of stake, people stake tokens that are part of that network. Staking locks the tokens for a period of time (agreeing not to sell them). People that stake their tokens are now able to be validators of that network. Instead of finding nonces with their computing power hashes are computed according to the amount of tokens staked (a blockchain with 2 tokens staked has twice the difficulty of one with a single token staked). Rewards still come from transaction fees and potentially coinbases.
There are other proof systems such as
· Proof of Capacity
o In this system computers share memory space · Proof of Activity
o Hybrid of both Proof of Work and Proof of Stake · Proof of Burn
o Burning (making them not able to be used) tokens · And More
Blockchain
Once a block is confirmed it is added to the blockchain. Blockchains can only be written on, existing data can't be updated.The blockchain is able to add a layer of immutability to these write actions.
The blockchain could be altered in the case that someone is able to gain control or create a false transaction that 51% of the network agrees to. Let's estimate the cost of a 51% attack which reverses a year of bitcoin transactions. At the current bitcoin price of $32,521 and reward of 12.5 bitcoins (including transaction fees) per 10-minute block, miners earn around $21 trillion per year ($32,521 × 12.5 × 6 × 24 × 365). If someone were to alter the blockchain it would cost miners in the network a huge amount of money, thus it is to each miners great advantage to keep the blockchain record valid. Blocks are only confirmed and awarded after an amount of time has past. If 51% of the network were to be gathered to alter the blockchain, that amount would need to be kept for an extended amount of time (potentially costing a lot of computing power energy in the case of Bitcoin). The further back a block is in the blockchain the harder it is to alter.
If alteration of the blockchain were to be successful there is still the possibility to fork the code of the blockchain and create an entirely new blockchain that goes back and erases the alteration, such as the case of Ethereum and Ethereum Classic (25).
Indexers
In order to make the data stored on the blockchain readable, indexers are used (such as application programming interface). These indexers allow for retrieving data from prior transactions as well as making it human readable (The Graph, Alchemy, and Moralis are examples of indexers).
Physical
To take the first step into web3, take your computer, mobile phone or other electronic device and replace it's operating system with a privacy preserving open source one (such as Linux or Tails). This operating system will allow you to keep personal control of your data, unlike Microsoft, Apple and other operating systems. In terms of what the device is, it doesn't really matter. Electronic devices will continue to be produced no matter the web version we are on or operating system we use.
All electronic devices (cellphones, smartwatches, sensors, computers, headphones, etc.) are able to be a part of web3. Most people don't want to run a lot of electronic devices that have a lot of storage space and computing power, some do. Event then, it's unlikely that you are always using all of the computing power and storage space that your electronic devices have. At times when this computing power and storage space is not in use by you, it should still be able to benefit you. Decentralized storage (Filecoin, Storj, IPFS, Arweave, etc.) and computing power systems (Golem, iExec, Sonm) allow you to sell excess storage and computing power when not in use. At the same time it allows you to purchase storage and computing power when needs demand, all while maintaining anonymity. The potential for this means that you could pay to trigger an analysis that needs the computing capacity of several super computers from your smartwatch or someone can pay to upload their data, retain sole control of it and have versions of it spread across hundreds of computers.
Electronic devices that are part of web3 will be able to receive and transmit in an ever increasing number of wavelengths (such as bluetooth, wifi, radio and other relay techniques) as well as translate them into other forms (such as translating radio into wifi).
Data
Interacting with the web is where it gets tricky in terms of data. Even the most advanced web browsers (TOR, Brave Browser, etc.) are profiting from the data of their users (26, 27). Codes on most websites track information on the people that visit them (such as Javascript). Though this code is not directly owned by any one organization. It's used by several, such as Google Analytics, as something that can be put into the website to track more info on the people that are visiting it. Google Analytics is used on 55.7% of all websites and caters data not only for those websites but for Google as a company (that's not to mention tracking done by Google Scripts) (28). TOR, Brave and other browsers don't pay their user base for the data collected of them by Javascript, instead they fund their organizations with this money (TOR has the ability for users to opt out). Luckily TOR, Brave and other browsers are open source and can be forked. Integrating the ability in this forked version of a browser can allow users to have ownership of this data and monetize off it using data marketplaces (Ocean Protocol, dClimate, etc.).
Applications
Applications for video sharing (Youtube, Tik Tok), social media (Facebook, Instagram), messaging and video calls (Zoom, Skype), Music (Spotify, Pandora) are already becoming decentralized. If you look up decentralized applications in front of each of the types of applications you are interested in, it will show a list of dapps already available. Levels of decentralization of these apps are questionable, one of the major NFT marketplaces for example (Opensea) was able to stop transactions from occurring rising questions over the level of centralized authority that OpenSea has (29).
Internet
In web2 interacting on the internet is routed through domain names, DNS, and IP addresses. In web3 these interactions are routed through decentralized naming conventions (like ethereum name service, ENS) that are tied to a contract address (mix of letters and numbers that looks like 0x2D237B830B6dC666439b963B2C0871E3e7f6C020).
Transport
Fiber transport layers are fragile as they break by getting gnawed by rodents, have a limited life span, and only distribute to areas attached to their cables. Satellites are likely to become an increasing transport layer. Satellite systems for transporting blockchains (such as Bitcoin) are already appearing (such as Blockstream Satellites). However, entities (such as governments) are able to block electromagnetic wavelengths (such as radio) from these satellites for receivers. The most powerful blockers known can only block a wavelength in a buffer of up to 125 miles (30). If receivers outside of this buffer are still able to receive it, the signal could be relayed through small range network connections, such as mesh networks. These networks connect to electronic devices to communicate with each other through the electromagnetic spectrum (bluetooth, wifi, radio and other relay techniques) (Helium, FOAM, TxTenna). Any electronic device, could be relayers in a mesh network. These same devices could also potentially serve as translators for altering the communication into another wavelength in the electromagnetic spectrum (such as translating radio to wifi). When an entity blocks the signal from a receiver the mesh network can send a message to transfer to another wavelength (for both transmission and reception). As there are almost an unlimited amount of wavelengths, using coordination, it would be very difficult to block.
Artificial intelligence (AI) and Machine Learning
As most of the data that is part of web3 is able to be accessed through reading the blockchain and paying for access to people's data, extensive machine learning and AI can be built. These AI and machine learning algorithms will enable greatly improved efficiency and accuracy in how we interact and interpret ourselves, the world around us and transactions. As these algorithms will be open source, further iterations can be created of them enabling further changes to suit our needs.
Metaverse
The way in which we interact with web3 and the data on it will likely transform into 3 dimensions, especially with further integration of IOT devices in our lives. Various metaverses, alternate online 3 dimensional realities, will be created based upon community values.
Web3
Currently web3 is ran on web2, though web3 could be done through carrier pigeons, smoke signals, or wire fences.
Web 3.0 is own, read, write. In order to interact with the web, people need to own hardware. What is done on this hardware is up to the individual and the data that is created from interacting with the hardware is owned by the individual, self sovereignty. People are able to read anything that is part of web3 as all the base code is meant to be open source (transparency). As the code is open source anyone can do a permissionless fork and build new iterations of that code. Codes work together and interoperate to create web3. When people write on this web, they sign transactions and with this transaction the web is further developed. As writing is creating new data, the writer needs to be compensated for their contribution. Often times this transaction is done through tokens. As anyone is able to purchase hardware that can engage with web3, anyone can actively participate and further develop web3. When they develop web3, they can do so anonymously. There is no intermediary that says you can and can't do a transaction. Empowering a decentralized network for continued contributions.
Product idea: Login to a device through a crypto wallet, create a virtual machine run Linux/ Tails on it, Fork TOR so no data is sold through organization and people have the choice to sell their data to benefit them on data markets, allow people to opt in their devices for decentralized storage and computing power systems, if they opt in for decentralized storage allowing that storage to be accessible to data markets, allow that computer to become a multi wavelength transceiver and translator. Integrate further components of web3 into this as they become applicable.
Resources
2: http://www.sciencefocus.com/future-technology/how-much-data-is-on-the-internet/
5: https://www.reuters.com/article/us-microsoft-windows-idUSTRE69K2L420101021
6: https://cdn0.vox-cdn.com/assets/4537135/WorldData.png
8: https://www.vox.com/a/internet-maps
9: https://www.thousandeyes.com/outages/
10: https://www.accessnow.org/cms/assets/uploads/2021/03/KeepItOn-report-on-the-2020-data_Mar-2021_3.pdf
11: https://en.wikipedia.org/wiki/Censorship_by_country
12: https://www.youtube.com/watch?v=K62fiw7inKE
15: https://www.top10vpn.com/research/cost-of-internet-shutdowns/
16: https://ioda.inetintel.cc.gatech.edu/
17: https://yudhanjaya.com/2016/06/who-owns-the-internet/
18: https://therecord.media/canadian-internet-outage-beaver/
19: https://www.1news.co.nz/2022/05/11/rats-gnaw-west-auckland-fibre-cables-knock-out-internet/
20: https://arkenea.com/blog/big-tech-companies-user-worth/
21: https://journals.plos.org/plosone/article?id=10.1371/journal.pone.0207101
22: https://ieeexplore.ieee.org/stamp/stamp.jsp?arnumber=8717702
23: https://xorbin.com/tools/sha256-hash-calculator
25: https://www.gemini.com/cryptopedia/ethereum-classic-etc-vs-eth
26 https://www.tor.com/privacy-
notice/#:~:text=to%20Contact%20Us-,Information%20We%20Collect,Sites%20or%20from%20third%20pa rties.
27: https://brave.com/privacy/browser/#brave-talk
28: https://w3techs.com/technologies/details/ta-googleanalytics
29: https://beincrypto.com/2-2-million-bored-ape-nfts-stolen-opensea-freezes-transactions/
30: https://www.afcea.org/content/jam-proof-signals-guide-navigation